Figure 1. Growth Projection for India's Automobile Industry (Kidambi & Mathur, n.d.)
Vehicle theft is a major crime all over the world, usually related with other crimes or just stolen for its spare parts. Car manufactures include immobilizers with the cars to prevent theft. Many anti-theft devices are available in the market, which alerts with an alarm or tracks the stolen vehicle. This paper proposes a novel method that uses facial recognition to prevent vehicle theft. Using this system only authorised person by the owner of the car can operate the car and they have to be registered in the system. The system works by scanning the face of the driver before ignition, and if the user's face is recognised with the images in the system, the car will start. When we switch on the device, it scans the owner's face for the first time. The car may be started after a successful registration. If the face does not match with the images in the system, the system denies access and the buzzer sounds and an alert message is sent to the owner's mobile phone. The image of the unauthorised person will be captured and sent to the vehicle owner. GPS can also be used to locate the vehicle.
The growth of the automobile industry is considered as primary indicator of economic development and stability in any country. The growth is supported by technical innovation and spans over several adjacent sectors in increasing employment. Understanding the growth of the auto sector in other nations provides a road map for emerging countries such as India.
India's car sector ranks sixth in the world by volume and value. According to the Society of Indian Automobile Manufacturers (SIAM), it has expanded 14.4 percent during the last decade. With around 35 automakers, the sector contributes 7% to India's GDP and employs between 7% and 8% of the country's entire workforce (SIAM, n.d.).
Due to the growing middle class and youth population, the two-wheeler market is leading in terms of volume. In addition, the increased investment of businesses in rural areas has also fuelled the expansion of the sector.
India is also a significant vehicle exporter, with significant development prospects in the near future. Additionally, various measures undertaken by the Government of India and major automotive manufacturers in the Indian market are expected to project India as a world leader in the two and four wheeler market by 2020 (SIAM, n.d.).
India's automobile sector has a comparable potential for expansion. China achieved India's present level of production (about 4 million cars) in the middle of 2004, and its GDP has expanded at a rate of 10.7 percent per year since then, while its auto industry has developed at a rate of 19.5 percent per year. As represented in Figure 1, using India's anticipated GDP growth and a similar association between GDP growth and automotive production, the sector might increase at a rate of more than 12% a year until 2020 (Kidambi & Mathur, n.d.).
Figure 1. Growth Projection for India's Automobile Industry (Kidambi & Mathur, n.d.)
As the volume of vehicles grows, theft of vehicles also increases, and thus, there is a need to increase the security within automobiles. Therefore, there is a need for anti-theft systems in automobiles to be installed in the vehicles.
Anti-theft systems are intended to keep the car safe from theft. These systems are in a continual state of evolution. Essentially, they function by interrupting an electrical circuit, preventing electricity from going to the automobile, causing it to not start instantly.
This device is installed in a vehicle that minimises the likelihood of the vehicle being stolen or it enhances the likelihood of retrieving a stolen vehicle. Global Positioning Systems (GPS), local alarms, and immobilizers are examples of such devices.
According to the National Crime Records Bureau's newest data, at least 95 automobiles were stolen per day in the national capital last year, the most across all states and union territories of India, as shown in Figure 2 (Hindustan Times, 2021).
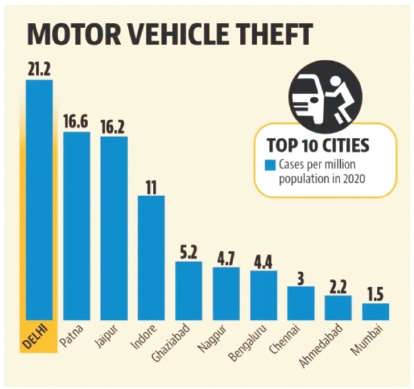
Figure 2. Vehicle Theft Cases in India (Hindustan Times, 2021)
Today, there are numerous types of automobile security systems available. Each of these systems has several advantages and disadvantages; for example, a vehicle alarm and a car tracker often function well together. Car alarms remain a highly popular choice, and they are often included in the majority of automobiles manufactured in recent years. These can be passive signalling devices that automatically turn on when the ignition is turned off and the last door is closed. Additionally, there are active devices that require activation or deactivation by pressing a button on the device. As can be seen, the numerous kinds of automobile security systems each have their own set of advantages and disadvantages. To provide the finest protection, it is important to consider all of the available choices and choose the ones that work best for the vehicle.
