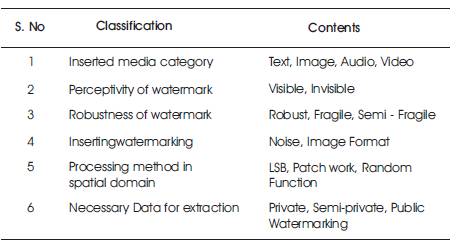
Table 1. Classification of Watermarking According to Several View Points
The Development of multimedia applications makes digital media to bring about conveniences to the people by easy processing of data. At the same time, it enables the illegal attackers to attack the works. For the protection of data, there has been growing interest in developing effective techniques to discourage the unauthorized duplication of digital data. Among Cryptography and Steganography, only the watermarking provides the copyright protection and authentication. This paper is a comprehensive review of diverse image processing methods and enormous number of interrelated solicitations in various disciplines, including various watermarking techniques. In this paper, different existing techniques are discussed along with their drawbacks, also explaining their future scope.
Information hiding means communication of information by hiding and retrieving from any digital media. The digital media may be a text, an image, an audio, a video or simply a plain text file. Information hiding is a general term encompassing many sub disciplines. However, generally it encompasses three disciplines: cryptography, watermarking and Steganography.
Steganography is the art and science of writing hidden messages in such a way that no one, apart from the sender and intended recipient, suspects the existence of the message, a form of security through obscurity. Generally, messages will appear to be something else: images, articles, shopping lists, or some other covert extra and classically, the hidden message may be in invisible ink between the visible lines of a private letter. The advantage of steganography over cryptography alone is that messages do not attract attention to themselves.
As an emerging technology, digital watermarking involves the ideas and theories of different subject coverage, such as signal processing, cryptography, probability theory and stochastic theory, network technology, algorithm design, and other techniques. Digital watermarking hides the copyright information into the digital data through certain algorithm. The secret information to be embedded will be some text, author's serial number, company logo, or images with some special importance. This secret information is embedded to the digital data (images, audio, and video) to ensure security, data authentication, and identification of owner and copyright protection. The watermark is hidden in the digital data either visibly or invisibly. Classification of watermarking according to several view points is shown in Table 1. Table 2 represents comparison of spatial and frequency domain. Watermark is embedded either in spatial or frequency domain. Both the domains are different and have their own pros and cons and are also used in different scenarios.

Table 1. Classification of Watermarking According to Several View Points
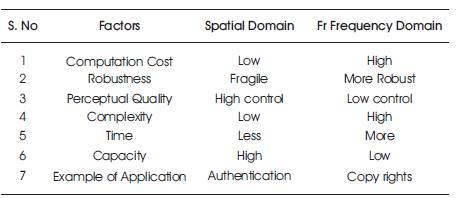
Table 2. Comparisons between Spatial Domain and Frequency Domain
Cryptography is the science of information security. The word is derived from the Greek word kryptos, meaning hidden. Cryptography is closely related to the disciplines of cryptology and cryptanalysis. Cryptography includes techniques such as microdots, merging words with images, and other ways to hide information in storage or transit. However, in today's computer-centric world, cryptography is most often associated with scrambling plaintext (ordinary text) into cipher text (a process called encryption), then back again (known as decryption).
Due to rapid development in the network and communication field, it has become necessary to protect the unauthorized duplication of a confidential image; it is done using watermarking. Watermarking is a technique which embeds a watermark signal into the host image in order to authenticate image and it is also used for hiding secret image along with high security using encryption key.
The objectives of the work are to provide information which is tacit by anybody for whom it is unintentional by means of translating color image or communications in such a way that no one, separately from the despatcher and envisioned receiver, perpetrates the forms of the message. The sanctuary of hidden data is augmented by odd and even bit scuffling during data implanting within the color image. In order to deliver veracity such that information will not be altered while storing or transiting among the senders and envisioned receivers without the change being detected. To offer validation by visible watermark overlay on color image so that the sender and receiver will confirm each other's identity individuality and the origin/destination of the information. High embedding capacity will be attained by embedding data in LSB of all three planes of the color image. To improve randomization and speed up, the encryption procedure is used by making a couple of keys per clock cycle.
The literature available within the scope of the proposed study is reviewed. It includes the issue of watermarking in the researches and surveys.
Remya and Sumithra (2013) have proposed the watermarking algorithm for telemedicine applications. In this method, Watermarking algorithms are used for embedding watermarks like patient's history and doctor's signature in binary image format into host's medical image for telemedicine applications. Medical images are done in DCT and DWT domains and the performance is evaluated based on PSNR and MSE. The most clear cut way to hide the watermark within the cover content is to directly embed it in the spatial domain. Read the CT image (cover image) and signature (watermark). Fix the alpha value to 1 (alpha=1). Multiply the alpha value with the sign and take the transform for the image (DCT/DWT). Add the watermark into the cover image and take the inverse transform to get the watermarked image. Calculate the MSE and PSNR between the original and watermarked image. Increment the alpha value. It is applicable only to medical image and here, the data embedding capacity is too low [23].
Manikandan et al. (2012) have proposed local distortion resistant image watermarking relying on salient feature. The watermark pattern is initially constructed in the DCT domain as a rectangular patch of size that is related to the size of the normalized image. If we let bi , i = 1, . . . , N be binary sequences of length K (which is the number of DCT coefficients that are going to be modulated) created by thresholding pseudo random values taken from the standard normal distribution (i.e., N(0, 1)), where N is the length of the multi bit watermark message, and mi is the ith bit of the message, then the middle zone of K DCT coefficients is modulated. The position of the middle zone of DCT coefficients is chosen so as to render the watermark both robust to attacks that affect high frequencies and invisible. The rest of the DCT coefficients are set to zero. The final watermark pattern is produced by inverse zigzag scanning of the zero padded C sequence. Insert the inverse DCT of the watermark in the spatial domain of the normalized image. It has Computational complexity and it is applicable only to gray scale images [38].
