
Figure 1. The Ericsson T39 was the First Mobile Phone with Bluetooth
Special Interest Group (SIG) manages the Bluetooth short-range wireless technology network. Bluetooth technology began with the replacement of cables and progressed to Low Energy and subsequently Mesh Technology. Different specifications are accessible in the market based on the needs of Application Development. Every standard has its own set of advantages and disadvantages. Low Energy Device is the Bluetooth 5.0 specification. The study of BLE 5.0 exhibits the development of BLE 5.0's design and performance at the Link Layer and PHY. In the controller, the BLE 5.0 architecture's Link Layer and Physical Layer (Radio channels) are employed. There has been a reduction in device complexity and power usage. The Link Layer and PHY design languages are synthesizable Verilog.
Ericsson Mobile Communications did the early research and development of Bluetooth technology. In 1994, the company began looking for alternatives to cables for connecting to its cellular phones and accessories (Bray & Sturman, 2001; Miller & Chatschik, 2001). Ericsson explored radio rather than infrared technology in their research, and found that radio is superior for wireless systems since it does not need a line-of-sight connection, and makes the connection between the two devices more reliable.
The Bluetooth SIG is in charge of Bluetooth marketing as well as the development of Bluetooth standards and protocols. Version 1.0 of the Bluetooth standard was released one year after the SIG was formed (Bray & Sturman, 2001). The SIG welcomed four new key promoters to their membership in late 1999, Microsoft, Lucent, 3Com, and Motorola were among them. Miller (BLE, 2018) estimated that there would be 1790 SIG members by mid-2000.
According to Bluetooth.org (Bluetooth, 2007), the SIG now includes over 9000 member firms from the telecommunications, computer, automobile, music, fashion, industrial automation and network sectors. SIG members drive Bluetooth wireless technology development, as well as deploy and sell the technology in their products (Bluetooth, 2007). On the one hand, the SIG's fast expansion reflects the fact that it welcomes new members to provide any additional information that may aid in the development and implementation of Bluetooth. Non-members, on the other hand, are not permitted to utilise Bluetooth technology per SIG regulation.
This particular organisation is not just a privately owned, non-profit trade association, but it also does not create, manufacture or sell Bluetooth enabled devices (Bluetooth, 2007). The SIG's contributions can be recognised through their efforts in the publication of specifications, administration of the qualification programme, trademark protection, and promotion of Bluetooth wireless technology, as well as global Bluetooth promotion through its global headquarters and local offices.
Infrared was offered as a wireless alternative earlier. Data connections (serial or USB) were used to, for example, sync data between the computer and PDA. However, line-of- sight was necessary, which meant that the two devices had to be "aimed" at each other throughout the data transmission.
Bluetooth was omni directional, but it only had a range of around 10 metres (30 feet), thus it did not truly have a range advantage. There was no speed gain in version 1.0, which clocked in at 721 Kbps.
The first Bluetooth-enabled phone was revealed in 2000, an Ericsson, the T36 – which was enough for the original use-cases envisioned. That was not however, the first Bluetooth phone to enter the market as the T36 was cancelled.
The Ericsson T39 was the first to use the technology, debuting in 2001 as shown in Figure 1. In the same year, IBM released the ThinkPad A30 notebook, which had a Bluetooth connection.

Figure 1. The Ericsson T39 was the First Mobile Phone with Bluetooth
When two devices need to communicate with one another, they must first agree on a few things before the conversation can begin, whether it require a wired or wireless connection. The Bluetooth Special Interest Group (SIG) creates wireless technology standards for hardware makers to employ when creating new products with no physical connection necessary. Wireless communications technology advances in tandem with technological advancements. Developers employ two Bluetooth technology standards to keep you linked at the time.
Bluetooth allows both point-to-point and point-to-multipoint communication. A piconet is made up of many Bluetooth devices that share the same channel (hopping sequence). The master is the unit that begins the connection, and it may have up to 7 active slaves and 256 parked slaves. The master and slave units are physically identical. In rare instances, the master unit and one of its slave units may exchange roles. This feature comes in handy when the master has to accommodate different piconets or put up a new piconet, as seen in Figure 2 (Schwartz, 2001).
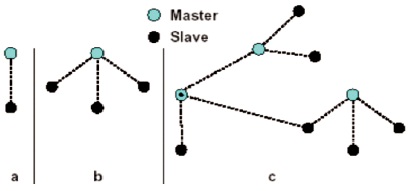
Figure 2. Bluetooth Network Topology
Every piconet has its own frequency hopping sequence. The Bluetooth Device Address of the piconet's master determines the sequencing. When the number of nearby piconets is modest, and distinct piconets have different hopping sequences, they can interact without interfering with each other.
Visualization of the four basic logical topologies tree, mesh, ring and shared slave topology (SST) are shown in Figure 3. Directed connections represent master-slave relations: the arrow points towards the slave. Bridge nodes are either of master/slave (M/S) or slave/slave (S/S) type.
