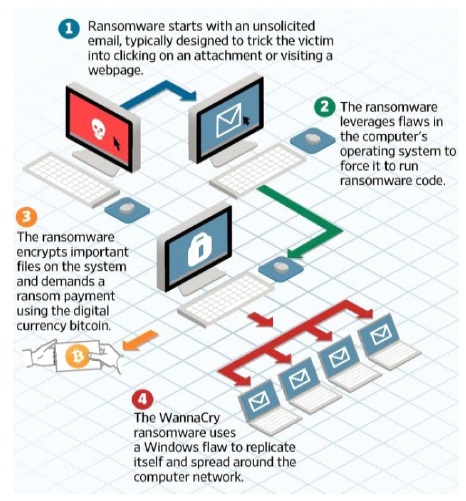
Figure 1. Stages of Ransomware Attack (The Business Times, 2017)
Ransomware is advanced malicious software which comes in different forms, with the intention to attack and take control of basic infrastructures and computer systems. The majority of these threats are meant to extort money from their victims by asking for a ransom in exchange for decryption keys. Most of the techniques deployed to detect this could not completely prevent ransomware attacks because of its obfuscation techniques. In this research work, an intelligent crypto-locker ransomware detection technique using Support Vector Machine (SVM) and Grey Wolf Optimization (GWO) algorithm is proposed to overcome the malware obfuscation technique because of its ability to learn, train and fit dataset based on the observed features. The proposed technique has shown remarkable prospects in detecting cryptolocker ransomware attacks with high true positive and low false positive rate.
Ransomware is a special kind of malicious software that uses on system vulnerability to lock a computer system and encrypt data using various encryption scheme to prevent access to the infected system until ransom is paid for the decryption key (Richardson & North, 2017). Malware developer considered the massive usage of information technology in the management and running buriners affairs and make the end users suffer in a very massive scale. The hackers direct the malware code to attack the information system using the internet via the browser exploit kits, attached email and other available vulnerabilities in order to take control of the entire systems (Bhardwaj, Avasthi, Sastry, & Subrahmanyam, 2016). Figure 1 explains the stages of ransomware attack.

Figure 1. Stages of Ransomware Attack (The Business Times, 2017)
Crypto-locker is an advanced ransomware that attack and perform dual functions of encrypting system files and locking the system screen with a ransom note, requesting for payment in exchange for decryption key (Savage, Coogan, & Lau, 2015). There are five distinct phases of a ransomware attack, regardless of whether it's a mass distribution or a targeted attack (Brewer, 2016). The Exploitation and Infection phase, is where the malware use phishing and pharming of email and exploit kit to execute files on the computer system. Delivery and Execution phase, is where the crypto-locker executables are delivered to the target system. Back-up spoliation is the phase where the malware remove the back-up files and folders to avoid system restore. File Encryption and the final phase sends the User Notification and clean-up, this is where ransom note is displayed and back-up files removed from the system.
Support Vector Machine (SVM) is a type of classification algorithm that is designed to adapt to a range of classification problems with ability to implicitly perform a non-linear feature space transform (Boswell, 2002). In recent times, application of SVMs in classification problems has increased because of its capability to segregate datasets using the best hyperplane. SVMs have been applied in multidimensional data classification, classification of microarrays, wind speed prediction, voltage stability monitoring, classification of power quality events, and contingency ranking (Boswell, 2002).
Grey Wolf Optimizer (GWO) is one of the Meta-heuristic optimization techniques, a concept inspired by the social hierarchy and hunting behaviour of a grey wolves. Grey wolves have been considered as the apex predator with a high social dominant hierarchy because of their natural hunting patterns which comprises of tracking, encircling and attacking of prey (Mirjalili, Mirjalili, & Lewis, 2014).
This research work, hereby proposes an intelligent cryptolocker ransomware attack detection by using GWO algorithm for feature selection and, improve the performance of SVM classifier for better results.
