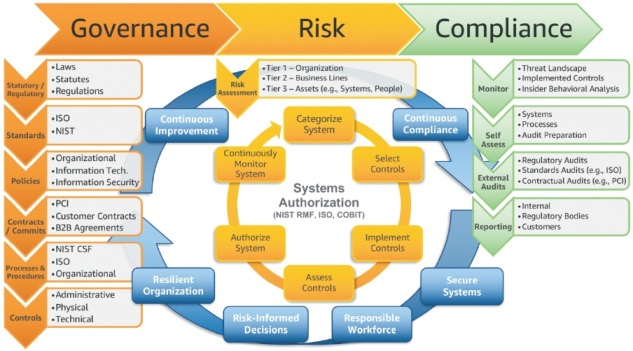
Figure 1. Symbiotic Relationship between Creating Governance, Risk and Compliance Frameworks (South, 2018)
It is important to view cyber security management from an integrated context that identifies how deliberated organizational strategies can be used to reinforce it in affiliated engagements. This study offers an insight as to how a highlyspecialized field can benefit both the specialized cybersecurity practitioners as well as the base level benefactors of cybersecurity. Ideally, cybersecurity management is integrated into the basic policies, systems, and procedures set up by an establishment with the desire to protect itself from cyberattacks. However, these interactions can be advanced into other aspects of organizational management and vice-versa. Consequently, this study uses a conceptual review of Governance, Risk and Compliance (GRC) frameworks and how they can make cyber-security system in an establishment efficient. The conceptual reviews consider the specific business continuity management planning framework that are built on a multi-cultural communication and management model, different pliability management models, as well as communication risk model systems, all designed to counter cyberattacks. The results of the study realize that cybersecurity management is a holistic process that cannot be demystified by a particular cyber-attack reaction but a conglomeration of efforts and ideas resulting from several cyber-attack reactions. Collective efforts can be built and reinforced through perpetual-oriented decisions/considerations of governance, risk and compliance frameworks.
The dynamism of the modern world has created a fastpaced environment for senders, receivers, and users of data. Each of the aforementioned groups of people seeks to apply specific cybersecurity management techniques that best suit their needs and deliverables (Limba et al., 2017). Consequently, a synergy ensues in their governance, risk, and compliance frameworks. A consensus exists with reference to cybersecurity experts on the need to create an interloping system that eases procedures geared at enhancing internal control, compliance, and system audits (Limba et al., 2017). Amalgamated systems of governance, risk, and compliance are crucial in maintaining transparent and efficient activities between the senders, receivers, and users of data (Salimath & Philip, 2020). However, a question exists on whether all cybersecurity management systems are relevantly appraised, as well as how organizations can apply governance, risk, and compliance standardized practices that support their cybersecurity management needs. If not properly tethered, governance, risk, and compliance frameworks can be viewed as bureaucratic red tapes for cybersecurity management problems.
Worldwide structured requirements exist, operating around cybersecurity management protocols. For instance, cybersecurity management modules offered by ISO (the International Organization for Standardization) and IEC (the International Electro-Technical Commission) seek to improve the cybersecurity approaches to be more proactive than reactive (Salimath & Philip, 2020). Organizations can liaise with such international bodies to form technical teams that assist with cybersecurity management. However, regardless of the tenacity employed, the governance, risk, and compliance frameworks must be considered on the basis of perpetuity and technical effectiveness (Zwilling et al., 2020) Given that cyber threats have become pervasive, cybersecurity system management has shifted to consider early detection and continued damage control (Limba et al. 2017). Ultimately, the subsequent desired effect is the reduced reactive incident response for organizations.
Cybersecurity management involves people, processes, and innovative technology. The process of engaging flexible and specific organizational principles and human behavior must be matched to scale. The symbiotic correlation between governance, risk, and compliance commences with governance, which determines the strategy and banisters for matching specific requirements that are specific to an organization's process, risk management links (Dar, 2016). Such cyber-based protocols link particular controls to the assessed risks (Chertoff & Simon, 2015). In additional, risk management offers the organization the information necessary to prioritize resources leading to more risk-informed decisions (Limba et al. 2017). Contrarily, compliance is derived from the constant and regulated adherence to the mentioned controls that are specific to the organization's governance requirements. A steady compliance follow-up ensures continuous monitoring and a closed feedback loop geared at realizing the organization's governance goals (Pham, 2019). The cybersecurity architecture, the engineering processes attached to it, as well as its technical operations, are dependent on the governance, risk, and compliance framework foundations. Figure 1 shows the symbiotic relationship between the aforementioned factors.