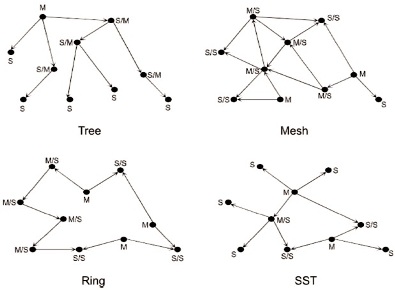
Figure 3. Basic topologies
Bluetooth BR/EDR devices must constantly be paired, which results in one device trusting the other and being able to communicate data in a safe manner utilising encryption.
When two Bluetooth BR/EDR devices get within range of one another, they hold an electrical chat to see whether they trust one other and have data to exchange. The user is seldom required to push a button or provide a command; instead, the electronic communication takes place automatically. The gadgets, whether they are part of a computer system or a stereo, establish a network when the dialogue is completed.
Bluetooth LE functions in a unique way. Devices may also be coupled to build a trusted connection; however, this is not required for all sorts of products. In the process of advertising, a Bluetooth LE device that wishes to be identified transmits unique messages (known as packets). Advertising packages are loaded with important information regarding the ad device. Another relevant device will locate the advertising device by scanning (listening) for advertising packets and picking those from appropriate devices. Scanning usually occurs only when the user initiates it, for as by hitting a button on a smartphone application. Typically, the user is then shown with information about the relevant devices that have been found and is given the option of connecting to one of them.
The range of Bluetooth devices is affected by many variables, including:
Bluetooth technology's frequency band makes it an excellent option for wireless communication.
This specifies certain fundamental features of how the radio transmits and receives data, such as transmission rate, error detection and correction, interference protection, and other methods that impact signal clarity across various ranges.
The minimal signal intensity at which a receiver can still receive and decode data.
The greater the intensity of the sent signal, the greater the range that may be obtained. However, raising the transmission power will cause the battery to drain quicker.
The process of converting electrical impulses from the transmitter to radio waves and then back again on the receiving end.
Several variables, like distance, humidity, and the medium through which the signal travels, might degrade the signal (such as wood, concrete or metal).
The current version of Bluetooth is Bluetooth 5.0.
Bluetooth Low Energy 5.0 has 4x the range, 2x the speed, and 8x the broadcast message capacity.
Bluetooth 5 provides three low energy PHYs:
LE 1M PHY –1M/s bit rate; uncoded. This PHY is used in Bluetooth 4.0.
LE Coded PHY (new) – 1Ms/s with error correction coding. Used for Bluetooth 5's “4x range”.
LE 2M PHY (new) –2Ms/s uncoded. Used for Bluetooth 5's “2x speed”. So, with two new PHYs, we gain 4x range and 2x speed, and additional message capacity.
31 octets payload was maximum in BLE 4.0. In Bluetooth 5, the payload was increased to 255 octets by adding additional advertising channels and new advertising PDUs.
In non-connectable advertising, interval reduces from 100ms to 20ms. It is known as High-duty cycle non-connectable advertising.
Summary of the major differences between Bluetooth versions (from 2.0 to 5.0) is shown in Table 1 (Bluetooth Low Energy (BLE) overview, 2018).
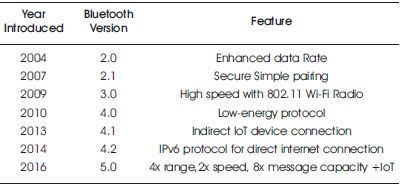
Table 1. Bluetooth versions (from 2.0 to 5.0)
Bluetooth wireless technology is described by Bluetooth.org (2007) as a worldwide wireless standard for personal connecting of a wide variety of electronic devices. Bluetooth is described as an open standard for short-range digital speech and data transfer that enables point-topoint and multipoint applications by Tech Encyclopedia (2007). According to Bluetooth.com (Bluetooth, 2007) the most recent core standard, Version 2.1+EDR, was issued to expand its short-range wireless technology and make it simpler for users to connect Bluetooth devices with greater security and reduced battery usage. This technology's advancement is based on its inherent qualities, which include small-form factor radio, low power, low cost, built-in security, resilience, ease-of-use, and ad hoc networking capabilities.
When Bluetooth devices are in close proximity to one another, they connect electrically and automatically to see whether they have data to exchange or if one needs to manage the other. Each Bluetooth-enabled peripheral has a programmed address transmitter that operates within a set of addresses for a particular device. The device sends out radio signals, which are received by another device within the same address range, which then sends a signal back to the originating device, forming a Personal Area Network (PAN). Bluetooth devices can only connect with one another if their profiles and capabilities are the same (Rysavy, 2004; Franklin & Pollette, 2005).
Bluetooth's security is a major problem. Because it is an open standard, hackers may easily break into it. It's also a concern when a device comes into range with another device that isn't from the same user since it might steal data from the other device, posing a security risk.
