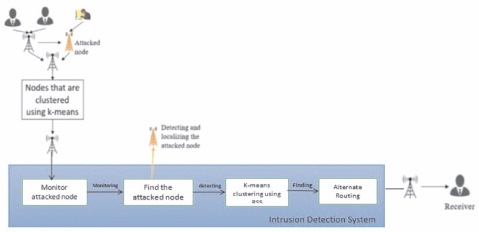
Figure 1. Architecture Diagram of Proposed System
Wireless spoofing attacks are easy to work with and play an important role in the performance of a wireless sensor network. Even if a node's identity can be verified using cryptographic authentication, traditional security approaches are not always desirable due to their ground requirements. Challenging tasks in wireless sensor networks are to detect spoofing attacks, and determine the number of views to attack it, localization of multiple adversaries and eliminating them. The clustering approach is used to identify the spoofing attackers and localize them. But this approach has less accuracy in predicting the attackers. The proposed Intrusion Detection System (IDS) to detect the spoofing attackers helps in solving this problem. The cluster head act, related to IDS, is necessary to monitor the behaviour of nodes in the cluster. For example packet transmission makes it possible to determine the misbehaving nodes of the wireless sensor network. The simulation result clearly shows that the proposed scheme detects the spoofing attackers in Wireless Sensor Network efficiently and robustly. In this, the clusters are formed dynamically and periodically. A digital signature based on a specific protocol must be provided to ensure reliability and reliable data transmission for clustered wireless sensor networks. This paper includes the feasibility of the protocol in terms of security and safety during various attacks, as well as problems to solve the orphan node. The results obtained show that the proposed protocol has a better performance than existing secure protocols for a clustered wireless sensor network in terms of surface, security, and power consumption.
Wireless sensor networks are networks that are simple sensing devices that can accept changes, events/settings, and interactions with other devices in a specific geographic area to allow some specific goals, tracking targets, monitoring, surveillance, environmental monitoring, etc. Wireless networks are usually deployed in an unattended manner and are controlled remotely by the network operator. The maintenance-free nature of wireless networks can be exploited by attackers. In particular, an attacker can capture and denigrate wireless access nodes, as well as launch a series of attacks using compromised nodes. Spoofing is a situation where any person or program successfully disguises themselves as others by falsifying information, and thereby gain an illegal advantage. A huge network of many adversaries are capable of disguising as one another and cooperating to launch malicious attacks quickly, including network resource attacks and denial-of-service attacks. Among different types of attacks, spoofing attacks are simple to launch but degrades the network performance highly. Spoofing is when an attacker pretends to be someone else in order to gain access to restricted resources or steal information. Hence, it is important to,
Most of the techniques were performed to correct possible spoofing attacks that are based on the cryptographic schemes. But the encryption scheme is based on applications that require a strong foundation for key distribution, because it involves infrastructure, management system, and administrative costs. Using spatial correlations based on RSS and physical properties associated with a wireless node, spoofing is difficult and not security-friendly. There are a number of places that have the right to use wireless nodes, geographical location, and data should only be used to detect the presence of a spoofing attack and also to specify adversaries. The spatial correlation method is used to detect spoofing attacks in a wireless sensor network at no additional cost or modification.
Opportunistic networks are mobile networks that rely on the store-carry-and-forward paradigm, using contacts between nodes to opportunistically transfer data. For this reason, traditional routing mechanisms are no longer suitable. To increase the success of successful message delivery, different probability-based techniques were previously studied by various authors. Here we address the question of how much of the forwarding probability of an opportunistic network has to be increased, in order for the network to achieve a given desired hit rate. We propose an approach based on percolation theory, which explains the influence of forwarding probability in a network's performance, and we try to prove that such a phenomenon is indeed present in Opportunistic networks (Wyner, 1975).
Network coding has been studied to enhance reliability and robustness of communications in lossy environments such as high mobile tactical situations. Previous network coding research has exploited on-demand multipath routing, multicasting, or broadcasting to leverage spatial redundancy and improve communication performance. However, one should not ignore proactive routing protocols such as link state protocol OSPF, since the latter is the prevailing protocol used in tactical field communications.
