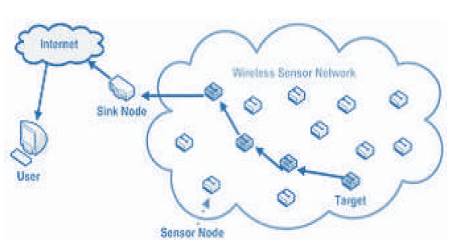
Figure 1. Overview for WSN [1]
Wireless Sensor Network is one of the vast areas of research for scholars. In this, energy consumption is a major problem and various protocols are applied till date to reduce it. The main purpose of this paper is to study some of the protocols such as direct transmission, MTE and LEACH. Nowadays, LEACH is a focused area to gain better results. So much research has already been done in this field, but still a lot more can be done to improve the overall performance. After analyzing all these, the authors have tried to decrease the power consumption of WSN using LEACH protocol. The experimental results show that there is an improvement in all parameter terms and more rounds have been energized when compared to basic LEACH. Simulation of the improved LEACH has been carried out on MATLAB and results have been verified and compared with parameters such as dead nodes, alive nodes, sending packets to Cluster Head or base station, etc.
Wireless Sensor Network (WSN) is generally considered as a standout amongst the most essential advances for the twenty-first century. In the previous decades, it has gotten enormous consideration from both the scholarly world and industry everywhere throughout the world [6]. A WSN (Figure 1) regularly comprises of countless small cost, lowpower, and multifunctional wireless sensor nodes, with detecting, wireless communications and calculation capacities. These sensor nodes perform communication over the short distance by means of a remote medium and work together to perform a typical task, for instance, environment observing, military reconnaissance, and modern procedure control.

Figure 1. Overview for WSN [1]
Wireless Sensor Networks are rapidly picking up an ubiquity because of the way that they are possibly minimal effort solutions for an assortment of formal objections of real world [1]. Their minimal cost gives way to send huge sensor arrays in an assortment of conditions fit for performing both military and regular citizen assignments. In any case, sensor organizes additional acquaint serious asset imperatives due to their absence of information and power. Both of these show the significant deterrents to the execution of customary PC security systems in a Wireless Sensor Network. The questionable correspondence channel and unattended operation makes the security barriers considerably harder. In reality, as pointed out in, wireless sensors regularly have the preparing qualities of machines that are decades old (or more), and the modern pattern is to lessen the expense of wireless sensors while keeping up comparative computing power. On account of that, numerous analysts have started to address the difficulties of amplifying the processing abilities and energy stores of wireless sensor nodes while likewise securing them against attackers. All parts of the remote sensor system are being inspected including secure and productive routing, data aggregation, group development and so on.
A wireless sensor network is a collection of nodes organized into a cooperative network [10]. Each node consists of processing capability (one or more microcontrollers, CPUs or DSP chips), may contain multiple types of memory (program, data and flash memories), have a RF transceiver (usually with a single Omni-directional antenna), have a power source (e.g., batteries and solar cells), and accommodate various sensors and actuators as shown in Figure 2.
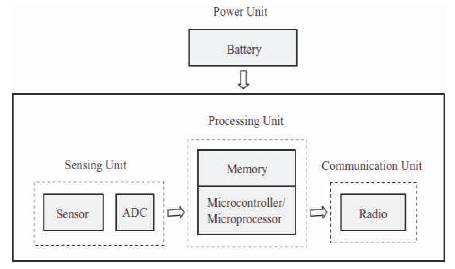
Figure 2. Structure of WSN [12]
The WSN comprised of "nodes" – from a couple to a few hundreds or even thousands, where every node is associated with one (or in some cases a few) sensor.
Each such sensor system node has normally a few sections: a radio handset with an inward receiving wire or association with an outside reception apparatus, a microcontroller, an electronic circuit for interfacing with the sensors and an energy source, as a rule a battery or an implanted type of energy harvesting.
Using a direct communication protocol, every sensor sends its information straight forwardly to the base station. In the event, that the base station is far from the nodes, direct communication will need a lot of transmission power from every node. This will rapidly deplete the battery of the nodes and decrease the network's lifetime. Be that as it may, the main reception in this protocol happen at the base station, so if either the base station is near the node, or the energy required to get information is vast, this might be an adequate (and conceivably ideal) technique for communication [8].
