 |
i-manager's Journal on Mobile Applications and Technologies |
View PDF |
|||
| Volume :2 | No :4 | Issue :-2016 | Pages :1-10 | ||
Nowadays MANETs have obtained a sensible interest due to the growing number of wireless device users. Hence, Mobile Ad-Hoc Networks are used in real time applications, and these real time programs need QoS assurance in terms of throughput and delay. Hence, it assets the QoS in MANETs. The main problem is the communication which is more a shared standard in a particular channel. In this work, the authors suggest an Achievable Throughput based Admission Control Protocol (ATACP) for controlling a channel from becoming overloaded, thereby making sure an assured throughput for real time traffic. Achievable Throughput based Admission Control Protocol works on a cross layer structural design that encompass the network and the MAC Layer and the admission control is carried in each node during the path discovery. The node broadcasts the route request to its neighbors providing its achievable throughput that satisfies the desired throughput considering the contention count. The performance of the ACP maintains the ineffective overhead throughput and End-to-End Delay MANETs. This work proposes the improving routing mechanism in MANETs using discovery routing protocols to achieve the effectiveness of throughput and less end-to-end delay over Mobile Ad-hoc Network.
Mobile Ad-hoc Networks (MANETs) are an infrastructure - less dynamic network or a group of wireless mobile nodes that communicate with each other completely different without using any centralized authority. Specifically, these wireless standards enable direct communications among network devices inside the transmission range of their wireless interfaces, therefore creating the single hop ad hoc network a reality, that is, infrastructure-less WLAN/WPAN wherever devices communicate without the necessity for any network infrastructure [1]. The multi-hop paradigm was then formed to increase the possibility to communicate with any few network nodes, without the necessity to develop any present network infrastructure. Standard protocols, AODV, Optimized Link State Routing (OLSR), Dynamic Source Routing (DSR), and Topology Broadcast supported Reverse Path Forwarding (TBRPF) have their execs and cons, and none of them is superior to the others altogether contexts. The performance of Mobile Ad-hoc Networks is related to the efficiency of routing protocols. Efficiency depends on many factors such as junction time after topology changes bandwidth overhead to enable the accurate routing and power consumption. The routing protocols in MANETs ought to scope well with dynamically every changing topology, and nodes should exchange the information on the topology of the network so as to ascertain routes. Routing in MANETs is difficult. The hop count is once a most commonly used metric for choosing a route from a supply to a destination. However, this metric might perform poorly in networks as a result of a route with a minimum hop count and might include slow links, therefore leading to poor end-to-end throughput. The existing paper proposes a Reward Based Routing Protocol (RBRP) to boost network stability [5], which tends to propose an Achievable Throughput based Admission Control Protocol to control the amount of traffic within the network and stop the channel from becoming overloaded, thereby the throughputs of the continued real time flows are not disrupted. Achievable Throughput based Admission control Protocol (ATACP) provide an admittance control for the introduced flows during a per node basis. It supports an achievable per node throughput. Every node calculates its achievable throughput by allowing the available resources for neighbors. Achievable Throughput based Admission Control Protocol is implemented over RBRP, which uses the on-demand nature of RBRP to do the admission control throughout the route discovery. There are four relevant problems to be considered, once calculating the achievable throughput during this context [3].
In multi-hop transmission, the forwarding nodes on a path at intervals has the sense range on a path that challenges to broadcast the information packets contention among the packets that are forwarded within an equivalent carrier sense range on the route. The amount of those nodes is termed as Contention Count (CC), in which every flow will consume bandwidth equal to the CC times needed throughput by the application.
Before transmission of a packet, the node performs handshaking among the spreader and also the next receiver using RTS/CTS packets. This handshaking method is used to reduce the collisions due to the hidden node problem. However, these packets will increase the delay of broadcast of data packets, and the RTS/CTS handshaking is completed as follows. The node that has an information packet required to be sent, sends Request to send the packet to the receiver which in turn waits to receive a packet. If the node receives the CTS packet following Short Inter Frame Space time, it sends its information packet. The nodes that respond to these messages defer their transmissions.
