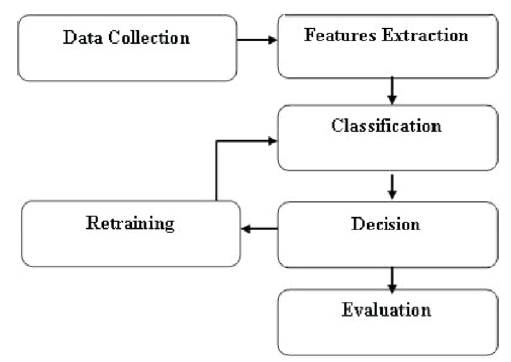
Figure 1. Overview of General Keystroke Dynamics Authentication System
Now-a-days people are heavily dependent on computers to store and process important information. User authentication and identification has become one of the most important and challenging issue in order to secure them from intruders. As traditional user ID and password scheme have failed to provide information security, keystroke dynamics authentication systems can be used to strengthen the existing security techniques. Keystroke dynamic authentication systems are transparent, low cost, and non-invasive for the user, but it has lower accuracy and lower performance compared to other biometric authentication systems. The aim of this paper is to depict a detailed survey of the researches on keystroke dynamic authentication that have used neural networks for classification described in the last two decades. The summary, accuracy of each experiment, and shortcomings of those researches have been presented in this study. Finally, the paper addresses some challenges in keystroke dynamic authentication systems using neural networks that need to be resolve in order to get better performance.
User authentication and identification these days have become a vital issue in preventing unauthorized access of information. Traditional user ID and password scheme have failed to prevent secure information from intruders because it has many flaws such as Dictionary attack, Brute Force attack, Phishing, Shoulder surfing, Spyware, Social Engineering, Guessing, etc. Biometric-based authentication techniques provide more reliable and efficient way of information security. Keystroke dynamics is one of the strong behavioral biometric based authentication system that can extract data and analyze the way a user types. It has made the authentication process simpler and smoother.
Statistical models such as Mean, KNN, t-Test, Bayesian, etc were found to be the first techniques used to analyze keystroke biometrics and dominated for couple of years. Introducing simple Multilayer Perceptron (MLP) with Back Propagation (BP) neural network approach in keystroke dynamics by Brown and Rogers (Brown & Rogers, 1993) gained much attention because of promising experimental result. After that a number of researches have been conducted in keystroke dynamics using different neural networks and achieved higher accuracy rate. Some researchers have also claimed that neural network can produce better result than the statistical methods.
In keystroke dynamics, input sample data are iteratively fed into the network to produce outputs based on its initial predetermined weights. This output is then compared with true output to compute error value. The error value is propagated backwards through the network to recalculate the weights at each hidden layer so that the error value can be reduced. These processes continue until the error value falls below the predefined threshold.
Although Neural Network gained so much attention for classification, nowadays other machine learning approaches are widely used by the researchers. This is one of the motivations for surveying researches in keystroke dynamics those have used neural networks for authentication and identification. Keystroke dynamic systems have low accuracy compared to other biometric systems, so how to achieve better accuracy in keystroke dynamic using neural network is also another motivation of this study. This paper offers a comprehensive comparison of different researches which shows the accuracy, features, and devices used in the experiments. It can be a good source for future researchers who want to work with neural network in keystroke dynamics.
The structure of this paper as follows: Section 1 presents related works in surveying keystroke biometric systems. Section 2 is a short overview of keystroke biometric authentication system. Section 3 describes various Neural Networks, Section 4 presents the findings of this survey. It compares different researches and summarizes some interesting research works. Finally the survey is concluded.
A very few numbers of survey have been conducted in keystroke dynamics. In general, all of them have discussed data collection and feature extraction method, different methods used for classification, and experiments result. A. peacock et al. (Peacock, Ke, & Wilkerson, 2004) have evaluated different researches based on classifier accuracy and usability. The study also has discussed security and privacy issues in keystroke biometric systems and concluded that number of samples greatly affect performance in keystroke dynamic systems.
