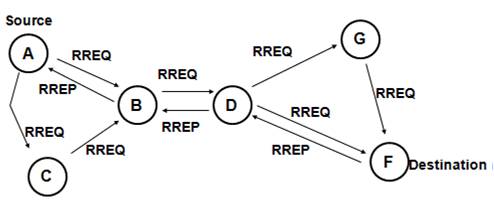
Figure 1. Message routing in AODV
In Ad hoc networks, nodes are trusted implicitly based on cooperation between the entities involved in routing operations. As wireless range of nodes are limited, the nodes cooperate with their neighbors in order to extend the entire size of the network. The explicit trust management allows entities to reason with and about trust and to take decisions regarding other entities. In the proposed work, trust is taken as a security solution for AODV protocol, which fits particularly with characteristics of ad hoc networks. Here implicit trust for the AODV protocol has been analyzed using trust specification language and how a trust based reasoning can allow each node to evaluate the behavior of the other nodes, is shown. During route discovery, a node with more trust is selected, based on a router based parameter called 'Trust value'. Route request from the source is accepted by a node only if its trust value is high. Otherwise, the route request is discarded. This approach forms a reliable route from source to destination. The prevention and counter measures have been proposed to resolve the inconsistency for the misbehaving nodes.
Mobile Ad-Hoc Networks are autonomous and selfconfiguring wireless systems. MANETs consists of mobile nodes that are free to move in and out of the network. These nodes can be a mobile phone, system, etc. Mobility affects the power indulgence of the nodes in a MANET. This is because of the high overhead incurred in Route Discovery and Route Maintenance in mobile nodes. Due to higher mobility of nodes, they form random topologies depending on their connectivity with each other in the network.
MANET is gradually emerging to be one of the most innovative and challenging areas of wireless networking. MANET's consists of Mobile Nodes (MNs) with autonomously self-organizing capabilities in arbitrary and temporary network topologies, communicating over wireless links. MANET's have self-configuration and self-maintenance capabilities in which network topology may change rapidly and unpredictably over time due to the mobility of nodes. All the network activity, including discovering the topology and message delivery is executed by the nodes by self/themselves. Research has resulted in a number of routing protocols [3] which can be classified as topology based routing protocols and position-based routing protocols.
The routing service in MANET can be attacked either by disrupting the message routing or by compromising the routing tables. In the former case, the main concern is to protect against misbehaving devices, and especially selfish devices (i.e. devices that do not properly forward messages). The traditional solution consists in forcing the devices to collaborate. One of the early works on collaboration is presented by Marti et al. [4] . The authors introduce the watchdog and path rater mechanisms. Basically, the watchdog mechanism is used by each node to monitor the behavior of its neighbors. Using the information of the watchdog, the device can locally compute a rating for each of its neighbors, and when this rating is below a given threshold, it uses the path rater mechanism to compute another path avoiding misbehaving devices. Thus, selfish devices are detected and not used anymore. Marti et al. do not allow each device to notify other devices when a malicious device is detected.
Today, a major part of the research work is on collaboration in MANET and has been inspired by this previous work, especially by using the watchdog mechanism to build a reputation system. For example, in [6] , the authors propose a collaboration system called CONFIDANT (Cooperation Of Nodes: Fairness In Dynamic Ad-hoc NeTworks) based on a reputation system. More specifically, each device uses a watchdog mechanism to monitor and report the message routing behavior of other devices. Given the observed and reported behavior, each device computes a reputation score for each device to detect misbehaving ones. The detection of misbehaving devices leads to their isolation. Thus, the devices are constrained to cooperate so as not to be isolated.
Later, the same authors extended their cooperation system in order to deal with devices that deliberately send false reputation scores [10] . Similarly, Michiardi et al. propose a cooperation enforcement mechanism, called CORE (Collaborative REputation) [7] . Basically, CORE uses a watchdog mechanism to allow each device to monitor its neighbors. Based on its own observation as well as the scores provided by other devices involved in the current operation, a device can compute a reputation score for each of its neighbors, and this score represents the degree of cooperation. When a selfish device is detected, it is gradually denied network services. Thus, a device cooperates, otherwise it can no longer use the MANET. However CORE allows to rehabilitate selfish devices if they behave correctly again.