The following are some of the benefits of using face recognition for vehicle security:
The goal of a vehicle security system is to prevent vehicle theft and assure vehicle safety by avoiding theft methods. Face recognition system that authenticates a user as an authorised individual to have access to the ignition system is one degree of assuring driving authenticity. When a human is detected in a parked car, the microprocessorbased control system installed inside the vehicle employs a GPS receiver, a GSM modem, and records an image from the camera. Face detection and recognition is accomplished using appropriate algorithm that overcomes position and lighting restrictions. The recognised picture is compared with the images of authorised user for that particular vehicle in the database. The technology enables the car to be operated if the two images are matched. If the image is not recognised, the system sends an MMS with the user's face and GPS coordinates to the owner. Hameed et al. (2011) focused on MMS and database technologies with fast reaction times in their research. This aids the owner in making decisions concerning vehicle control. The owner determines whether or not to allow the individual to drive the car and instructs the system accordingly.
With increasing smart gadgets equipped with the latest internet technologies such as IPv6, LTE, and 5G, intelligence is being incorporated into the numerous devices having applications in areas such as health, agriculture, transportation, and the energy industries (Agiwal et al., 2018). The goal of embedding intelligence in a machine, achieved through the use of an applicationspecific embedded microcontroller, sensor shields integrated with signal conditioning and signal processing circuitry, communication modules, and a smart power management system, is to allow the machine to communicate with other machines equipped with similar facilities, known As Machine-2-Machine (M2M) communication. The Internet of Things (IoT) provides the flexibility to access devices via the internet utilising Device- 2-Device (D2D), Device-2-Server (D2S), Server-2-Device (S2D), and Server-2-Server (S2S) communication protocols (Patel et al., 2021; Ru, 2013; Sehgal et al., 2012).
In recent years, a great deal of attention has been paid to retrieving a stolen or lost vehicle, where GSM communications from the owner may be used to switch off the car as well as to determine its current position by using a triangulation algorithm from the closest base station (Ganesh et al., 2011). It is common for these systems to be referred to as Vehicle Monitoring Systems, and they are important in maintaining control over and tracking the position of a stolen vehicle.
Guo et al., (2009), in their Vehicle Tracking System, enabled the owner to remotely halt the vehicle. In addition, an auto tamper detection technology has been included, which disables the vehicle in the event of tampering with the security system of the vehicle. The car immobilisation system is the second most significant security element that has been implemented in recent years, behind the intrusion detection system.
The Internet of Things (IoT) is an example of connecting the digital and physical worlds. The Internet of Things (IoT) idea has aided in the development of a more intelligent and connected world by enabling communication between items and humans. With IoT, daily communication is getting more informational, everyday processing is becoming more intelligent, and everyday gadgets are growing smarter, leading to a vision of communications that can take place anytime, anywhere, and about anything in any opportunistic way (Feki et al., 2013). After global mobile accessibility and the worldwide web, the Internet of Things (IoT) is considered to be the most inventive shift of our generation. Real-time localisation, short-range wireless communications, RFID, and sensor networks are just a few of the essential technologies that are often employed in the Internet of Things.
The analysis of relevant works shows that the vehicle security systems introduced in recent years have been mostly focusing on increasing the capabilities of remotely controlling of automobiles. Using RFID in the security solutions, on the other hand, have gained widespread adoption in recent years. In the vehicle anti-theft system by Sasi and Nair (2013), the use of biometrics had been considered for both tracking the vehicle and as well as a method to implement the anti-theft function.
The Internet of Things (IoT) conducts cognitive operations to prevent car theft. There have been several researchers working on car security systems to give the best methods not only to prevent theft of vehicle contents but also locate the lost vehicles, as well as for the personal safety of people travelling in a vehicle. Several works that implemented car security systems had used biometric authentication techniques such as eye, fingerprint, and face recognition, among others, to protect vehicles
Sehgal et al. (2016) proposed an embedded system for anti-theft and driver surveillance. The driver can gain entry into the car using of biometric authentication. According to the authors, the system makes use of the LBPH algorithm for facial recognition. Additionally, they demonstrated that the technique was straightforward and produced superior outcomes both under low light and high light conditions.
In the vehicle security system by Nandakumar et al., (2014), a microprocessor-based control system was used for image processing by conducting a real-time facial detection and recognition. The infrared sensor connected to the driver's seat of the vehicle triggers the concealed camera mounted in the suitable location inside the vehicle as the individual enters the parked car breaching the current security mechanisms. The face of the individual is recognised using the Viola-Jones algorithm as soon as the image is collected from the active camera. The extracted face is identified using the improved Linear Discriminant Analysis (LDA) technique, which discriminates many of the characteristics rather than searching for a precise pattern based on Euclidean distance and is also trustworthy enough to be employed with huge datasets. The process of authorisation is based on setting the threshold value and comparing it with the Euclidean distance over which the user is not authorised to use the vehicle. Through the running GSM modem, the face of the person classed as unknown is delivered as an MMS to the owner's mobile phone. The owner can issue instruction to control the vehicle after receiving the information, and if unauthorised person is in the driver seat, the system will cut off the fuel to the vehicle via the relay. This would be useful for verifying a person's identity in a variety of settings and for ensuring vehicle security.
