Figure 1. Persuasive Technology
This paper introduces and presents the result of a systemic study of the persuasive cued click point graphical password scheme, including usability and security evaluation and implementation consideration. An important usability goal for the knowledge-based authentication system is to support user in selecting a better password thus increasing security by expanding the effective password space. They use persuasion to influence user choice in click based graphical password, encouraging users to select more random and hence more difficult to guess click-points.
The problems of knowledge-based authentication, typically text-based passwords, are well known. Users often create memorable passwords that are easy for attackers to guess, but strong system-assigned passwords are difficult for users to remember[3]. A password authentication system should encourage strong passwords while maintaining memorability. The authors propose that authentication schemes allow user choice while influencing users toward stronger passwords. In our system, the task of selecting weak passwords (which are easy for attackers to predict) is more tedious, discouraging users from making such choices. In effect, this approach makes choosing a more secure password the path of least resistance. Rather than increasing the burden on users, it is easier to follow the system's suggestions for a secure password—a feature lacking in most schemes. We applied this approach to create the first persuasive Click-based graphical password system through Persuasive Cued Click-Points (PCCP) [1,2,]. The paper is structured as follows: It covers related authentication schemes and Persuasive Technology in subsections of Introduction Section 1 covers the proposed model, design and security issues. Section 2 discusses the results and future enhancements. Finally, the paper is concluded in the last Section.
Graphical password systems are a type of knowledgebased authentication that attempts to leverage the human memor y for visual information [5]. A comprehensive review of graphical passwords is available in a cued-recall click-based graphical passwords (also known as locimetric) [7]. In such systems, users identify and target previously selected locations within one or more images. The images act as memory cues[8] to aid recall. Example systems include PassPoints[9] and Cued Click-Points[4]. In PassPoints, passwords consist of a sequence of five click-points on a given image. Users may select any pixels in the image as click-points for their password [10]. To log in, they repeat the sequence of clicks in the correct order, within a system-defined tolerance square of the original clickpoints. Attackers who gain knowledge of these hotspots through harvesting sample passwords can build attack dictionaries and more successfully guess PassPoints passwords [6].
Figure 1 shows the Persuasive Technology which was first articulated by Fogg [10] using technology to motivate and influence people to behave in a desired manner. An authentication system which applies Persuasive Technology should guide and encourage users to select strong passwords, but not impose system-generated passwords. To be effective, the users must not ignore the persuasive elements and the resulting passwords must be memorable. The path of least resistance for users is to select a stronger password (not comprised entirely of known hotspots or following a predictable pattern). The formation of hotspots across users is minimized since click-points are more randomly distributed.

Figure 1. Persuasive Technology
Previous work shows that hotspots and patterns reduce the security of click-based graphical passwords, as attackers can use skewed password distributions to predict and prioritize higher probability passwords for more successful guessing attacks. Visual attention research shows that different people are attracted to the same predictable areas on an image. This suggests that if users select their own click-based graphical passwords without guidance, hot spots will remain an issue. By adding a persuasive feature to CCP [4], PCCP [1] encourages users to select less predictable passwords, and makes it more difficult to select passwords where all five click-points are hot spots. Specifically, when users create a password, the images are slightly shaded except for a viewport. The viewport is positioned randomly, rather than specifically to avoid known hot spots, since such information might allow attackers to improve guesses and could lead to the formation of new hot spots. The viewport's size is intended to offer a variety of distinct points, but still cover only an acceptably small fraction of all possible points.
A password consists of five click points. During password creation, most of the image is dimmed except for a small view port area that is randomly positioned on the image. Users must select a click-point within the view port and if they are unable or unwilling to select a point in the current view port, then the view port guides users to select more random passwords that are likely to include hotspots.
Database design is the process of producing a detailed data model of a database which is shown in Figure 2. This logical data model contains all the needed logical and physical design choices and physical storage parameters needed to generate a design in a Data Definition Language, which can then be used to create a database. A fully attributed data model contains detailed attributes for each entity.
