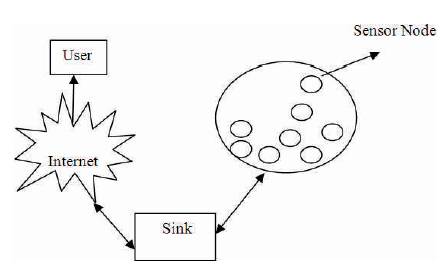
Figure 1. Wireless Sensor Network
Wireless Sensor Networks are composed of innumerable little accuse, low control devices with sense, local processing and wireless communication capabilities. Minimizing energy expenditure and maximizing the networks natural life are considerable issues in the devise of routing protocol for sensor networks. In this paper, the author has analyzed the competence of LEACH protocol in extending the subsistence for energy- constrained Wireless Sensor Networks. Based on LEACH protocol, a new text of LEACH protocol distance based leach protocol that is to be energy consumption protocol in Wireless Sensor Network is surveyed.
A sensor network is a collection of large numeral of sensor nodes and a sink. A Wireless Sensor Network (WSN) is a type of self-organizing and self-managing network, which is not complete of enduring the antenna nodes of the state of not having internet infrastructure [1]. The WSN is a construct of nodes from a few to numerous hundreds or even thousands, where each node is connected to one (or sometimes several) sensor. A Wireless Sensor Network consists of a large number of nodes multiplied over a explicit area where we want to look after at the changes going on there. A sensor node normally consists of sensor, actuators, memory, and a processor with better ability. All the sensor nodes are acceptable to communicate through a wireless direct. The wireless conduit is of radio frequencies, infrared or any other medium of course having no wired connection. These nodes are deployed randomly and it makes an ad-hoc network because they can communicate themselves [2]. If a node is unable to communicate others through direct link, it means the node is out of range. So the data can be sent to the other node by using the nodes in between them. This concept is referred as multi-hoping. All the sensor nodes work cooperatively to serve the requests [4].
In sensor network architecture, it is possible to deploy in extremely large number of sensor nodes or devices. Sensor network consists of a sensor field, where the sensor nodes are deployed in a physical environment, which is shown in Figure 1 having a low cost. A low-cost device can thus be expected to have fairly limited computational and communication capabilities, considering the fact that sensing capabilities are also to be included in the device [5]. Sensor nodes are deployed in many applications, where human intervention is not easy to maintain the sensor node. These type of sensor nodes where human intervention is not possible, operate on limited battery power. These batteries are not easily replaced. Sensor nodes have a limited power, so they have to be designed in such a way, that the sensor nodes use the power in an efficient way. Sensor nodes automatically shut down when they are not in use. For more specific applications like physical intrusion detection, sensor nodes have more advanced capabilities which are not in other nodes that are used in simple fields. Thus, the sensor devices may range from millimeter-sized devices fabricated on custom silicon to more general purpose cell-phone-sized devices with advanced capabilities. Figure 1 shows the simple sensor network architecture, where the sensor nodes are deployed with limited capabilities in a sensor field [6] . The sensor nodes are communicated to a powerful base station. Base station links the sensor nodes with internet and central manager for processing the sensed data which is given by sensor nodes. All the sensor nodes will not be able to communicate directly to the base station, so the sensor nodes go through several nodes, which are connected with each other. May be they are not in the range of a base station, due to limited communication range and so on. Base station or gateway may have other storage and processing capabilities that are useful for other applications. The base station is more powerful in sensor network [3].

Figure 1. Wireless Sensor Network
There are many applications of Wireless Sensor Networks that have gained considerable popularity due to their flexibility in solving problems in different application domains.