In 2009, D. Shanmugapriya et al (Shanmugapriya & Padmavathi, 2009) conducted a survey on keystroke dynamics and discussed the performance of different researches. H. Crawford (Crawford, 2010) reviewed concurrent researches in keystroke dynamics and provided recommendation based on those work. The survey commented that statistical classifiers are less computationally intensive, but they do not provide strong level of classification.
S. P. Banerjee(Banerjee & Woodard, 2012) have compared different researches based on different algorithms. The study also discussed explicitly the factors that affect system performance. According to the author, keystroke biometric authentication systems have potential to grow in the area of cyber-security, and biometric monitoring because of its not-intrusive and cost effective characteristics. Similar kind of survey has been done by P. S. Teh et al. (Teh, Teoh, & Yue, 2013) in 2013 The authors have mentioned that keystroke biometric properties such as low cost, high user acceptance and ease of integration with existing security systems made it promising and can play important role in enhancing the overall security system. A. Alsultan et al(Alsultan & Warwick, 2013) survey in keystroke is also of similar kind but may vary by the length and depth of the review, number of research papers and the way of presentation.
Y. Zhong et al. (Zhong & Deng, 2015) have discussed recent trends in keystroke dynamic research including mobile environments. The authors have suggested that desirable databases for keystroke pattern should reflect data variations in realistic applications including number and diversity of subject, size of input, and session's time. M. L Ali et al. (M. L. Ali, Monaco, & Tappert, 2015) have presented a detailed survey on hidden Markov model in keystroke dynamics. The study compared the performance and drawbacks of different researches and finally proposed some recommendations.
A keystroke dynamics system measures a person's typing rhythm on some digital devices such as mechanical keyboard, mobile device, touch screen-based devices, etc and creates a unique signature to identify a legitimate user. A typical keystroke authentication system consists of six components such as data collection, feature extraction or normalization, classification, decision, retraining, and evaluation.
Figure 1 shows an overview of general keystroke dynamics authentication system. In data collection step, raw data are collected via various input devices such as normal keyboard(Bleha & Obaidat, 1993) to pressure sensitive keyboards (Loy, Lai, & Lim, 2005). Most of these keyboards are common QWERT mechanical keyboard, build-in laptop keyboard, and some researchers have modified the existing devices to add pressure feature. Some researchers have used number pad, cellular phone and also touchscreen-based devices. Most of the researchers have generated their own data set but some have used publicly available data sets. Moreover, number of participants also vary in different experiments. Usually inputs were character-based text, but some also have used purely numerical input, and some have used mixed. Texts can be short or long, some of them had input freedom and some were fixed. After data collection, features should be extracted. They need to be processed, normalized and stored for classification. Most of the experiments have used timing features and they can be classified into two groups-Di-graph and N-graph. Digraph is the timing information of two consecutive keystroke such as Dwell Time (DT) and Flight Time (FT). DT is the hold time which is the time interval between key press and key release. FT is the time interval between releasing one key and pressing next key. In N-graph, three or more consecutive keystroke events are used as features. Some other features are pressure of keystroke (P), position on the touchscreen (FA) and typing rate.

Figure 1. Overview of General Keystroke Dynamics Authentication System
Classification is the most important phase of keystroke dynamic system. Different statistical and machine learning approaches have been used for classification by various researchers. Some of the researches have used mixed methods to increase accuracy rate. Most of the Artificial Neural Network (ANN) used by the researchers are Multi-Layer Perceptron (MLP), Radial Basis Function Network (RBFN), Learning Vector Quantization (LVQ), and Self-Organizing Map (SOP), etc. In decision phase, a reference template is matched with the claimant's user and compute the distance between the current typing pattern and the reference template, and final decision is made from the outcome of this method.
Most of the researchers have not paid attention in retraining the model but some researchers have proposed some methods to retrain the model because user typing pattern may change with time and environment. Biometric systems have two functions such as verification/authentication and identification. In identification stage, system classifies the input pattern into one of the N-known class and system will accept or reject the claimant user in verification stage. The performance of biometric system is mainly characterized by three factors: False Acceptance Rate (FAR), False Rejection Rate (FRR), and Equal Error Rate (EER). FAR is the rate at which the system incorrectly accept imposter sample, FRR is the rate at which the system reject genuine user's sample. EER is the point at which FAR and FRR is same and lower EER means the better performance.