This section explains the concept of VSS−IoT presented by Elngar and Kayed (2020). The primary goal of the existing system is to identify and distinguish the faces of professional thieves. Furthermore, this system has a high cost, and increasing complexity, and while lacks user-friendliness, which is a crucial factor to consider when implementing an integrated real-time vehicle security system. The system must first verify the identity of the authorised driver before granting the access into the vehicle system.
Figure 3 explains the flow chart of the existing system. The system uses Raspberry Pi 3 Model B+ controller, PIR motion sensor, USB 3G Modem, USB camera module, Micro-SD card, Servo Motor, power supply, owner mobile device and police workstation. The components are wired and wirelessly linked, with the police workstation and real owner terminals being wirelessly connected to the Raspberry Pi 3 Model B+ controller.
Figure 3. Flowchart of the Existing System (Elngar & Kayed, 2020)
Model B+ Raspberry Pi 3 offers several advantages over other models. It features a high number of USB ports as Raspberry Pi OS, which has excellent hardware integration and a graphical user interface with programming tools.
The Internet connection is required for this project for the Raspberry Pi 3 Model B+ to interact with the IoT protocols. The design shows that the IP address of the Raspberry Pi 3 Model B+ has to be changed from static to dynamic. This was accomplished by using the command to modify the network interfaces file.
Some key objectives considered with the newly proposed system are:
Figure 4 shows the block diagram of the proposed system. It has a low-power CPU with facial recognition ability. As a result, depending on the camera, the suggested system uses 76 percent of the CPU and 53.5 percent of the RAM, respectively.
This is an advanced system which can be used in a variety of vehicles. It is now quite easy to produce duplicate car keys, and the use of such keys raises the danger of vehicle theft. This paper proposes a solution to prevent vehicle theft using duplicate keys. The system employs facial recognition technology to identify approved vehicle users, and only authorised users are permitted to operate the car. The system employs a Raspberry Pi kit and includes a camera, a 24 x 4 LCD, a motor, and a buzzer alert. When we switch on the system authority, which has three options: registration, start, and clean data, it scans the owner's face first. The car may be started after a successful registration. The owner must use the reverse command to bring the car to a halt. When an unauthorized user attempts to use the automobile, the system the system refuses the request, and the buzzer sounds. The system architecture of the intelligent automobile anti-theft unit is explained in Figure 5.
The microprocessor, which incorporates an image processing unit, does the face detection and authorises the individual as shown in Figure 6. The image processing procedure is divided into two stages:
Figure 6. Image Processing based Authorization (Nandakumar et al., 2014)
The Viola-Jones method (Viola & Jones, 2001), which successfully leverages cascade object detection, is used to identify the face in the captured picture.
The face of the obtained picture is detected by the cascade detector, and the face area is removed.
The database of the authentication based security system saves the facial photographs of authorised individuals in various situations. The facial photos are upgraded by normalising them during acquisition to eliminate undesirable information caused by lighting limitations and then updated in the database. Face recognition must now be conducted on the faces that have been discovered.
Face recognition may be accomplished using featurebased or model-based methods. In real-time security systems, feature-based algorithms are often utilised. In terms of extracting features for recognition, the Principal Component Analysis (PCA) and Linear Discriminant Analysis (LDA) methods are effective. Both techniques are compared (Hese & Banwaskar, 2013), and they are determined to have comparable features, however, when large training sets are involved in recognition, Linear Discriminant Analysis (LDA) surpasses Principal Component Analysis (PCA). Furthermore, by generating the intra-class and inter-class scatter matrices, LDA effectively discriminates the majority of the information included in the picture.
The LDA method is used to do recognition in the vehicle security system using a database of normalised facial photos. LDA extracts features from recorded photos in the database, referred to as training images, and a face image acquired by the system camera, referred to as the test image. The test picture is compared to the database images, and the algorithm's classifier uses the Euclidean distance and the threshold value to determine if the image is known or unknown.
The Euclidean distance between the matching weights of features is determined, and the picture with the smallest distance is the best match for the test image.
When the Euclidean distance is less than the threshold value, the individual is categorised as known or authorised; when the distance value exceeds the threshold, the person is classified as unknown or unauthorised. Figure 6 depicts the stages involved in the image processing method and permission.
When the image detection and image recognition unit identifies the unauthorized face then it captures the face through the camera and sends the alert to the owner and sends the image to the owner's mail. GPS updates the location of the vehicle to the owner.
