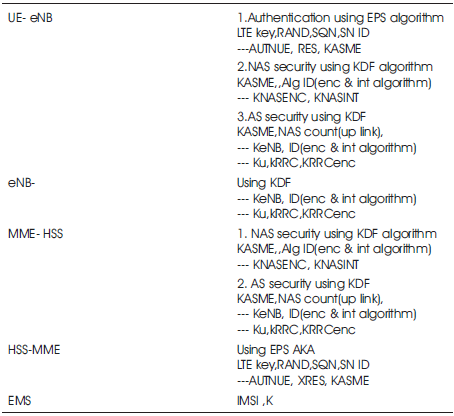
Table 1. Key Management in LTE network
The integration of LTE –WiMax wireless mobility aids in seamless mobility and cost effective mobile data services with the use of IP core and OFDMA air interface technology. The onslaught of 3G/4G and Wifi/WiMax interworking capabilities introduces a multitude of possibilities like security and Quality of Service (QoS). Each network has several similarities and has its own technology for authentication and link layer security. The interworking is performed on a data link layer using EAP authentication protocol by integrating key authentication procedure. In this paper, security key management for various protocols and its numerical analysis are presented across interworking domain. Interworking security is isolated in view of the fact that the authentication protocol has its limitation. It is desirable to avoid several round trips, delays in handover, computational overhead, hence a fast re-authentication procedure has been proposed in LTE-WiMax network.
Wireless network security is important for interworking concepts. In particular, LTE- WiMax [1] interworking increases the complexity of network entities as it need to negotiate the interworking solution. Thus, an efficient authentication protocol with dynamic key exchange provides seamless mobility and reduces handoff delay. The link layer mechanism was utilized to propose authentication and key procedure for internet application. Hence each technology uses its own authentication mechanism. IEEE 802.16 protocol uses public-key authentication algorithm, and X.509 digital certificate to perform key exchanges. LTE describe the authentication and key agreement protocol [2] for network security protection. LTE authentication process is in fact a combination of authentication key derivation and mobility management. But these processes are still separate in the internet. However, it has some shortcomings including bandwidth consumption and imperfect mutual authentication. These networks can support end to end security with PKMv2, AES and WPA/WPA2 and using a common set of authentication credentials. The performance of these networks can be improved particularly by minimizing the number of message exchanges between the entities.
IEEE 802.16m uses Extensible Authentication Protocol (EAP) for authenticating networks. WiMax security solutions sustains with the help of Extensible Authentication Protocol (EAP) to achieve mutual authentication. An uninterrupted authentication methodology is used in PKM-EAP which relies on the public key encryption. EAP can be actualized with EAP-TLS protocol (Extensible Authentication Protocol-Transport Layer Security) based on X.509 certificate. The authentication procedure [4] during handoff is reduced and made faster. Mobility related security requirement should be fulfilled by using re-keying mechanism. Once the user has entered into a host network, it has to proceed in a similar way as the initial network authentication. The re-authentication of Mobile Stations (MS) key exchange is performed and the host network Base Station (BS) can acquire the user information from the serving BS. With this information, the basic transformation of public/ private key, integrity and encryption key establishment phase can be reduced for the new network entry.
Remaining of the paper is organized as follows. The section 1 of this paper describes LTE security and key management related to AKA mechanism and specifies the authentication procedure of WIMAX networks in Section 2. Section 3, 4 and 5 describe key management and message length of EAP-AKA' protocol, EAP-TLS protocol and EAP re-authentication (ERP) protocol. Section 6 presents the proposed authentication method and key management mechanism in terms of handoff cost and bandwidth consumption. The results and analysis are finally concluded in the last section.
LTE supports mobility between heterogeneous access systems such as radio access networks and supports access control (authentication, authorization), migration aspects and privacy. In addition, LTE[15] also provides many security enhancements like mutual authentication root key length (64 and128 bits), integrity protection and signaling data encryption with five layers of key hierarchy.
The security property of key management [14] is to separate the access network technologies, base stations, and user planes. The key parameters linked with the use of Orthogonal Frequency Division Multiplexing (OFDM) technique is subjected to the choice of bandwidth within LTE. Further, OFDM has two layers of security which minimizes the effect of negotiation security layer. The procedure of EPS AKA is shown in Table 1.