Manoj and Gireendranath (2012) have proposed invisible and blind watermarking scheme for copyright protection of digital images. This scheme makes use of a binary image as watermark data for protecting the copyrights of images. The embedded binary watermark is extracted from the watermarked image using watermark image size and the embedding strength. The host images size should be dyadic (2n x 2n) and a binary image is used as watermark. Initially, the non-overlapping blocks of size 2 x 2 are extracted from the host image. A pixel of binary watermark image is embedded into a single block. The mean calculation, embedding strength (γ) and sign function are employed in the process of embedding the watermark. Originally, each non-overlapping block is converted into a vector, and the mean value of the vector is computed. Afterwards, the mean value is divided by the embedding strength (γ) and used in the embedding. As the watermark is a binary image, the embedding of watermark involves two cases: embedding pixel value “1” and embedding pixel value “0”. Two distinct mathematical operations are performed for embedding pixel values “0” and “1”. It is applicable only to gray scale images and has a limited embedding capacity [24] .
Shinfeng and Shih (2010) have proposed improving the robustness of DCT- based image watermarking against JPEG compression. Every pixel of the watermark pattern at coordinate (i, j) is moved to (i*, j*), and k and m are the key parameters given by the user. Let Wp be the permuted watermark after Torus auto Orphism permutation, then divide Wp into non-overlapping pairs. The watermark information is embedded into the luminance components of images. After color transformation, the luminance Y of the image is divided into non-overlapping blocks of size 8 × 8, and each block of Y is DCT transformed independently. DCT-transformed block of Y is quantized based on the quantization to improve the invisibility of watermark, the complex blocks of images are selected for watermark embedding. In the DCT domain, the number of non-zero coefficients in each block is computed to estimate the complexity of the image block. Let N (n) represent the number of non-zero coefficients in block n. The image blocks will be sorted into descending order based on their corresponding N (n) s. The binary information of watermark pattern W is sequentially embedded into the selected image block. Two bits of a watermarked pattern are embedded into the low-frequency components of each selected block for preserving the visual quality of the watermarked image. It has less robustness and lower embedding capacity [25] .
Arathi and Chandra (2012) have proposed authentication of images through (LWM) technique with the aid of elliptic curve cryptography. In data embedding process, the signed message is embed into the image by using the LSB method. Initially, divide the given input image into a number of blocks and select the number of pixels from every block by vertical raster scanning. Embed the message (information) or host signal into an image by the Elliptic Cur ve Cr yptography. Elliptic Cur ve Cryptography (ECC) is also called as public key cr yptography, where each user or the device participating in the communication usually have a couple of keys, a public key and a private key, and a set of operations related with the keys to do the cryptographic operations. It has a poor randomization in key generation and lower security [2].
Tomaz and Andrej (2012) have proposed block-wise authentication method for digital images. The authentication scheme is in general, a MAC (Message Authentication Code) algorithm based on universal hash functions. Such an algorithm consists of two building blocks, an efficient keyed compression function that reduces long inputs to a fixed length and an encryption function that encrypts the hash. The encryption unit uses the 128 bit AES algorithm to encrypt the data. AES has a fixed block size of 128 bits and uses a 128 bit secret key. The reason we use a block-wise authentication method is not localization but speed. Because the pixels are read from the image sensor sequentially, it is convenient to process the image in a sequential manner. To process the image as a whole, we would have to first read the image from the image sensor and then store it in memory. This would require extra time and memory [26].
Umaamaheshvari and Thanushkodi (2012) have proposed a watermarking technique based on visual cryptography. To embed multiple binary watermarks into digital medical images based on the concept of Visual Cryptography (VC). Multiple watermarks are embedded as shared in the same image. The secret key K is used as a seed to generate wxh random numbers over the interval [1 to rxc ]. Let Ri be the ith random number. A binary matrix A of size wxh is created such that the entries in the array are the most significant bits of Ri , the pixel of the cover image I. A binary matrix C of size wxh is created such that the entries in the array are the most significant bits of the Ri , the random number. Now, both the matrices A and C are bitwise Exclusive-OR ed to create a binary matrix B of size wxh . Finally, a Master Share M is created by assigning a pair of bits for each element in the binary matrix B. It is applicable only to medical images and has a Poor quality watermark image [9].
Veera et al. (2010) have proposed email messages encryption and image steganography schemes for image authentication. So an observer is unable to know if a message is being sent or not. Steganography in images encodes each pixel as a series of numbers which represent the red, green and blue values which make up the color of that pixel. Since a slight change in this color scheme is not detectable by the human eye, it is used to hide information. This is usually accomplished by changing the least significant bit LSB for each pixel to correspond to the bits of the hidden message. It applies AES encryption algorithm by block. Each cipher text modify only one bit of one encrypted pixel of the image. It uses bit substitution-based data hiding method in order to embed the bits of the hidden message. For each block, the secret key k is used as the seed of the Pseudo-Random Number Generator (PRNG) to substitute the bit of a pixel with the bit to be hidden. Data embedding capacity is low. It has data loss during recovery of data [27] .
Gouenou et al. (2013) have proposed a reversible watermarking based on invariant image classification and dynamic histogram shifting. The first one corresponds to a invariant classification process for the purpose of identifying different sets of image regions. These regions are then independently watermarked, taking advantage of the most appropriate HS modulation. Then distinguishing two regions, where HS is directly applied to the pixels or applied dynamically to pixel prediction errors. Modulation such as PHS and DPEHS is chosen depending on the medical image dataset, for which PHS may be more efficient and simple than the DPEHS in the image black background, while DPEHS will be better within the regions where the signal is non-null and textured. Considering a specific run into the image, possibly based on a secret key, pixels are classified into PHS region or DPEHS region. One part of the message is embedded in the PHS region along with some overhead in case of overflows/underflows. The rest of the message is embedded into the pixels of the DEPHS region. This technique has a lower embedding capacity and is applicable only to gray scale images [28].