In recent times, studies have been carried out on the detection of ransomware attack. (Brewer, 2016; Boswell, 2002; Mirjalili et al., 2014; Weckstén, Frick, Sjöström, & Järpe, 2016) mostly proposed a signature-based approach which relies on the malware information stored in the repository for detection. The drawback of this technique is the inability to detect ransomware whose signature are yet to be stored in the malware repository. (Savage et al., 2015; Continella et al., 2016; Patyal, Sampalli, Ye, & Rahman, 2017; Kolodenker, Koch, Stringhini, & Egele, 2017; Al-rimy & Maarof, 2018; Cabaj, Gregorczyk, & Mazurczyk, 2015; Yang, Yang, et.al. Qian, Lo, Qian, & Tao, 2015; Moore, 2016; Sgandurra, Muñoz- González, Mohsen, & Lupu, 2016; Shaukat & Ribeiro, 2018; Ferrante, Malek, Martinelli, Mercaldo, & Milosevic, 2017; Scaife, Carter, Traynor, & Butler, 2016) focused on improving the signature-based approach by designing a behaviour-based system with different detection mechanisms and classifier to perform live monitoring of window and Android event logs in real-time to detect ransomware attack. The limitation of this system is its inability to stand the malware sophisticated packing techniques (obfuscation) and created system noise which resulted in misclassification of the crypto-locker and benign applications with high false positive and error rate.
After intensive exploration of the research on ransomware detection approaches, users still find themselves vulnerable to cr ypto-locker ransomware attacks (Ahmadian & Shahriari, 2016; Hong, Liu, Ren, & Chen, 2017; Kharraz, Arshad, Mulliner, Robertson, & Kirda, 2016; Kharraz & Kirda, 2017). This indicators call for further improvement in the current detection techniques or build another with a unique characteristics that will match crypto-locker ransomware method of attack.
To overcome the noticeable drawback of the existing techniques, the authors proposed an intelligent cryptolocker ransomware detection technique with GWO algorithm for feature selection of the extracted features from crypto-locker and benign application datasets, to enhance the performance of SVM classifier for better accuracy with low false positive rate.
The key contributions of this research include:
The proposed framework of SVM-GWO crypto-locker ransomware detection consists of features selection, extraction and classification as shown in Figure 2.
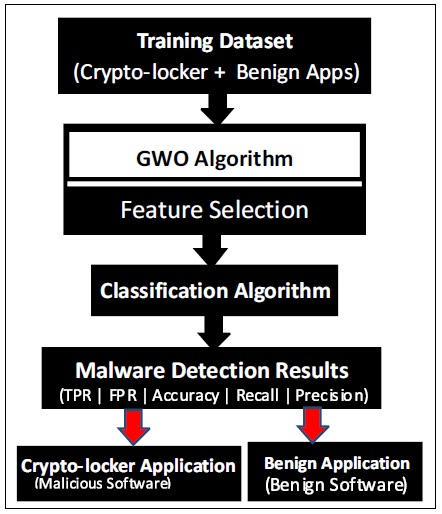
Figure 2. Proposed SVM-GWO Detection Framework
Given a training dataset sample l such that {xi, yi}, i = 1, ..., l, each sample with d inputs (xi ϵ Rd), with a class label with one or two values (yi ϵ {-1, 1}).
2.1.1 Linearly Classifier
This follows all the hyperplanes in Rd which was parameterized with a vector (w), constant (b), and expressed as:
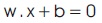
(Note: Vector w is orthogonal to the hyperplane.) Given such hyperplane (w, b) which separates the data and gives the function as:
2.1.2 Perception Classifier
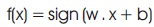
This equation perfectly classifies the training data and possibly other unknown dataset. Meanwhile, a given hyperplane denoted by (w,b) is similarly expressed by all pairs {λw, λb} for λ ϵ R. This can now be defined that the canonical hyperplane separates the data from the hyperplane by a “distance” of at least 1 which satisfy:
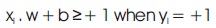
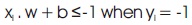
which can be combined as:
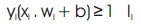
All such kind of hyperplanes have a “functional distance" ≥ 1 (which exactly means, the function's value is ≥ 1). It should not be confused with the “geometric" or “Euclidean distance" (known as the margin). For any given hyperplane (w, b), all pairs {λw, λb} define the same hyperplane, but with a different functional distance to a given data point. To find the geometric distance from the hyperplane to a data point, regularize the magnitude of w which will define the distance as:
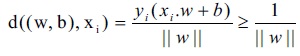
Relating to the equation, see that this is accomplished by minimizing which is subject to the distance constrains. The entire problem is ultimately transformed into:
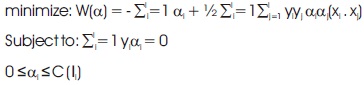
Where α is the vector of l non-negative Lagrange multiplers to be determined, and C is a constant. The matrix can define:
(H)ij = yiyj(xixj), which is presented in compact notation:
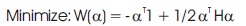

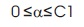
from the derivation of these equations, hyperplane becomes
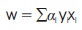
Meaning that vector w is a linear combination of the training examples shown as:
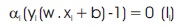
That is, the functional distance of an example is higher than 1 when yi(xi . w i+ b) > 1, then αi = 0. Which means that only the nearest data points contribute to w. The training example αi >0 are referred to as support vector. This is required to define optimal hyperplane.