Table 1. Key Management in LTE network
The required bandwidth controls the number of carriers that in turn provide accommodation within the OFDM signal. Link layer has enhanced Hybrid Automatic Repeat-Request (HARQ) protocols, which extensively improve the reliability of wireless link. This layer has in turn has two layers of security, which minimizes the effects of negotiation security layer.
At the time of setting AS [16] security the initial KeNB-0 is derived from the KASME and the current NAS uplink COUNTS. The initial NH1 is also derived at the same time. For the initial NH1, NH changing count value (NCC) is initiated to 1 as the initial KeNB is assumed to have 0. When mobility management equipment (MME) [12] receives request for the initial access to the network from user equipment (UE), MME sends the authentication data request to AuC/HSS. Through eNB, the distribution of authentication data occurs from the UE to serving MME. An EPS Mobility management (EMM) sends an authentication request with authentication parameters (RAND, LTE Key, SQN, SN ID) to the UE. MME allocates KSIASME to uniquely identify the KASME which is stored in the serving MME and UE, where this process allows the KASME to be cached and during subsequent connections it is re-used without re-authentication. However, for a new authentication procedure a different KSIASME should be included.
The successful processing of all the authentication parameters occurs including the user response (RES), the UE returns with an authentication response to the MME. This is followed by the validation of the RES correctness through the MME. Further, as agreed upon by the MME and UE, the intermediate KASME is identified after the completion of EPS AKA successfully [22]. A key is derived with the root key which is further sent to access key distributer network without without returning to the authentication server in particular KeNB is used for deriving K RRCint, K RRcenc and K UPenc. The protection of NAS traffic, KNASint with integrity algorithm and KNASenc with encryption algorithm is used. Similarly, for the protection of UP traffic, KUPenc with an encryption algorithm, while for the protection of RRC traffic, RRCint with an integrity algorithm. Session key context (SKC) is created within the KD and this enables to each and every base station where it creates integrity protection and encryption key from it. The encrypted session key and base station identities are as follows:
SQN1-n = SEQ1-n || IND1-n.
Derived Authentication vectors [16] are based on IK.CK, AK, XRES, MAC and AUTN
AUTN = SQN * AK || AMF || MAC
key derivation function (KDF) = HMAC-SHA-256 (Key, S)
Following steps are required to calculate KASME.
To compute KeNB subsequent steps are essential.
WIMAX Authentication issues
Worldwide Interoperability for Microwave Access (WIMAX) from the IEEE 802.16 group [17] is a wireless broadband that provides point-to-point, point-to-multipoint, and multi-hop access. WiMax has an ability to operate both on FCC licensed (10 to 66GHz range) and unlicensed frequencies (2 to 11 GHz range). WiMax solution is capable of supporting Extensible Authentication Protocol (EAP) methods to achieve mutual authentication.
However, the authentication of Network relies on TLS (Transport Layer Security) and PKM-EAP (Extensible Authentication Protocol). User data encryption supports CCMP (uses AES) and Triple DES standard. For aiding fast handovers and preventing man-in-the-middle attacks simultaneously a three-way authentication handshake scheme is used to optimize the reauthentication mechanisms.
For confidentiality and integrity protection, WiMax client devices decides on the types of cryptographic algorithms [10] to be supported with their key length limitations and re-keying period (Table 2). However, there are several limitations of the WiMax. The secret keys need to be periodically replaced in accordance with an IT security policy in order to reduce the potential effect of a key negotiation. While, another challenge with WiMax technology is Key Management [3], (Table 3)that uses Traffic Encryption Key (TEK) where sequence numbers are used to create different messages. Every single Traffic Encryption Key (TEK) is identified by the protocol with a 2 bit sequence number, by enclosing the sequence number from 3 to 0 on every fourth re-key. Table 4 shows that Message key length of WIMAX security.