Rajendra and Narawade (2012) have proposed reduced pixel shifting and backward histogram shifting based reversible watermarking for providing high embedding capacity along with high PSNR. This method is applicable to cartoon images. Generally, histogram of cartoon images concentrates at 255 pixel value, which is called as maximum point. Backward method finds minimum point before Maximum point. Backward histogram shifting method shifts required pixel values to left by “1” number, which is called the minimum point. Embedding capacity of cartoon images are maximum because maximum numbers of pixels are available at 255, than any other images. There is a complexity in backward shifting of histogram. It is applicable only to gray scale images. It possess limited embedding capacity [29].
Bo et al. (2010) have proposed high payload histogram based reversible watermarking using linear prediction. Linear prediction is used to obtain the initial prediction and it is corrected into a more accurate prediction. The whole image is divided into M non-overlapping blocks and the prediction error expansion is applied for data embedding. In the linear prediction process, the image is divided into N non-overlapping blocks, and then they calculate the prediction-error histogram and restore the i LP and i RP of all blocks as a part of the extra information. Then, 1 E and 2 E are compressed as extra information. The cover image is divided into three parts: Unchanged Area (UA) containing the first row, the first column and the last column of area; Additional Area (AA) containing the last three rows of area; Embedding Area (EA) containing the rest of image. In the embedding process, apply the prediction-error histogram shifting and embed the watermark information. It possess less security and it is applicable only to gray scale images [11].
Shyang et al. (2011) have proposed a modified reversible non-overlapping block based multilevel residual image histogram shifting method and the central block prediction method was used to generate the difference values. The confidential information is hidden in the peak point of the residual image. Residual image whose histogram generally follows the laplacian distribution with more number of pixels are centered around the zero value two peak points (M1 and M2) from the histogram, such that M1< M2, and their corresponding zero points (m1, m2), such that the first peak point (M1) is just greater than m1 and the second peak point (M2) is just smaller than m2. The strategy of this is to avoid overlapping in the shifting phase. Once the peak and zero pair are searched, the histogram between (m1, M1) is shifted left by 1 unit and the histogram between (M2, m2) is shifted right by 1 unit. It is applicable only to gray scale images and it has a low embedding capacity [30].
Yang and Tsai (2010) have proposed histogram-based reversible data hiding by interleaving predictions. In this method, most pixels are predicted by their two neighboring pixels and four neighboring pixels in using column-based and chessboard-based approaches respectively. The difference value of each pixel between the original image and the steno image remains within +1. In interleaving predictions, pixels in odd columns will be predicted by pixels in even columns, then pixels in even columns are predicted by pixels in odd columns. In the embedding process, predictive error values of odd columns are used to generate a histogram to embed secret data. Then predictive error values of even columns are used. In the extracting and reversing process, predictive error values of even columns are processed first. Then predictive error values of odd columns are processed. It is based on spatial domain so it is less robust to potential attacks [10].
Anumol et al. (2013) have proposed FPGA implementation of invisible image watermarking algorithm for images. The Discrete Wavelet Transform analyzes the signal at different frequency bands with different resolutions by decomposing the signal into an approximation and detail information . The decomposition of the signal into different frequency bands obtained by successive high pass g(n) and low pass h(n) filtering of the time domain. After the DWT decomposition of secret image and original image, the bits are embedded from the Secret image into the original input image bits. Then convert the bits in the form of an image using Simulink block set and the Watermarked image is obtained. In this work, Vertex 6 and Vertex 4 FPGA devices are used for the implementation of watermarking embedding stage. In the extraction stage, the watermarked image is separate out using DWT and IDWT. The group of bits are written into a file and then it is converted from bit to image using Simulink block set. The watermark must be able to easily and securely embedded and retrieved by the owner. In this work, Vertex 6 and Vertex 4 FPGA devices are used for the implementation of watermarking extraction stage. DWT decomposition and reconstruction makes data loss results in poor quality of recovered image [7].
Kiran and Kanwal Garg (2015) have proposed the design and implementation of FPGA based invisible image watermarking encoder using wavelet transformation. A watermarking system can be implemented with either a software or hardware. Once the images are acquired, watermarks are inserted in them offline and then images are made available. The objective of this work is to implement hardware based invisible watermarking scheme so as to bridge that gap, so that watermarking is done in real time while capturing the image. VLSI architecture for implementing invisible watermarking scheme based upon Haar wavelet transformation is proposed. This technique uses a 2D DWT to decompose an image into various frequency channels. A scaled image is used as the watermark and inserted into mid frequency wavelet channel. Taking 2D IDWT of the altered wavelet decomposition produces the watermark embedded image. In order to reduce the complexities of the design, linear algebra view of DWT and IDWT has been used. It has limited the embedding capacity [31] .
Sandeep and Rajiv (2013) have proposed watermarking using MFHWT. In this method, the watermarking algorithm in the DWT Domain and WPT using a Modified Haar Wavelet Transform (MFHWT) evolutionary algorithm to improve the quality of the image was given. The algorithm is to decompose the original image using DWT and WPT according to the size of watermark. Modified Fast Haar Transform (MFHT) will be done by just pleasing (w +x + y + z) 4 instead of (x + y)/2 for approximation and (w +x .y -z) /4 instead of (x- y)/2 for differencing process. 4 nodes are considered at a time. The calculation for (w+ x .y -z)/4 will yield the aspect coefficients in the level of n-2. To obtain specify coefficients, differencing processes (x.y)/2 are still required to be done. MFHWT algorithm is used which reduce the memory requirement and the amount of inefficient movement of Haar coefficients. Due to wavelet compression, there is some loss of data and complexity in color image watermarking [8].