The Raspberry Pi Foundation launched the Compute Module in 2014, which is a reduced version of the famous Raspberry Pi Model B board is shown in Figure 7. The Compute Module has gone through many generations since then, including the 3+ with restricted feature set and same size. Compute Module 4, the fourth version having some size comparisons with the previous-generation Compute Module 3+, various other popular Pi models, including an SD and micro-SD card.
The Compute Module 4 is essentially a Raspberry Pi 4 Model B that has had all of its ports removed. Instead of ports, the Compute Module's specific board-to-board connections are used to connect it with another board. The Compute module has more features when compared with the earlier versions.

Figure 7. Raspberry Pi 4 Module
There are now thirty-two distinct Compute Module varieties to pick from, depending on whether you want integrated Wi-Fi or not, eMMC Storage or 1, 2, 4, or even eight gigabytes of RAM!
A microSD memory card will be placed into the Raspberry Pi 4 Model B to save the Python code written on the board.
Raspberry Pi board is connected with accessory devices and other circuit boards using jumper cables.
The Global Positioning System (GPS) is a global radio navigation system comprised of 24 satellites and their associated ground stations as depicted in Figure 8. GPS is increasingly being integrated into automobiles, boats, aircraft, construction equipment, film production equipment, agricultural machinery, and even laptop computers.
Figure 8. Global Positioning System
Python laid its foundation in the late 1980s and has evolved as preferred language for programming IoT devices. The reason for using Python is as follows:
Python is capable of Exception Handling and can be interfaced efficiently with Raspberry Pi OS.
Python code snippets from the programme developed for anti-theft system proposed in this paper are listed below:
# USAGE
# python pi_face_recognition.py
--cascade haarcascade_frontalface_default.xml
--encodings encodings.pickle
# import the necessary packages
from imutils.video import VideoStream
from imutils.video import FPS
import face_recognition
import argparse
import imutils
import pickle
import time
import cv2
import pynmea2
import RPi.GPIO as GPIO
# Import Raspberry Pi GPIO library
from time import sleep
# Import the sleep function from the time module
import smtplib,ssl
from email.mime.multipart import MIMEMultipart
from email.mime.base
from email.utils import formatdate
from email import encoders
import paho.mqtt.client as mqtt
def on_connect(client, userdata, flags, rc):
print(f"Connected with result code {rc}")
client = mqtt.Client()
client.on_connect = on_connect
client.connect("broker.emqx.io", 1883, 60)
GPIO.setwarnings(False)
# Ignore warning for now
GPIO.setmode(GPIO.BOARD)
# Use physical pin numbering
GPIO.setup(40, GPIO.OUT, initial=GPIO.LOW)
The overall implementation in the system is shown in Figure 9. This gadget is quite useful in providing optimum safety to the vehicle and preventing theft by observing all of the output. The main purpose of this system is facial recognition, which recognises the face of a vehicle's authorised person and allows to start the vehicle. If an unauthorised person gets into the car, it reports the owner about the authorized person by message as shown in Figure 10 and sends the photo through the email. There is also an IoT notification system that sends a message to the vehicle's owner about the location of the vehicle (Figure 11). The message or notice will be presented to the phone using IoT, such as where the car is travelling.

Figure 9. Overall Implementation of the System
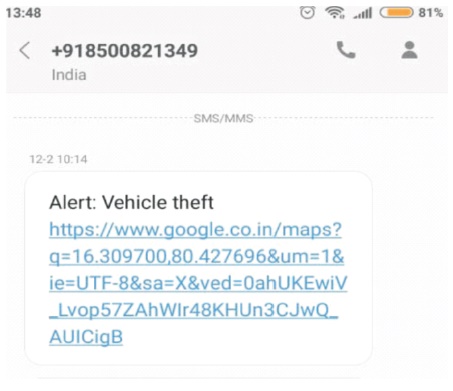
Figure 10. Alert Message Sent to the Owner
The trial of the proposed system revealed a high level of accuracy. IoT improves sensitivity to 97.7%, which is critical for real-time applications.
Furthermore, the suggested solution took less time in various lighting situations, as seen by the results.
This system is capable of preventing theft by an unauthorised person. It may contribute to the vehicle's safety. According to main and previous testing findings, the suggested systems acquired the highest accuracy rate when compared to other existing systems.
GPS can provide a far more precise position than earlier technologies. The suggested system's security technology is incapable of locating an unauthorised user. The integration uses current technologies and embedded system. Additionally, the suggested system works faster when compared to previous systems. Additionally, the findings indicated that the cameras' pixel size was 720p. It provided greater memory space and CPU use than the others by more than 65 percent. As a result of its cheap cost and good performance, it is an excellent candidate for enhancing the vehicle sector's security.