Now-a-days, sensor networks are also applied in environmental applications like habitat monitoring, agriculture research, fire detection and traffic control. By using sensor network in environmental area, there is no interruption to the environment, sensor networks are not strict as in battlefield [7]. Bush Fire Response is defined as environmental monitor and disaster response is a low cost distributed sensor network. An integrated network of sensors combining with the ground sensors monitoring local moisture levels, humidity, wind speed and direction, together with satellite imagery and longer term meteorological forecasting will enable the determination of fire risk levels in targeted regions as well as valuable information on probable fire direction. Such a network will provide valuable understanding of bush fire development and most importantly assist authorities in organizing a coordinated disaster response that will save lives and property by providing early warning for high risk areas. Information gathered by sensor networks could guide irrigation or harvesting to improve quality, providing vineyard owners and managers a better return on their investment [8].
Since most of the elemental knowledge of sensor networks is basic on the defense application at the beginning, especially two important programs, the DSN and the Sensor Information Technology (SenIT) form the Defense Advanced Research Project Agency (DARPA), sensor networks are applied very successfully in the military sensing [8]. Today, Wireless Sensor Networks are more important for militar y command, control, communications, computing, intelligence, surveillance, reconnaissance and targeting systems. WSN is also a part of military applications. In the battlefield context, rapid deployment, self-organization, fault tolerance security of the network should be required. The sensor devices or nodes should provide following services; Monitoring friendly forces, equipment and ammunition, Battlefield surveillance, Reconnaissance of opposing forces, Targeting, Battle damage assessment, Nuclear, biological and chemical attack detection reconnaissance.
Now Sensor networks are also used in health care areas too. The hospital sensor networks are used to monitor patient’s physiological data, to control the drug administration track and monitor patients and doctors within a hospital. In spring 2004, some hospitals in Taiwan even use RFID basic of above named applications to get the situation at first hand [7]. Long-term nursing home: this application focuses on nursing of old people. In the town farm cameras, pressure sensors, orientation sensors and sensors for the detection of muscle activity to construct a complex network are used. They support fall detection, unconsciousness detection, vital sign monitoring and dietary/exercise monitoring. These applications reduce the personnel cost and increases the reaction of emergence situation and in medical monitoring behavior monitoring [9].
Control the new construct process and control the conditions. For example monitoring and control the production process [7].
Routing protocols for Wireless Sensor Networks are responsible for maintaining the routes in the network. Many routing algorithms were developed for wireless networks. All major routing protocols are proposed for WSNs may be divided into five categories. The sample routing protocols are reviewed in each of the categories in preceding sub-sections [10].
Hierarchical routing in Wireless Sensor Networks are usually divided into several clusters, each cluster consists of a Cluster Head and a number of cluster membership, and multiple Cluster Heads form the high-level network. In the high-level network, Wireless Sensor Networks can be divided into clusters, which forms a higher level of network again until sink node of the highest level. The hierarchical approach breaks the network into clustered layers. Nodes are grouped into clusters with a Cluster Head that has the responsibility of routing from the cluster to other Cluster Heads or base stations. Data travels from lower clustered layer to the highest one [11].
In heterogeneity sensor network architecture, there are two types of sensors namely line-powered sensors which have no energy constraint, and the battery-powered sensors having limited lifetime, and hence should use their available energy efficiently by minimizing their potential of data communication and computation. There are different heterogeneity in WSNs to extend the network lifetime as IDSQ describes the problem of heterogeneous WSNs of maximizing the information gain and minimizing the detection latency and energy consumption for target localization and tracking through dynamic sensor querying and data routing. To improve the tracking accuracy and reducing detection latency, communication between sensors is necessary and consumes significant energy. In order to conserve power, only a subset of sensors need to be active when there are interesting events to report in some parts of the network. The choice of a subset of active sensors that have the most useful information is balanced by the communication cost needed between those sensors. Useful information can be sought based on predicting the space and time interesting events would take place. In IDSQ protocol, first step is to select a sensor as leader from the cluster of sensors and CHR describes the routing protocol uses two types of sensors to form a heterogeneous network with a single sink: a large number of low-end sensors, denoted by L-sensors, and a small number of powerful high-end sensors, denoted by Hsensors. Both types of sensors are static and aware of their locations using some location service. Moreover, those L and H-sensors are uniformly and randomly distributed in the sensor field. The CHR protocol partitions the heterogeneous network into groups of sensors (or clusters), each being composed of L-sensors and led by an H-sensor. Within a cluster, the L-sensors are in charge of sensing the underlying environment and forwarding data packets originated by other L-sensors toward their Cluster Head in a multihop fashion. The H-sensors, on the other hand, are responsible for data fusion within their own clusters and forwarding aggregated data packets originated from other Cluster Heads towards the sink in a multihop fashion using only Cluster Heads. While L-sensors use Short- range data transmission to their neighboring Hsensors within the same cluster, H-sensors perform longrange data communication to other neighboring Hsensors and the sink [12].