This paper proposes a new routing and network coding strategy based on a link state protocol. This strategy extends the shortest path generated by the link state algorithm to multipath routing; thus providing the spatial redundancy required for efficient network coding (Hong et al., 2013). Liu et al. (2016) have designed an energy efficient multipath routing protocol using adjustable sleeping window (EMRAS) by implementing two algorithmspower and delay aware multipath routing protocol (PDMRP) and slow start exponential and linear algorithm (STELA) using cross layer design. STELA algorithm helps to improve the energy efficiency of the network by adjusting the sleeping window when there are no network activities. When there is any network activity, PDMRP helps to select the path which is energy efficient and also the shortest. Simulation results show that EMRAS protocol has improved the overall residual energy and reduced the total energy consumption without degrading the QoS parameters.
A wireless sensor network consists of a series of sensing devices. These track parameters such as those required for tracking and surveillance and then effectively passes on this information with other such sensors over a specific geographical area within the wireless network. The problem with traditional wireless networks lies in the way that they are positioned in an unattended manner, and being controlled remotely by the network operator. This opens up a pathway for attackers, which compromise and capture wireless nodes and launch a variety of attacks that impair the functioning of the system. The proposed system aims to localize and cluster these nodes together, according to their position, wherein the cluster head acts as an Intrusion Detection system by monitoring node behavior such as packet transmission. This information is used to identify the attacked nodes in the wireless sensor network (Chen et al., 2016).
In this paper, we compute the perfect secrecy capacity of the multiple antennas MIMO broadcast channel, where the number of antennas is arbitrary for both the transmitter and the two receivers. Our technique involves a careful study of a Sato-like upper bound via the solution of a certain algebraic Riccati equation (Oggier et al., 2011). Compared to conventional cryptography that works to ensure all involved entities to load proper and authenticated cryptographic information, PHY-security technologies perform security functions without considering about how those security protocols are executed (Liu et al., 2016). In other words, it does not require implementing any extra security schemes or algorithms on other layers above the physical layer. This survey introduces the fundamental theories of PHY-security, covering confidentiality and authentication, and provides an overview on the state-ofthe- art works on PHY-security technologies that can provide secure communications in wireless systems, along with the discussions on challenges and their proposed solutions. Furthermore, at the end of this paper, the open issues are identified as our future research directions.
Wireless spoofing attacks are easy to work with and play an important role in the performance of a wireless sensor network. Even if a node's identity can be verified using cryptographic authentication, traditional security approaches are not always desirable due to their ground requirements. A difficult wireless sensor network is detected by spoofing attackers, a certain number of views attack it, and localize multiple adversaries, and remove them. The cluster approach is used to detect spoofing attacks and localize them. This approach has less accuracy on predicting attackers. The cluster head act, related to IDS, is thus necessary to monitor the behaviour of nodes in the cluster, for example packet transmission makes it possible to determine the misbehaving nodes of the wireless sensor network. The simulation result clearly shows that the proposed scheme detects the spoofing attackers in Wireless Sensor Network efficiently and robustly. In this, the clusters are formed dynamically and periodically. The identity based digital signature protocol is introduced in order to provide reliable data transmission for clusterbased wireless sensor networks. This paper includes the feasibility of the protocol with respect to security requirements and security analysis over several attacks and deals with orphan node problem. The calculations and simulations are provided to illustrate the efficiency of the proposed protocol. The results show that, the proposed protocol have better performance than the existing secure protocols for cluster-based wireless sensor networks, in terms of security overhead and energy consumption.
In our proposed system, the methods of detecting the attackers are as shown in Figure 1.

Figure 1. Architecture Diagram of Proposed System
Further the attackers have been detected using the GADE mechanism. After the attackers have been detected, we will be using the IDOL method for localizing these attackers. The major difference is that we use a fictious node or an intermediate node between the server and the other users.
Before the user's request is received by the server it has to pass through this dummy node or the intermediate node. This intermediate node serves 2 purposes.
There are three stages in the module;
There would be multiple data requests from the trusted as well as the attacker nodes to the server. Hence there would be huge traffic which would slow down the performance as the server would have to process all the requests from all the users.
In the present system the server is receiving request from User 1 and User 2 but receiving multiple requests from User 3 as well which thus creates traffic as shown in Figure 2.