Umaamaheshvari and Thanushkodi (2013) have proposed a robust image watermarking based on block based error correction code. An algorithm based on block based error correcting code and DWT watermarking is applied on digital images. It is based on convolutional code to improve the robustness of the embedded watermark. The watermarking is preferred in low frequency band of the Discrete Wavelet Transform (DWT) and as a result, it can refuse to accept the destruction of image processing. The Haar wavelet filters are preferred for the DWT decomposition to give recovered outcome in embedding process. Here the embedding process is done using the weighted addition rule while essentially considering the case where the host image was obtainable at the extraction and so, host intrusion was not a problem. By applying Inverse Discrete Wavelet Transform (IDWT) at the extraction phase, the watermarked image will be retrieved. The performance of the proposed watermarking method is estimated with the parameters PSNR, MSE, SSIM, Correlation, and Entropy. It is applicable only to gray scale images and has a limited embedding capacity [32].
Mohamed and Sujatha (2012) have proposed DWT based invisible watermarking for digital images. In this method, frequency domain based blind robust watermarking, watermark is constructed from the spatial domain and data embedding is done in the high frequency band. DWT is performed on the host image and values in LL1 sub band forms the first matrix. The second matrix is formed by finding the average values from every 2x2 blocks. Watermark construction process finds the disparity values between those two matrices and is converted into a binary matrix. The resultant matrix is disordered with the help of Arnold Transform. The extraction is done without using original image. It is not resistant to all malicious attacks. Distortion occurs during the recovery of an image [33].
Baisa (2011) has proposed wavelet based color image watermarking. The cover image is decomposed using simple “Haar” wavelet into four non overlapping multi resolution coefficient sets: LL1 , HL1 , LH1 and HH1 . A second level DWT was performed on LL1 to give 4 coefficients: LL2 , HL2 , LH2 and HH2 . Arnold transform was used to scramble the watermarked image. The PN sequence is generated depending on “KEY” and the sum of random sequence is found as say SUM. If SUM > T where, T is some predefined threshold value, then find two scrambled images applying Arnold transform with KEY1 and KEY2. Absolute difference of two scrambled images are taken to give the “Final scrambled image”. If SUM < T , then apply Arnold transform directly to the watermarked image with “KEY” to get “Final scrambled image”. Add “Final Scrambled image” to HL3 coefficients of the cover image. Take IDWT at level 3, level 2 and level 1, which gives a watermarked color image. Wavelet decomposition and reconstruction causes error during recovery of images [3].
Dinu (2011) has proposed a data embedding for prediction based reversible watermarking. This method split the expanded difference between the current pixel and its prediction context. The embedding is performed at a lower distortion than the simple embedding of the expanded difference into the current pixel. At detection, the same expanded error is recovered and the extraction of the embedded data and the recovery of the original pixels follow. Embedding data into the prediction context may diminish the performances of further prediction. The increase of the prediction error increases as well the distortion is introduced by watermarking. The optimization of the embedding should be tuned in order to surpass the loss caused by prediction error increase. This method is applicable only to gray scale images and has a low security for the hidden data [5].
Karthigaikumar et al. (2011) have proposed FPGA is Implementation of high speed low area DWT Based Invisible Image Watermarking Algorithm. In the VLSI implementation of digital watermarking, original image is converted into vector form. Then the entire decimal signal is converted into binary signals which mean bit form. The group of bits are stored in a file and using the Simulink block sets read an image in a bit by bit format. The secret image is also read in the same way. After the DWT decomposition of secret image and original image, the bits are embedded from the Secret image into the original input image bits. Finally, the image which is in the bit form is converted into an image using Simulink block set to get the Watermarked image. The Xilinx System Generator for DSP is a plug-in to Simulink that enables designers to develop high-performance DSP systems for Xilinx FPGAs. In this research, the invisible watermarking algorithm is designed and the system is simulated using MATLAB, Simulink, and Xilinx library of bit/cycle-true models. The tool will then automatically generate synthesizable HDL code mapped to Xilinx FPGA. Due to DWT decomposition, the image may suffer loss of data and will not withstand all intentional attacks [15] .
Devapriya and Ramar (2010) have proposed statistical image watermarking in DWT domain. It embeds watermarks by modifying log-scaled singular value of selected coefficients of all sub-bands. In a DWT-based scheme, the DWT coefficients are modified with the data that represents the watermark. Let X = {x1 , x2 … xN } and Y = {y1 , y2 … yN } be the vectors representing DWT coefficients of the cover image and watermarked image in the H2 region. For embedding, a bit stream is transformed into a sequence. This sequence is used as the watermark. In this case, the watermark W = {w1 , w2 … wN } is chosen from a set M, is embedded into X giving Y. W is inserted into the X by using multiplicative rule, yi = xi (1 +aiwi) i = 1, 2, … N, where a is the embedding strength and xi , wi and yi are the values of the random variable Xi , Wi and Yi respectively, whose Probability Distribution Functions (PDFs) are (si), (wi) and (yi ) respectively for i = 1, 2, …N. The elements of the watermarks from the set M are independent and uniformly distributed in the interval [-1, 1]. It is not suitable for all statistical modelling and color images [4] .