The second traditional methodology is minimum energy routing protocol. In this protocol, the nodes’ route information ordained eventually for the base station through middle nodes. Along these lines nodes go about as routers for other node's information in expansion to detecting the atmosphere. These protocols contrast in the way the routers are picked. Some of these protocols just consider the energy of the transmitter; ignore the energy dispersal of the reception in deciding the routers. Whereas, for this Minimum Transmission Energy (MTE) directing protocol, as opposed to only one (high-power) transmit of the information, every information message must experience n (low-power) transmits and n receptions. Based upon the relative expenses of the transmit enhancer and the radio gadgets, the aggregate energy used in the network may really be more noteworthy utilizing MTE routing than direct transmission to the base station [7].
In MTE routing, the nodes nearest to the base station will be utilized to route an extensive number of information messages to the base station. In this manner, these nodes will vanish rapidly, bringing about the energy required to get the remaining information to the base station to increment and more nodes to pass on. This will make a cascading impact that will abbreviate network lifetime. What's more, as nodes near the base station disappear, that region of nature is never again being checked [2,7].
A last traditional protocol for wireless systems is clustering, where nodes are sorted out into clusters that communicate with a nearby base station, and these neighborhood base stations transmit the information to the worldwide base station, where it is accessed by the end-client. This significantly lessens the distant nodes’ need to transmit their information, as normally the neighborhood base station is near to the nodes in the cluster. Thus, clustering seems, by all accounts, to be an energy efficient protocol [7].
LEACH is an energy-conserving routing protocol for wireless sensor network. It is a various leveled protocol in which most of the nodes are transmitted to the Cluster Heads, and the Cluster Heads total and compact the information and forward it to the base station. LEACH protocol is a benchmark Clustering Protocol, which forces upon Cluster Heads, the complete burden of accumulation and transfer of messages to base-station. It can develop the system life-cycle.
Figure 3 shows that the core idea of LEACH protocol is to divide the whole wireless sensor networks into several clusters. The Cluster Head node is randomly selected, the opportunity of each node to be selected as Cluster Head is equal, and the energy consumption of the whole network is averaged. Therefore, LEACH can prolong network life-cycle.
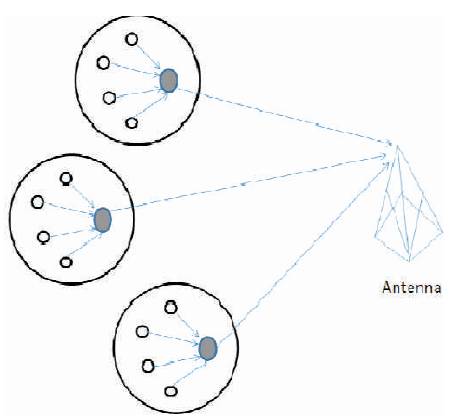
Figure 3. LEACH Clustering Model [3]
LEACH algorithm is patterned; it gives a concept of round. LEACH protocol keeps running with numerous rounds. Each round has two states [9], named as cluster setup state and steady state.
There are certain objectives that are to be followed [14].
This work proposed a two levels hierarchical approach as shown in Figure 4.
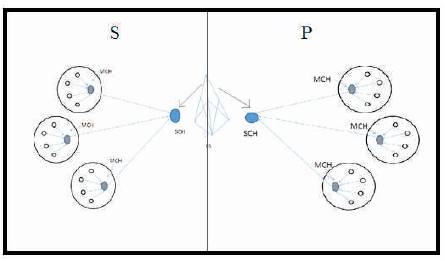
Figure 4. Cluster-based Hierarchical Model in MODLEACH [4]
In the first level, the division of the network is done into super clusters like the way LEACH does. The authors just changed the metric used for CH selection upon the creation of super clusters. In each super cluster, by selecting some Mini-Cluster Heads (MCH), they began the construction of mini clusters. The choice of this list of MCHs is based on two criteria; density and the residual energy of the candidate node. By using this way, the super clusters are divided into small clusters called mini cluster, and each mini cluster is controlled by MCH.