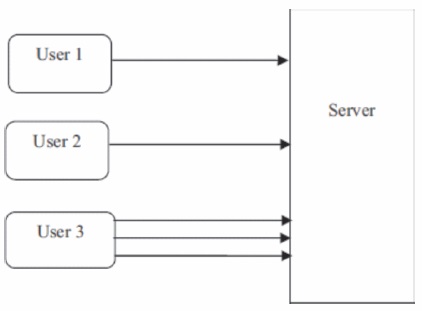
Figure 2. Present Server
In order to reduce the traffic as well as avoid the attack, we propose a method which uses an intermediate node. As seen in Figure 3, the intermediate node would lie between the server and the users and would act as a proxy i.e., the users will assume that they are sending requests directly to the server but in reality, the request is being sent to the intermediate node. It would find the number of data requests from various nodes and then send them accordingly to the server so that the server could respond to them immediately.
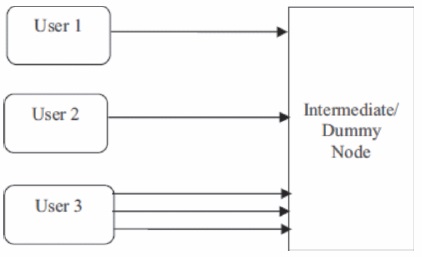
Figure 3. Intermediate Node
RSS is the signal strength of a received frame measured at the receiver's antenna and is interrelated to the transmission power, the distance between the transmitter and the receiver, and the radio location because of multipath and inclusion effects.
Further, the attacker from its victim, have more possibility in the variation of RSS pattern extensively, and thus easier to identify the spoofing attacks.
Under the spoofing attack, the victim and the attacker use the same ID to transmit data packets, and the RSS readings are measured for each individual node (i.e., spoofing node or victim node) as shown in Figure 4.
Figure 4. Detection Method
Our proposed method for preventing describes that once the attack is detected, the intermediate node may accept the data requests from the attacker, but not forward it further to the server, thus suppressing the attacker to have data access from the server, along with making the server independent from serving such requests.
Once the attacker node is found, IDPS will pass a request to AOMDV, and it will find an alternate path for the sender to send the message as seen in Figure 5.
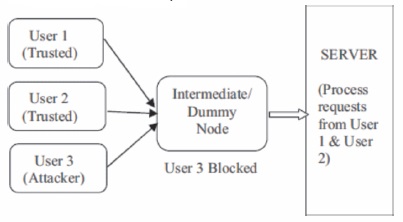
Figure 5. Preventing Spoofing Attack
INPUT: The location information from all the nodes and assign the centroid.
OUTPUT: Cluster the nodes.
Step 1: Assign each node to the group that has the closest centroid.
Step 2: Calculate the distance from the data point to each cluster.
Step 3: If the data point is close to its cluster, leave it where it is. If the data is not closest to its cluster, move it to its closest clusters.
Step 4: Repeat Step 2 and 3 until a complete pass through all the data points' results in no data point moving from one cluster to another.
Step 5: At this point the clusters are stable.
Step 6: At the end, collection of nodes are partitioned into K clusters and the data points are randomly assigned to the clusters.
INPUT: A topology in which ‘m’ number of malicious node is present in a set of ‘n’ number of sensor nodes.
OUTPUT: Set of clusters which are having IDS as a header is used to find malicious nodes. Set initial parameter of network.
Step 1: Create node = IDPS;
Set routing = AOMDV;
Step 2: If ((node in radio range) && (next hop! =Null))
{Capture load (all_node)
}
Step 3: Create normal_profile (rreq, rrep, tsend, trecv, tdrop)
{Time;
Tsend, trecv, tdrop, rrep, rreq
}
Threshold_parameter ()
Step 4: If ((load<=max_limit) && (new_profile<= max_threshold) && (new_profile>=min_threshold))
{No any attack;
} Else {
Attack in network;
Step 5: Find_attack_info ();
}
Else {
“Node out of range or destination unreachable”
}
Step 6: Find_attack_info ()
{
Step 7: Compare normal_profile into each trace value
Step 8: If (normal_profile! = new trace_value)
}
Check pkt_type;
Count unknown pkt_type; Arrival time; Sender_node; Receiver_node;
Step 9: Block_Sender_node(); //sender node as attacker
The centroid node sends signals to the neighbouring nodes in a particular distance and forms a cluster with those nodes as shown in Figure 6. The source node sends signals to the nearby nodes to find the shortest path to the destination as shown in Figure 7. The attacker node sends signals to the nodes pretending to be the shortest path to the destination as shown in Figure 8.