Hazem and Nedal (2010) have proposed blind color image watermarking based on wavelet-tree bit host difference selection. Wavelet-Trees (WT) are constructed for each layer. The trees are generated individually for each color component; each watermark bit is embedded using two trees from two different color components. The bit insertion process modifies the difference (energy) between the selected two trees in such a manner that this difference carries the bit sign with sufficient energy. Next, the resulting trees are searched, based on dominant relations. To find the robust bit host locations, these locations are used by the encoder to construct robust host differences and then to embed the watermark bits. Here, the implemented watermark is a binary sequence that carries the author information or his signature. Finally, the WTs are decomposed to restore the DWT image and the inverse DWT (IDWT) is performed to obtain the watermarked RGB image. It has low PSNR value and poor image quality of the retrieved image [34] .
Jih et al. (2010) have proposed watermarking technique based on DWT associated with embedding rule. 1-level DWT in the host image and divide the HL and LH sub band into non-overlapping blocks of size 2*2. The watermarks are then embedded in the blocks located at the even columns of the HL sub band and the blocks are located at the odd columns of the LH sub band. A watermark bit is embedded in a block by modifying the four coefficients in the block according to a embedding rule. To embed a watermark bit w in a block of size 2*2, the mean value of the four coefficients is first calculated. Let r be a integers such that 3r ≤ me< 3(r +1), then each of the four coefficients are modified by adding a common value so that the mean of the modified coefficients equals 3r if (w = 0 and r is even) or (w=1 and r is odd), and equals 3 (r+1) if (w=0 and r is odd) or (w=1 and r is even). This modification causes the mean value becoming the even or odd multiple of 3 closest to the original mean value depending on the embedded watermark bit w=0 or 1. It is applicable to particular statistical model and gray scale image [6].
Pan et al. (2010) have proposed an additive and lossless watermarking method based on invariant image approximation and haar wavelet transform. This scheme embeds the message into the wavelet coefficients of the image associated to watermark ables to block while preserving the invariance. Because of this latter constraint, the watermark pattern W added to pixel block in the spatial domain is predefined. The distortion is applied on one wavelet coefficient is also fixed. Haar wavelet transform then Haar (Bw) = Haar (B) + Haar (W) = Haar (B)+W wave, where B, Bw , W and Wwave are the original pixel block. The Haar wavelet transform of W = [+Δ-Δ; - Δ+Δ] leads to W wave = [0 0; 0 Δwave ]. As a consequence, adding or subtracting W to one block in the spatial domain allows modulating the related high-high subband coefficient in the wavelet domain. Thus, invariance of the classification is preserved and it is possible to modulate wavelet coefficients in a reversible way. This method having lower embedding capacity and distortions occurs in the watermarked image [12] .
Mohamed and Sujatha (2010) have proposed an invisible watermarking technique for image authentication. The watermark is generated from pixel value of the original image and so there is no need of external image or logo. Hence it is necessary to devise a method to generate watermark, the resolution of watermark is assumed to be half of that of the original image. For embedding the watermark, a1-level Discrete Wavelet Transform is performed. Watermark information is embedded in the high frequency bands (HH ). The image matrix will be 1 changed into a new matrix by the Arnold transform which results in a scrambled version to offer security. It is a mapping function which changes a point (x, y) to another point (x1, y1). In detection phase, two kinds of watermarks will be obtained. One is generated from watermarked image and the other is extracted from HH sub band 1 which has been already embedded within the host image. The resolution of watermark is half that of the original image and this is applicable only to gray scale image [13].
Rohollah, Sami, and Shumei (2014) have proposed image watermarking using FPGA hardware using DCT. A Discrete Cosine Transform (DCT) is defined as the summation of cosines function oscillation at different frequencies and it is closely related to the Discrete Fourier transform (DFT). The two dimensional DCT is applied to the two input images. Host Image is taken and then divided that to non-overlaying blocks partition. Using Ni method, the host image with size M × N is divided into a set of m ×n blocks where m and n are even, m=n=8 as block size is chosen. The watermarked image is created according to message data, take the message image and convert it to black and white image and reshape it to one dimensional vector that need to be coded in the host image. According to message data (zero or one), they compare two specific elements of DCT block and then swap them. It should be mentioned that the difference between two specific values must be less than threshold K that which is defined in the code. In otherwise, two specific values are adjusted that the difference is less than the threshold by adding and subtracting K/2 values appropriate to DCT elements values. Finally, the watermarked image is created by applying new blocks according to message data to the watermarked image. For extracting message data from host image, inversely in the receiver part for decoding message from Watermarked image, they apply IDCT to the blocks and by comparing two specific values of blocks, the message data (black and white) was reached from watermarked image. The drawback of this paper is that DCT does not work well at edge singularities and the robustness towards the attack is low [18] .
Karthigaikumar and Baskaran (2010a) have proposed FPGA and ASIC implementation of robust invisible binary image watermarking algorithm using connectivity preserving criteria binary image is given as input to the algorithm. The Watermark is included in the input signal. The insertion algorithm inserts the watermark into the object, whereas the verification algorithm authenticates the object. Software implementation of watermarking algorithm is less useful when the image size and bit depth grow to a high value. Hence, hardware description languages are used to implement the media applications. Once the design has been programmed using VHDL, and the desired performance is achieved, it can be downloaded into an FPGA. An invisible watermarking algorithm is implemented in FPGA and ASIC. An image signal is taken as an input and converted into decimal format using MATLAB. This process would give an array of 256x256 pixels. Each pixel ranging from 0 to 255 levels of its intensity. This is converted into binary value using threshold value. The binary value 1 represents black pixel and 0 represents white pixel. Hence, an image is converted into binary form and partitioned into 3x3 windows. Four formulae are applied to each window to check the flip ability of the center pixel. One control unit operates black transition formula, another one white transition formula the other one Interior Right (IR) angle formula and another one 'C' transitions. The pixel can be flipped so that an intruder cannot get the original bit. The flip ability of a pixel depends on the transitions of the pixel to its 8 neighbour in 3x3 blocks, in particular, the 4 connectivity and the 8 connectivity among pixels. The drawback of this paper is that DWT does not work well at edge singularities and the speed of processing is high, the area consumed for processing is also high [16].
