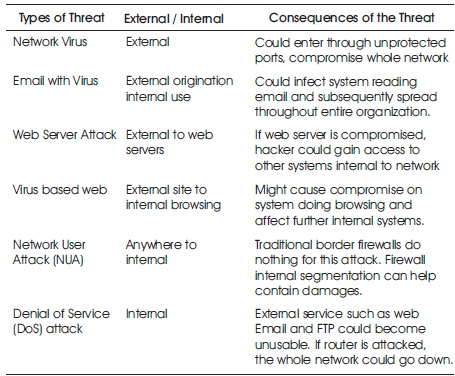
Table 1. Identify the Threats (Ali, Hossain, & Parvez, 2015)
In order to safeguard a University's networked assets, a network administrator must decide how to harden the network. To aid the decision-making process, network administrators may use network hardening suggestions. A critical drawback of currently available analyses is the lack of consideration for the network administrator on identified vulnerabilities, risk figure, risk priority level classification, and network security mechanism. Nessus and Nmap are network vulnerability scanners used for this research. Internal and external scan results were tabulated. The result shows that firewall constitute 81 on scale of 1-100 risk priority level classification of university Information and Technology Service (ITS) network with high risk security level and open email relay constitute two with low risk level. Thus, the research established a university secure network architecture model that contributed towards understanding risk priority level and also overcame shortcomings in choosing appropriate security measures.
In the modern education institutions, universities campus network has become a routine for work, teaching, scientific research, and sharing the important tool of all kinds of resources. In a network, all kinds of leak occur through computer, which brought a lot of concern. To prevent the network attack, it is important to set up and improve the campus network against illegal invasion (Wei, 2016).
University network and large network possesses enormous similarities, however each has its own challenges and problems securing the networks. This has always been an issue to Information Technology (IT) administrators and experts in security. A considerable number of accused persons transiting inside the university network, finger point at students of the institution. To create a secure network system for convenience in a learning environment is a challenging task. Currently, universities give attention to information technology, which improve student's research experience (Al Maskari, Saini, Raut, & Hadimani, 2011)
Security and network professionals have risen their primary concerns to network security vulnerabilities, where network vulnerability provide severe threats to the effectiveness and efficiency of an organization. (Awodele, Onuiri, & Okolie, 2012). It is essential for an network administrator to identify the system's security weakness before a hacker intrudes into organization network.
Information Technology (IT) security practices are critically significant for University System and its subsidiaries to protect large amounts of sensitive information stored on the Database. For instance, more than 70,500 students and 11,200 workforces access the internet in a university. Universities traditionally have a strong academic freedom culture that values free exchange of ideas and open access to information, which make them a target for computer hackers. Security problems in university ITS are happening more frequently through vulnerability web based Network computer applications and programs as well as via social engineering techniques. With nearly half of Ministries, Departments and Agencies (MDAs) web apps contain both informational and low security vulnerability risk level of 45.82% and 27.88%, respectively. A4-Insecure Direct Object Reference is the largest contributor of web security risk in MDA's websites in Nigeria (Idris, Majigi, Abdulhamid, Olalere, & Rambo, 2017).
A vulnerability is a hole or a weakness in an application and it consists of three fundamentals, namely: a system flaw or defenselessness, attacker’s capability to exploit the flaw, and attacker’s access to the flaw. A flaw can happen during coding, compiling, or implementation of a software known as a bug and allows an attacker to indirectly harm the stakeholders of the software. Stakeholders are entities that depend on the software as well as the software owner and users (Maistry, Ramkurrun, Cootignan, & Catherine, 2015). Most vulnerabilities, if not all, may allow a hacker to take advantage of the system by introducing an attack.
Nathan proposes a cyber vulnerability in facilities accommodating system’s critical infrastructure and general methodology for physical assessment. The methodology intended to scale multiple installations, thus establishing a baseline for prioritizing improvements and allocating resources.