To have optimal α (on the construct w), find the fully specified hyperplane. To implement this, take any “positive” and “negative” support vector, x+ and x-, for which
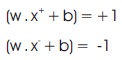
By solving these equations
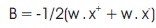
Based on the analysis presented above, any application in the dataset that tend to possess some characteristics of a violator is made a Support Vector (SV). Blocking points will be identified and pruned using the ideas presented by the equation. The algorithm stops when all points are classified within an error bound plane, for instance, yi f(xi) > 1 – ϵV. The outline of the algorithm is presented in Figure 3.
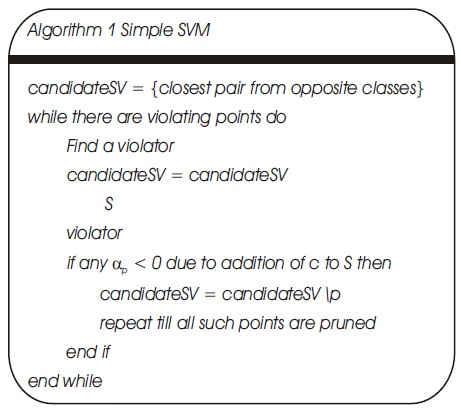
Figure 3. Pseudocode for SVM Classifier
2.2.1 Encircling Prey
Considering the analysis carried out, the grey wolves encircle prey during the hunting period which has been mathematically model in the equations (12) and (13).
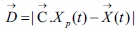
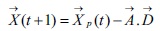
Where t refers to the current iteration,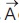 and
and 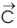 are coefficient vectors,
are coefficient vectors,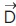 , the distance between wolf and prey depends on the location of the prey
, the distance between wolf and prey depends on the location of the prey 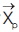 while
while 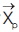 defines the position vector of the prey, and
defines the position vector of the prey, and 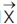 specifies the position vector of a grey wolf. The vectors
specifies the position vector of a grey wolf. The vectors 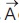 and
and 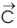 are formulated as follows
are formulated as follows
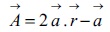
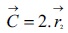
At this point, components of 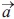 linearly decreased from 2 to 0 over the course of the iterations while r1 and r2 are random vectors in [0, 1] coordinates.
linearly decreased from 2 to 0 over the course of the iterations while r1 and r2 are random vectors in [0, 1] coordinates.
2.2.2 Hunting
The hunting style of a Grey wolf is usually conducted by the alpha, but the beta and delta may also participate in hunting sometimes. More so, in an abstract search space there is no idea about the location of the prey. To mathematically simulate the hunting behavior of grey wolves, assume that the alpha, beta, and delta have better information of the target location of a prey. Therefore, the first three best solutions gotten already, oblige the other search agents (including the omegas) to update their positions according to the position of the best search agent by the formula presented below.
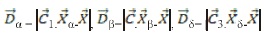
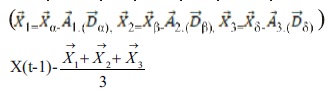
2.2.3 Attacking Prey (Exploitation)
Finally, the grey wolves' conclude the hunting exercise by attacking the prey after the movement has stopped. In order to mathematically model the grey wolf approaching the prey, decrease the value of 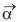 . while, the variation range of
. while, the variation range of 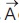 is also decreased by
is also decreased by 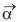 ; meaning that,
; meaning that, 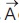 is a random value in the interval [-2a, 2a] where a is decreased from 2 to 0 over the course of iterations, the random values of A are in [-1,1], and next position of a search agent can be in any position between its present position and the position of the prey which will finally lead to the attack on the prey as shown in Figure 4.
is a random value in the interval [-2a, 2a] where a is decreased from 2 to 0 over the course of iterations, the random values of A are in [-1,1], and next position of a search agent can be in any position between its present position and the position of the prey which will finally lead to the attack on the prey as shown in Figure 4.

