Figure 1. Wireless Sensor Network Architecture
A data discovery and circulation protocol for Wireless Sensor Networks (WSNs) play a major role for updating the configuration parameters of the sensor nodes and a distributing commands to the Sensor nodes. Circulation protocols are capable of self organizing as the WSN are deployed in critical zones and rural areas where the manual reprogramming of nodes are complicated to configure. All existing data discovery and circulation protocols have two shortfalls one which is that the, existing protocols are based on the centralized manner, i.e. data items can only be circulated by the base station. Such approach is not sufficient for emergent multiuser Wireless Sensor Networks. Secondly, those existing protocols were designed with a lack of proper security and hence adversaries can easily launch attacks to attack the network suddenly. This paper proposes the more secured and distributed Data Discovery and Circulation protocol named DiDcip. This protocol allows the network owner to authorize the various network users with different privileges to circulate Data items to the Sensor node efficiently and directly. This protocol enables more security for the Data.
Wireless Sensor Networks are basically a collection of sensor nodes which collect the information and pass through a network monitoring its physical or environmental conditions. In modern communications, most of the applications setup Wireless Sensor Networks (WSN) in remote and host areas for efficient management and extreme working constraints. A WSN comprises sensor nodes which are used for analysis purpose.
These sensors are used to collect the information from the environment and pass it on to the base station. A base station provides a connection to internet where the collected data is processed, analyzed, and presented to useful applications. Thus by embedding the processing and communication within the physical world, WSN can be used as a real time platform to bridge real and virtual environment.
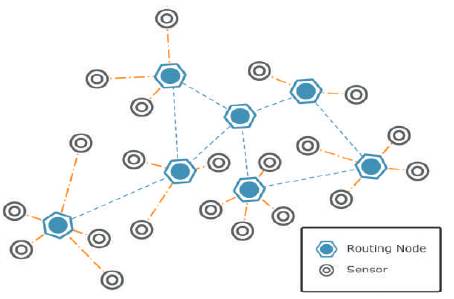
Sensor network consists of three main components, these are the sink, monitored events, and sensor nodes. Routing messages from moving node is more challenging since route stability is more important factor, in addition to energy and bandwidth. Figure 1 shows the Network Architecture of WSN.

Figure 1. Wireless Sensor Network Architecture
Wireless sensor nodes are resource constrained and have limited amount of energy. Therefore, designing protocols that conserve energy is an important area of research. Researchers have investigated architectures and topologies that allow energy efficient operation of WSNs.
Data dissemination in Wireless Sensor Networks is based on the concept of traditional communication system in which we have a sender and receiver. The scenario is basically a sender sending out some information and the receiver collects the information sent, processing it, and then sending some information back. While in data dissemination we are applying only half of this concept. Some information is sent out and received at the destination, but reply is not given back to the sender. The sender sends out the information, not only to single node, but to many same nodes.
Data Circulation can be achieved in two ways:
Data Discovery Circulation: To send small variables, queries, configuration parameters, and commands in a packet.
The data dissemination in a wireless medium is very vital and critical. As it is done using broadcasting system the sender node sends out information to many nodes in that network. A good dissemination protocol must be fast, reliable, secure, and energy efficient.
But dissemination brings in a lot of challenges. One major challenge is proper and complete dissemination of information to all sensor nodes in the network.
The above Figure 2 shows data dissemination in wireless communication using broadcast system in a centralized approach, where the base station collects information from sensor nodes within the network, which is distributed through server to end users.
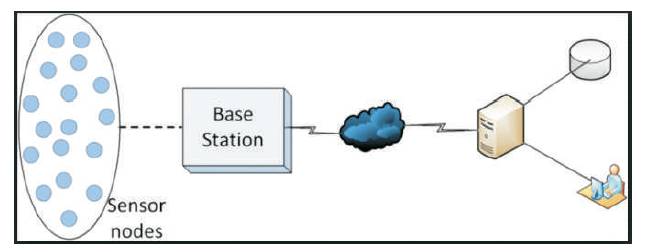
Figure 2. Data Dissemination in WSN
In Centralized approach the data transmission takes place from single base station to the network nodes. From Figure 3 Data Dissemination takes place only from base station.