A developed critical systems illustrate interconnection diagram and dependencies demonstrated. The ordering of system repair and timing, emergency responder, spare parts, key personnel, and when defining the degree of dependency system changes are considered (Timbs, 2013).
Risk management typically starts with risk assessment, a process used to discover, define, and comprehend risk (Hoo, 2000). An intended risk assessment “prioritise, identify and organizational operations risk estimate (i.e reputation, image, mission, and functions), Nation organizational assets, persons and the other organisation resulting from the use of information systems and operation” (Shanthamurthy, 2011; Stoneburner, Goguen, & Feringa, 2011). Divides risk assessment into three different phases. First, preparation phase includes assessment scope, constraints and purpose that are defined. Threat and vulnerability information sources are well-known. Finally, risk factors and risk models used to establish key terms are defined. Second, analysis phase that includes threats, vulnerabilities, likelihood, and outcomes are identified and analysed. A list of prioritized information security risks is produced which is used to make risk-related decisions concerning security controls. Third and final maintenance phase includes ongoing monitoring and updating of identified risks. Identification of threats are tabulated in Table 1.

Table 1. Identify the Threats (Ali, Hossain, & Parvez, 2015)
Campus network security are numerous, below are common types of threat on a network.
Attack classes might consist of exploitation by insider, passive monitoring of communications, close-in attacks, attacks through the service provider, and active network attacks. Networks offer attractive targets and information systems and full range of threat agents should be resistant to attack, from hackers to nation-states. System must recover rapidly to limit damage when attacks occur (Ali, Hossain, & Parvez, 2015). Figure 1 shows traditional campus network design.
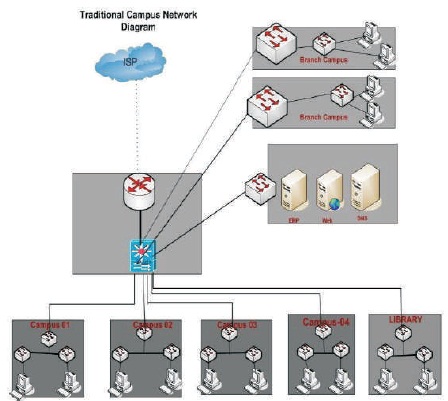
Figure 1. Traditional Campus Network Design (Ali et al., 2015)
Eight related vulnerability and risk assessment based research works were reviewed. Meta table reviews of related literatures are shown in Table 2.
The research is aimed at developing secure university network architecture based on identified vulnerabilities, risk priority level classification using Nessus and Nmap vulnerability scanners. In this section, all materials, methods, steps, and processes undertaking to achieve the paper's aim and objectives are listed and explained, including the software tools used, how to identify vulnerabilities, and techniques used for identification by the tool for the purpose of classification.
Network security scanners are used in order to successfully identify vulnerabilities for the purpose of classification and grouping. The study has collected security reports related to some key university network. Although, two or more universities cannot have the same architecture. In some universities, central IT group only provides high level service and bandwidth, where departments will have its own IT staff, budget, and department. Policy enforcement and policymaking raises a lot of challenges having decentralized IT group. Figure 2 illustrates a sample university network setup vulnerability points.
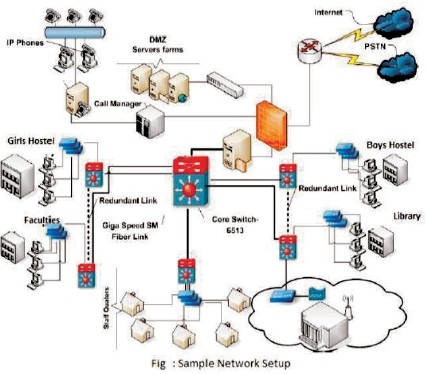
Figure 2. Sample University Network Setup
In Information Technology (IT), security today is uniquely ambitious and multifaceted concern fronting corporate institution. 99% of all attacks are as a result of security breaches and faulty misconfiguration, known vulnerabilities which cost institutions millions of Naira in financial losses each year, where a solution is not forthright. Security professional, application related vulnerabilities, and operating system are growingly mindful of the basic to cope possible risks and assess on the systems and network with a myriad of networks. This requires a more intelligent approach to fortifying the enterprise and effectiveness.