In location-based protocols, sensor nodes are addressed by means of their locations. Location information for sensor nodes is required for sensor networks by most of the routing protocols to calculate the distance between two particular nodes so that the energy consumption can be estimated. There are different location-based protocols to identify the address as GAF as an energy-aware routing protocol primarily proposed for MANETs, but can also be used for WSNs because it favors energy conservation. The design of GAF is motivated based on an energy model that considers energy consumption due to the reception and transmission of packets as well as idle (or listening) time when the radio of a sensor is on to detect the presence of incoming packets. GAF is based on the mechanism of turning off unnecessary sensors while keeping a constant level of routing fidelity (or uninterrupted connectivity between communicating sensors). In GAF, the sensor field is divided into grid squares and every sensor uses its location information, which can be provided by GPS or other location systems to associate itself with a particular grid in which it resides. This kind of association is exploited by GAF to identify the sensors that are equivalent from the perspective of packet forwarding. The GAF aims to maximize the network lifetime by reaching a state where each grid has only one active sensor based on sensor ranking rules. GEAR is an energyefficient routing protocol proposed for routing queries to target regions in a sensor field. In GEAR, the sensors are supposed to have localization hardware equipped, for example, a GPS unit or a localization system so that they know their current positions. Furthermore, the sensors are aware of their residual energy as well as the locations and residual energy of each of their neighbors. GEAR uses energy aware heuristics that are based on geographical information to select the sensors to route a packet toward its destination region. Then, GEAR uses a recursive geographic forwarding algorithm to disseminate the packet inside the target region [13].
Data-centric protocols differs from traditional addresscentric protocols in the manner that the data is sent from source sensors to the sink. In address-centric protocols, each source sensor has appropriate data responded by sending its data to the sink independently of all other sensors. However, in data-centric protocols, when the source sensors send their data to the sink, intermediate sensors can perform some form of aggregation on the data originating from multiple source sensors and send the aggregated data towards the sink. This process can result in energy savings because of less transmission required to send the data from the sources to the sink. There are different data-centric protocols such as SPIN protocol was designed to improve the classic flooding protocols and overcome such as implosion and overlap. The SPIN protocols are resource aware and resource adaptive. The sensors running the SPIN protocols are able to compute the energy consumption required to compute, send, and receive data over the network. Thus, they can make informed decisions for efficient use of their own resources. The SPIN protocols are based on two key mechanisms namely negotiation and resource adaptation. SPIN enables the sensors to negotiate with each other before any data dissemination can occur in order to avoid injecting non-useful and redundant information in the network. SPIN uses meta-data as the descriptors of the data that the sensors want to disseminate. The notion of meta-data avoids the occurrence of overlap given sensors can name the interesting portion of the data they want to get. It may be noted here that the size of the meta-data should definitely be less than that of the corresponding sensor data. Contrary to the flooding technique, each sensor is aware of its resource consumption with the help of its own resource manager that is probed by the application before any data processing or transmission [14].