Table 1 shows the input parameter for the proposed work which are considered to achieve result.
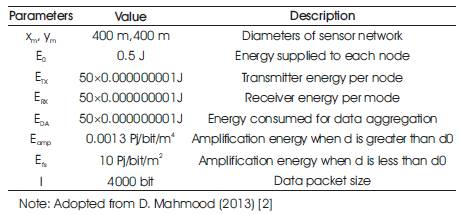
Table 1. Simulation Parameters used in the Proposed Work
The role of the MCH is to collect data from the members of its mini cluster and to retransmit this data to the SCH. The SCH sends all the received data to the sink. In fact, SCHs are the gateways between MCH and the sink.
The idea behind this system of clustering is to pass over the assumption of LEACH, it is assumed that any node in the network can communicate directly with the sink; however this is nearly impossible, especially when networks are deployed in large areas. MODLEACH manipulates two hops inter cluster communication. In fact, MCH does not communicate directly with the sink, but they use any node as a medium, the SCH, that is located in an area covered by the base station.
The parameters which is taken under consideration to propose the system and those are shown below in steps:
To select the Cluster Heads from all the given nodes, the steps which are given in Figure 5 are needed to follow [11].
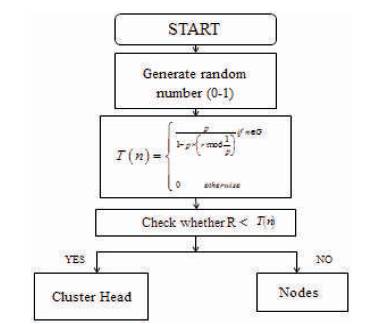
Figure 5. Selecting Cluster Head [5]
Out of all nodes, the Cluster Head is selected which has more energy compared to all nodes and must also be near to the base station. If both requirements are fulfilled, then the node is selected as Cluster Head [13].
In a single cluster, many Cluster Heads are selected using the same criteria which communicates with each as per the requirement.
Once the Cluster Head is selected, there is a need to select the sub base station as shown in Figure 6. In this process, all the Cluster Heads advertise them to become the Super Cluster Head.
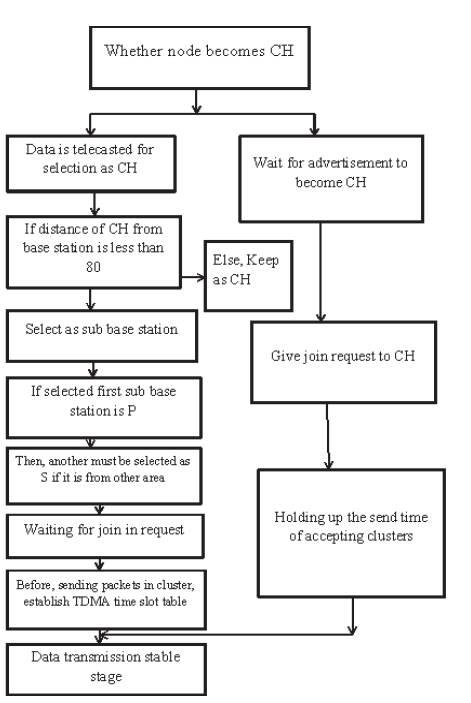
Figure 6. Selecting Sub Base Station [5]
The Cluster Head near to the base station and with more energy has more chances to be a Super Cluster Head.
Simulation is conducted by using MATLAB (R2015a) in a confidence interval to get the precise plots. The core idea of LEACH protocol is to divide the whole wireless sensor networks into several clusters. Initially, all nodes have same energy. The Cluster Head node is randomly selected, the opportunity of each node to be selected as the Cluster Head is equal, and the energy consumption of the whole network is averaged.
In experiment, the field dimension is taken as 400 m x 400 m (Figure 7).
Figure 7. 100 nodes Dispersed in Space
From all nodes, few ones have been selected as Cluster Heads, as Figure 8 shows CH for round 500 after simulation in MATLAB.