Figure 1. Symbiotic Relationship between Creating Governance, Risk and Compliance Frameworks (South, 2018)
The specific governance strategy (including the statutory regulations adhered to, the standards and policies upheld, the controls set in place as well as the cyber protocols/contracts, processes, and procedures) assumed by a business or an organization may vary. However, the need to uphold a specific compliance framework is necessary for different kinds of management practices. Some of the most prominent governance tools for governance management include corporate management techniques, cyber-safety oriented strategies, and risk assessment policy management modules. Synced strategic management determines the person or department responsible for different kinds of information in the organization (Pham, 2019). In addition, the governance structure determines the goals of the organization while ensuring the selected strategies ensure that the roles and responsibilities are aligned with the organization's goals (Chertoff & Simon, 2015). Hence, such activities ensure everyone why they must do something and how it benefits the organization.
Moreover, governance influence in cybersecurity issues include policy management. Policy management confers regulations that dictate whether cybersecurity processes, policies, and procedures are necessary for the people in each organizational jurisdiction to follow (Limba et al., 2017). Policy management helps create consistency across the organization so that everyone can produce consistent results. With regards to how it benefits cybersecurity management, policy management ensures specific goals are set for customized frameworks that best meet the goals (preventing data security breaches) (Chertoff & Simon, 2015). For example, the organization can direct focus on the risk portion of the framework that highlights and counter their substantial threats (Pham, 2019). In the case where the organization upholds its compliance standards, then specified attention is directed at performing constant audits and verifying that processes are consistently in line with its compliance standards.
Risk assessment involves monitoring and managing the different types of risk that an organization face daily. By identifying the most occurring risks that will have the invariably higher impacts, the organization can put down security measures that will have the most significant mitigating effect at the lowest cost realizable (Chertoff & Simon, 2015). Figure 2 shows the cost implications of data breaches across different countries. The United States has the highest cost implication of data breach surmounting to 7.9 million US dollars (Limba et al. 2017). Countries such as Canada and Germany come in second and third. The lost revenue is foregone opportunities for investments that would have been prevented under integrated cyber security management strategies.
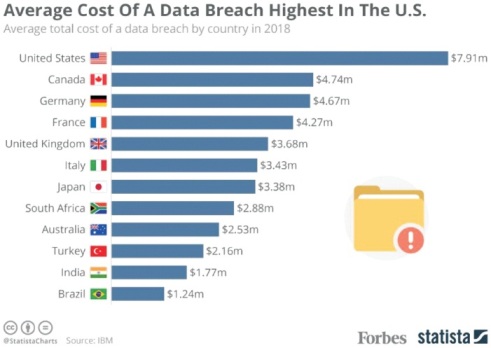
Figure 2. Cost Impact of Data Breaches in Sample Countries (Mc Carthy, 2018)
To continue, risk management ameliorates security personnel's endeavors in early detection of the risks that a particular organization faces on a routine. The organization notes the kinds of accidents or breaches that might impact the operations (Chertoff & Simon, 2015). Risk assessment demands that the organization maintains an updated inventory of the acquired assets and new processes and verifies whether they pose any threat to their operations (Dar, 2016). Risk assessment involvement in cybersecurity management takes on the risks with the significant and monitors them through their returns on investment based on their cybersecurity expenditure.
Various benefits are accruable from incorporating effective risk management techniques on cybersecurity management above the cost factor. Risk assessment helps with the classification of risks using the likelihood of occurrence as well as their scale of impact (Chertoff & Simon, 2015). Risk management begets sound decisionmaking that later on translates to the kinds of policies upheld by a firm (Limba et al. 2017). Examples of such impactful decisions include those behind the addition of new network security tools, the cybersecurity awareness programs, as well as determining appropriate security controls and procedures that address the specific threats.
Based on the analysis above, it is evident that upholding the measures in place against cyber-attacks is relative based on the volatility of the cyber-attacks and the organization's responses. Compliance management demands that organizations consider other exogenous influences on their cybersecurity management practices (Chertoff & Simon, 2015). Compliance management of cybersecurity strategies ensure the organization matches and upholds the industry requirements (Limba et al. 2017). Examples of internationally acceptable standards on cybersecurity management include the Payment Card Industry Data Security Standard (PCI-DSS), and Health Insurance Portability and Accountability Act (HIPAA) (Trim & Yang-Im, 2016). Ultimately, the PCI-DSS is specific to companies dealing with an invariably high credit card transaction.
Moreover, the regulation demands that the aforementioned organizations take up controls that protect their customers from credit card fraud as well as systems capable of identifying theft. The HIPAA Act standardizes security controls on the protection of all credit card information (Pardini et al., 2016). Conversely, the HIPAA Act requires that all medical institutions adhere to the regulations set for protecting the privacy and security of the patients' health information (Von Solms & Von Solms, 2006). The acts, amongst many other industry-specific acts, increase uniformity on the level of data security amongst different organizations in the industry.