Different types of paradigms of Computational Intelligence (CI) such as Artificial Neural Network (ANN), Fuzzy logic, Evolutionary Computation can be used in learning, adaptive decision and providing response in complex and dynamic environment. An Artificial Neural Network is an information processing paradigm, composed of a large number of highly interconnected processing elements (Neuron) working together to solve specific problem. ANN became universal approx-imators for approximating any continuous and many noncontinuous functions and it is capable of yielding nearoptimal solutions to a wide assortment of problems. ANNs have wide variety of applications and potential in different field including medicine, internet security, engineering, retail, robotics, war-fare, intelligence control and finance. There are different types of ANN such as Perceptron, Multi-Layer Perceptron (MLP), Radial Basis Function Networks, Kohonen Self Organizing Maps and Hopfield network etc. In practice MLP is the most commonly used network. The following section summarizes basic concept of different ANNs.
Rosenblatt's Perceptron is known as the first Perceptron model that relies on the assumptions that the perceiving processes of the brain are entirely a function of neurocomputation and the signal propagation between neurons. Perceptron can be described as an algorithm for learning a binary classifier; a function that maps its input x to an output value f(x),
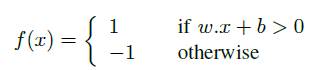
Where, w is the vector of real-valued weights, w.x compute the weighted sum and b is the bias, a constant term that does not depend on the input value. The function can be used to classify x as either positive or a negative instance. Figure 2 shows Frank Rosenblatt's single layer perceptron. Frank Rosenblatt explained that the Perceptron algorithm can be used to model linearly separable function and can be used to classify and make prediction. For example, in case of logical operation such as AND, Perceptron learns the relationships between inputs from samples by adjusting the weight vector. In the figure sample inputs are fed into the Perceptron and the output is the prediction of the form,
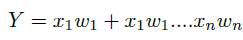
The prediction Y is then compared to the known truth and error. The difference between Y and the known truth is computed. The connection weights are adjusted to minimize the error according to learning rule and other set of samples fed to the system. The process continues until the prediction error is reduced to acceptable label or until the number of iterations reaches to its maximum.
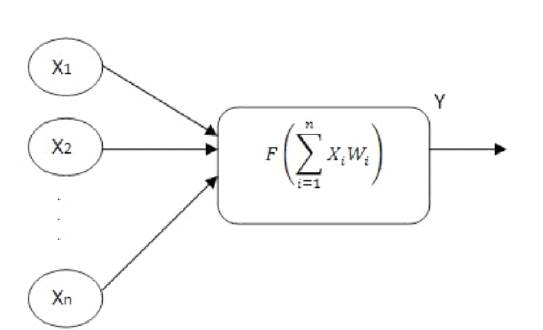
Figure 2. Frank Rosenblatt's single layer Perceptron
Multilayer Perceptron is a feed-forward Artificial Neural Network model used in pattern recognition, classification and prediction that maps sets of input data onto a set of appropriate outputs. It consists of multiple layers of nodes in a directed graph and each layer is fully connected to the next layer. The input layer and output layer can be directly accessible but the hidden layers are not directly accessible. MLP utilizes a supervised learning technique called Feed-Forward Back-Propagation (FF-BP) and gradient decent to minimize the error or difference between expected and obtained result for training the network. For the last decades, FF-BP is the most commonly used and studied in ANN topology. The performance of MLP depends on various factors such as number of layers, number of neurons in each layer, the activation functions used by the neurons and the choice of initial weights. For a given input pattern xp, the output of neuron is calculated by
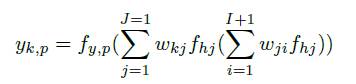
Where, fyk is the output neuron, k is transfer function and fhj is the hidden neuron j transfer function. wkj is the weights of connection between output neuron k and hidden neuron j, and wji is the weights of connection between hidden neuron j and input neuron i. After completing one training cycle, the gradient of the error function is computed and the weights are updated using back-propagation algorithm to minimize error. The advantage of MLP is that it is computationally efficient and can be easily parallelized. It is an universal adaptive learning computing machine and one of the preferred techniques for gesture recognition. The drawback of MLP is that when an initial connection weight is chosen randomly, gradient descent might end up in one of the local minimum Mean Squared Error (MSE) and never immerse to sample the rest of the error surface. Moreover Back-Propagation algorithm is complex which makes ANN training slow and resource intensive. Another drawback of MLP is hard to scale.