Figure 4. Pseudocode of the GWO
The Crypto-locker ransomware and benign applications datasets was gotten from the work of (Sgandurra et al., 2016). The dataset contains 582 samples (38.19%) of crypto-locker ransomware and 942 (61.81%) of benign applications making a total of 1524 samples from 11 different families. GWO is employed to evaluates the following categories of features found in crypto-locker and benign application datasets. Crypto-locker extracted features includes: (i) Windows API calls (ii) Registry Key Operations (iii) File System Operations (iv) the set of file operations performed per File Extension, (v) Directory Operations (vi) Dropped Files and (vii) Strings contain in the binary.
The benign application features includes: (i) generic utilities for Windows (ii) drivers (iii) popular browsers (iv) file utilities (v) multimedia tools (vi) developers tools (vii) games (viii) network utilities (ix) paint tools (x) databases (xi) emulator and virtual machines monitors and office tools.
GWO does the feature selection using the Mutual Information (MI) criterion which allows the algorithm to select the most discriminating features extracted from crypto-locker and benign application datasets to improve SVM classification problem with better performance.
The experiment on the classification of Crypto-locker datasets was implemented using SVM classification scheme together with GWO optimization algorithm on standard simulation platforms. The GWO algorithm (Java source code) was uploaded on the simulation platform to perform feature selection of the dataset and output fed into SVM classifier for classification of the dataset into crypto-locker and benign applications.
Table 1 shows the family of the Crypto-locker ransomware with their identifiable codes as contain in Sgandurra dataset.
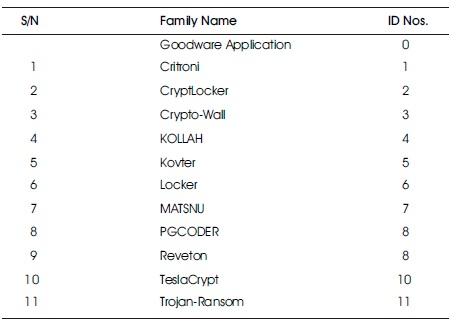
Table 1. Families of Sgandurra Crypto-locker Ransomware Dataset
The Table 2 gives full details of the descriptive features of the Sgandurra ransomware dataset with their respective codes and attribute types to aid the classification experiment.
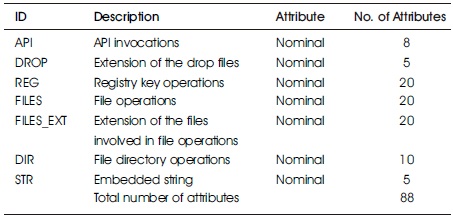
Table 2. Sgandurra Dataset Id Terms with Descriptive Features
The performance evaluation of Support Vector Machine after feature extraction and selection with Grey-Wolf Optimization algorithm used different percentage split on 10-folds cross validation.
The Table 3 summarizes the results calculating the average, minimum, maximum, variance and standard deviation from the performance metrics of the tests carried out.
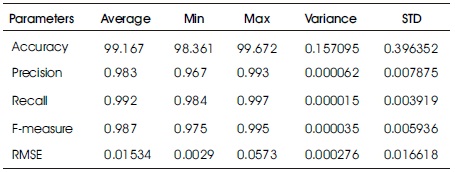
Table 3. SVM With GWO Classification Result
The performance evaluation of the SVM and GWO accuracy is used to show level of perfection with regards to the correctly classified Crypto-locker ransomware as against the benign applications. The highest level of accuracy is considered to be 100. The experimental test result obtained after using different percentage split values of the Crypto-locker dataset with constant 10-folds cross validation is shown in Figure 5.
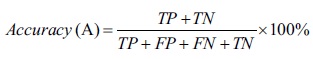
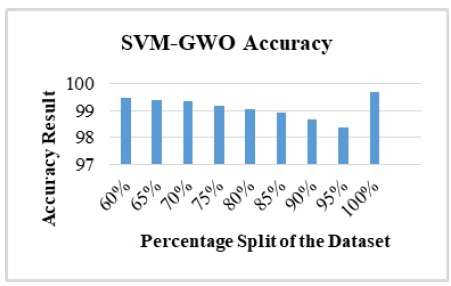
Figure 5. Performance evaluation of SVM accuracy at percentage split of the datasets
The RMSE is one of the parameters used to indicate the levels of the classifier perfection during and after the experiment. The lower the values of RMSE the better the classifier predictions. This means that value zero gives the perfect result while higher values indicate a poor performance of the classifier. The results show the gradual decline of error as the percentage split of the dataset increases. Figure 6 shows various results of other performance metric from the SVM classifier as against each percentage split of the Crypto-locker datasets.