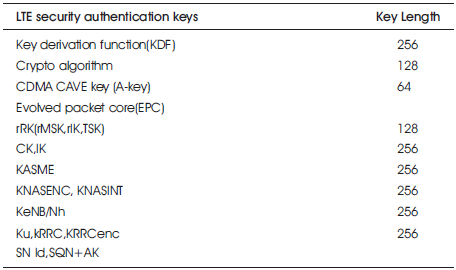
Table 2. Message key length of LTE security
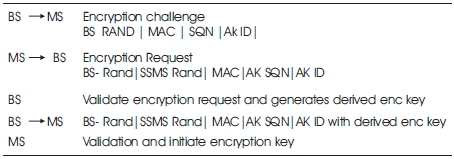
Table 3. Key Management in WIMAX network
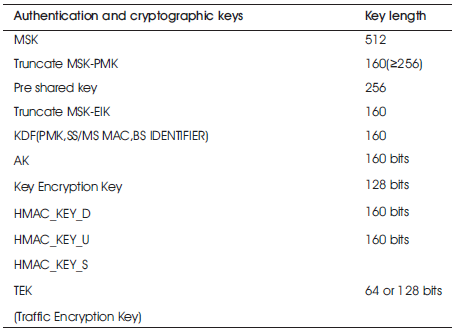
Table 4. Message key length of WIMAX security
Derived key for the hash function, Krrc-int/Krrc-enc/Kup-enc = HMAC-SHA-256 (Key, S)
Enhanced Extensible Authentication Protocol Improved Extensible Authentication Protocol (EAP) method is used for non-3GPP access to a 3GPP core network through WiMaX. Both the networks are the revision of EAP-AKA Extensible Authentication Protocol [8, 9, 16] (Table 5), where a new key derivation process unites the keys derived within the access network. This protocol [6] consent to its use in EAP in an interoperable manner and utilizes SHA-256 function. This further ensures that both the user and server know the name of the access network. It ropes key derivation function concession via the AT_KDF feature allowed for upcoming extensions.
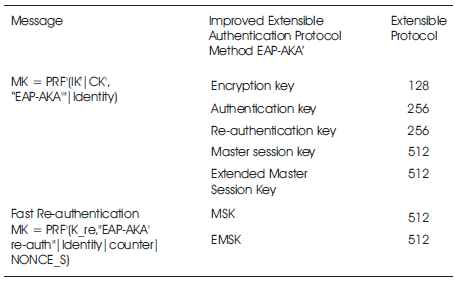
Table 5. Message key length of EAP-AKA’
EAP-TLS is a data link layer authentication mechanism. It uses Public Key Integrity (PKI) method to secure connections to a RADIUS server. The main impenetrability with EAP-TLS [18] is the requirement of individual certificates and the management through which client and the server verifies the certificates and exchanges the premaster secret (Table 6).
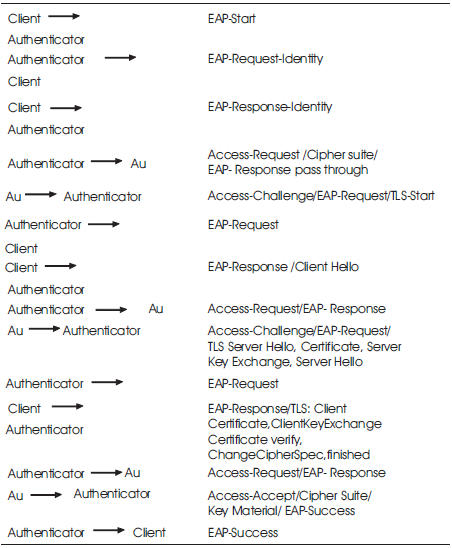
Table 6. Key Management in EAP-TLS Protocol
The session key computed from EAP-TLS is H (c, s, and p), where S and C are nonce while p is the pre-master secret. The client chooses p with an encryption to the AS's public key and sends back to the AS unless there is a valid certification of AS's. Since, p is encrypted with AS's public key, with the private key only the AS can decrypt p. The computation of the session key occurs using the hash of three values such as c, s, and p and the AS exchange.
TLS supports cipher suite negotiation, while with the implementation occurs with the encryption and hashing methods along with key exchange (DHE-RSA, DHE-DSS), Encryption (DES, 3DES) and Hash function (SHA) (Table 7).
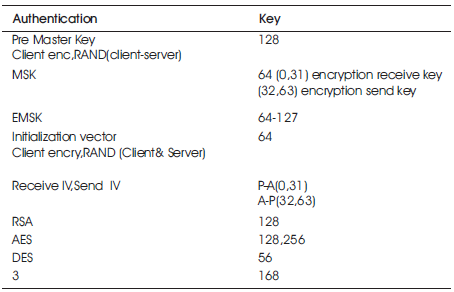
Table 7. Message key length of EAP-TLS protocol
The faster authentication is allowed by a wireless security protocol called as EAP Re-authentication Protocol (ERP) [RFC5296] [13] (Table 8). This is designed in such a way that no repeats are found with the complete EAP exchange with another authenticator that leads to mobile device re-authentication in a faster way. The server responsible for re-authentication may be present in the home or the local network from which the peer connection is established. Once the authentication becomes successful, the MSK are transported by the EAP server to the EAP authenticator where the MSK is used as an authentication key, key derivation key, or a key transport key by the EAP authenticator and the EAP peer establish Transient Session Keys (TSKs). TSK is used for the Per-packet access enforcement. At the time of the EAP exchange initial process, the EMSK is derived from the peer and the server, is used for derivation of a re-authentication Root Key (rRK) where DSRK by itself is derived from the EMSK. Both the peer and the ER server only have access to rRK than other entities where both employs the re-authentication [5,7] Integrity Key (rIK), derived from rRK, which provides proof of possession during the ERP exchange performance.
