Figure 1. Steps in Anti-Spoofing Method
Face recognition is the second most widely used biometric approach after fingerprint. The applications of Face recognition are widely accepted and finding their space either at an organization or individual level due its adaptability among the people. But FR systems are vulnerable to spoofing attacks made by non-real human faces. Liveness detection is required for a secure program to protect against such spoofing. In this work, face liveness detection approaches are categorized based on types of techniques used for liveness detection. This classification helps in understanding various spoof attack scenarios and their relation to the formed solutions. A review of the previous works respect to face liveness detection is presented. The main objective is to outline the future development of a new and more secure liveness detection approach for face.
Now-a-days, the security of private data has become an essential requirement. For identifying someone's identity Knowledge- based methods (e.g., password, PIN, secret question) and token-based methods (e.g., smart cards, token code) are the majority used methods. However, these methods concern what the user knows, rather than who the user is. As an alternative, biometric systems verify the identity of a person requesting for accessing certain services. In biometrics, Human body is the password, so there is no need to remember any passwords or key. Also, biometric solves the problem of stolen tokens, as it cannot be stolen. Biometric verifies the identity of a person based on one or more physiological and behavioral characteristics. The widely used physical biometric traits are fingerprint, face, iris, ear, retina, hand geometry, palm print, DNA etc., whereas behavioral biometric traits include signature, speech patterns, gait, keystrokes etc ( Ito et al., 2017; Kähm & Damer, 2012). FR is one of the widely used physiological biometric approaches. A Face recognition system recognizes an individual from a digital image or a video frame from a video source. FR has significant advantages over other biometric systems such as irises and fingerprints; it is a more user-friendly, cost- effective and convenient solution ( Kähm & Damer, 2012). Also, face is the second most largely deployed biometric in the world level after fingerprint ( Matthew & Anderson, 2014; Sharma & Dahiya, 2014). FR systems can be used in a number of applications such as crime prevention, mass identification, video surveillance, person verification, and similar security activities. Even though the biometric adds a supplementary layer of protection than traditional methods by secure identification and authentication, they are still at risk of attacks ( Kumar et al., 2017), Anjos et al. (2013).
There are diverse levels of spoofing attacks such as placing fake biometrics on a sensor, attacking the enrollment database, corrupting the matcher and decision module or attacking the application ( Kähm & Damer, 2012).
After the success of the FR system, it is really annoying that FR is susceptible to fake face attacks. As biometric traits are not confidential, it is easily available to anyone. By means of cameras and cellular phones, or very soon social media on the Internet, people's faces can be obtained effortlessly. Additionally, with the aid of present technology, obtained face images can be represented with various mediums like high-quality photographs, LCD display, or 3D mask ( Galbally et al., 2014). Therefore, it is hard to differentiate fake faces from actual ones for the face recognition system, which is a major security issue.
In a spoofing attack, an attacker tries to gain illegal access to the service by providing forged biometric statistics of legitimate users to the authentication system. According to a recent analysis, nearly 80% of the spoofing attempts successfully identified as valid users in the FR system. This vulnerability creates the need for verifying the authenticity of the biometric data before it processes for verification or recognition ( Määttä et al., 2012).
Generally, there are three types of attacks carried out to spoof the sensor:
Because a person's facial image is usually readily available to the public, a print attack or photo attack has become an inexpensive and easy cheat approach. For example, face image can be obtained from the web, captured unknowingly by a camera etc. The imposter can fool the authentication system by rotating, shifting and bending the photo in front of the camera space a live person does. So for the FR system, it is difficult to detect whether an input face image is from a live person or from a photograph.
Another big threat is replay spoofing. Video can also be obtained from the same source as the photo of a real person can be obtained. Because video is very similar to a live person as it has many physiological activities such as head movement, facial expression, blinking etc (Pan et al., 2008). It is more difficult to prevent the FR system from replay attacks.