Karthigaikumar and Baskaran (2010b) have proposed an ASIC implementation of a low power robust invisible watermarking processor. FPGA and ASIC implementation of an invisible robust data hiding watermarking algorithm was given. In this watermarking technique, the pixels are flipped and hidden from the intruders. Reconfigurable techniques can be applied to different blocks of processing elements, so that different image blocks can be watermarked in parallel. Choose the processor size (8- bit or 16-bit or higher bit), which gives less power to implement the above algorithm. This is done by writing a VHDL program for the watermarking algorithm. The power analysis is done by converting the Register Transfer Language (RTL) schematics of codes into transistor level and implementing the circuit in Electronic Design Automation (EDA) tool. The watermarking algorithm was chosen which gives less power and then it is implemented it using FPGA. The procedure is continued same as their previous research work. The algorithm is implemented in XILINX Vertex FPGA. The drawback of this paper is that DWT does not work well at edge singularities and the speed of processing is high, area consumed for processing is high [14].
Zuhair and Yosuf (2010) have proposed FPGA based image security and authentication in digital camera using invisible watermarking technique. The invisible watermarking algorithm used here allows for verification of the image as well as the identity of the carrier and hardware efficient FPGA based invisible watermark module towards the development of the complete digital camera. Input image is applied with DCT. The DCT module calculates the DCT coefficient of the host image and it consists of 2-1D DCT sub module. The 1D row DCT of each 8x8 block was first computed. The column DCT of each block is then carried out. The algorithm inserts a binary image as a watermark into the host image. The watermark is inserted in the perceptually significant components so that the watermarked image is robust with respect to common attacks. After the preprocessing phase, the host image I is divided into 8 × 8 blocks and the DCT (Discrete Cosine Transform) of each block is calculated. For the insertion phase, the DC component c00 and the three low frequency components c00, c10, and c11 are considered for insertion. The watermark (biometric image) is partitioned to the same number of blocks as the host image (passport photo) with a block size of 2×2. If the watermark's binary value in block k is W (k), ij the insertion process is carried out as i, j, and k. The prototype will be implemented in VHDL and synthesized using Xilinx Vertex II technology with an Xc2v500-6fg256 target device. The drawback of this paper is that DCT does not work well at edge singularities and the speed of processing is high, and the area consumed for processing is also high [39].
K. Tamilvanan and Selvakumar (2014) have proposed FPGA implementation of digital watermarking system, Discrete Wavelet Transform (DWT) to authenticate the multimedia image and it can convert the image from spatial domain to frequency domain. The LSB algorithm is to insert the bits of the hidden message into the least significant bits of the pixels. Field Programmable Gate Array (FPGA) technology has become a viable target for the implementation of real time algorithms suited to video image processing applications. This system is developed on Xilinx Spartan3 Field Programmable Gate Array (FPGA) device using Embedded Development Kit (EDK) tools from Xilinx. The least significant bits of the cover-image are altered so that they form the embedded information. The LSB based image watermarking embeds the secret in the least significant bits of pixel values of the cover image (CVR). LSB watermarking can be extended to embed secret information in the least n-bits to increase the capacity of the secret information n/8 the size of the CVR. Random data are embedded in the n least significant bits, where 1 < n < 7. A slight variation of this technique allows for embedding the message in two or more of the least significant bits per byte. This increases the hidden information capacity of the cover-object, but the coverobject is degraded more, and therefore it is more that detectable that the coprocessor Micro blaze is converted into morphological processing architecture using Xilinx platform studio in system C language and then tested in Spartan 3EDK FPGA kit. RS232 cable is used for interfacing the test circuit with PC. The Micro blaze processor is a 32- bit Harvard Reduced Instruction Set Computer (RISC) architecture optimized for implementation in Xilinx FPGAs with separate 32-bit instruction and data buses running at full speed to execute programs and access data from both on-chip and external memory at the same time. An interrupt controller is available for use with the Xilinx Embedded Development Kit (EDK) software tools. The drawback of this paper is same as the previously discussed work [17].
Rosline and Sumalatha (2012) have proposed Fuzzy Based Chaotic and Logistic Method for Digital Watermarking Systems, the Fuzzy based Chaotic and Logistic (FCL) method with three steps. In the step one, the proposed FCL method modifies the original image into transform domain and identifies the pixel location to insert the watermark bits in the difference values between the original image and its reference image based on a novel Fuzzy Logic (FL) method. In the second step, the selected bit positions of step one are shuffled using Arnold cat map, to achieve outspreading of orbits over the entire space, for further authentication and security. In step three, logistic maps are used. On step two, pixels are shuffled to determine the bit positions of host image for watermark embedding. FCL method modifies the original image into transform domain and identifies the pixel location to insert the watermark bits in the difference values between the original image and its reference image based on a Fuzzy Wavelet (FW) method. The discrete wavelet transform decomposes an image into sub bands having a bandwidth approximately equal on a logarithmic scale. The selected bit positions of FW scheme of step one are shuffled using Arnold cat map, to achieve further authentication and security. To shuffle the embedding position of the host image, two dimensional Arnold cat map is employed. Logistic map in step three, to determine in which bit positions of image pixels, the watermark is to be embedded. The drawback of this paper does not have a good PSNR and MSE value [35] .