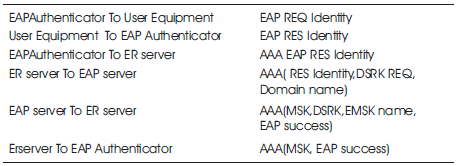
Table 8. EAP Re-authentication Procedure

Table 9. Message key length of ERP protocol
In turn, the rIK is available only to the server and peer while access is restricted to other entity. The server and peer make use of rRK and rIK obtained from EMSK when ER server source is the home domain. Also, in case of ER software, other than home domain, DS-rIK and DS-rRK is used corresponding to local domain. Identification of ER server is established by the real portion with key name NAI in ERP messages. In order to avoid peer shifts between authenticators, it is advisable not to implement round trips several times, computational overhead times and delay in handover times while employing a re-authentication is preferable. A Domain-Specific Root Key (DSRK) consequent from Extended Master Session Key (EMSK). For informing clients, Dynamic Host Configuration Protocol Version 6 (DHCPv6) is used through EAP Re-authentication Protocol ERP.
Local root key (DSRK) generated using the local domain name (LDN) is an important part of re-authentication while LDN is integrated with ERP via a lower layer mechanism, referred as ERP-local-domain-name (length is no more than 256 octet). If a DHCPv6 client requires the DHCPv6 server to provide the DHCPv6 ERP LDN option and is not aware of the ERP LDN.
The performance evaluation of the protocol is made by comparing the different protocols in terms of number of authentication, cryptographic keys (message length) and signaling bandwidth. User can prefer the authentication procedure which has to reduce the overall transit time of communication. Steps for accessing and configuring EAP-TLS and EAP-AKA' in LTE –WIMAX [7, 11] interworking are described in Figure 1.
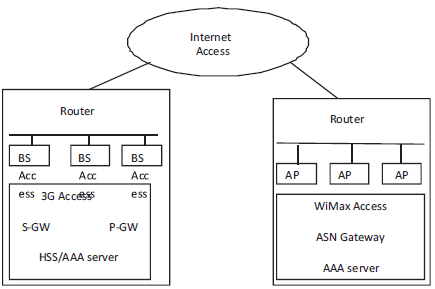
Figure 1. LTE-Wimax Interworking
The Multi Protocol Label Switching Tunnel, connects the gateways of both target (WiMax AP) and serving base station (LTE eNodeB) [21] in gateway relocation mechanism. The following service procurement, [20] every user is appointed with a home area and its authentication credentials at home AAA (H-AAA) are established. Before the service can be accessed H-AAA must authenticate the user and with the authentication procedure users are assigned temporary keys per session.
In wireless IP networks, the reduction in the radio signal strength occurs beyond the threshold with break in the flow when the users moves from the serving base station (LTEeNodeB) In order to continue the ongoing session [19], the authentication process entails eventual communication between a foreign AAA (F-AAA) server and the user's H-AAA with mutual trust, particularly, security associations must be maintained in visited networks to allow establishment of roaming agreements.
In LTE-WIMAX interworking, an authentication procedure is performed by combining re-authentication and new key derivation which together provide seamless handover.
Case 1: EAP-AKA' with EAP Re-authentication protocol ERP
Case 2: EAP-TLS with EAP Re-authentication protocol ERP
Re-authentication [7, 8] is necessary during the switchover of users from the registration areas and using mobility model, the traffic and bandwidth consumption of these movements are monitored. It is assumed that the number of Radio access network (E-UTRAN) in each core of LTE network is MRNC and while each radio network manages MBS base station and mobile nodes MMN and the area of base station BAS and ρ is the user density of the base station. If MMN= ρ* BAS, where the base station shape is assumed as 1.732/24, then the processing cost of the protocol is calculated as,
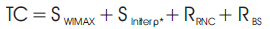
The interworking authentication key management total cost is calculated as,
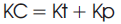
Where Kt is the transmission cost of message length; Kp is defined as the entity's function.