The third threat of a spoof attack is a synthesis attack or a 3D model attack. 3D masks have 3D information on the face, however, it does not have physiological information; it is rigid. 3D information like depth is used to fool the FR system. An imposter somehow used rubber, clay or plastic etc., to construct the 3D model of a genuine person. The photo and video attacks are commonly used spoofing ways to attack face recognition systems because of its ease of availability
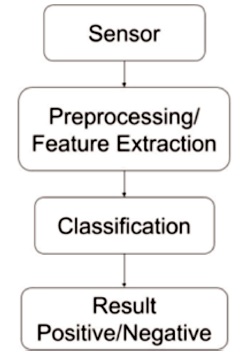
Anti spoofing process ensures that only live biometric samples will be processed for biometric identifications, whereas the non live samples are automatically rejected. The basic components of a face anti-spoofing system are shown in Figure 1.

Figure 1. Steps in Anti-Spoofing Method
In the first step, a user need to present the face to the sensor, which is a camera. The preprocessing step involves the elimination of noise from the captured image and to improve the feature of the image. Diverse methods used for preprocessing are blurring, sharpening, edge detection or scaling etc. Later, the preprocessed samples are forwarded to the feature extraction section, where the most important features of the face can be extracted to distinguish the live feature set from the spoofed feature set ( Parveen et al., 2015). Some of the techniques of feature extraction are Local Binary Patterns (LBP), correlation coefficient, discriminative analysis, etc.
In the anti-spoofing process, the spoofing detection of the presented face is evaluated by matching the queried feature vectors aligned with those stored in the record composed during the training phase. This procedure produces a binary answer that states the type of the input image, as either accepted as live or discarded as a spoof sample ( Parveen et al., 2015). The general use for face liveness detection are SVM classifiers, binary classifiers, Hamming distance, Manhattan distance, weighted fusion, difference degree calculation, etc.
After only live faces are supplied to the FR system, a fake face does not gain access. The literature term “antispoofing” refers to “liveness detection”. With the help of liveness detection, face biometrics are more secure and the performance of a biometric system can be improved significantly. There are lots of anti-spoofing techniques that exist with their specific advantages and disadvantages ( Peng & Chan, 2014). Indeed, there is still a need to develop one general approach that works with the existing system and with a wide variety of databases.
Galbally et al. (2014) presented a technique to identify spoofing attacks, which are broadly categorized into sensor level, feature level and score level. In most existing work, authors classify the anti-spoofing techniques based on liveness clues, motion analysis and texture analysis. We classified anti-spoofing methods broadly as follows:
An additional device has been included in the system for identifying particular properties of a living trait. In the literature, device-specific approaches are typically referred by the phrase of hardware-based techniques. In general, hardware-based approach measures: 1) natural properties of a live body, such as physical properties (e.g., density or elasticity), electrical properties (e.g., capacitance, resistance or permittivity), spectral properties (e.g., reflectance and absorbance at given wavelengths) and visual properties (e.g., color and opacity); 2) spontaneous signals of a live body which can be recognized for the anxious system. For example, pulse, blood pressure, perspiration, pupillary unrest (hippos), brain wave signals (EEG) and electric heart signals; 3) uncontrolled responses or reaction reflections to an external signal. Examples of such methods can be the pupil abbreviation after alighting occurrence or the head movement following a random pathway firm by the system ( Galbally et al., 2014).
Killioğlu et al. (2017) developed a pupil direction observing system for anti-spoofing in face recognition systems using basic hardware equipment. Firstly, the eye area is being extracted from the real-time camera using the Haar-Cascade Classifier with specially trained classifiers for eye region detection. The feature points have been extracted and traced for minimizing the head movements of a person and getting a stable eye region by using the Kanade-Lucas-Tomasi (KLT) algorithm. Pupils are extracted from the eye area, and then the proposed spoofing algorithm selects a random direction and sends a signal to Arduino to activate the LED of that selected direction on a square frame with a total of eight LEDs for each direction. After the chosen LED has been activated, eye direction is observed whether pupil direction and LED's position matches. This method depends on the uncontrolled responses of the user.
