Figure 1. Ridge Patterns
Biometrics has an important role in privacy protection, when compared to traditional privacy protection methods like tokens, PIN, passwords etc. With the widespread use of fingerprint techniques in authentication systems, privacy protection of the fingerprint becomes an important issue. Traditional encryption is not sufficient for fingerprint privacy protection because decryption is required before the fingerprint matching, which exposes the fingerprint to the attacker. In recent years, significant efforts have been put into developing specific protection techniques for fingerprint. The main objective of this paper is to make a study on mixing fingerprints and how they are used in privacy protection of fingerprints. In this paper various methods of biometric template protection of fingerprint by mixing the fingerprints or multi-biometrics has been surveyed.
For the last few decades, Personal identification based on fingerprints have been used. Fingerprint Techniques are commonly used in authentication systems. Unlike traditional authentication methods like passwords, tokens, and smartcards, Fingerprint Authentication Recognition Systems doesn't need to memorize their passwords or tokens. Besides, passwords can be stolen or may get forgotten or exchanged. So automated human identification using physiological and/or behavioral characteristics are solutions. Biometrics is more mapped to new civilian applications for commercial use. Fingerprint Recognition is one of the leading biometric technologies based on Fingerprint Uniqueness, Persistence and Ease of Acquirement. Biometrics is a significant biological attribute used for identification of an individual.
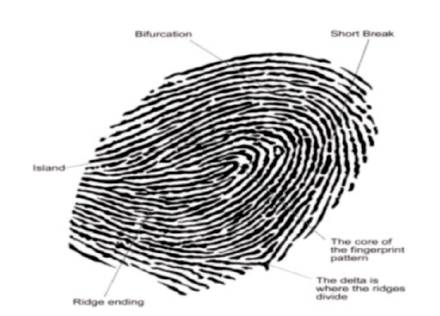
A fingerprint is the design of ridges and valleys on inner surface of fingertip. Fingerprints have graphical flow like ridges present on fingers of individual. Each individual has unique fingerprints. Local ridge features and relationship help to determine uniqueness of fingerprints. The two outstanding local ridge features called Minutiae are ridge ending and bifurcation. The ridge ending is the point where there is unexpect termination or end of ridge. Types of Ridges:
a) Ridge Endings - A ridge that ends abruptly
b) Ridge Bifurcation - A single ridge that divides into two or more new ridges
c) Short Ridges, Island or Independent Ridge - A ridge of short length
d) Ridge Enclosures - A ridge that bifurcates and rejoins itself, continues as a single ridge.
Figure 1 shows the Ridge Patterns. Finger Image contains core point and delta point. The Core point is found at the center of finger image, used as reference point for measuring other minutiae and also during classification. The Delta point is the point on the first ridge bifurcation, abrupt ending ridge, meeting of two ridges, dot, fragmentary ridge or any point upon a ridge at or nearest the center of divergence of two type lines located at or directly infront of their point of divergence.

Figure 1. Ridge Patterns
Fingerprint Recognition comprises of proving a match between two fingerprints. There are three basic ridge patterns of fingerprint like Whorl, Loop and Arch. Arches are more open curves -from one side of finger, ridges enter forming an arc in middle and then ends at other side. Loop-ridges enter from one side, loop is formed and exit from the same side. Loops may slant left or right or may be presented as double loop. Whorl-ridges circularly form around median point on finger or defined by atleast one ridge making a complete circle. A Minutia is defined as the points of interest in a fingerprint, such as bifurcations (a ridge splitting into two) and ridge endings or irregularities in local regions of the fingertip. Minutiae and Orientation can be extracted from a fingerprint.
The fingerprint Recognition System consist of following stages: Fingerprint Enrollment and Verification and Identification or Matching. The goal of verification is to prevent multiple individuals from accessing the same identity and it is typically used for positive recognition. Fingerprint verification is the technique, which is used to verify the authenticity of one person by his fingerprint. During the identification or matching, the system recognizes a person or authenticates by searching the templates of all the users in the database for a match. If result is a match, then authentication is successful, otherwise it is a non-match.
As biometrics popularity is increasing, there is increased concern over the loss of privacy and potential misuse of biometric data stored in the central databases. On the other hand, the alternative suggestion of keeping biometric data in smart cards does not solve the problem, since coiners can always claim that their card is broken to avoid biometric verification altogether. So it is important to generate a better and Robust fingerprint privacy protection system.
Many global approaches that use additional features have been explored to minimize the error rate in matching the fingerprints. The literature survey of various existing techniques of mixing the fingerprint has been done.
Analysis on the paper “Combining multiple biometrics to protect privacy,” by Berrin et.al introduced a method in which two distinct fingerprints were combined to a single identity either in the image level or in the feature level. As per this paper, the concept of combining two different fingerprints into a new identity as a unique identifier was first proposed where the novel identity is created by combining the minutiae positions or locations extracted from the two different fingerprints. Thus the new identity protects the original minutiae locations of each fingerprint. So, it is easier for the attacker to identify such a new identity since it contains more minutiae positions than that of an original fingerprint.