Figure 3. Centralized Network
We have many protocols, such as Dip, Trickle, CodeDrip which follows the centralized approach which leads to bottleneck as number of node requests increase in a network, the network owner becomes cumbersome in distributing information within the nodes. There is no proper security for data transmission and if there is a crash of network owner or network base station there may be chance of lose of data.
In Distributed approach each node shares the data with other node. If the problem arises with one network the data is available with other network. This approach has more security when compared to other.
Figure 4 shows the distributed network that all the nodes share the data. Here we make use of distributed approach protocol, i.e., secured and distributed Data Discovery and Circulation protocol named DiDCip which allows the network owner to authorize the various network users with different privileges to circulate Data items to the Sensor node efficiently and directly. The protocol enables more security for the Data circulation using distributed system.
Figure 4. Distributed Network
Trickle is a self regulating algorithm which is used effectively in wide range of networks. Trickle, an algorithm for propagating and maintaining code updates in wireless sensor networks was proposed by Levis et al. (2004). Propagating code is costly; learning when to propagate code is even more complicated. Motes must periodically communicate to learn when there is a new code. To reduce energy costs, motes can transmit metadata to determine when code is needed and this is based on the concept called “Polite Gossip”.
Sensor Network Management System (SNMS) is designed to be simple and also has very minimal impact on the memory and network traffic. The system is mainly evaluated in light of issue which is derived from real deployment experiences.
Drip provides a transport layer interface to multiple channels in order to achieve the reliable message dissemination and also provides the standard message reception interface. Each component which wishes to use the Drip registers with a specific identifier represents the reliable dissemination channel. Messages which are received on that channel will be delivered directly to the component. Each node is responsible for caching the data extracted from the most recent message received on each channel to which it subscribes, and returning it in response to periodic rebroadcast requests. Drip avoids the redundant transmission and achieves greater efficiency.
DIP is a hybrid data detection and dissemination protocol. DIP stores a version number for each of the data item. DIP periodically broadcasts the summary messages which consists hashes of its keys and versions. Hash-tree based algorithm is used to detect if there is any update. If a node hears a hash that differs from its own then it knows that there exists a difference in hash value. On receiving a data message whose version number is newer than its own then DIP installs the new item. DIP improves the searching performance by combining hashes over ranges of the key space with a bloom filter. The overhead problem is reduced by using this protocol and also this protocol sends 20-60% fewer packets compared to previous protocols.
DHV is a code consistency maintenance protocol and name comes as (Difference detection, Horizontal search, and Vertical search). The main objective of DHV is to overcome the disadvantages with the previous dissemination protocols like DRIP and DIP by reducing the complexity.
DHV mainly includes two important phases like Detection phase and Identification phase. In detection phase, each node will broadcast a hash of all its versions in “summary ” message. In identification phase, the horizontal search and vertical search steps are used. In horizontal search, the node broadcasts a checksum of all versions called a “hsum” message. In vertical search, the node broadcasts a bit slice which starts with the least significant bit of all versions, called as a “vbit” message. After identifying this, the node broadcasts those key and version tuples in a “vector” message.
CodeDrip uses Network Coding technique to improve energy efficiency, reliability, and speed of dissemination. Network coding allows recovery of lost packets and then by combining the received packets hence dissemination is robust to packet losses. CodeDrip uses Network Coding to improve the efficiency of dissemination in Wireless Sensor Networks. Network Coding is a technique which combines packets in the network thereby increasing the throughput, decreasing the energy consumption and reducing the number of messages that are transmitted. Dropped packets can be recovered using retransmissions. By combining the packets using network coding, it is possible to recover the transmitted information without needing to retransmit all the lost packets to all the nodes.
Tiny ECC provides a number of optimization switches which can turn specific optimizations like ON or OFF based on the developers needs. Different combinations of the optimizations have different execution time and also resource consumptions thereby giving developers great flexibility in integrating Tiny ECC into sensor network application.