The channel in MANETs is shared among the nodes that are settled within the variety of nodes, so the packets of two or more nodes are sent at the same time, may collide at the receiving. Moreover, the channel in MANETs is time unstable and is prone to bit error. The error and also the collision lead to the corruption of the packet that leads to retransmit the packet.
In a MANET, the incoming flows will affect the throughput of the continued flows within the contention space. So, every node should inform its neighbors within the carrier sense range regarding its available resource, thus, every node uses the minimum of the available resources within that range.
A number of approaches have been reported in the literature for improving the routing mechanism in Mobile Ad-hoc Networks, when the link is a failure.
This existing paper proposes a Reward Based Routing Protocol (RBRP) for MANETs. The goal is to improve the routing excellence of MANETs, use the information obtainable and towards increasing the quality of the path finding in MANETs using data available in the network. By choosing a stable path, the overhead and the amount of hops in the path discovery are decreased and the use of powerful and vigorous paths are optimized. The important parameters of the planned method are as follows [7] .
Hop count is the distance among the routers or the number of hops for a possible path, the smaller the HC the more consistent is the routing path. The route collection algorithm prefers the route that reaches the destination node first, because it is fewer congested than the others, also this route may contain highly available mobile nodes which create link breakdown more likely.
Figure 1 shows, the source node ‘S’ more balanced to check the hop count to make the finishing choice for a route. If each intermediate host has a large roaming area and the MANETs has many nodes, then a possible path with a low hop count is chosen. When a source node wants to send data to a destination node for which no admission in its route cache is available, the route detection is initiated and a route request is broadcasted. Node D knows the Hop Count value of the three possible paths via the hop count in the RREQ packet.
As shown in Figure 1 for, Path I= S, A, K, M, H, D; HC1 = 5, and path II= S, B, D; HC2 = 2, and path III=S, C, E, F, D; HC3 = 4.
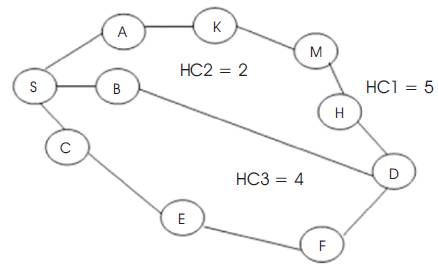
Figure 1. The Hop Count of each Possible Path
The method to define the Bandwidth is to evaluate the available bandwidth between two adjacent nodes at the similar velocity that they are alienated by a direct and symmetric link. A simple method described defines the available bandwidth on the beginning of broadcast speed, where this technique can be used to measure the bandwidth for an (I, J) connection. This link has an obtainable bandwidth as given below,
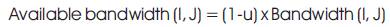
where, u is the link use and (u = A (t)/t). A (t) is the sum of amount of time, at what time the link is used by the nodes throughout an interval of time t.
This parameter accounts for the power necessary to complete sending of a file or data before the data package is distorted by allowing for the size of the package.
This parameter shows the rate of mobility for mobiles. The reliability of a possible path is based upon Hop Count, Bandwidth, Power of Battery, and Speed based on the preceding conversation. An algorithm powerfully unite all four parameters with evaluate factors K1, K2, K3, and K4, the values of which can be selected according to the system supplies.
Figure 2 shows the threshold value for the parameters. For example, Power of battery is very important in MANETs, therefore the weight of this issue can be greater than the flexibility to modify factor that helps the algorithm to select a direction-finding path with better values of bandwidth and the power of battery which represents the higher reliability with lower values of Hop Cunt and Speed, if suppose the quantity threshold for each parameter [13] .