When the number of radio network coverage in each core LTE network is given by,
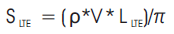
Therefore, the cost of per user can be calculated as follows,
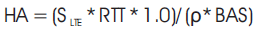
Where RTT is the round trip time between user equipment and connectivity service network.
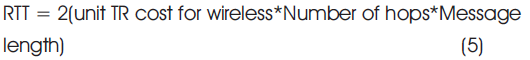
CML = Number of hops*Message length and 'L' define as the length of the key between mobile station.
Bandwidth width computation of all nodes in LTE(MME,e-NB,HSS,EMS) and Wimax(BS,MS) can be calculated with authentication key length .
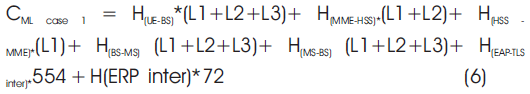
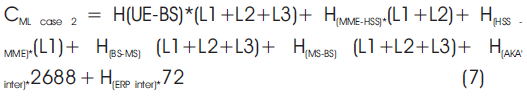
Number of hops between the domain and the authentication protocols are H(UE-BS) = 3, H(MME-HSS) = 4, H(WIMAX-inter) = 2, H(inter-LTE) = 3, H(BS-MS) = 3, H(AKA' inter) = 3, H(EAP-TLS inter) = 3, H(ERP inter) = 5.
In a LTE network, the handoff rate[19] is perceptive to the density of user. In addition, the data packets transmission cost is also subjected to the variance of user density in a LTE area. Figure 2 shows that the cost of case1 and case 2 with cryptographic key analysis. To eliminate the security problems, a novel authentication, key agreement and Re-authentication are proposed, as this method enhances the mutual authentication, avoid false BS attack and provide strong security.
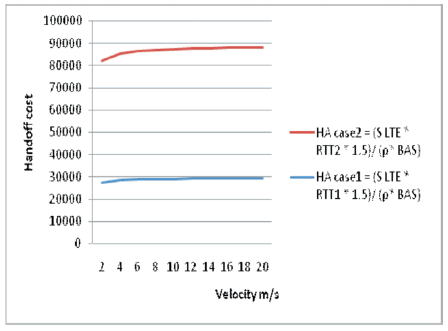
Figure 2. Hand off cost Vs Velocity(m/s) for Case1 and Case2
A concert holdup in the network occurs when the correlation of authentication with the signaling traffic occurs with number of concurrent authentication and abundant key mechanism. Consequently, the bandwidth used by the signaling traffic could be used as an index to compare the performances of case 1, case 2 and interworking network.
The calculation of each key size in case 1 and case 2 is shown in Table 10. The size of message length for case 1 can be calculated as 141879.04 bits per second and for Case 2, 210144 bits per second. The comparison activity is shown in Figure 3. However, the case1 service is pretty lesser than the case 2 (EAP-AKA') method.
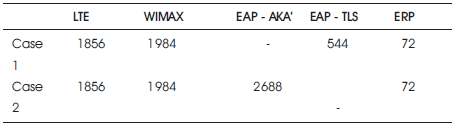
Table 10. Compares total number of authentication and cryptographic keys
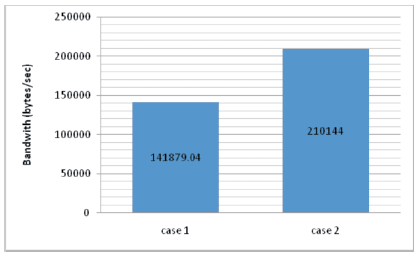
Figure 3. Bandwidth comparison
Increasing various types of applications and interworking networks create a different types of handover with security. In this paper, the proposed authentication procedure was analyzed in LTE-WIMAX networks based on authentication key management. The results showed that in terms of delay in authentication, EAP-AKA' fast re-authentication protocol outperformed EAP-TLS full re-authentication protocol. Furthermore, EAP-TLS, communication with the re-authentication protocol(EAP-ERP) reduces authentication delays and supports key management hierarchy. The network analysis and numerical results showed that the interworking scheme outperformed various authentication key management including signaling bandwidth and signaling costs.