Figure 6. Clustering Nodes
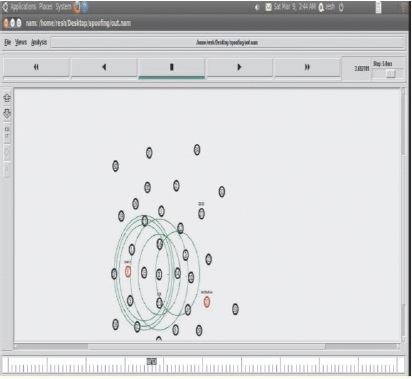
Figure 7. Source Finding Shortest Path to Destination
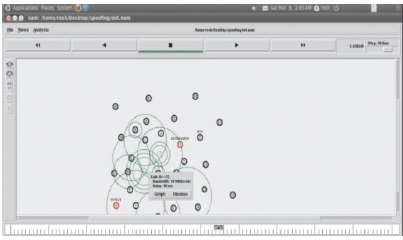
Figure 8. Signals from Malicious Nodes
The malicious node is caught by our IDPS by checking the RSS and a dummy node is assigned as the source node to confuse the malicious node so that it thinks the dummy node as the source node and keeps sending signals as shown in Figure 9.
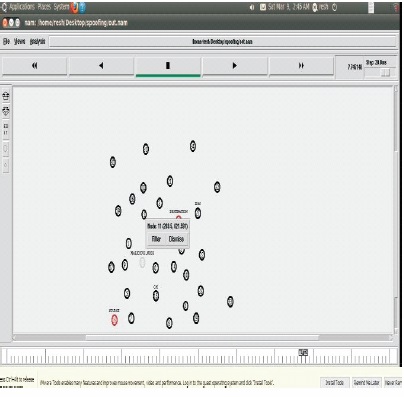
Figure 9. Malicious Node Caught by IDPS
The AOMDV routing protocol will update the shortest path from source to destination and send it to the original source so that the message gets transmitted in the new path assigned by AOMDV and the malicious node sending message to the dummy node is eliminated as shown in Figure 10.
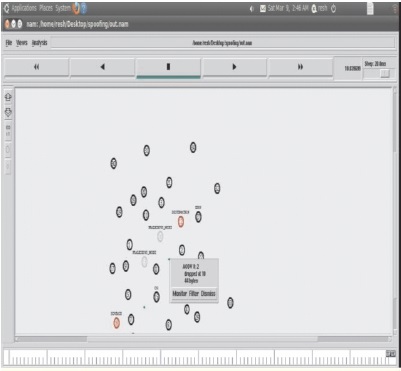
Figure 10. Eliminating Malicious Node
In this paper, the spoofing attack detection and localization scheme such as K-Means and Intrusion Detection System (IDS) are analysed in Wireless Sensor Network using NS2 simulator. The K-Means approach with Received Signal Strength (RSS) is performed to identify the spoofing attackers in wireless sensor network. The Intrusion Detection System (IDS) with AOMDV is proposed to detect the spoofing attack. The simulation results show that the performance of the IDS with AOMDV is better for efficient data transmission from sender to receiver by updating the next shortest path. When the packets are received by the attackers, its route will be diverted towards the Dummy node thus stopping their communication with the sender, as the dummy node will receive the requests from attackers but will discard it i.e., receive the requests but not processing it further and thus preventing the data from being stolen.
At the outset we would like to express our sincere gratitude to our beloved Chairman Dr. B. Babu Manoharan, M.A., M.B.A., Ph.D., St. Joseph's Institute of Technology, Chennai, Tamil Nadu, India, for his constant guidance and support.
We would like to express our thanks to our respected Managing Director, B. Jessie Priya, M.Com., and our Director B. Shashi Sekar, M.Sc., for their kind encouragement.
We express our sincere gratitude and whole hearted thanks to our Principal Dr. P. Ravichandran, M.Tech., Ph.D., for his encouragement to make this project a successful one.
We wish to express our sincere thanks and gratitude to our Head of the Department Dr. C. Gnana Kousalya, M.E., Ph.D., of Electronics and Communication Engineering for leading us towards the completion of this project.
We also wish to express our sincere thanks to our project guide M. Senthil Murugan M.E., (Ph.D.)., Supervisor & Assistant Professor, Department of Electronics and Communication Engineering for his guidance and assistance in solving the various intricacies involved in the project.
Finally, we thank our parents and friends who helped us in the successful completion of this project.