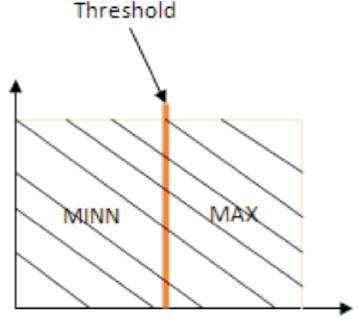
Figure 2. The Threshold Value for the Parameters
If the value of the Bandwidth and Power of battery parameters are bigger than the threshold, then the reward value of this parameter can be selected as 1 or -1. If the values of the additional parameters Hop Count and Speed are larger than the threshold, then the reward value of these parameters can be designated as -1 or 1. For example, suppose the threshold for Bandwidth has a rate of 6,000,000.0, the Bandwidth is significant in the mobile ad hoc networks and it is a preferable use for the price of bandwidth to be a greatest span. If the value of BW is 6,000,000.0, then the reward rate of BW (ROBW) can be elected as 1 or -1. The reward function is defined as an experimential mean value, where each point is standardized as main and next, the four quantities are combined with equation (2).
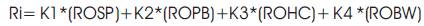
where, |K1|+|K2|+|K3|+|K4|=1; ROSP = Reward of Speed; ROPB = Reward of Power of Battery; ROHC =Reward of Hop Count and ROBW = Reward of Bandwidth.
To reveal the route collection process on the base of the reward function, if suppose K1=-0.4,K2=0.3,K3=-0.1,K4 = 0.2 then the adverse input to the reliability is build into the depressing coefficients. The route with the maximum reward value is preferred as the routing path [11] .
1. Start
2. Source S receive a packets from transport layer of destination D
3. Checks if route exists for destination
4. If already has a route it transmits the packets to the next hope.
5. If node X receive a RREQ packet request with source S, destination D with Sqn1.
6. X calculating R
7. Ri=K1x(ROSP)+K2x(ROPB)+K3x(ROHC)+K4(ROBW)
8. If
9. Pair(S,D) is existing in a routing table of Sqn2
10. If
11. {
12. (Ri>0 and Sqn1=Sqn2)
13. (Sqn1>Sqn2)
14. }
15. X updates the routing table
16. If
17. {
18. X=D
19. X calculating existing reward value in the PREQ packet and Ri.
20. }
21. X create a new pair(S,D) with Sqn= Sqn1
22. When node X receive an RREP packet from node Y
23. Calculating reward Ri
24. Ri=K1x(ROSP)+K2x(ROPB)+K3x(ROHC)+K4(ROBW)
25. If pair(S,D) exist in the reverse routing entry table
26. If(Ri>0)
27. {
28. X updates the reverse route entry table
29. X forward the RRER packets to the previous node
30. }
31. Else{
32. X forward the RREP Packets to the previous node
33. Else
34. X create a new type in the reverse route entry with next node
35. }
36. If
37. {
38. X≠S
39. X forward the RREP packets to the previous node.
40. }
In Mobile Ad hoc Networks (MANETs), interferences diminish the network performances like data breakdown, retransmission difference and delay. Hence the interferences are the main factors that have an effect on the network performances. The dropping of interferences on top of the paths are an important problem to improve the performance of the networks. Here, they have proposed a protocol call link disjoint interference aware QoS Routing Protocol supported MARIA Protocol. The capability of networks is strictly affected by the interferences among links and various efforts were made to represent this effect, create the use of 'Cliques' structure in ad hoc graphs [2]. This application gives a thorough overview of the QoS routing metrics, resources and factors affecting the performance in a MANET. The aim here is to improve the communication in wireless mobile ad hoc networks by identifying the locality of mobile node using the Predictive Location Based Routing Protocol and admission control mechanism. This application proposes an optimization based on connections between routing and the admission control layer proposes an essential presentation improvements [11]. An effective Mobile Ad hoc Networks need QoS capability that gives the fault acceptance and fast improvement mechanism when there is a link breakdown and Mobile ad hoc network is a dynamic topology in nature, so the protocols used in multi-hop networks preserve the routing constancy in this document. An efficient call admission control scheme is used to preserve the flows in the network. The use of bandwidth by a flow and the accessibility of property to any wireless node depends upon the adjacent nodes within its transmission range [4]. To reserve an end-to-end bandwidth, in Quality of Service supported wireless ad hoc networks, the neighboring bandwidth responsibility should be cautiously resoluted by considering the amount of challenging nodes in an interfering range. The authors proposed a new admission Control Protocol called DACP (Distributed Admission Control Protocol) which implements more than a reactive ad hoc routing protocol by minimal overhead. Distributed Admission Control Protocol computes the essential bandwidth for an end-toend bandwidth condition at each node and estimates the available bandwidth at the standard access control layer. After that, the DACP makes a resolution for admitting a flow in a per hop basis [12].