In addition to minimizing energy consumption, it is also important to consider Quality of Service (QoS) requirements in terms of delay, reliability, and fault tolerance in routing in WSNs. QoS based routing protocols help find a balance between energy consumption and QoS requirements. Energy-aware QoS Routing Protocol describes QoS aware protocol for sensor networks, and real-time traffic is generated by imaging sensors. The proposed protocol extends the routing approach in and finds a least cost and energy efficient path that meets certain end-to-end delay during the connection. The link cost used is a function that captures the nodes' energy reserve, transmission energy, error rate and other communication parameters. In order to support both best effort and real-time traffic at the same time, a classbased queuing model is employed. The queuing model allows service sharing for real-time and non-real-time traffic. The protocol finds a list of least cost paths by using an extended version of Dijkastra's algorithm and picks a path from that list which meets the end-to-end delay requirement. The simulation results show that the proposed protocol consistently performs well with respect to QoS and energy metrics; however, it does not provide flexible adjusting of bandwidth sharing for different links [14].
A comprehensive review of the research work in the field of Wireless Sensor Networks (WSN) and its routing algorithms reported by various researchers are presented.
Tarun S., et al. [2015] elevates an energy consumption in the LEACH protocol. The LEACH protocol is an energy efficient protocol to reduce their energy consumption where different modes are applied on the sensor nodes. These modes are sleep, active and ready mode. These modes are applied on LEACH protocol and this enhancement is called as RFID protocol. The main problem exists in RFID protocol is of clock synchronization due which packet loss happened in the network which reduces network performance. To overcome this problem, the proposed algorithm is contention Avoidance Algorithm (RTS/CTS). In this technique, the Cluster Head node sends RTS packets containing a NONCE feed to all its cluster members. The member nodes would adjust their clocks according to the feed and revert back with CTS packets for synchronization of their clocks. The proposed technique has been implemented in Network Simulator. The graphical results show that the proposed technique performs better than LEACH, and RFID protocol in terms of throughput, energy and packet loss, delay and control overhead in the network [3].
Tarun S. et al. [2016] described the modern growth to fabricate an energy efficient Wireless Sensor Network, which is liberal a novel way to systematize WSN in applications like surveillance, industrial monitoring, traffic monitoring, habitat monitoring, cropping monitoring, crowd including, etc. The increase in use of these networks is making engineers to evolve novel and efficient ideas in this field. A group of research in data routing, data density and network aggregation have been proposed in recent years. The energy consumption is the main apprehension in the Wireless Sensor Network. There are many protocols in Wireless Sensor Network to diminish the energy consumption and to put in to the network lifetime. Among a range of types of techniques, clustering is the most efficient technique to diminish the energy expenditure of network. In this effort, LEACH protocol has been considered second-hand for clustering in which Cluster Heads are nominated on the basis of distance and energy. The LEACH protocol has been implemented in a simulated environment and their performance was analyzed graphically [22].
W. Su et al. [2002] described the concept of sensor networks with viable convergence of micro electrom echanical systems technology, wireless communications and digital electronics. First, the sensing tasks and the potential sensor network applications were explored, and reviewed factors influencing the design of sensor networks are provided. The flexibility, fault tolerance, high sensing fidelity, low-cost and rapid deployment characteristics of sensor networks create many new and exciting application areas for remote sensing.
Pant S., et al. [2010] described various data caching techniques in Wireless Sensor Networks. Because in WSN, sensor nodes are battery powered devices which consumes energy during data transmission, processing, etc. The critical task in WSN is to deal with optimizing power consumption by caching the data [16] . Caching reduces the overall network traffic and bandwidth [17] .
Sumathi R. and Srinivas, [2012] presented the state of research by summarizing the work on QoS based routing protocols. Simulation, the performance of the SAR, MMSPEED, MCMP, MCBR, and EQSR protocols are evaluated and analyzed with respect to different combinations of network and traffic control parameters [18] .