A routing algorithm is proposed that adds a field in request packet, which stores the trust value indicating node trust on neighbor [7] . Based on the level of trust factor, the routing information will be transmitted, depending upon the highest trust value among all, that results not only in saving the node's power but also in terms of bandwidth. A trusted path irrespective of shortest or longest path is used communication in the network.
Likewise, trust based OLSR routing protocol [13] have been proposed. This uses trust classes to evaluate a trust value and then it would be used to identify the more reliable path.
AODV is one of the most popular MANET routing protocols [2] named as re-active or on-demand protocols. Upon arrival of data if no route exists, source broadcasts a route request to the destination. Each intermediate node hop automatically builds a reverse route to the source and also rebroadcasts the route request. The destination replies to the first route request and send a route reply in the direction it was received. The conventional AODV finds the shortest path between the source and destination. The objective is to generate “reliable routing” instead of minimum hop routing.
This protocol performs route discovery using control messages
When a source node needs a route to a destination node and there is no valid route in the routing table, the source node broadcasts a route request packet (RREQ) to the destination node. When each node receives the RREQ, it creates or updates a reverse route to the source node in the routing table. If it does not have a valid route to the destination node in the routing table, it re-broadcasts the RREQ. When the RREQ flooding from the source node arrives at the destination node, the destination node creates or updates the reverse route. And it uni-casts a route reply packet (RREP) which has incremented the sequence number to the reverse route. When each node receives the RREP, it creates or updates a forward route to the destination node and it forwards the RREP to the reverse route. When the RREP arrives at the source node along with the reverse route, it creates or updates the forward route, and starts communication.
For example, Figure 1 shows the process of the route discovery, in which the source node S broadcasts the RREQ and the destination node D uni-casts the RREP. If each node has the valid route to the destination node in the routing table when it receives the RREQ, it uni-casts the RREP to the source node instead of the destination node.

Figure 1. Message routing in AODV
On the other hand, when the node that detects the link break is far from the destination node, or when the local repair is unsuccessful, the node propagates a route error packet (RERR), which contains the addresses of the unreachable destination, towards the source node. When each intermediate node receives the RERR, the routes which have the unreachable destination node and have the next hop which is the propagation node of the RERR are made invalid, and it propagates the RERR again. When the source node receives the RERR, the route to the destination node is made invalid similarly, and it rediscovers the route again.
In this proposed work the authors have used trust specification language and Trust-AODV Mechanism to evaluate the trust value and to identify reliable path.
Trust [1] [5] is recognized as an important aspect for decision-making in distributed and auto organized applications. The notion of trust is fundamental for understanding the interactions between human beings, organizations, nations and others. The fact that a node A trusts a node B in some respect, informally, means that A believes that B will behave in a certain way and will perform some action under certain specific circumstances. The trust class and a language is used to express trust proposed by Yahalomet al. which together allow formalizing and clarifying trust aspects in communication protocols.
2.1.1 Trust Specification LanguageThe language proposed by Yahalom et al. has been used for expressing the clauses concerning trust in a networking protocol. The trust relation is taken into account if the possibility of realization of a protocol operation (the action) is evaluated by entity A on the basis of what it knows about entity B and the circumstances of this operation.
There are two types of trust relation
A trust relationship derived from direct interactions is termed as direct trust. In direct trust relation, trust is calculated based on what entity A nodes infer about an Entity B. Its does not depend on other entity information.
2.1.1.2 Indirect trust relationsA trust relationship or a potential trust relationship built from recommendations by a trusted node or a chain of trusted nodes, which create a trust path, is called indirect trust. In indirect trust relation, trust is calculated based on indirect observation, that is, getting the information about distant nodes from the nodes which are the neighbors of immediate neighbors.
2.1.2 Trust classesHere trust classes [8] defined in the context of the analysis of authentication protocols are used. An entity may trust another one for one of the following actions:
Then, the authors also use the classes proposed in specifically:
When a network entity establishes trust in other entities, it can predict the future behaviors of others and diagnose their security properties, this is defined as an implicit trust. Trust helps to make decisions to improve security and robustness, adaptation to risk leading to flexible security solutions, misbehavior detection and quantitative assessment of system-level security properties.