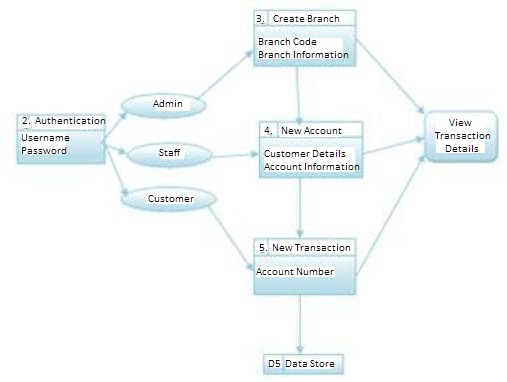
Figure 2. Database design for PCCP
The most basic guessing attack against PCCP is a brute force attack, which expected after half of the password space. However, skewed password distributions, could allow attackers to improve on this attack model. Our project examined the password distributions based on several characteristics. Password capture attacks occur when attackers directly obtain passwords by intercepting used rendered data, or by tricking users into revealing their passwords. Given that hotspots and click-point clustering are significantly less prominent for Pass Points, guessing attacks based on these characteristics are less likely to succeed. Sequence of images rather than a single image offers further reduction in the efficiency of guessing attacks. Capture attacks is susceptible to shoulder surfing and malware capturing user input during password entry. However, we expect social engineering and phishing to be more difficult than for other cuedrecall graphical password.
The viewport visible during password creation must be large enough to allow some degree of user choice as shown in Figure 3, but small enough to have its intended effect of distributing click points across the image. Physiologically, the human eye can observe only a small part of an image at a time. Selecting a click-point requires high acuity vision using the fovea, the area of the retina with a high density of photoreceptor cells. The size of the fovea limits foveal vision to an angle of approximately 1 degree within the direct line to the target of interest. At a normal viewing distance for a computer screen, say 60 cm, these results in sharp vision over an area of approximately 4 cm . We choose the size of the viewport to fall within this area of sharp vision. Where we had control over the size of the screen and the screen resolution, we chose a viewport of 75 X 75 pixels. However, for the webbased system, we used a slightly larger 100 X 100 pixel viewport since participants may be using a wide variety of system configurations. While the web-based prototype was designed primarily for standard size screens, it could be modified to accommodate smart phones or smaller screens. The system could determine the type of device (e.g., through browser settings data) and alter the size of the viewport dynamically.

Figure 3. PCCP Create Password interface. The viewport highlights part of the image
A possible strategy for increasing security is to enforce a minimum number of click-points, but allow users to choose the length of their password, similar to minimum text password lengths. The system would continue to show next images with each click, and users would determine at which point to stop clicking and press the login button. Although most users would likely choose the minimum number of click-points, those concerned with security and confident about memorability could select a longer password.
Figure 4 shows the interface for the two image sizes. The small and large image conditions shared images resized to different dimensions. The viewport was 75´75 pixels. We evaluated the usability of PCCP through several performance measures. We consider the following performance measures for memorability and usability[6]: login and recall success rates, times for password creation, login, and recall, and the effect of shuffling on success rates.
PCCP has a fair success rate to the other authentication schemes. PCCP password entry takes similar time to the other schemes in the experiment time, but the results indicate longer recall times for PCCP when recalling passwords beyond the initial session. Users who shuffled more had significantly higher success rates in the PCCP and the difference in success rates between high and low shufflers was very significant.
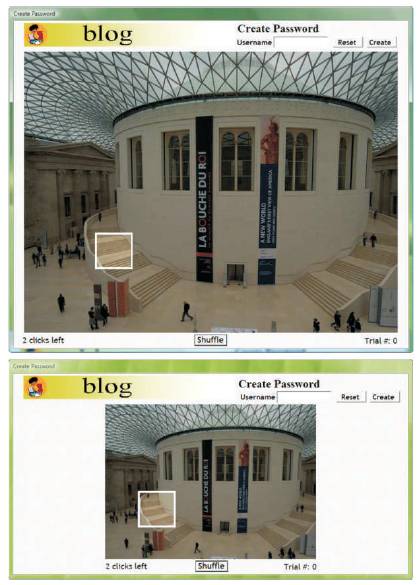
Figure 4. User interface for password creation for the small and large image sizes in PCCP
It is understood that hotspots and click-point clustering are significantly less prominent for PCCP results guessing attacks based on these characteristics which are less likely to succeed. For capturing attacks, PCCP is susceptible to shoulder-surfing and malware capturing user input during password entry. However, we expect social engineering and phishing to be more difficult than for other cued-recall graphical password schemes due to PCCPs multiple image options.
The authors present an integrated evaluation of the Persuasive Cued Click-Points graphical password scheme, including usability and security evaluations, and implementation considerations. An important usability goal for knowledge-based authentication systems is to support users in selecting passwords of higher security, in the sense of being from an expanded effective security space. We use persuasion to influence user choice in click-based graphical passwords, encouraging users to select more random, and hence more difficult-to-guess click-points. For further enhancement, user can upload multiple pictures and select the region through which we can set the password to secure the access of the application.