However, these methods require extra hardware or sensor. Such approaches cannot be utilized with the existing FR system and are expensive compared to others.
Despite the effectiveness of hardware-based methods, there is a sufficient work proposed in the challengeresponse approaches system, ( Tirunagari et al., 2015) called intrusive methods. Intrusive methods are those which involve user collaboration. These methods are based on the fact that true people can respond to certain challenges. Challenges are those that FR system gives certain tasks to perform, such as specific head movement, eye blinking, hand rising or may some words to speak. Speaking tasks require extra voice recorder with the system, which may include in Hardware-based methods but speaking is on the whole challenge to act in response.
Ali & et al. (2012), designed the visual stimulus to direct the gaze of the user to a sets of collinear points on the screen. The user is required to follow a visual animation of a moving object on a display screen while his/her gaze is measured. Features based on the measured collinearity of the observed gaze are then used to discriminate between live attempts at responding to this challenge.
Asaduzzaman et al. (2015) exploited the eye blinking as a password. Module was developed, that sets the number of blinks as a password. The user responds to the number of times with eye blinking for gaining access.
Drawback of these methods is, it requires heavy interaction from the users and may be unsuccessful if only very vague facial motion exists. Due to such limitations, challenge- response approaches do not gain too much attention in spoof detection application. It is useful in the application developed for capturing user response while human device interaction is taking place.
Now-a-days the need for non-intrusive and without extra hardware techniques are gaining too much attention in anti-spoofing. Anti-spoofing techniques are broadly categorized as Static and Dynamic analysis. ( Galbally et al., 2014; Kollreider et al., 2008; Yan et al., 2012) Static methods are focused on the analysis of a particular one static image while dynamic methods are carried out on video. In general static techniques are more rapid than their dynamic counterpart and, therefore, more suitable for the user ( Luan et al., 2017; Yeh & Chang, 2018).
Dynamic anti-spoofing schemes use a temporal face sequence of sufficient duration. It tries to detect, as humans do, facial physiological clues like blinks, mouth movements and changes in facial expression. Furthermore, dynamic approaches are those which utilize consecutive two frames or any two or more frames from input video for differentiating motion patterns of live and fake frames. It can be divided into two groups as mentioned in Figure 2; They are Liveness clues and Motion analysis.
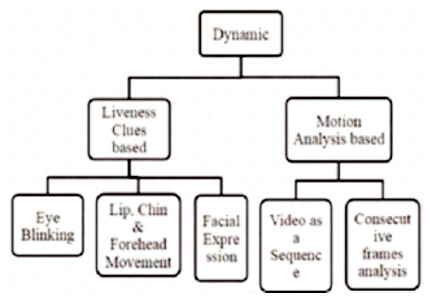
Figure 2. Classification of Dynamic Approaches
Liveness clues are nature clues that are carried out by the human body and are not copied to photograph such as eye blink, mouth movement and head rotation and facial expression ( Królak & Strumiłło, 2012; Singh et al., 2014). Thus, face photo attacks can be detected through many state of the art algorithms that recognize physiological clues of vitality. In particular, these algorithms are based on the trajectory analysis of particular face segments.
Some researchers detected the study of humans blink once every 2-4 seconds and anticipated an eye blinkbased anti-spoofing method ( Pan et al., 2007; Sun et al., 2007). Normally, the blinking rate of human beings is around 15 to 30 eye blinks per minute that is human blinks once every 2 to 3 seconds and blink time is about 205 milliseconds. So a generic camera can easily capture the face video with more than 15 frames per second, so the interval between frames is not more than 70 milliseconds. Then the camera can capture two or more frames at the time of face looking in the camera. The authors define a three-state set for eyes, Q = {a: open, g :close, ß: ambiguous}. Thus, a typical blink activity can be described as a state change pattern of a → ß → g → ß → a. HMM produces observations to produce joint probability tractably assuming that there is an underlying sequence of states drawn from a finite state set. Eye blinking behaviors modeled in an undirected Conditional Random Field framework.