The proposed ATACP identifies the problems earlier and exposes the gaps in the existing literature [7]. The achievable throughput is defined as the number of packets that can be broadcasted among two nodes exclusive for disturbing any obtainable flows. The ATACP is implemented over the routing protocol RBRP. It considers both types of contentions, the intra flow argument and the inter flow argument. Also, the additional issue mentioned previously to ATACP utilizes the Hello messages which are used in RBRP for ensuring the connectivity, to execute two functions, receiving the identity of the neighbors inside node's carrier sense range which is useful in calculating the contention count throughout the route detection.
In ATACP, instead of exchange, the achievable throughputs between the nodes of the careful local idle fractions are exchanged within two hops. This makes every node to calculate its achievable throughput inside the smallest of the exchanged idle fractions based on it's situation possessed, which are the packet size of new flow and the condition of the MAC layer. This allows the utilization of the protocol in various surroundings. The ATACP is a cross-layer move based on two layers which are the MAC and routing layers which cooperate in order to evaluate the achievable throughput as shown in Figure 3 [10].
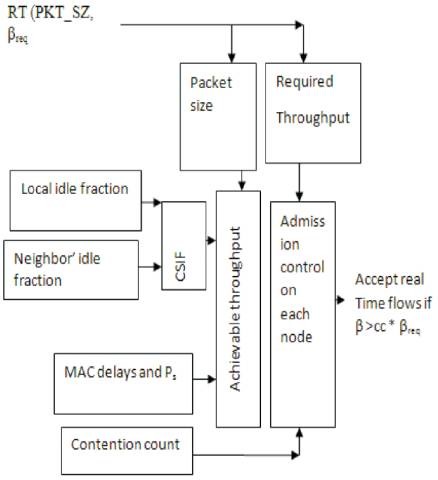
Figure 3. ATACP Model
ATACP is an on-demand routing protocol and its route discovery process is similar to that of AODV. The route finding procedure is starting, when a source node wants to converse with another node for which it has no routing in order in its table. The source node initiates the route discovery by broadcasting an RREQ packet to its neighboring nodes [6]. The RREQ packet format is shown in Figure 4. The Request ID is increased each time, whenever the source node sends a new RREQ packet. So the couple source address requests an ID to identify an RREQ packet uniquely. Upon receiving an RREQ packet, each node checks the source attend to and the request ID. If the node has already received an RREQ packet with the same pair of parameter, the new Route Req packet will be useless. Otherwise, the RREQ packet will be either forwarded (broadcast) or replied to an RREP packet.
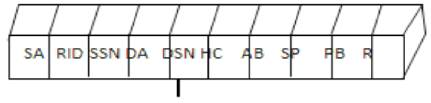
Figure 4. Admission Control in Request Phase
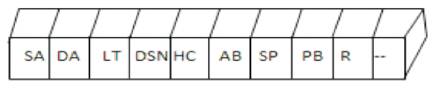
Figure 5. Admission Control in Replay Phase
Due to high mobility of nodes in MANETs, the links breaks easily. The ATACP route maintenance is initiated, when the route is energetic and the data packet is transmitting. A link failure occurs, when a mobile node moves regardless of the radio broadcast range of the one more mobile node. The mobile nodes check their own neighborhood. When a node in an active route gets lost, a route fault RERR packet is generated to alert the further nodes on both sides of the link which is lost. The proposed algorithm can be summarized as follows, assume that the source node S wants to discover a path to target node D that nodes I, J are choose to be the transmit node, and that the link between node I and node J is broken. When a link is broken down, node I receives an RERR packet, if node I detects the breakdown of the link to the after that node,
1) I sends the fault packet.
2) S receives the fault packet.
3) S stops sending the data.