The Radial Basis Function Network is an artificial network proposed by Moody and Darken which is based on locally tuned and overlapping receptor fields found in cortex. Although RBFN is architecturally similar to MLP ANN, there are some differences. MLP produces one output and the activation function is used in the single hidden layer from a class of basic function. The fundamental difference is the way in which hidden units combine values that are coming from the prior layers. The activation function of hidden neuron in MLP use inner product of the input vector and synaptic weight vector of that neuron and RBF uses Euclidean norm between input vector and center of that neuron. There are no weights connections between input and hidden layers. Instead of weights, vector of centers, c i and Euclidean distance (the norm is taken) between the input vector u and c is placed between input and hidden i i layer although in general Mahalanobis distance appears to perform better. The hidden layer's nodes typically use either logistic functions or Gaussian function to drive the maximum value of each hidden node's at the center of that node. RBFN's learn local patterns in its immediate neighborhood where MLP's learn global patterns (Nikelshpur, 2014).
Recurrent Artificial Neural Network is similar to feedforward neural network with unlimited back loop. In this case, information is transmitted in both forward and backward direction. The most basic type of topology of recurrent artificial neural network is fully recurrent artificial network where every neuron is directly connected to all other neuron in all direction. Hopfield, Elman, Jordan, bidirectional, etc, are the special cases of Recurrent Artificial Neural Networks(Krenker, Kos, & Bester, 2011).
Kohonen Self Organizing Maps (SOM) are unsupervised competitive networks consisting of weighted, fully connected neural network. Several activation functions such as inner production of input and weight vectors and Euclidean distance can be used with SOM. In each SOM iteration, SOM update output neurons connection weight and also neurons neighborhood. Usually neurons neighborhood starts from surrounding output neurons and decreases in each training iteration. Choosing initial weight is a great factor for the training efficiency of SOM (Kohonen, 1982). The main advantage of SOM is data and can be easily interpreted and understood. SOM is also capable of handling several types of classification problems and also provide interactive and useful data. Moreover SOM can be trained in short amount of time which makes training process easy. The main drawback of SOM is that it needs necessary and sufficient data in order to develop meaningful cluster. When grouping are unique within the map, it is difficult to obtain a perfect mapping. Often clusters are divided into small group which creates several areas of similar neurons. Finally, SOM needs that the neighbor data points behave similarly.
A Hopfield Artificial Neural Network is a special form of Recurrent Artificial Neural Network introduced by John Hopfield in 1982. Hopfield networks serve as contentaddressable memory systems with binary threshold node. These binary units take only two different values for their states and the value is determined by whether or not the units input exceed their threshold. Binary units can take either values 1 or -1 (or values of 1 or 0). To update a unit, Hopfield network perform the following rule:
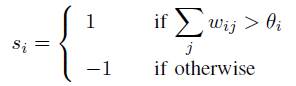
Where wij is the strength of the connection weight from unit j to unit i (the weight of the connection), sj is the state of unit j and θi is the threshold of unit i. Hopfield network has a scalar value in each state of the network which is called energy E.
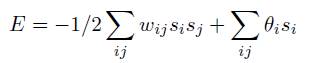
This ensures that when units are randomly chosen to update, energy will either lower the value or remain same. Moreover in the situation of repeated updating, the network will converge to local minimum in the energy function. So, if a state is in local minimum in the energy function, it means that it is the stable state for the network. In general, the major advantages and limitations of ANN over other approaches are given below:
Now-a-days, researchers are getting more and more interested in ANN because of rapid advances in understanding of biological brain, hardware and algorithm. Evolutionary ANNs which use Generic Algorithm (GA) or Particle Swarm Optimization (PSO) to train or to generate ANN topologies, are the most successful models explored by the researcher to increase performance of ANN. Although there is an improvement in performance but still these are not consistent and particular problem specific. The performance of ANN greatly depends on the number of neuron in hidden layer(s). In training phase, it has shown that more the number of neurons in the hidden layer(s), the better ability to recognize specific sample. Performance on the training data improves with training but degrades on testing data.