A new approach for the detection of eye blink is carried by ( Li, 2008). It is based on the observation of the liveness, the edges along some scales and orientations vary homo-responsively to the behavior of eye blink. By analyzing the varying tendency of multi-scale and multiorientation Gabor Response Waves (GRW), five key Gabor response waves (KGRWs) are selected from the wave set since they are considered most homo- responsive to the behavior of eye blink. They intercept the probable blinking signals from KGRWs and reshape them into pulses to improve the ratio of signal to noise (SNR). At last, the parameter of the ratio of the union to the intersection of the reshaped pulses (RUI) is proposed. Its value determines the extent of an eye blink. Compared to previous approaches, this algorithm is thought to be more accurate for fusing multiple weak detectors. Moreover, it can detect weak signals of eye blink and quantitatively estimate the extent of an eye blink.
Next, the liveness detection using variations in facial eye, lip, chin and forehead movements are evaluated in Nalinakshi et al. (2013). The proposed system is implemented by integrating a standard algorithm like Voila Jones for face detection, LBP ( Chingovska et al., 2012) method for feature extraction, Manhattan Distance classifier for matching. The developed system is tested for 60 persons from the Indian database. The developed system is also tested for 50 persons from their own database (viz. real-time database). The accuracy of 86.3% and for the authenticated users the accuracy of liveness detection around 88% is achieved.
Krystyna Malik and Bogdan Smolka, recently adopted a new direction. Malik and Smolka (2014), introduced a method utilizing the technique of Local Binary Patterns (LBP), which enables to build off a descriptor capturing the features of the current eye state. In the initial step, the histogram of LBP describing the open eye is constructed and then it serves as a template, which is compared with the histogram of the LBP of subsequent frames. The eye blinks are detected as sharp peaks of the dissimilarity between the template and the histogram of the current frame. The efficiency of the proposed eye blink detector has been compared with the state-of-the-art approaches using two video databases.
As all these methods work well with Print attack attempts with good lighting conditions. But as a video containing all vitality clues, these methods fail completely when Replay attack occurs.
Motion analysis tries to identify some correlation between the two frames. This hypothesis is based on the concept that the spoofing media are ordinarily flat 2D planes similitude to the 3D composition of a real face. Furthermore, motions in spoofing attacks are rigid whereas aggregations of both rigid and non-rigid motions subsist in real-access activity.
Kollreider et al. (2005; 2009) proposed a method based on lightweight optical flow, which is applicable in the face motion estimation based on the structure of a tensor. The basic idea was a 3D face creates a special 2D motion which was high in central face parts, For example, nose has been analyzed for outermost face regions, Ideally, the outermost and the innermost parts are in opposite directions. For this scheme liveness of the face was evaluated by the trajectory of several face parts using the optical flow of lines. Similarly, Bao et al. (2009) presented a method used in an optical flow field. It analyzes the difference and property of optical flow generated from 3D substance and 2D planes. Four fundamental movements of the optical flow field are translation, rotation, moving and swing. In general, the swing of the 2D plan is diverse from the 3D face.
Anjos et al. (2013) proposed to recognize the spoofing attacks based on the correlation between optical flows in two regions. According to the authors, the intensity of the relative motion between the face region and the background can be used as a clue to distinguish valid access for attempted attacks. More recently, Tirunagari et al. (2015) proposed the use of the dynamic mode decomposition (DMD) method for modeling dynamic information of the video content, such as blinking eyes, moving lips, and facial dynamics. The authors proposed a classification pipeline consisting of DMD, local binary patterns and SVMs. The DMD approach is used to represent the temporal information of an image sequence as a single image ( Lee et al., 2013).