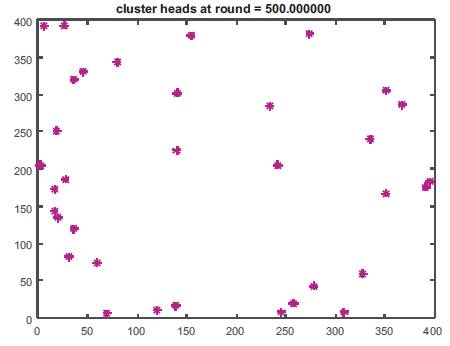
Figure 8. Cluster Heads at Round 500
Figures 9 and 10 show the graph for alive and dead nodes which are completely opposite to each other. In beginning, all nodes are alive and so there is no dead node, whereas at round 500, there were 64 alive nodes and 38 dead nodes. We are able to send 9900 packets to Cluster Head (Figure 11), and only 1100 packets to base station at round number 109 (Figure 12) as shown in Table 2.
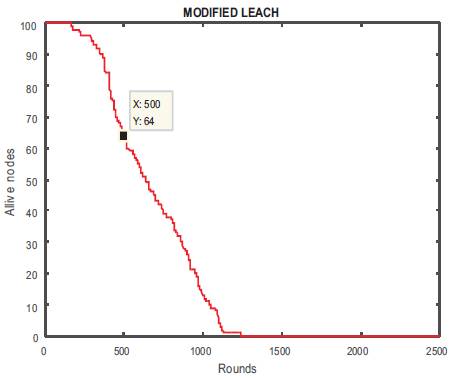
Figure 9. Alive Nodes
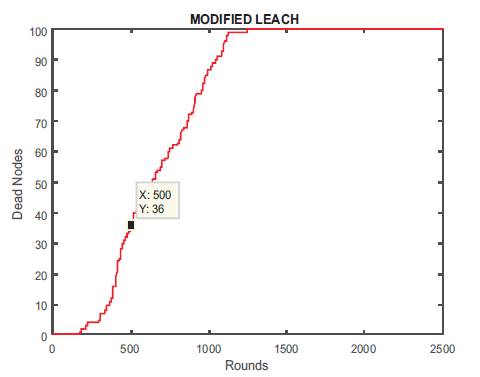
Figure 10. Dead Nodes
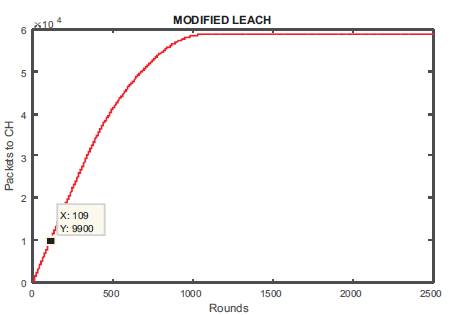
Figure 11. Packets to CH
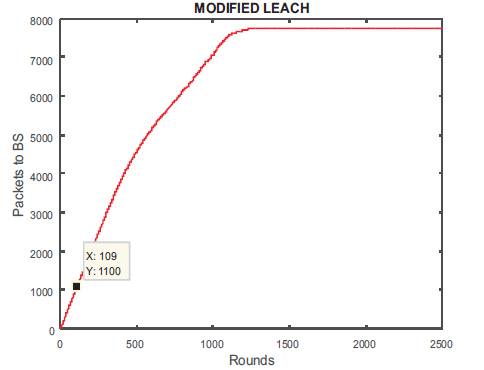
Figure 12. Packets to BS
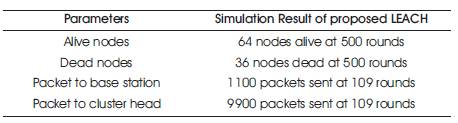
Table 2. Resultant Parameters
In WSN, energy consumption is a challenging issue. MODLEACH is proposed to reduce this problem. Simulation is done using MATLAB (R2015a) and showed better results compared to the existing LEACH. The parameters such as decreased energy consumption, increment in round for alive nodes, decrement in round for dead nodes show the improved results. As a result, lifetime of the system prolongs.
Wireless Sensor Network is an emerging area for research in which many scholars showed their interest and is still open for further improvement. In this work, improvement is done in energy consumption. As a continuation of this reaearch, future work could include the investigation of LEACH in its safe form [14].