4) S restarts the route finding process or finds an another path for routing. Otherwise, Node I continues to send the data [9].
Accordingly the delay (D) by MAC layer,
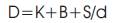
Get greatest throughput with an intention that can be achieved between two nodes in a particular hop,
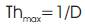
Probability of the successful transmission,
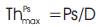
Achieved throughput can be estimated within the measured Local Idle Fraction (LIF),
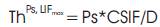
Avoid degradation of throughput of the ongoing flows within the carrier sense range, maximum idle fraction (CSIF).
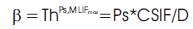
Contention Count,
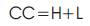
1. Admission control (βreq, pkt_ sz, Destination _ IP, Hop _ count)
2. {
3. Get LIF, K, Ps , Medium capacity;
4. CSIF + Min(LIFI,MLIFN); // calculation of the contention count
5. If (this node is the destination)
6. L = 0;
7. Else
8. {
9. L = lookup in neighbors Table(destination _ IP)
10. If (L = null)
11. L = 3;
12. }
13. If ( L < > l) & & (prev status = 0)
14. {
15. Discard the route request;
16. Exit();
17. }
18. Prev_ status =1;
19. If (hop count <=2)
20. H = hop count;
21. Else
22. H=2;
23. CC = H + L; // calculation of the achievable throughput
24. D = K + Pkt_sz / Medium capacity;
25. β = (Ps * CSIF)/D;
26. β = (s * LIFI) / D;
In this part, the effectiveness of the solution is calculated in relation to the existing Reward Based Routing Protocol (RBRP). The ATACP routing protocol, uses the broad simulations. The simulation is conducted by network simulator Ns2 and the simulation is presented in a 1200 m 9 1200 m with 50 randomly positioned nodes [7]. Table 1 shows tha parameters required for the simulation.
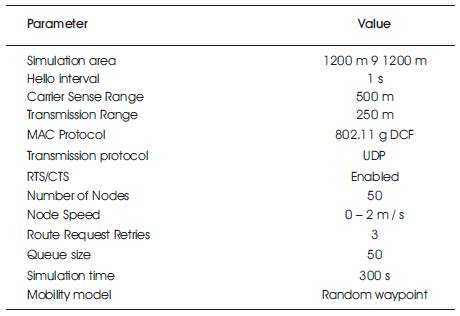
Table 1. The Parameters of the Simulation
The metrics which are used to measure the performance of ATACP is compared with the previous techniques be the flow of admission ratio, throughput, end-to-end delay and normalized overhead routing. The flow admission percentage is defined as the portion of demand assembly that was accepted. This is used to measure the accuracy of the admission control method, where the number of accepted session beyond the capacity of the network affects the performance of the system. The throughput is defined as the standard amount of packets that can be delivered over a communication channel.
For each flow, the average end-to-end delay refers to the average time taken for a packet to be transfer through a system from a source to destination. The normalized overhead routing is the ratio of the amount of overhead towards the total number of transferred data packet. The overheads include routing packets such as the route request and the route reply. The flow admission ratio for video and voice traffic, the ratio between the numbers of the conventional flows more than the sum of admission requests, as a function of the traffic load. The ATACP and RBRP reduces their admission fraction as the obtainable traffic load increase establishes that, the ATACP outperformed RBRP for both traffic. The reason is that the ATACP admit only the flows whose essential throughputs could be met by the network [8]. The ATACP considers the resources used for the obtainable flows within a carrier sense range. Also, it estimates the contention count more accurately than RBRP, especially for routes that have more than four hops [2].
Figure 6 shows the results of scenario to evaluate the average throughput of the admitted flows as a function of the simulation time. In this situation, 10 flows with data rate of 1 Mbps are introduced and the reason is that the network becomes congested, which causes the channel overload and collision thereby several packets are dropped. The hop count of ATCP is compared with the RBRP protocols at different simulation times. The hop count of the ATACP protocol was less than that of RBRP, because hop count is one of the certainty factors defined between the nearest mobile nodes. The accepted improvement was about 4.47%.