The research uses the Network Vulnerability Scanners given below:
According to Kak (2016), Nessus is an open-source venture and remote security scanner. Nessus typically runs on one mechanism to scan all the devices obtainable by a remote machine in order to determine whether the latter is protected against all known security exploits. Figure 3 shows Nessus login interface.
Figure 3. Login Interface for Nessus
To scan on Nessus environment: Open a web browser and connect user interface of the Nessus scanner and click on the Policies tab to edit an existing policy or create new policies, and select the credentials tab on the left. Select windows credentials from the menu at the top and dropdown.
Optional domain, account name, and password should be specified.
Click at the bottom of the window and the configuration will be completed and then click submit. The list of managed scan policies and the new scan policy are added together.
The main feature of Vulnerability Scanner Nessus includes (Singh, 2011):
Network Mapper is a licence free open source utility for network auditing security/ exploration. Nmap is also valuable for tasks like managing upgrade scheduled services, network inventory and service uptime, or monitoring host. Nmap official binary packages are obtainable for Windows, Mac OS X and Linux, and it runs on all main computer OSs (operating systems).
Common characteristics of these tools (Singh, 2011) are Flexibility, Powerful, Portable, and popular.
Some important Nmap features are: Port Detection, Host Discovery, Version detection, and OS Detection using Nmap.
Table 3 summarizes scan manifest of university ITS. The external and internal scans vulnerability are used as an instrument to collect data to evaluate the efficiency of recent security control measures in use at the system level of University's ITS network. However, in security assessment document, this data will be used as an evidence to backing recommendations found. The internal scan took place at the University ITS to determine all vulnerabilities.
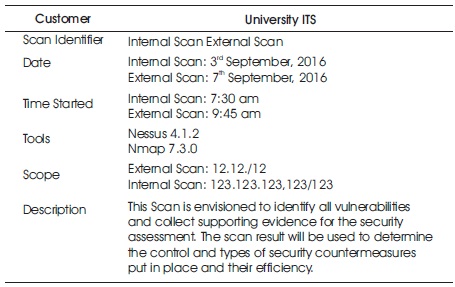
Table 3. University its Scan Manifest
The scanner was plugged into the switch that is situated inside ITS's network.
To get a detailed look at system configurations, is to sidestep countermeasures and external security controls. The 123.123.123/123 network for internal scan was selected by ITS staff. The security posture of the external scan is seen through the eyes of Internet user. The University ITS's network is to know what a hacker would see if he were trying to probe. The IP address 12.12.12/12 was chosen by ITS staff for external scan.
External and internal groups that may be affected by the scan are informed. The three phases invulnerability scan are: vulnerability assessment, manual checks (optional), and network discovery. The first and third phases call for the use of scanning tools. Discovering live hosts on the directed networks involved only network discovery phase. To determine hosts on the network, Nmap tool is used. Phase three output is inputted into phase one. External scan is conducted only on phase two.
Result findings generated from the external and internal scan using Nessus and Nmap are tabulated in Table 4.
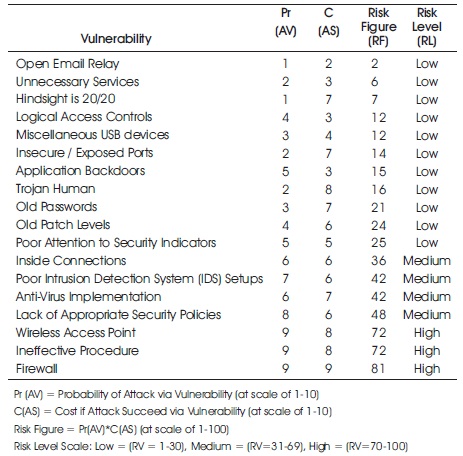
Table 4. Risk Priority Level Classification of the Network Vulnerability
Table 4 shows estimated product of probability of attack via vulnerability, cost if attack succeeds via such vulnerability at a scale of 1-10 and risk Figure.