Static approaches are based on the basic idea that a certain loss of information occurs and also abnormal noise is introduced during the built-up process of attack. Loosely we can decompose available static techniques into attack specific clues and texture descriptors as shown in Figure 3.
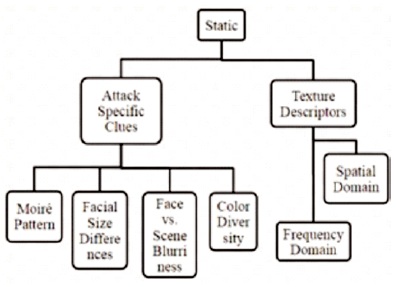
Figure 3. Classification of Static Approaches
The very first algorithm was proposed by Li et al. (2004) based on the analysis of the Fourier spectra of a single face image or face image sequences. The size of the fake images is usually different than that of a live face. If fake faces are held in front of the camera, many details of the image may be lost. This all brings a great difference between live face and fake face image by using 2D Fourier spectra. HFD (High-frequency Descriptor) is used to analyze the texture of images.
Kim et al. (2013) proposes a novel method using one of the camera features like variable focusing. By controlling a camera, images focusing on facial components such as a nose and ears were captured. In the case of real faces, focused regions are clear and others are blurred due to depth information. In contrast, there a little difference between images taken in different focuses from a printed copy of a face, because they are not solid. Further to this work, Yang, (2014) has proposed an approach by focusing on the nose and the background of two images taken from the camera. If the images are displayed by a photograph or tablet, both images will be similar and the object is classified as an imposter. The limitation of these methods is the quality of the image affects the performance of the method significantly ( Albu, 2015).
The method DHFD, based on HFD is proposed in Peng and Chan (2014) to carry out the face liveness detection. Rather than calculating the energy of high-frequency components of a single captured image, a difference of high-frequency components energy between images with and without additional illumination was evaluated. The extra flashlight raises the energy of high-frequency components of a real face by exposing more details of the hair and skin and lowers it by causing a glisten on the planar surface. The experimental results show that the proposed method far outperforms the original HFD method on a dataset attacked by a high-resolution screen, which also demonstrates the robustness of the method.
Most simple and efficient work presented by Galbally and Marcel (2014) based on general image quality. Feature space of 14 general image quality measures are combined with a simple LDA classifier to detect real and fake access attempts. The approach is tested with a public domain database. Pinto et al. (2015), highlighted the fact that there is a significant increase in the lowfrequency components due to the blurring effect added during the recapture process of the face. Garcia and Queiroz (2015) presented the advantage of the noise and artifacts contained on such fake biometric samples, which can be referred to as a noise signature. Fourier analysis of the noise signature was carried out to capture the information encoded in the frequency, phase and amplitude of the component sinusoids. Fourier spectrum is used to quantify the artifacts such as Blurring Artifact, Flickering Effect and Moiré Pattern. Instead of these, Wen et al. (2015) studied only Moire patterns for identifying spoofing. Moiré patterns are rising due to the overlap of the digital grids. The conditions under which these patterns arise are first described, and their detection is proposed based on peak detection in the frequency domain. Results are goods for an image database of facial shots under several conditions when the condition holds.
Kim et al. (2015) proposed an efficient face spoof detection algorithm based on Image Distortion Analysis (IDA). Four different features (specular reflection, blurriness, chromatic moment, and color diversity) are extracted to form the IDA feature vector. An ensemble classifier, consisting of multiple SVM classifiers trained for different face spoof attacks (e.g., the printed photo and replayed video), is used to distinguish between genuine and spoof faces. The proposed approach is extended to multi-frame face spoof detection in videos using a votingbased scheme.
