
Figure 1. Obverse and Reverse Side of the New `10 Note
Counterfeit currency has always been a threat to the economy of the country. Despite the addition of several security features to prevent this, people have always found ways to duplicate currency. It is also difficult in most cases for a common man to identify a fake note and thus, one falls prey to such tricks of counterfeit currency. Hence, it becomes important to adopt newer and better methods to counter the same for all the denominations of currency in circulation, the most vulnerable being the ones with higher denomination. While there exist a number of ways to check for the correctness of the older variants of Indian currency, the newer lot that has been released however has incorporated in themselves, a number of changes and newer features. This paper aims to bring out some of the vital parameters to be extracted to distinguish between real and fake notes in the new set of Indian currency of denominations 2000, 500, 200, 50 and 10 brought out by the Reserve Bank of India (RBI), using various image processing techniques.
Counterfeit refers to the exact fraudulent imitation of something that is valuable. Counterfeit of currency without legal sanction of the government authorities is fraud or forgery. The Reserve Bank of India (RBI) is the sole authority to issue any form of currency throughout India. To counter the counterfeit of currency, like all other banks around the world, RBI also introduces newer bank notes with either addition of security features or with a completely different layout (Chambers et al., 2015). Back in time, anti-counterfeiting measures used fine details with raised intaglio printing that helped anyone detect counterfeit currency with ease. The act of counterfeit of currency is as old as the currency and is still prevalent, causing a huge disruption in the country's economy, thus hindering the growth of the country (Manoharan, 2013; Alekhya et al., 2014). Every year, millions of counterfeit notes get circulated and most remain unidentified as counterfeit until they are scrutinized by the bank authorities. Most often than not, a common man, be it a vendor or a consumer, fails to identify legitimate currency or rely on anti-counterfeiting tools such as the counterfeit pen which only detects counterfeit currency if printed on a laser printer. The Ultra-violet (UV) imaging technique used by most banks is one of the most efficient techniques (Swami and Naveen, 2016; Yadav et al., 2014). However, they involve complex circuitry and prove costly for the use of a common man. Hence, it becomes vital to have a technique and a setup which is not only pocket and user friendly but also provides accurate results.
The main objective of the paper is the identification of counterfeit currency. This paper proposes a vision based system which not only involves simple construction but is associated with better algorithms to detect counterfeit currency. This is done by identifying an array of vital features needed for the distinguishing of counterfeit currency using the concept of feature extraction and feature reduction, using a number of image processing tools and algorithms. The first method of identification involves checking for the genuineness of the security thread using simple morphological image processing methods. The second method involves measuring various features and prints in the note, and comparing their position and size with that of the original. Here, the serial number panel that contains the banknote number is most vitally measured, which grows from small to big on the top left and bottom right side. Apart from this, all other major objects are measured for their size and placement, and the obtained numbers are compared with that of the original for verification.
This section of the paper presents a survey of various image processing and other methods used to distinguish between real and counterfeit currency.
Alekhya et al. (2014) discussed various methods to detect fake currency using image processing and other standard methods. They also proposed a solution for the same using MATLAB technique. In this technique, they split the Red Green Blue (RGB) components of an original note as (r1, g1, b1) and that of the note to be tested as (r2, g2, b2). Then a new image is constructed with the components (r1, g2, b1) or (r2, g1, b1) or (b2, g1, b1), while (r1, g2, b1) combination was said to be the most preferred. Since the human eye is known to be more receptive to the green component, the green component is maximum in most of the images. This helps in better identification of the fake note. The newly constructed note is compared against the first two for identification.
Gururaj and Naveen (2016) proposed a system for counterfeit currency detection using Raspberry Pi, which aimed at small scale applications. Identification of counterfeit currency was achieved with the use of basic image processing algorithms on MATLAB and Simulink model using a web camera and Raspberry Pi. They make use of UV light photography and algorithms such as Hue Saturation Lightness (HSV) conversion, to check genuineness of the security thread. Other algorithms such as template matching, aspect ratio identification, dominant colour and feature extraction were used to differentiate other features of the currency.
Yadav et al. (2014) proposed an automated fake currency detection using MATLAB. A note under inspection is placed in the mechanical set-up that uses UV light. They used MATLAB and feature extraction techniques with HSV colour space along with other image processing algorithms. The system in place is used to analyse the older currency notes of the denomination of 100, 500 and 1000.
Mirza and Nanda (2012) presented the design and implementation of a counterfeit currency authentication system. This system specifically checks for three characteristics of the currency namely identification mark, security thread and water mark. These characteristics are extracted by edge based segmentation using Sobel operator with gradient magnitude.
Suresh and Narwade (2016) proposed recognition and verification of Indian currency using various digital image processing techniques. They rely upon eight characteristics of the currency to do so. For recognition of currency, they used optically variable ink, the identification marks, currency colour code and see through register. The water mark, security threads, microlettering features and latent image are used for currency verification. These features are extracted using edge detection, image segmentation, and the final results are verified against the genuine currency using MATLAB.
Thakur and Kaur (2014) summarized various fake currency detection technique, namely, (1). Commonly used Methods to Detect Fake Currency, (2) Digital Image Processing Method to Detect Fake Currency, (3) MATLAB technique, (4) Counterfeit Detection Pen and (5) Ultraviolet counterfeit detection scanner.
This section presents the features on the obverse and reverse side of the set of new Indian currency of denomination 2000, 500, 200, 50 and 10 brought out by the Reserve Bank of India. The obverse and reverse sides of these currencies are shown in Figures 1-5.