Trust relies on the fact that the trusted entities do not act maliciously. In ad hoc networks, nodes that have never met before can communicate with each other based on mutual trust relationships developed over a period of time. In this context, trust is subjective (different nodes may have different perceptions of the same node's trustworthiness), asymmetric (two nodes need not have equivalent mutual trust) and time dependent (it grows and decays over time according to experiences).
Trust value of each node is evaluated based on the various parameters like packets forwarded successfully and remaining energy of each node.
Based on the above parameters, trust level of each node can be of the following types:
a) Node i is a stranger (S) to neighbor node j If node i has never sent/ received messages to/from node j.
b) Node i is an acquaintance (A) to neighbor node j If node i has sent/received few messages from node j.
c) Node i is a friend (F) to neighbor node j
If node i has sent/received plenty of messages to/from node j, trust value is initially set to zero. It is incremented based on how many numbers of packets are successfully transmitted from node i to node j.
The number of packets forwarded is calculated as ratio of number of packets forwarded successfully by the neighbors to the total number of packets sent to that neighbor.
Every node in the MANET calculates its power consumption and finds the remaining energy periodically.
Each node may operate in any of the following modes [11] [12] .
The power consumed for transmitting a packet is given in Eq (1)
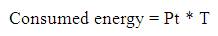
Where Pt is the transmitting power and T is transmission time.
The power consumed for receiving a packet is given by Eq (2)
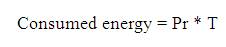
Where Pr is the reception power and T is the reception time. The value T can be calculated as
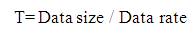
Hence, the remaining energy of each node can be calculated using Eq (1) or Eq(2)
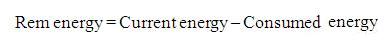
Initially every node has full battery capacity say 100% which is assigned to current energy. On each transmission or reception of a data packet the remaining energy is found using the Eq (4). If the remaining energy falls below 50%, that node will not act as a router to forward the packets.
Table 1 shows the trust levels and corresponding trust value that is used to determine the reliable route.
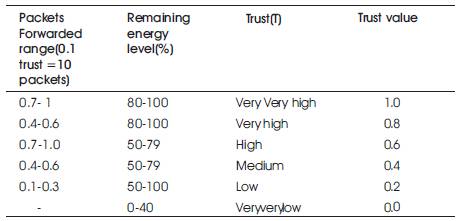
Table 1. Trust Value of Each Node
When source node wants to communicate with another node, if no routing information is available, it initiates path discovery by sending the route request that contains source id, broadcast id, destination id, hop count and trust values of each neighbor. On accepting the route request the neighbor node calculates its trust using Table 1 by checking its trust value it takes the following decision:
If the trust is very low (0.0) the node discards the route request else if the trust is an acceptable value, cumulative trust is found by adding the predecessor trust with its trust. If the node has already received the route request with same source address and same broad cast id and if the cumulative trust is less than the cumulative trust of current route request, the previous route request path is rejected and the current route request path is recorded. The route request is then forwarded to the intermediate node's neighbors which contains trust values of each neighbor and cumulative reliability. Each time when route request is forwarded from one node to another, hop count is incremented and it is also sent along with the route request.
2.4.2 Route ReplyWhen two or more route requests reach the destination from the same source, same broadcast id and in different path, it selects the most reliable path by finding the average trust. Average trust is computed as follows:
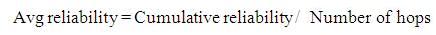
If average reliability of one path is greater than reply of another path, that path is selected and the route is sent by the destination in that path to the source. The source receives the new path and sends the packet in that reliable path and records the path for future use.
The attack [9] is generated to check the implicit trust in AODV routing protocol. In the resource consumption attack an attacker or a compromised node can attempt to consume battery life by requesting excessive route discovery, or by forwarding unnecessary packets to the victim node. With this more energy will be consumed and the node loses its energy and the energy levels are reduced. This is identified by decrease in the energy level of an compromised node. Furthermore the node cannot be able to transfer data to the destination. Each node needs minimum energy to transmit a packet to the destination node. To overcome an attack the new path is identified to transfer data to destination by using routing table information. Then the data is transmitted to the destination through the new path identified.