Similarly, risk level was also calculated. Low Risk Value (RV) is between 1-30, medium is on interval of 31 -69, and high risk value is between 70-100. Table 5 shows risk level order of priority starting from most to least.
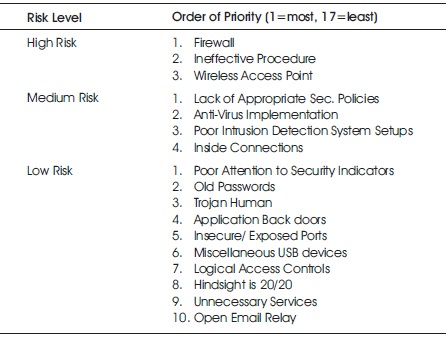
Table 5. Grouping of Risk Level Based on Identified Priority
Two way approaches to network vulnerability scan are External and Internal. To get a complete status picture of all machines, internal scanning should be carried through network from inside. The firewall and router external scanning is done outside the network from a host. The Network manager is able to see his network as the way an external aggressor might not. The external scans when performed comes with downside that only safeguards the administrator's network from an external aggressor. There is no protection from a vicious member of staff. Internal scans permit the security manager for providing remedy to security vulnerabilities and to provide additional information. The external IP galaxy in a university network can be separated into each subnet scanned for security weaknesses and subnet. Similarly, to check for application vulnerabilities and errors configuration that form critical parts of the network should be scanned internally. Toward ensuring that communication channel is not back through from the web tier to the Internal Network/database tier used by the administrator, internal scan is used.
The proposed countermeasures (security mechanism) based on identified vulnerabilities were outlined. Vulnerability scanners detect vulnerabilities and offer patches to identified vulnerabilities. For this reason, vulnerability scanners do not consider the interdependencies that may exist between vulnerabilities.
The selection of the appropriate set of security measures is nontrivial; however, removal of security flaws is performed by implementing one or more security measures.
Flow chart in Figure 4 shows the vulnerabilities, probability of attacks via vulnerability, cost if attacks succeed via vulnerability, and risk figure of the vulnerabilities.
Firewall, ineffective procedure, and wireless access point have a high risk level security and open email relay is the least low risk level security as in Figure 4.
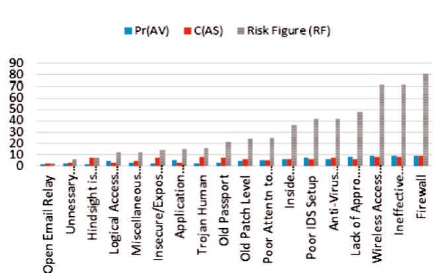
Figure 4. Risk Priority Figure Classification of the Network Vulnerability
The risk figure graph in Figure 5 shows that firewall have the highest risk level of 81 on 100 risk figure and open email relay with lowest risk of 2 on scale of 1 -100 risk figure. The linear line on the graph illustrates the order of priority (high, medium and low risk levels).
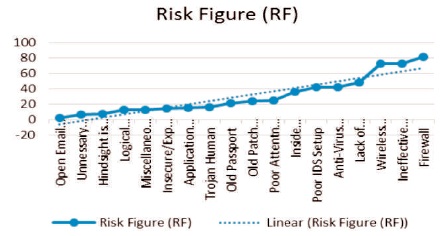
Figure 5. Risk Figure (RF) Graph
The ways to prevent or recover in good time from security glitches, below are itemized countermeasure steps for the secure university network based on identified vulnerabilities.
4.1.1 Wireless Access Point
Using RADIUS in WPA2 enterprise is intensely recommended with Access Point (AP) that is capable of implementing security measures and performing authentication. Frequent password change on regular basis and very strong mixed passwords should be used.