Figure 1. Obverse and Reverse Side of the New `10 Note

Figure 2. Obverse and Reverse Side of the New `50 Note

Figure 3. Obverse and Reverse Side of the New `200 Note

Figure 4. Obverse and Reverse Side of the New `500 Note

Figure 5. Obverse and Reverse Side of the New `2000 Note
The following are the features of vital importance of the counterfeit currency detection system, shown in the obverse side of Figures 1-5.
The following are the features of vital importance of the counterfeit currency detection system, shown in the reverse side of Figures 1-5.
This section presents the hardware and software required to implement the aforementioned system.
Various hardware components needed to implement counterfeit detection system are as follows:
LED lights are electric lights which are used for various lighting purposes that produce light with the use of light emitting diodes. These display high electrical efficiency and a very good life span. However, these succumb to heat dissipation as they are adversely affected by high temperature and thus need heat sinks and cooling fins. LEDs need an appropriate circuit as an LED driver, and are typically controlled by direct current.
The camera consists of a small circuit board of dimensions 25 x 20 x 9 mm which connects to the RPI3 via the CSI (Camera Serial Interface) bus connector. It has a native resolution of 5 mega pixels and a fixed focus lens. It supports the capture of wider images up to 2592 x 1944 pixels and has a video resolution of 1080p30, 720p60 and 640 x 480p60/90.
L293D, a driver primarily used for DC motors uses the concept of H-bridge. The H-bridge enables the voltage to flow in either direction to control its clockwise and anticlockwise motion. Since there are two H-bridges in one IC, it is possible to operate two motors at the same time.
DC motors are used on a small scale replica of the wheelchair, which is connected to the driver and powered by a 12 V on-board battery. The speed with which the motor rotates depends upon the current carried by the armature and the magnetic field that is produced in the magnets of the motor.
Raspberry Pi is a small computer, actually a series of small single board computers, which are however devoid of peripherals such as keyboards, mouse, etc. One of the latest roll out, the Raspberry Pi 3 is a quad core Cortex A53 processor. This is highly dependent upon task threading and instruction set use. It has a 40 pin GPIO with 1GB RAM, full size HDMI, 4 USB 2 ports, CSI camera port to support a Pi camera.
Various software needed to implement the algorithms are as follows:
MATLAB essentially stands for MATrix LABoratory which is a multi-paradigm that provides a numerical computing environment. MATLAB provides a platform for matrix multiplication, implementation of algorithms, plotting of functions and data, creation of user interfaces and so on.
OpenCV 2 stands for Open Source Computer Vision (version 2); it is a programming function library that is used for real-time computer vision and image processing. This library acts as a cross-platform and supports various deep learning frameworks. OpenCV is written with its primary interface in C++ and there are bindings in Python, Java and MATLAB.
Python is a high level programming language widely used for various general purpose programming. This language emphasises code readability and syntax that allows concise codes. This supports a dynamic type of system and provides for an automatic memory management system. It supports multi-programming paradigms such as procedural, functional, imperative and object oriented. It also has a large and comprehensive standard library.
The following section presents the design flow and implementation of the counterfeit detection system along with the algorithm used.
To distinguish between counterfeit and real currency, the system used here to capture the image and process, is as shown in Figure 6. The major component is a box like structure that houses the camera, lighting equipment, power supply, motors and motor driver and also the processor and LCD display equipment which is shown in Figure 6. The lighting system used helps maintain a constant brightness for image capture, thus evading preprocessing techniques to a large extent. The camera captures the image and its motion is controlled by the microprocessor via the motor drivers and motors. The capturing instant is also triggered by the microprocessor or can alternatively triggered manually by adopting an additional circuit for timing and trigger. Once the camera captures the image, it is sent over to the microprocessor, wherein various algorithms are used to distinguish between counterfeit and real currency. The Liquid Crystal Display (LCD) display outputs a message as to whether or not the currency under scan was genuine.