The performance of AODV is analyzed by taking four parameters into account. From the obtained results it is inferred that the performance of AODV is improved by implementing trust. The simulation tool used for analyzing the performance of AODV is Network Simulator 2 (NS2). The following are the parameters which are taken into account for comparison:
By comparing the performance of OLSR after implementing the trust as security solution it has been identified that throughput and packet delivery ratio is increased. The packet delay and total energy consumed have been reduced which makes a network transmit data successfully.
Throughput is the rate of successful message transmitted over a communication channel in KBps. The throughput for AODV is increased by 3.45% after implementing trust in the AODV protocol. Throughput variation is shown in Figure 2.
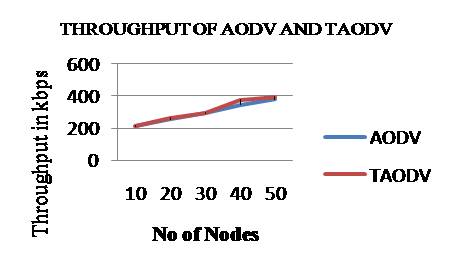
Figure 2. Nodes Vs Throughput
Packet delivery ratio is number of packets successfully received by destination nodes to the number of packets sent by source nodes. The Packet delivery ratio for AODV is increased by 4.12% after implementing trust in the AODV protocol. Packet delivery ratio variation is shown in Figure 3.
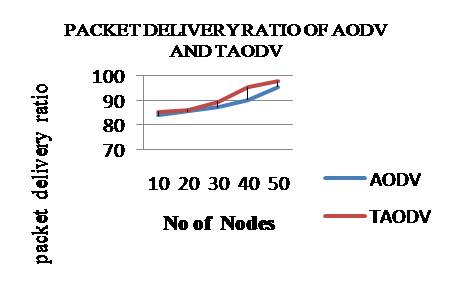
Figure 3. Nodes Vs Packet delivery ratio
Packet delay is the difference in end-to-end one-way delay between selected packets in a flow with any lost packets being ignored. The Packet delay for AODV is decreased by 3.26% after implementing trust in the AODV protocol. Packet delay variation is shown in Figure 4.
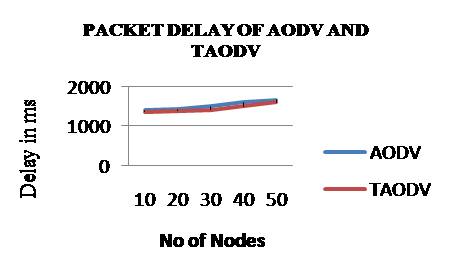
Figure 4. Nodes Vs Packet delay
Total energy is consumed to transmit all data packets to destination node. To achieve better energy efficiency, energy consumed should be as low as possible. The total energy consumed for AODV is decreased by 4.65% after implementing trust in the OLSR protocol. The variation of total energy consumed is shown in Figure 5.
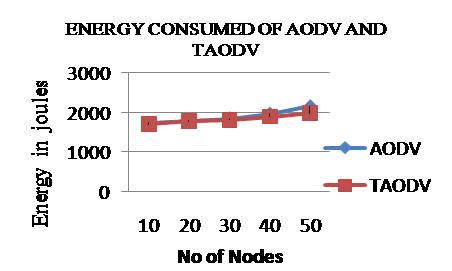
Figure 5. Nodes Vs Total energy consumed
Thus Implicit trust based analysis for securing the AODV routing protocol have been implemented and analyzed for better network performance. This analysis highlights the possible measures to make AODV more reliable and secure by exploiting the operations and information already existing in the protocol. The simulation results shows that the proposed approach decreases packet drops and improves reliability. The life time of the network and each node is increased by choosing more reliable node as a router to route the packets.
The trust value calculated based on the packet forwarded successfully and remaining energy level of a node enables the AODV to consume less energy both during transmission and idle mode and to forward the packet successfully. Further attack is generated to evaluate the trust and possible measures have been taken to encounter the attack and threat to security during the attack. By maintaining the energy level the throughput and energy efficiency were increased. Comparison of an AODV protocol has been analyzed with the trust based AODV protocol to show how the performance varies before and after the implementation. These results motivate to extend this approach in other routing protocols to analyze implicit trust.