New era proposed by Alotaibi and Mahmood (2016) based on the light on a live face is quite randomly reflected because of the 3D structures (e.g., nose, lip, etc.), whereas the reflectance of the light on a 2D fake face is relatively uniform. This leads to a difference in the illumination effects of captured images of live and fake faces. In order to estimate this difference in a single image, the authors are exploiting the concept of diffusion. This is because the illumination energies on a 2D surface are evenly distributed and thus are expected to diffuse slowly, whereas those on a live face tend to move faster because of their nonuniformity. In particular, it was an attempt to model this diffusion by allowing for the total variation (TV) flow scheme, and extract anti-spoofing features based on the local patterns of the diffusion speed values computed at each pixel position. An AOSbased schema with a large time step size to generate the speed-diffused image has been exploited in Boulkenafet et al. (2016). Applying a large time step parameter helps in extracting the sharp edges and texture features in the input image. Fake face images had fewer sharp edges and flattened surfaces around the eyes, nose, lips and cheek regions when we recaptured the input video twice, which destroys the sharp edges and changes the pixel locations. In contrast, the real face frame had sharp edges and rounded surfaces, especially around the nose and lips. A specialized deep convolutional network was used.
Similarly, Boulkenafet et al. (2015) and Garud and Agrwal (2016) investigated RGB, HSV and YCbCr, provide useful face representations for describing the olor texture differences between genuine faces and fake ones. The effectiveness of the different color character representations was studied by solution color LBP features from the individual image channels. Excellent results are reported on CASIA-FADA, Replay Attack DB and MSU MFSD with HSV+YCbCr pipeline. Furthermore, the proposed approach has very promising generalization capabilities.
Approaches that use any texture descriptor to differentiate fake and real images are known as texture descriptor type. Such an algorithm was proposed in Määttä et al. (2011) wherein description was obtained with the combination of feature descriptors focusing on different image characteristics, such as shape, color, and texture. To take advantage of the rich information provided by multiple feature descriptors, the antispoofing proposed a solution, which integrates feature descriptors based on histogram of oriented gradients (HOG), color frequency (CF), gray level co-occurrence matrix (GLCM), and histograms of shear let coefficients (HSC) with a weighting scheme based on partial least squares (PLS) ( Schwartz et al., 2011). After the evaluation of individual classifiers and combination of all descriptor, SVM is employed for the classification.
Yang et al. (2013) worked on a component-based face coding approach for liveness detection. First, the author locates the components of the face then coding the low-level features respectively for all the components. Secondly, high-level face representation is generated by pooling the codes with weights derived from the Fisher criterion and concatenating histograms from all components. The proposed framework makes good use of micro differences between genuine faces and fake faces ( Housam et al., 201419). Similarly, in the previous method of de Freitas Pereira et al. (2014), the LGS (Local Graph Structure) is used as a facial descriptor for liveness detection. It calculates several local descriptors from divided face regions by applying LGS in each region to extract the texture information. Results from each region have been concatenated to form the feature vector. The reason is that local features are better than the holistic representation.
Kose and Dugelay (2012) combined three different LBP configurations: LBP (8,2), LBP (16,2), and LBP (8,1) in a normalized face image and trained a support vector machine (SVM) classifier to discriminate real and fake faces. Evaluations carried out with NUAA Photograph Impostor Database, showed a good discrimination power (2.9% in EER). And in Yang et al. (2013), a rotation- invariant LBP Variance (LBPV) based method together with a preprocessing step of Difference of Gaussian (DoG) filtering is used to detect the photograph spoofing. The authors adopted the LBP-based spatiotemporal representation. Furthermore Arashloo et al. (2015) authors introduced a compact face liveness description that combines facial appearance and dynamics using spatiotemporal (dynamic texture) extensions of the highly popular local binary pattern (LBP) approach. More Specifically, local binary patterns from three orthogonal planes (LBP-TOP) were considered. Face liveness description was extracted from an average of LBP-TOP features over longer temporal windows.