More importantly, all existing data discovery and dissemination protocols employ the centralized approach, data items can only be disseminated by the base station. Unfortunately, this approach suffers from the single point of failure as dissemination is impossible when the base station is not functioning or when the connection between the base station and a node is broken. In addition, the centralized approach is inefficient, nonscalable, and vulnerable to security attacks that can be launched anywhere along the communication path.
A distributed method has been proposed in order to overcome all the limitations of the centralized approach. In this approach the authors have developed a protocol called “DiDcip” that allows network owners to authorize multiple network users with different privileges to simultaneously and directly disseminate data items to the sensor nodes.
Figure 5 represents the architecture in four modules, such as initialization phase, user joining phase, preprocessing phase, and Packet verification phase.
Sensor nodes are randomly distributed in the sensing field. In this research work, Wireless Sensor Network has been used. In this network, the nodes are static and fixed. The sensor nodes sense the information and then send to the server. If the source node sends the packet, it will send through the intermediate node. The nodes are communicated only within the communication range. So, we have to find the node's communication range.
DiDcip Protocol allows the network owner to authorize multiple network users with different privileges to simultaneously and directly disseminate data items to the sensor nodes.
DiDcip Protocol mainly includes four phases in order to disseminate the data between the nodes among the Wireless Sensor Networks. The data discovery and dissemination of data from source to destination is performed by the authorized users only and it contains the following mechanisms:
The protocol consists of four phases, namely; system initialization phase, user joining phase, packet preprocessing phase, and packet verification phase, each of which are described in detail in the following sub - sections.
In the system initialization phase an Elliptic Curve Cryptography (ECC) algorithm is used in order to provide the communication between the network owner and users. The working of ECC algorithm is explained in the next section. In this phase the network owner creates the public key and private key and loads the public parameters on each node before network deployment is done.
When a user wants to join the network in order to obtain the dissemination privileges, the user joining phase is invoked. The privileges can be obtained by registering with the network owner. In this phase the user requests for the certificate from the network owner. After computing the public key and private key, the network owner generates the certificate and then sends back to the user.
When a user enters the network and has some information to disseminate over the network, first the user has to
construct the packet. This is done in packet preprocessing phase. After construction of packets only the user sends the data to the nodes. For this, data hash chain method has been used in which it contains hash values of all the chain of packets. In order to sign the hash value of the packet the Elliptic Curve Digital Signature Algorithm (ECDSA) is used. This cryptographic algorithm is used to provide the communication between the user and the sensor node. The working of ECDSA algorithm is explained in the next chapter.
When any sensor node receives the disseminated data from the user the sensor node has to first verify whether the received data is from the authorized user or not and whether the packet maintains data integrity. Also a node verifies each received packet. The following steps are performed.
In this section, the performance of simulation is evaluated. They use X-Graph for evaluating the performance. Four evaluation metrics were chosen: Packet reception ratio is the ratio between number of received packets and number of sending packets, Endto- End delay is the time taken to be data transmitted from source to destination. Using these evaluation metrics, the performance level can be represented.
In this work, two cryptographic techniques namely Elliptic Curve Cryptography (ECC) and Elliptic Curve Digital Signature Algorithm (ECDSA) are used. These cryptographic techniques are used in order to provide the communication between the network owner, user and sensor nodes. ECC Algorithm is used to provide the communication between the network owner and user. ECDSA Algorithm is used to provide the communication between the users and sensor nodes. By using these algorithms the data will be more secured and also less prone to attacks.
Elliptic Curve Cryptography (ECC) is a public key cryptography technique. In this public key cryptography technique each user or the device taking part in the communication consists of a pair of keys which are known as public key and private key. A set of operations are associated with the keys to perform the cryptographic technique. Only the particular user knows the private key, but the public key is distributed to all the users taking part in the communication. Some public key algorithm may require a set of predefined constants to be known by all the devices taking part in the communication. Domain parameters which are used in ECC can be considered as an example of such constants. Public key cryptography does not require any shared secret between the communicating parties like private key cryptography. But the performance of public key cryptography is much slower than the private key cryptography.