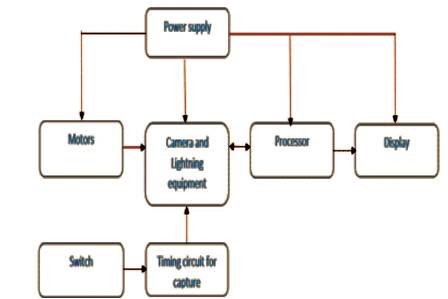
Figure 6. Block Diagram of Counterfeit Currency Detection System
This section presents the two algorithms used to distinguish between real and counterfeit currency.
The images captured in most cases are prone to distortions and noise, hence the information content in the image gets degraded.
Before operating the images in any way, it is important that the input images are pre-processed as discussed in the algorithm shown in Figure 7 (Chitradevi and Srimathi, 2014). This is to make the image devoid of any distortions or noise by supressing it or to enhance some essential features required for further processing.
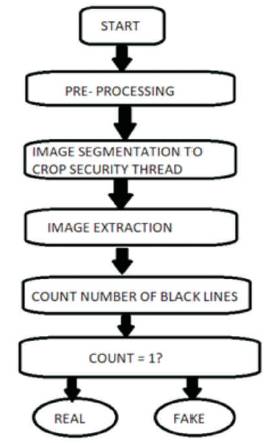
Figure 7. Algorithm to Check for Genuine Security Thread
In all denominations of currency, be it 10, 50, 200, 500 or 2000, a windowed security thread is incorporated as a security measure. In an original note, this thread is continuous and the continuity of the thread can be verified by viewing it under high intensity / bright light. Here a picture of the note is captured under very bright light and a few processes are performed to check the continuity of the security thread. The first step in doing so is to read the captured image as input. A number of preprocessing procedures are applied (Chitradevi and Srimathi, 2014). This includes resizing of the image, increasing the sharpness and removal of any noise or distortions. Noise removal is done by applying smoothening filters which blur the image. Any increase in sharpness is done by using sharpening filters to enhance the edges. The steps are as follows:
Before successfully measuring the contours of a 10, 50, 200, 500 or 2000 rupee note the measurements need to be calibrated using a reference object. In this case, it is a 1 rupee coin which has a predefined diameter of 0.84 inches. The reference object chosen must have two known properties.
In this case, the reference object is a 1 rupee coin which is placed at the bottom left corner. The proposed algorithm will start detecting the object from left to right and while it traverses from left to right it should find the reference object first to find the Pixel Metric Ratio (PMR); only after measuring the pixel size of this object the algorithm will proceed to measure rest of the objects.
The pixel metric ratio is given by the equation,
Pixel_metric_ratio = (object width in pixels)/ (known object width)
An Indian one rupee coin has an object width of 0.84 inches. If the known object width in pixels is 150 pixel then the PMI turns out to be 150/0.84 = 178. From this, one can infer that the there are approximately 178 pixels per 0.84 inch of picture.
The proposed work is coded in Python 3.6 with all the necessary modules such as SciPy, Contours, NumPy, OpenCV 2 and Imutils.
Using this code, all the individual parameters of note such as font size, face diameter, RBI logo, Governor's signature and many more can be detected and compared with a genuine currency. If all the features of the note being inspected matches with original specifications, it is real; otherwise it is fake.
The following procedure explains the working of the algorithm depicted in Figure 8.
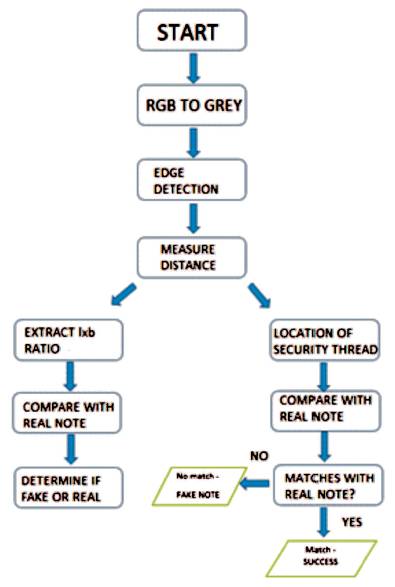
Figure 8. Flow Diagram of Distance Measurement Algorithm for Detection of Fake Note
This section presents the results of the two algorithms discussed earlier, as applied to a 2000 and 500 note to check for their genuineness.
As per the algorithm, the image is first converted into a grey scale image and then morphological operations such as opening, followed by closing are applied, whose output images are shown in Figures 9 and 10. In the final step, if the morphological operations produce a continuous line, it means that the security thread is genuine and hence the note is also genuine. Any discontinuity in the line proves it to be fake as shown in Figures 9 and 10.