Maruthu Perumal and Vijayakumar (2012) have proposed sorted pixel value difference on fuzzy watermarking scheme. The watermark is embedded in the sorted pixel locations of fuzzy based wavelet approach by using Pixel Value Difference method. PVD method, determines whether the two consecutive pixels belong to an edge or smooth area by checking out the difference value between two consecutive pixels. If the difference value is large, i.e. the two pixels are located in an edge area; more secret data can be hidden here. On the contrary, if the difference value is small, i.e. the two pixels are located in a smooth area and less secret data can be embedded. Fuzzy Wavelet approach is determined based on the pixel locations, where watermark is embedded. DWT decomposes an image into sub bands having a bandwidth approximately equal on a logarithmic scale. The second step, groups only those pixel coordinates selected by step one based on their pixel values in ascending order. If two or more pixels are having same values, then they will be sorted by row wise positions. The watermark is inserted on the group of pixels in the sorted order by using SPVD method in the second level of wavelet transformed image as indicated in step two. By inserting watermark, the pixel value maybe changed; and the sorted order may also be changed. It does not have a good PSNR and MSE value [36].
Ramezani et al. (2013) have proposed for encrypting the image by using Fuzzy logic algorithm. The algorithm provides security levels and their corresponding processing levels by generating random keys for the encryption/decryption process. This facility is achieved by using fuzzy logic. Fuzzification is the operation of making a crisp quantity Fuzzy. It is simply done by recognizing that many of the quantities that are regarded as crisp and deterministic are actually not deterministic at all; they carry considerable doubt. Defuzzification, for a given input, several IF/THEN rules could be begun at the same time. Each rule will have a different strength because a given input may belong to more than one Fuzzy set, but with different membership values. The procedure follows, loading Image to be encrypted from data store, processing of image using fuzzy Set, and generating the randomly prime number between (1- 256). Storing seven random keys in a matrix (A). Getting Image Width and Image Height. Dividing the image into a set of blocks. Encrypting each 7 bits with the seven keys which stored in matrix (A). Substituting each block in the image by converting the row to the column. Take each 2 vertically adjacent bits from the bottom of the image (b1, b2) and doing XOR between (b1 and b2). Perform XOR between the (b and 256). The test images employed show a positive result. The encryption and decryption algorithm are implemented in VISUAL BASIC.NET and the test of lossless in MATLAB 7.0, in core2duo of 2.66. It does not have a good PSNR and MSE value [40].
Sridevi (2013) has proposed Digital Image Watermarking using Fuzzy Logic approach based on DWT and SVD. A transform domain with the help of fuzzy logic system is used to embed the watermark in the reference image. Fuzzy logic is used to find the alpha value that is used to embed the watermark. Watermark embedding is based on DWT and Singular Value Decomposition (SVD). After decomposing, the cover image into four bands, SVD is applied to one of the frequency bands, and embed the same watermark frequency coefficients of the cover image's blocked DCT based transform domain. Neural networks are used to implement an automated system of creating maximum-strength watermarks. Host image is first decomposed into non-overlapping 8x8 blocks, and the DCT process is performed for each block. Coefficients are then selected for data by modifying the singular values. Quantitative measures like PSNR, NCC are also calculated to test the watermarked image and also extracted watermarks with and without attacks. The singular value decomposition of a rectangular matrix A is a decomposition of the form A=UDVT (2) Where A is an m*n matrix, U, V are ortho-normal matrices. D is a diagonal matrix comprised of singular values of A. D=diag (σ1, σ2, σ3...). The principle of fuzzy logic reaches the human approach in the sense that the variables treated are not binary but of variable linguistic relatives of human language as high contrast, a lot more clearly, very textured, very homogeneous, etc. linguistic variables are processed with rules that refer to some knowledge of system. Perform 1 level DWT to original image. Take LLband and apply one level DWT to LL-band. Calculate directive contrast and threshold for middle and high frequency bands. Initialize high frequency components to zero whose directive contrast are less than the threshold. Perform inverse DWT and obtain reference image. Replace reference image in the selected LL band and apply inverse DWT. A new reference image is obtained. Perform 1 level DWT to original image and this new reference image. Select LL bands of both the images and calculate difference between them. MATLAB platform is used for the proposed watermarking algorithm. It does not have a good PSNR and MSE value [37].
Sameh et al. (2011) have proposed Adaptive image watermarking scheme based on Neural network image watermarking approach based on the Human Visual System (HVS) model and neural network technique. The watermark was inserted into the middle watermark insertion. Human Visual System (HVS) is adopted to further ensure the watermark invisibility. Integrating HVS into watermarking process can assist in satisfying these conflicting requirements. HVS essentially results in the fact that each pixel value of an image can be changed only by a certain amount without making any perceptible difference to the image quality. Artificial neural network is an important embranchment of artificial intelligence field. It has self-learning, self-organizing, association of ideas, blur extend abilities, etc. and has great comparability with human visual system. The selected Neural Network is Back propagation Neural Network. There are three layers including an input layer, hidden layers and an output layer. The four feature components form a feature vector. The u1, u2, u3 and u4 represent the sensitivity value of luminance, frequency, texture, and entropy of respectively. Each u represents one of the input components in NNS algorithm and each pixel generates a corresponding feature vector u. These inputs are then fed to a hidden layer using tan sigmoid activation functions (output in the range (-1 to 1); this is then fed to the output layer. During training samples, information is propagated back through the network and used to update connection weights. It repeats learning many times for every example in the training set until it has minimized the output errors. It does not have a good PSNR and MSE value [20].