Norouzi and Zaim, [2009] proposed a new version of LEACH protocol called multihop-LEACH protocol. In LEACH, each CH directly communicates with BS no matter the distances between CH and BS. It will consume a lot of its energy if the distance is far. It selects an optimal path between the CH and the BS through other CHs and use these CHs as a relay station to transmit data over through them [19] .
Yassein M., et al. [2009] proposed a new version of LEACH protocol called V-LEACH which aims to reduce energy consumption within the wireless network. Both LEACH and V-LEACH were evaluated through extensive simulation using OMNET++ simulator, which shows that VLEACH performs better than LEACH protocol [20].
It is the first energy efficient routing protocol for hierarchical clustering [21] . LEACH (Low Energy Adaptive Clustering Protocol) form clusters and selects Cluster Heads randomly for each cluster. Non-cluster heads sense the data and transmit this data to Cluster Head, and then Cluster Head aggregates the data and forwards this data to sink. The principle of this protocol is that it assigns an overall energy consumption of the network uniformly to each node by selecting different nodes periodically as a Cluster Head. There are two phases of LEACH, that are Setup phase and Steady state phase. In Setup phase, clusters are formed and Cluster Heads are selected. In Steady state phase, data from non-cluster heads is transmitted to sink. The sensor nodes communicate with Cluster Heads with allotted time using TDMA. Cluster Heads are randomly selected in each round. LEACH operation is divided into several rounds. Each round begins with set-up phase, where the clusters are organized. LEACH set a threshold value T (n) and then sensor node I generates a random number between 0 and 1. If random number is < T(n), the node will become the Cluster Head for current round and the common nodes join the cluster and become cluster members.
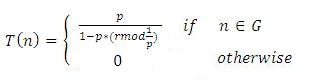
where p is probability of node to be selected as Cluster Head, r is the number of rounds passed, and G is selection of ordinary nodes. Once a node becomes Cluster Head, it never becomes a Cluster Head again. Only the node which have not become the Cluster Head and have high energy can become Cluster Head at r+1. When Cluster Head assigns time slots to the members using TDMA, then it is shifted to the steady state phase. After the shift in steady state phase, members sent data to Cluster Heads; Cluster Head process as the data and then sends data information to the base station. After this round, it turn to next round and begins reconstruction as a new round. Advantages of LEACH are that LEACH is completely distributed. LEACH does not require the control information from the base station and the nodes do not require knowledge of the global network in order for LEACH to operate. LEACH reduces communication energy by eight times as compared to direct transmission and minimum transmission energy routing. Disadvantages of LEACH are that the Cluster Heads are elected randomly. So the distribution of Cluster Heads cannot be ensured. In this protocol, the nodes with low energy have same priority as the nodes having high energy and nodes having low energy can become Cluster Heads, but that can't be used in large scale communication networks [20] .
During cluster formation of LEACH algorithm, some nodes have to select Cluster Heads that have longer distance to BS as compare to them. In this case, the Cluster Head sends the data directly to the base station due to which energy consumption is high [21] . These transmissions are called extra transmissions and it affects the network's lifetime by wasting node's energy as demonstrated in Figure 2.
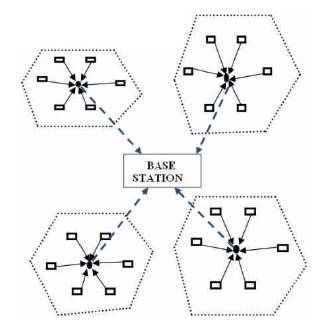
Figure 2. Distance based Leach Protocol
In this paper, the author has considered a well-known protocol for Wireless Sensor Networks called LEACH protocol, which is the initial and the most vital protocol in Wireless Sensor Networks which uses clusters based broadcasting techniques followed by an outline of LEACH protocol implementations, then we survey a new edition of LEACH protocol, the distance based LEACH protocol that is considered to be an energy consumption protocol in Wireless Sensor Network.