In general public key cryptography system uses the technique hard-to-solve problems as the basis of the algorithm. Nowadays the most commonly used algorithm for public-key cryptography is RSA which is mainly based on the prime factors of very large integers. While RSA can be successfully attacked, the mathematics of the algorithm has not been comprised, per se; instead, computational brute-force has broken the keys. ECC is based on the difficulty of solving the Elliptic Curve Discrete Logarithm Problem (ECDLP). Elliptic curve combines both the number theory and algebraic geometry. These curves can be defined over any field of numbers like real, integer, complex numbers, although we generally see them that they are used over finite fields for applications in cryptography.
An elliptic curve consists of the set of real numbers (x,y) that satisfies the following equation:
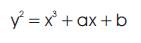
An elliptic curve E is defined by an equation of the form:
where a, b Î F and 4a +27b º 0 mod p. The set E(F ) p p consists of all points (x,y) Î F on the curve, together with a p special point O, called the point at infinity.
Let G = (x , y ) be a base point on E(F ) whose order is a G G p very large value N.
User A selects a random integer dÎ[1, N-1] as his private A key. Then, he can compute his public key Q from Q =d´
One main advantage of ECC is its key size which is small. A 160-bit key in ECC is considered to be as secured as 1024- bit key in RSA.
Signature algorithm is used for authenticating a device or a message sent by the device. For example consider two devices A and B. For authentication of a message which is sent by the device A, firstly the device A needs to sign the message using its private key. The device A sends the message and the signature to the device B. It is only by using the public key of device A the signature can be sent and verified by device A. Since the device B knows A's public key, it can verify whether the message