Nanda Yalamali and Manjunath (2012) have proposed an Adaptive image watermarking algorithm based on neural networks. Neural network intelligence is used based on characteristics of human visual system. Discrete wavelet transform is used which gives lossless compression. The watermark is embedded by the methods like watermark pretreatment, and neural network recovery. Extraction of an image can be done by watermark post processing & key inverse scrambling transform. DWT can carry more watermarking signal and has a good concealing effect. After the original image has been DWT transformed, it is decomposed into 4 frequency districts which is one low-frequency district (LL) and three frequency districts (LH, HL, HH). The frequency districts of LH, HL and HH respectively represent the level detail, the upright detail and the diagonal detail of the original image. The input image is transformed into first order wavelet transform. The low frequency components are blocked by Discrete Cosine transform. The watermark signal is the training signal to neural network recovery. The Hopfield network is used with neural network training. The watermark signal is coded first 0 of binary image is changed to -1.1 is not changed W' is gotten. W’ is divided in n1×n2 sub-blocks, and the last translated to one dimensional signal training mode is set to P. The pretreatment- watermark signal is scrambled by key times then the watermark signal is embedded in low frequency components of high frequency band. Image containing watermark and watermarked image is gotten by IDCT and IDWT respectively. The software code and supporting tools are based on the leading software in the field: MATLAB and the Image Processing Toolbox from the Math Works. The 256×256 “mountain” diagram is used as experiment image; the 32×32 binary images “Ep” is used as watermark image [22]. It does not have a good PSNR and MSE value.
BibiIsac and Santhi (2011a) have proposed a study on Digital Image and Video Watermarking Schemes using Neural Networks. A neural network represents a highly parallelized dynamic system with a directed graph topology that can receive the output information by means of a reaction of its state on the input actions. Signal function that generates the output signal of the neuron based on its activation is called a signal function. Functions may differ from neuron to neuron within the network; although most networks are field-homogeneous i.e. all neurons within a field or layer have the same signal function. Pattern of connectivity determines the interneuron connection architecture or the graph of the network. Activity aggregation rule, aggregated the activity at a particular neuron (f) Activation rule determines the new activation level of a neuron based on its current activation and its external inputs (g). Learning rule provides a means of modifying correction strengths based on both the external stimuli and the network performance with the aim of improving the network performance. (h) Environment is where the neural network can be viewed as a weighted directed graph in which artificial neurons are nodes and directed weighted edges represent connections between neurons. Local groups of neurons may be connected in either : (a) Feed-forward architecture, the network has no loops. (b) Feedback architecture, loops occur in the network because of feedback Connections. In Digital video watermarking scheme based on 3D-DWT and Artificial neural network, a 3D wavelet transform was performed on each of the selected video shots and then the watermark was embedded in the LL sub-band wavelet coefficients of the low-pass frames. To ensure perceptual invisibility, the coefficient was selected adaptively to embed the watermark and the embedding intensity was adaptively controlled using statistical characteristics such as mean and standard deviation. The watermarking is carried in both spatial domain and frequency domain. The average PSNR values was obtained using the different neural networks for a Blurred Baboon image. The average PSNR values for different methods when they were applied on a Filtered Lena image is determined. The results have been found to be better on using a BPN for the watermarking process [21].
Nallagarla and Varadarajan (2012) have proposed robust digital watermarking scheme with Neural Network and Fuzzy logic approach. Two approaches are compared to embed watermark into the host image using quantization based on Back Propagation Neural Network (BPNN), and Dynamic Fuzzy Inference System (DFIS). The cover image is decomposed up to 3-levels using quantization and DWT. The bitmap is selected as a watermark. The Back Propagation Neural Network is implemented to embed and extract the watermark in one method, while the DFIS is utilized to generate the watermark weighting function to embed & extract the imperceptible watermark in the other method. Digital image watermarking algorithm is presented to insert the watermark in blue plane of the cover image using quantization with BPNN and DFIS in DWT domain. The bitmap is selected as watermark and is resized to 64x64 pixels. The DWT is applied to blue plane of cover image and watermark is embedded in high and middle frequency components. Select the beginning position of watermark using the secret key. Quantize the DWT coefficient T(j+key) by Q as the input to the BPNN, then get the output of BPNN. The drawback of this paper is that it does not have a good PSNR and MSE value [19] .
Sabarinathan et al. (2015) have proposed a Shearlet based watermarking technique. In today’s internet era, fortification of digital gratified during communication is penurious. Watermarking affords the security for digital content. Robustness of such watermarking procedure is quite low. For increasing the robustness, an approach is introduced which is the Neuro fuzzy based watermarking embedding process. Conventional methods having information loss during recovery, easily hacked, lower embedding capacity, requires more memory and power consumption. The proposed scheme binary image is embedded over color image which uses Shearlet and Inverse Shearlet algorithm for preprocessing of an image and Neuro fuzzy algorithm to embed the bits in green plane of an image. Lower memory requirements, and speed of encryption are improved by Neuro fuzzy algorithm [1].
Watermarking will be used to identify and protect copyright ownership. Digital content will be embedded with watermarks depicting metadata identifying the copyright owners.
Digital content is watermarked to indicate that the digital content will not be illegally replicated. Devices capable of replication then detects such watermarks and prevent unauthorized replication of the content.
In an image authentication application, the intent is to detect modifications to the data. The characteristics of the image, such as its edges, are embedded and compared with the current images for differences. A solution to this problem could be borrowed from cryptography, where digital signature has been studied as a message authentication method.
Multi-bit watermarking is used to annotate an image. For example, patient records and imaging details related to a medical image will be carefully inserted into the image. This would not only reduce storage space, but also provides a tight link between the image and its details. Patient privacy is simply controlled by not keeping the sensitive information as clear text in human readable form, and the watermark will be further secured by encryption.
Conventional methods having poor quality of recovered image, it will be easily hacked, it possess lower embedding capacity, requires more memory and power consumption and more hardware resource utilization. In future, the suitable technique selected and rectified the all types of existing problems and also it possess a good PSNR value with high quality recovered image than conventional methods. Also in future, the watermarking and its implementation in FPGA can be extended to the concept of video processing.