Analysis on the paper “Multi-biometric templates using fingerprint and voice” by Camlikaya et.al introduced a multi-modal biometric verification system by mixing fingerprint and voice technologies. The system combines the two technologies at the template level, using multibiometric templates. This technique combines two different biometrics into a new identity, by extracting the minutiae positions or locations from a fingerprint and the artificial points generated from the voice features to produce a new identity. The combination of fingerprint and voice data productively reduces privacy concerns through hiding the minutiae points from the fingerprint, between the artificial points produced by the features which are attained from the utterance of the speaker. This method preserves privacy and increases the accuracy.
“Mixing fingerprints for template security and privacy,” Ross et.al introduces the method in which the input of fingerprint image is mixed with another fingerprint that is from a different fingers, so as to produce a new mixed image that produces the identity of the original fingerprint that is difficult to understand. Mixing the fingerprints produces a new print that looks like a reasonable fingerprint and, therefore, (a) it can be practiced by traditional fingerprint algorithms and (b) an intruder may not be able to decide if a given print is mixed or not. In order to mix two fingerprints, each fingerprint is partitioned into two components, viz., the spiral and continuous components. Subsequent to the pre-aligning the two components of each fingerprint, i.e the continuous component of one fingerprint is combined with the spiral component of the other fingerprint image so as to create a mixed fingerprint.
“Mixing fingerprints for generating virtual identities,” Othman et.al introduced a method in which combination at the feature level combines the continuous and spiral component of two different fingerprints to generate a new identity. The ridge flow of a fingerprint can be represented as a 2-D Amplitude and Frequency Modulated Signal. This phase is then decomposed into continuous and spiral component. Pre-aligning the two components of each fingerprint is done, i.e the continuous component of one fingerprint is combined with the spiral component of the other fingerprint image so as to create a mixed fingerprint. The continuous component represents the orientation of the fingerprint image while spiral component represents the minutiae positions of the fingerprint image.
“A novel system for fingerprint privacy protection,” Li et.al introduced a feature level based technique for fingerprint privacy protection by combining two fingerprints into a new identity. The introduced technique creates a new identity by combining the minutiae location extracted from the one fingerprint and directions extracted from another fingerprint. Thus, the original minutiae positions and orientation of first and second fingerprint respectively can be protected in the new identity (i.e. virtual identity).
Fingerprint Combination for Privacy Protection” Li et.al, introduced a novel system based on feature level for protecting privacy of fingerprint by combining two different fingerprints into a new identity. There are two phases - Enrollment and Authentication. During Enrollment, the fingerprints from two different fingers are captured, then features are extracted from both fingerprints. From one fingerprint, minutiae positions are taken and from other fingerprint minutiae orientation are taken and after that both fingerprint reference points are also taken and a combined minutiae template is created using combined minutiae template Generation Algorithm and the templates will be stored in a database. For Authentication, fingerprints from two query fingerprints are taken, features are extracted and combined minutiae template is generated. For matching two query fingerprints against template of combined minutiae a two stage fingerprint matching process is done. The complete minutiae feature of single fingerprint will not be compromised even if the database is stolen. As there is combined minutiae template of similar topology to original templates it can be converted to a real look alike fingerprint by using a reconstruction approach. A new virtual identity is issued for two different fingerprint matching. The authentication will be successful if matching score exceeds the predefined threshold.
“On mixing fingerprints” Othman et.al introduces the mixing of two different fingerprints, related to two different fingers, at the image level in order to create a new fingerprint. To combine or mix two fingerprints, each fingerprint pattern is fragmented into two different components- the continuous and spiral components. After pre-aligning the components of each fingerprint, the continuous component of one fingerprint is combined with the spiral component of the other fingerprint. A remote fingerprint system maintains a small set of preselected auxiliary fingerprints corresponding to multiple fingerprints. During enrollment local machine fragments the fingerprint into continuous and spiral components. To ensure the privacy of the fingerprint image in the local system, the remote system transmits the fingerprints in the auxiliary set and the local machine searches through the received fingerprints, to locate a “compatible” fingerprint, based on the continuous component of enrolled fingerprint which is then fragmented into continuous component, and mixed with spiral component of enrolled fingerprint. The new mixed template is enrolled in the remote system database. During authentication, when the subject presents a sample of the left index finger, it is decomposed and its continuous component is used to search through the fingerprints in the auxiliary set from the remote fingerprint system to determine the most “compatible” fingerprint. In the local machine, the spiral component of enrolled template is mixed with the continuous component retrieved from the remote machine to generate a mixed fingerprint, which is then compared against the database entry. The mixing of fingerprints has several benefits:
This paper presents the survey of various methods related to fingerprint matching techniques for privacy protection. Multi-biometric template scheme has been used for providing robust integrity among fingerprint templates and it is difficult for the attacker to distinguish a mixed fingerprint from the original fingerprints or it is not easy for the attacker to recover the original minutiae templates from a combined minutiae template or a combined fingerprint. This paper also highlights some schemes that provide security to the template by creating virtual identity that are more secure than traditional techniques that makes use of key or token for the fingerprint privacy protection.