Recently, Some researchers proposed an approach for ace liveness detection using histograms of dynamic texture descriptors on three orthogonal planes to encode texture micro-structure of an image sequence (Määttä et al., 2012). For this purpose, the use of two effective Spatiotemporal texture descriptors, namely histograms of multiscale dynamic binarized statistical image features (MBSIF-TOP) and multiscale dynamic local phase quantization (MLPQ-TOP) are advocated. Once the histograms of dynamic textures are obtained, then they are projected onto a discriminative subspace constructed by KDA to separate real faces from spoofing attempts. The discriminative subspace for face liveness detection is constructed using an efficient kernel discriminant analysis approach based on spectral regression (SR-KDA), which has been found to be faster than the ordinary KDA by avoiding costly Eigen-analysis computations.
Tronci et al. (2011) and Yan et al. (2012) performed both dynamic and static analysis in order to employ complementary information about motion, texture and liveness. In static analysis, the author use visual features such as Color and Edge Directivity Descriptor, Fuzzy Color and Texture Histogram, MPEG-7 Descriptors (like Scalable Color and Edge Histogram), Gabor Texture, Tamura Texture, RGB and HSV Histograms, and JPEG Histogram. These features are used to represent each image with a set of different feature spaces. In video analysis, the first clue is the classic vitality clue, which is eye-blinks. Secondly, the movement is measured on the foreground mask extracted from a classic motion detection system. The movement score (Sm) is computed through the average movement across the image. A score level fusion is performed to combine different visual cues to improve the performance. The method has achieved good performance on the Replay-Attack database. As an example of the methods in this group, one can consider the work in Siddiqui et al. (2016) and Pravallika et al. (2016). A multiscale configuration of LBP (referred as multi-LBP) is proposed that encodes the texture of videos and SVM used for classifying into spoof and non-spoof. A novel spoofing detection algorithm is proposed based on motion estimation using optical flow encoded with a Histogram of Oriented Optical Flow (HOOF). The proposed framework is a combination approach that utilizes both texture and motion estimation along with preprocessing using motion-magnification.
Summary of the most relevant face anti-spoofing techniques is drawn in Table 1.
The face recognition system offers safe identification and validation but these systems are open for spoofing attacks. There are numerous proposed methodologies with the intention to overcome spoofing attacks. The biggest challenges to the face recognition technology today are i) the need of designing non-intrusive techniques without using extra hardware and human interaction and ii) designing liveness detection techniques that are robust to change in pose and illumination.
To date, proposed methods to prevent spoofing attacks are presented. These approaches are broadly classified into static and dynamic techniques, although each have their own pros and cons. Static methods are far faster than dynamic approaches, in most cases it process a single image only. Therefore, static approaches are suitable for real-time general purpose applications, where security is not an important constraint. Whereas liveness clue based dynamic approaches are simpler to understand, but it totally fails against video attacks. Now-a-days methods such as fusion of two clues, deep learning and processing input in all aspects have succeeded in producing the desired results.
Still no system is completely free from spoofing, however anti-spoofing techniques simply make it hard for the intruders to attack the face biometric systems. Biometric liveness detection techniques generally concentrate on the FAR(False Acceptance Rate), FRR (False Rejection Rate) and SFAR (Spoofing False Acceptance Rate), but it is necessary to evaluate the efficiency of anti-spoofing system by the consideration of FLR (False Liveness Rate, number of fake samples classified as real) and FFR (False Fake rate, number of real samples classified as fake).
Also there is a necessity to measure a number of spoofed attacks performed against the specific users and its nature also. This mechanism can surely help to predict the behavior of spoof attackers and may eventually help to forecast the possible future victims. It is quite certain that people would like to get rid of remembering the passwords and hence near future itself demand the installation of biometric security at various places. Under such circumstances, it is ample need for the exploration and development of theoretical background for the assessment of spoofing behavior and anti-spoofing system with aspect of financial, social and political.