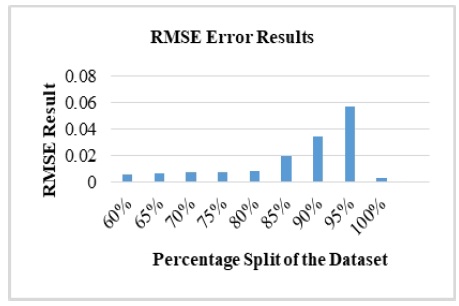
Figure 6. RMSE results against percentage split of the datasets
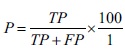
Precision (P) indicates the number of instances which are positively classified and are relevant. A high precision shows high relevance in detecting positives.
Recall (R) shows how well the system can detect positives
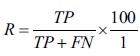
F-Measure = 2 x Precision * Recall /Precision + Recall
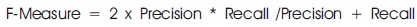
TPR and FPR: True Positive Rate and False Positive Rate were calculate based on the overall true number of benign and ransomware processes after about 10 fold of cross-validation using different percentage split
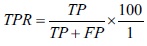
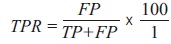
The Table 4 shows results of each performance metric obtained at different levels of the percentage split of the Crypto-locker dataset using a fixed 10-folds cross validation. The results obtained show the highest level of accuracy and perfection over other detection techniques proposed. This is an indication of superiority of a machine learned behavioral detection techniques against Crypto-locker ransomware attacks.
Table 4. SVM Classification On Sgandurra Crypto-locker Datasets Using Different Percentage Split On 10-folds Cross Validation
Table 5 and Figure 8 shows the comparative analysis and comparison of the accuracy result of this proposed system (SVM with GWO) against other related works.
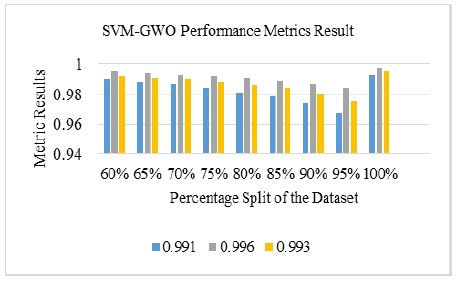
Figure 7. Performance Metrics of other Parameters
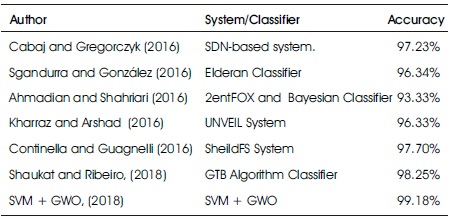
Table 5. Accuracy Result Comparison
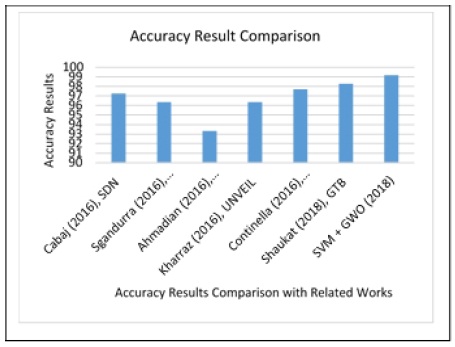
Figure 8. Performance Metrics of other Parameters
Ransomware has become a significant problem to a growing number of individuals, communities, organizations and companies. The attackers are beginning to consume each other; which is a sign of adverse rivalry among ransomware mobs. The geography statistics show that attackers will shift to previously unreached countries, where users are not as well prepared for fighting ransomware, and where competition among criminals is not so high, and if this eventually happens, the consequence will be devastating.
Several detecting techniques have been proposed ranging from a static-based approach which depends heavily on the store signature in malware repository, but could not detect unknown ransomware whose signature are yet to be store in the malware repository. The behaviour-based approach which monitor the system logs and actions on the stored files in real time could not stand the malware obfuscation techniques which result into generated system noise from the detection mechanism.
Therefore, the proposed intelligent Crypto-locker ransomware detection technique using SVM classification and GWO algorithm is a machine learned behavior-based approach that has the ability to learn, train and fit Cryptolocker applications, extract behavioral trait to improve the classification and prediction result.
The experiment was performed on a standard simulation platform where GWO optimized and selected the extracted features to improve SVM classifier for better result. The test was carried out using 10-folds cross validation with percentage split of the dataset and obtained 99.18% accuracy on the average. The result comparison from SVM with GWO algorithm has outperformed other related detection techniques in term of accuracy.