Figure 9. Output Images showing Image Segmentation followed by RGB to Grey Conversion for `2000 Note
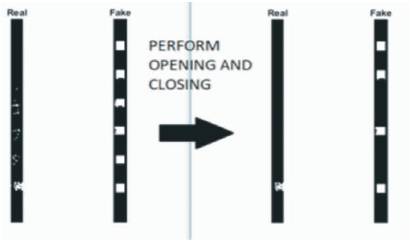
Figure 10. Output Images showing Removal of Connected Noise Components after Post Processing for `2000 Note
First, measurements are calibrated using a reference object as shown in Figure 11. Post this, various features such as the dimension of the note, dimension of RBI logo, dimension of denomination in Devanagari script are measured in inches as shown in Figures 12 to 15.

Figure 11. Comparison of Dimension of Note with Known Dimension of Coin

Figure 12. Dimension of the Edges Measured

Figure 13. Dimension of the RBI Logo Measured

Figure 14. Dimension of Denomination in Devanagari Script Measured

Figure 15. Dimension of Raise Print of `500 Measured
These measurements are used as standard measurements. The same algorithm is applied to a fake note and any discrepancy in the measurements as compared against the standard will determine it to be fake.
This paper provides a system and vision based algorithm to inspect for counterfeit currency. The system helps to check the genuineness of the security thread. A continuous line after morphological operations in place of the security thread proves it to be real, while any discontinuity means fake. Also, the dimensions and placement of various features in the note as well as the note dimensions are measured. The measured values are checked against the prescribed or the original to find any discrepancy for the note to be a fake. This system helps in eroding the circulation of such currency, which in-turn aids as a boost for the economy and growth of the country.
The system can be made modular by decreasing the size of the equipment. Another addition to this could be to provide the use of this software/ algorithm on a platform such as an application which could be wirelessly used on any device. This increases the reach of this method to detect counterfeit currency even to a common man. Further, one can work on detection of a number of other features on a currency to strengthen the algorithm. This work shall then be applied to compare original or forfeited currency.
The authors thank Dr. T Shreekanth, Assistant Professor, Department of Electronics and Communication Engineering, Sri Jayachamarajendra College of Engineering, Mysore, India for providing support and guidance in accomplishing this work.