Neural Networks are considered to have the highest potential in keystroke biometrics by several researchers, because of its capability to explore many competing hypothesis in parallel rather than performing a sequential set of instructions. It is capable of estimating parameter without precise information of all contributing variables. A number of researches have been conducted in keystroke dynamics using Artificial Neural Network. Table 1 shows the comparison among different researches based on neural networks approaches.
Joyce and Gupta (Joyce & Gupta, 1990) were one of the early researchers who reported the uniqueness of a user's typing pattern and have used absolute distances for authentication. From then, statistical models dominated for couple of years before the Neural Network models appeared. Neural Network approach was first brought by Brown and Rogers(Brown & Rogers, 1993). They have used simple multiple layer perceptron with back propagation. Their work was extended by D.T. Lin (Lin, 1997) by doing variation in architecture and parameters of the neural network with modified keystroke latency. Their experiment gave 1.1% False Acceptance Rate (FAR) and 0% False Rejection Rate (FRR).
Abdullah and Ahmed(Ahmad & Abdullah, 2000) made a comparison between ADALINE and Back Propagation (BP) Neural Network model used hold time and digraph latency time. The study concluded that back propagation gave better result than ADALINE. Bleha and Obaidat (Bleha & Obaidat, 1993) have used perceptron algorithm to verify the identity of computer users. Data was collected over a period of eight weeks from 10 valid users and 14 invalid users and achieved 8% False Acceptance Rate (FAR), and 9% False Rejection Rate (FRR). Obaidat and Macchairolo (M. Obaidat & Macchairolo, 1994) have presented a new way to classify inter-character times using three different neural network such as Back Propagation, Sum-Of-Products (SOP), and Hybrid Sum-Of-Products during the investigation phase. The study found that hybrid sum-of-products performs better that other neural networks and achieved an identification rate of 97.8%. M. S. Obaidat extended this work with S. Sadoun (M. S. Obaidat & Sadoun, 1997) and has used key hold time for classification, combining interkey and hold times for the identification process. The study has achieved 2.2% FAR, and 4.7% FRR using fuzzy ARTMAP, RBF and Learning Vector Quantization (LVQ) Neural Networks. However, the neural networks were trained in advance by using legitimate users samples as well as intruders samples which is the main drawback of the study. Authors concluded that hold times classification is superior to interkey time-based classification of computer users.
N. Capuano et al. (Capuano et al., 1999) have used MLP with Radial Basis Function (RBF) rather than using sigmoid one previously used by other researchers and achieved 97% correct authentication with 0% intrusions. S. Cho (Cho et al., 2000) have used NN approach in java applet for secure web based transaction. L. K. Maisuria et al. (Maisuria et al., 1999) have used MLP and K-means cluster algorithm for classification. The authors have collected and tested approximately four thousand sets of typing patterns. The study achieved 84% and 85% acceptance rate and a 69% and 85% rejection rate for MLP and K means respectively.
F. W. M. H Wong et al. (Wong et al., 2001) depicts the use of time latency between keystrokes to create typing patterns for individuals. Both Artificial Neural Networks and KNearest Neighbors have been used to compare the classification capabilities. The study found average authorized acceptance rate and false acceptance rate 84.63% and 1.03% for KNN and 99% and 29% for ANN respectively. J. Mantyjarvi et al. (Mantyj¨arvi¨ et al., 2002) have used an Infrared (IR) transceiver array for detecting the proximity of a finger. Keystroke recognition accuracy was examined by K-Nearest Neighbor (KNN) and Multi Layer Perceptron (MLP) neural network. The study achieved classification results between 78%-99% for KNN and between 69%-99% for MLP classifier respectively. The drawback of the study is that, the finger had to be held perpendicular to surface of the keyboard which is not practical in real time situation.