Above the specific compliance measures taken up by organizations to enhance their cybersecurity, pertinent standardized actions exist that are key to the compliance process. First, the aforementioned organizations must pick up internal audits that act as buffers against impending compliance issues. Moreover, the organizations must use external auditors that offer objective feedback on compliance issues faced by the organization. Second, given that cybersecurity is a dynamic field faced by different organizations in varied scales, constant research must be conducted to ensure the organizations remain compliant at all times (Von Solms & Von Solms, 2006). The organizations can use the input from the external auditors as well as their legal counsel and local authorities to determine whether they are still compliant.
To continue, on a third note, organizations can ensure that all their controls and security procedures are compliant. A considerable number of compliance requirements include procedures that organizations must use if they want to protect their stakeholder's interests (Von Solms & Von Solms, 2006). Consequently, organizations must adopt compliance reporting. Compliance reporting acts as a comparative threshold over how the organization has and continues to be compliant (Dar, 2016). To enhance more transparent reporting, organizations can come up with penalties if they fail to offer the proper audit documentation.
Based on the introduction, the breadth of governance, risk, and compliance efforts vary across different establishments. However, as much as there are variations in the adaptation, similar opportunities exist for the eased absorption of emerging innovations and future technologies. Organizations can use governance, risk, and compliance software as shown in Figure 3. Conversely, organizations can also use Security Information and Event Management (SIEM) tools. Such tools act as buffers against intrusive efforts as well as create a log of cyber-attacks (Pardini et al., 2016). The overall effect is the increased visibility of the security incidents faced by the organization making investigations more efficient and effective. Also, having this data can be useful for complying with key industry cybersecurity regulations.
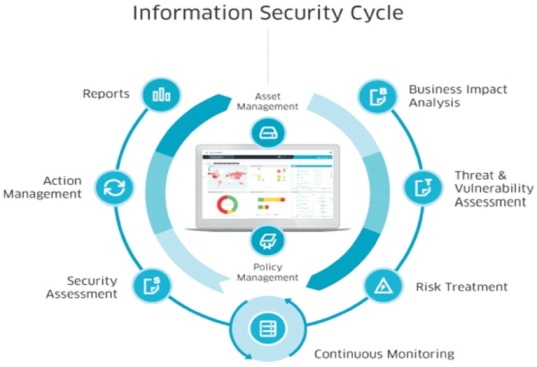
Figure 3. Example of a GRC (Governance, Risk, and Compliance) Framework (BWise, n.d.)
Depending on the level of cybersecurity, technical or nontechnical enhancement desired by an organization, the entity can supplement the relevant security software with constant audits procedures. The constant audits (both in-house and third party) are reinforcements for the production of noticeable results.
Various organizations may find it challenging to holistically adopt governance, risk assessment, and compliance strategies in their cybersecurity management citing various endogenous and exogenous factors. To ease adoption, an organization might consider several tips. First, the organization must have in place specific goals for the integrated cybersecurity system (Salimath & Philip, 2020). Knowing these goals can help a business customize their framework to best match their outcomes. Second, organizations can access their current situation, in the form of taking stock. An ideal uptake of an integrated GRC system may not be realized (Dar, 2016). The adopted integrated cybersecurity systems must be put in place in a manner that supplements the current system (Dar, 2016). Stock recognition of current resources aids in optimizing these resources so that it aligns with the new integrated strategy for the best impact.
Third, an organization may align their personnel, using a clear governance framework, to specific roles and responsibilities in the newly integrated system. Assigning the roles and responsibilities eases the path to accountability (Salimath & Philip, 2020). Additionally, assigning the roles establishes a clear chain of communication. An open communication system makes it easier to address issues from the front-line employees, as backed by the individuals in charge of creating the integrated framework.
Fourth, the hypothesized organization may conduct a test before rolling in the integrated cybersecurity system. Through the feedback from the trial run, the organization can access the simulated results based on their real-life environments (Dar, 2016). The subsequent results are the removal of twists that may reduce the predetermined risks to the business (Pham, 2019). Ultimately, it is essential that business access have the requirements to establish the integrated cybersecurity system.
Cyber Security Management is a diverse field that can have a standardized protocol for creating governance, risk and compliance through applying a working framework. Nonetheless, as much as the integration of different protocol requirements is lauded for its ease in reinforcing a strong cybersecurity system, several instances exist where the change has not been realized with ease (Pham, 2019). For example, the governance, risk, and compliance framework officials may not be authorized to enforce the plan. Different stages and institutionalized technical and/or non-technical breakdowns in communication may pose a challenge as to the goals desired by the organization's leadership (Salimath & Philip, 2020). Conversely, cases exist whereby auditing software may not be feasible due to the peculiarities of the GRC system. The most common inefficiency limiting the realization of an integrated GRC system is the lack of crucial security tools necessary to match the compliance requirements. Furthermore, few cases exist where the systems are inherently underdeveloped.