is indeed sent by A or not. ECDSA is a variant of the Digital Signature Algorithm (DSA) which mainly operates on the elliptic curve groups. In order to send the signed message from A to B, both the parties should have to agree upon the Elliptic Curve domain parameters. The domain parameters are defined before. Sender 'A' have a key pair which consists of a private key dA which is randomly selected integer and the value is less than n, where n is the order of the curve taken from the elliptic curve domain parameters and a public key QA = dA * G where G is the generator point which is an elliptic curve domain parameter. An overview of ECDSA process is defined below.
This is the first part of ECDSA algorithm for signing a message m by sender A, using A's private key dA and the algorithm follows the following steps:
For B to authenticate A's signature, B must have A's public key QA.
After that, B follows these steps to verify the signature:
Finally X-Graphs are generated to evaluate Packet delivery rate, Packet loss rate, and throughput as shown in Figures 6, 7 and 8 respectively.
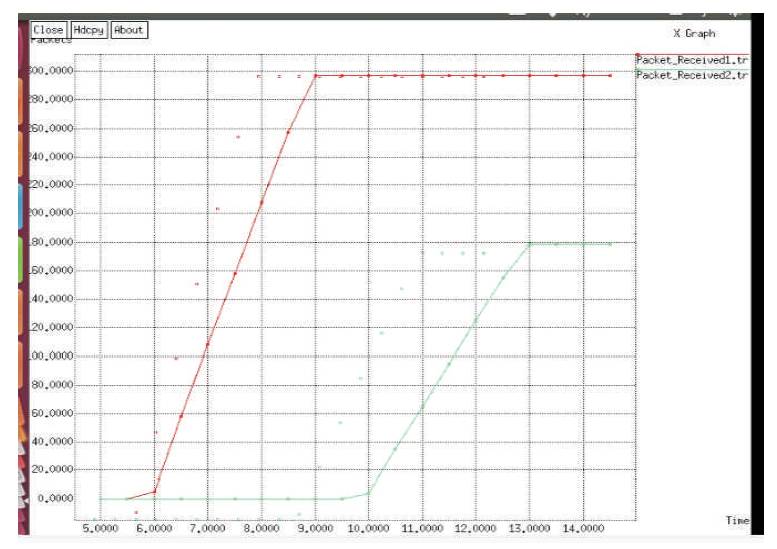
Figure 6. Packet Delivery Rate
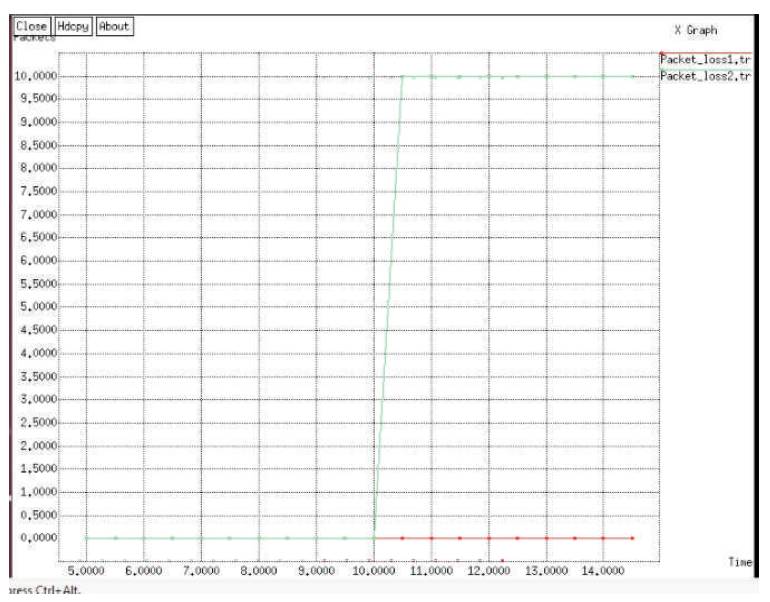
Figure 7. Packet Loss Rate
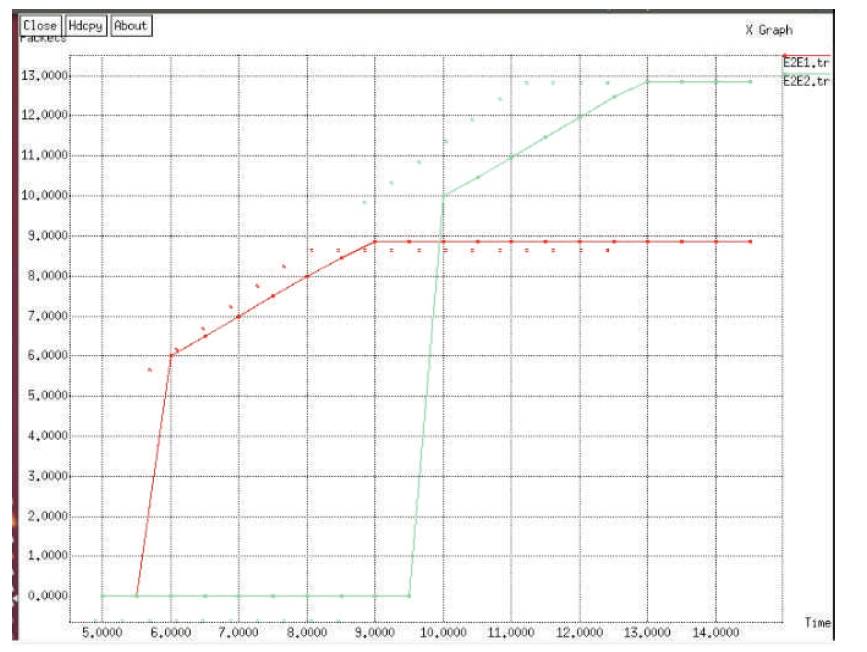
Figure 8. Throughput
In this research work, the authors have identified the security vulnerabilities in data discover y and dissemination when used in WSNs, which have not been addressed in previous researches. Also, none of those approaches support distributed operation. Therefore, a more secure and distributed data discovery and circulation protocol named DiDcip has been proposed. Besides analyzing the security of DiDcip, this paper has also reported the evaluation results of DiDcip in an experimental network of resource-limited sensor nodes, which shows that DiDcip is feasible in practice. They have also given a formal proof of the authenticity and integrity of the circulated data items in DiDcip.