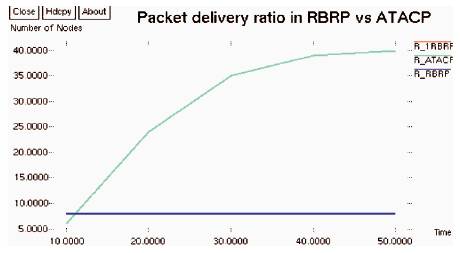
Figure 6. Packet Delivery Ratio
Figure 7 compares the average delay of ATACP and RBRP protocols for different simulation times. The RBRP protocol in Figure 7 can be explained by the fact that the number of drop packets was better for the RBRP protocol than for the ATCP protocol and that the dropped packets that are not in use, report in the average delay calculation. When a packet was not dropped and delivered with a huge delay, the overall average delay was improved. However, if ATCP increases, the network reliability and average delay decreases and the average development was about 67.7%.
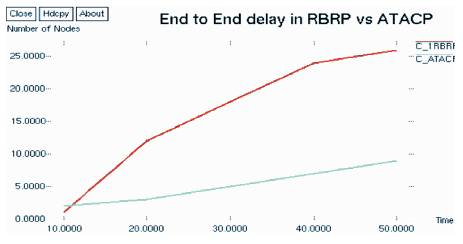
Figure 7. End-to-End Delay
Figure 8 compares the number of ATCP packets sent by the two protocols at dissimilar simulation times. The RBRP protocol generated more requests because, when a node expected a request and the series number was bigger than that of the route entry table, it forwarded the request packet. The average improvement was about 10.12%.
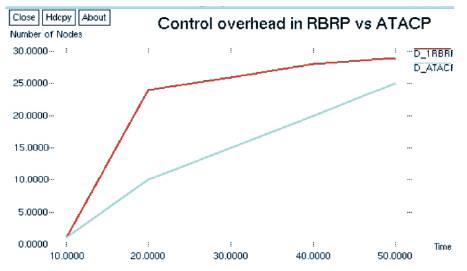
Figure 8. Overhead
Figure 9 compares the route discovery time of the two protocols. The ATCP protocol greatly decreases the route discovery time. The improvements became more important as the simulation time improved. The average improvement was about 35.6%.
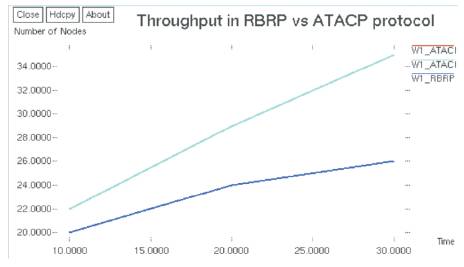
Figure 9. Throughput
The ATACP protocol, uses the admission control based algorithm that determined the suitability of the link, and if the link was fitting, the given node was able to effectively transmit data to it. Thus, the throughput of the proposed algorithm was higher than that of the RBRP algorithm, with the average improvement being about 4.03%.
The throughput by RBRP also decreases, because the RBRP overestimates the achievable throughput and neglects the resources of the existing flows within the carrier sense range as ATACP limits the amount of the admitted flows, thus achieving the throughputs of all flows to be stable [2].
In this document, the obtainable Achievable Throughput based Admission Control Protocol is considered for a guaranteed throughput in Mobile Ad-hoc Networks. ATACP does admission control during the route request; each node broadcasts the route request to its neighbors only if the achievable throughput satisfies the required throughput. This is considered with the contention count and the achievable throughput is provided with the estimation count. The achievable throughput is expected reactively based on the MAC delay, successful packet transmission possibility, packet size and the minimum idle fraction within the carrier sense area. The presentation of ATACP was calculated through the wide simulations using an NS2 simulator. The performance metrics such as flow admission ratio, throughput, average end-to-end delay and overhead of the proposed protocol is compared with the existing RBRP. The results shows that the ATACP maintains the desired throughput of the admission flows efficiently and gives less end-to-end delay and less overhead, improved throughput and a better packet delivery ratio. For future work, the authors plan to evaluate the effectiveness of the priority – based distributed flow admission control in the real world environment.