4.1.2 Miscellaneous USB Devices
If enforce asset control and policies are implemented around what devices should be connected and when should it be connected. And frequent policy reminders should follow up. For instance, US Department of Defense in 2008 developed policies banning removable media and USB from exiting/entering their environments.
4.1.3 Inside Connections
For access levels of any staff and authentication, an employee is required to have access to systems/file shares for their schedule duties only. Passwords are changed regularly. Any special requests should be directed always to appropriate team who can approve the call.
4.1.4 The Human Trojan
Employees should always be reminded of authorizing third parties by asking question to source of the person without assumptions on safeguarding network infrastructures.
4.1.5 Hindsight is 20/20
Alert and being mindful about this threat whenever working on sensitive material is the best safeguard, momentarily stopping what one is doing by observing the surroundings against hindsight.
4.1.6 Firewall
These are hardware devices or program that gives protection to the assets of a private network from other network users. To allow incoming traffic to pass, refused or blocked firewalls are responsible for that and they also work with proxy servers. They protect private networks from attackers or intruders.
4.1.7 Making Security Policies
Security policies are drafted documents which define the security measures that is expected to be implemented in an organization at a high level without it, where the organization cannot protect itself from likely lost revenue, lawsuits, basic security attacks, and bad publicity. The rules and objectives of these policies set behavior for users, administrators, and suggest the safety measures to be followed in a university. Three goals achieved by the policies are:
4.1.8 Intrusion Detection Systems (IDSs) / Prevention
Mechanisms used to monitor network traffic, prevent/ alerts them from attacking the network and checks for suspicious actions. For instances in some cases, the IPS/IDS react to anomalous or malicious traffic and will take action such as barring the IP address source or user from gaining access to the system. In this view, both network and host based intrusion/prevention systems are recommended for the university network.
4.1.9 Patch Management
The process to make sure that suitable patches are installed on a system is called Patch Management. It includes the following:
4.1.10 Logical Access Controls
Firewalls enforced Logical Access controls for networks, where Local Area Network (LAN) on dedicated computers restrict traffic to and from the network which are some features of communications protocol. Regrettably, access controls may also be vulnerable to attacks stated above, in general it may not protect against attacks by insiders such as staff with technical know-how.
4.1.11 To Prevent Password Cracking
4.1.12 Physical Security
These defines the apparatuses set in place to safeguard network critical assets against intended and unintended threats. To prevent pilfering and tampering of data, unauthorized access, natural disaster to data and trustworthiness of the data stored in the computer system, below are few mitigations:
Universities go all-out to create a suitable education environment via IT infrastructure. In a University network, there are many software applications, network devices, online systems, and various servers running. Knowing what is inside a network is a critical security requirement.
From Figures 3 and 6, the research identified vulnerabilities on the network using Nessus and Nmap, respectively. However, the research proposed a secured university network infrastructure in Figure 7 in accordance with best practice in the world to fix and provide countermeasure for feature vulnerabilities.

Figure 6. Basic Nmap Command (Saxena & Kumar, 2006)

Figure 7. University Secure Architecture
4.2 Mitigiting the Known Attacks
The proposed steps for mitigating the known attacks of a University ITS network are:
Measures for the secured University network can be shown in the collected form according to Figure 7. Numerous measures and discrete points are clearly stated.
The research proposed a secure university architecture design based on the required scalability, security, and work environment. To offer high assurance of suitable level of availability, confidentiality, and integrity of information, vulnerability assessments are significant through which universities can identify possible security threats.
Nessus and Nmap are two network vulnerability scanners used for discovering vulnerabilities. Internal and external scan results are tabulated. Conversely, we can deduce that firewall, ineffective procedure, and wireless access point are at high risk level security and open email relay is at the low risk level security. Firewall have the highest risk level of 81 on 100 risk figure and open email relay with lowest risk of 2 on scale of 1 - 100 risk figure.
The research has established a university secure network architecture model that contributed towards understanding risk priority level and also overcame shortcomings in choosing appropriate security measures.