E. Yu et al. (Yu & Cho, 2003) have applied 4-layer Auto Associative Multilayer Perceptron (AaMLP) as well as SVM as novelty detector to keystroke dynamics identity verification, and found impressive result of nearly 0% for both FAR and FRR. Another interesting finding of their work is that, the computational effectiveness of SVM is much higher that of neural network. SVM model need only 0.1 second training where neural network need more than 100 seconds to achieve similar accuracy. However, users were required to repeatedly provide their password for 150 to 400 times which is not feasible in real situation. Moreover, keystroke sample repetition at later time may be significantly different from the initial samples as users get used to the input text.
S. Yong et al. (Yong et al., 2004) suggested for weightless neural networks for classifying users. The authors have scaled the data before discretizing it into linear and nonlinear intervals and observed that the non linear intervals gave better results. N. Pavaday et al. (Pavaday & Soyjaudah, 2007) focused on commonly used MLP/BP model as well as the multi-technique employing neural network and achieved 1% false acceptance rate and 8% false rejection rate. C. C. Loy (Loy et al., 2007) have developed a keystroke dynamics-based user authentication system using the ARTMAP-FD neural network. Combining pressure and time latency features, the study achieved 11.78% EER. H. Ali et al. (H. Ali et al., 2009) have examined the use of pressure and timing features to create typing patterns for individual users. The authors have combined Artificial Neural Network (ANN) and Adaptive Neuro-Fuzzy Inference System (ANFIS) to classify the authorized and unauthorized users. The study found 100% classification rate with an average training time of 0.9094 second. Similar kind of study was done by A. Sulong et al. (Sulong et al., 2009) but instead of using ANFIS, authors have used Radial Basis Function Network (RBFN). Their study also achieved 100% classification rate with an average training time of 22.4 second. N. Harun et al. (Harun, Woo, & Dlay, 2010; studies proved that MLP NN gives better accuracy and improvement in classifying keystroke nonlinear data. The study also proved that MLP/BP outperforms the RBF.
From 2011 to mid of 2014, no well known research was found in keystroke dynamics using ANN. Researches were involved with other machine learning approaches such as Support Vector Machine (SVM) and they gave much higher accuracy than the neural network approaches. Recently, Antal et al. (Antal et al., 2015) have examined the keystroke data with several machine learning classification algorithms such as Nave Bayes, Bayesian Network, C4.5(J48), K-NN(IBk), SVM, Random forest, and MLP. Data set was collected from touch screen android devices, and both timing and touchscreen based features were included. The best performance was found in Random forest, Bayesian nets, and SVM respectively, and the addition of touchscreen-based features to the default feature set caused an increase to over 10% accuracy for each classifier. The verification measurements were per formed on Euclidean, Manhattan, and Mahalanobis metric. The study shows that the lowest error (12.9%) was obtained by Manhattan metric using both timing and touchscreen-based features. The research concludes that touchscreenbased features increase classification and verification accuracy.
This paper provides a comprehensive survey of researches on keystroke dynamics using neural network in the last two decades. The summary and relative performance of all researches has been included in the comparison table. FAR, FRR, and ERR of each research have been reported in this study when available. The study found that researches were done in different platform, different features, and different number of samples. Most of those works have used keystroke latency as a feature and short fixed texts as sample. Many researchers have used neural networks successfully with good results. But it is not possible to say which one has the lowest error rate or has achieved highest accuracy. Because there is lack of uniformity on those researches and their evaluation methods.
The drawback of traditional neural networks is that they may be trapped in local minimum during training phase. This drawback has been alleviated by introducing deep neural networks which already has shown its performance in many other biometrics applications. One important properties of neural networks is that they can handle many parameters. But it is difficult to decide important features for classification which can be a problem for continuous keystroke authentication in real time. Neural networks also become very slow during training and application phase. In context of keystroke biometrics, neural network needs genuine keystroke patterns as well as imposters samples at initial enrolment stage to train the network which may be impractical. Moreover, updating or removing user profile needs to retrain the whole system which causes increase in processing time. Some solutions such as database partitioning, and retraining during system idle time, etc has been proposed by several researchers to mitigate the problem. But they are in initial stage and more exploration is required to solve the problem.
Md Liakat Ali would like to thank Dr. Charles C. Tappert, Dr. Lixin Tao, and Pace University for Graduate Assistantship in the doctoral study and also for their support.