When compared to other wireless communications such as 802.11, which may provide hundreds of feet of connection, Bluetooth's communication range is also a drawback. Despite the fact that it is more difficult to interfere between two peripherals at a short distance, Bluetooth still needs to enhance this component of the technology while also providing a stronger security mechanism. Because if the communication range increases, it will be simpler for outside attackers to attempt to hack into the peripherals. A better security architecture is required. Nonetheless, Bluetooth 2.1, was intended to improve the security of future devices.
Bluetooth has become the most popular technology in the acquisition of proximity traces because of its success in personal electronic devices (cellular phones, smart phones, laptops, and so on). These traces are only concerned with determining the proximity of mobile nodes. There are several important references among Bluetooth-based initiatives, beginning in 2004 with the experiments conducted by MIT (Eagle & Pentland, 2006), in which a group of students and staff at the university used their mobile phones to record their location (based on the cellular network's base station identification) and proximity information.
It is a layer protocol architecture (Figure 4) made up of core protocols, cable replacement protocols, telephone control protocols and adopted protocols. LMP, L2CAP, and SDP are required protocols for all Bluetooth stacks. Furthermore, two protocols: HCI and RFCOMM, may be used by practically any Bluetooth-enabled devices.
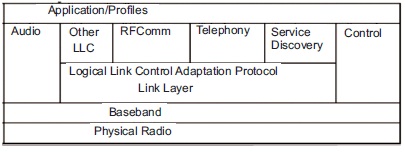
Figure 4. Protocol stack of Bluetooth
Any Bluetooth device in discoverable mode will broadcast the following information on demand:
Any device may conduct a search for other devices to connect with, and any device can be set up to react to such searches. If the device attempting to connect knows the device's address, it always replies to direct connection requests and, if asked, communicates the information listed above. Although using a device's services may need pairing or approval by the owner the connection itself may be created and maintained by any device until it is out of range. Some devices can only connect to one other device at a time, and connecting to them prohibits them from connecting to other devices or show in enquiries until the other device is disconnected. Every device has a 48-bit address that is unique. Inquiries, on the other hand, seldom display these addresses. Instead, the user may choose from a list of friendly Bluetooth names. This name displays in listings of linked devices and when another user searches for gadgets. The Bluetooth name on most cellular phones is set to the phone's manufacturer and model by default. Most mobile phones and computers simply display Bluetooth names, and extra software is necessary to get further information about distant devices. This might be confusing since there could be multiple cellular phones in the T610 range, for example.
Many Bluetooth services can disclose private data or give the connected party power over the Bluetooth device. It is vital to be able to detect individual devices for security concerns, and to be able to manage which devices are permitted to connect to a given Bluetooth device. At the same time, Bluetooth devices should be able to establish a connection without the need for human involvement (for example, as soon as they are in range). Bluetooth employs a technique called bonding to settle this issue, and a connection is created via a procedure called pairing. The pairing process is either triggered by a user's explicit request to create a bond (for example, when the user explicitly requests to "Add a Bluetooth device"), or it is triggered automatically when connecting to a service where the identity of a device is required for security reasons (for the first time). Dedicated bonding and broad bonding are the terms used to describe these two situations. User contact is often required during pairing; this user interaction is the foundation for authenticating the devices' identities. When pairing is successful, a link is created between the two devices, allowing them to connect to each other in the future without having to go through the pairing procedure to validate the devices' identities. The user may subsequently delete the bonding connection if desired.
In Bluetooth v2.0 and before, this is the only technique accessible. Each device must input a PIN CODE, and the pairing will only work if both devices use the same PIN code. A PIN code may be any 16-byte UTF-8 string; however, not all devices are capable of inputting all conceivable PIN codes.
A Bluetooth Hands-free headset is an apparent example of this kind of equipment, which typically has minimal inputs. These devices normally have a set PIN that is hard-coded into the device, such as "0000" or "1234".
Mobile phones are a good example of this type of device. They allow the user to enter a numeric value with up to 16 digits.
Smartphones and PCs are two examples of these gadgets. As a PIN code, they enable the user to input complete UTF-8 text. When connecting with a less capable device, the user must be aware of the other device's input limits; there is no way for a competent device to decide how to limit the available input a user may utilise.
Although a Bluetooth v2.1 device may only utilise legacy pairing to communicate with a v2.0 or older device, it is needed by Bluetooth v2.1. The following are the features of SSP:
This strategy, as the name suggests, just works. There is no need for user participation; nevertheless, a device may ask the user to validate the pairing procedure. This approach is often employed by headsets with extremely limited IO capabilities, and it is more secure than the fixed PIN mechanism used for legacy pairing by this group of constrained devices. There is no Man In The Middle (MITM) protection with this strategy.
Numeric Comparison may be used if both devices have a display and at least one can receive binary Yes/No user input. On each device, this approach shows a 6-digit numeric code. To guarantee that the numbers are same, the user should compare them. If the comparison is successful, the user(s) must confirm pairing on the device(s) that may take input. This approach protects against MITM if the user verifies on both devices and does the comparison correctly.
This approach may be used between a display device and a device with numeric keypad entry (such as a keyboard), or between two devices with numeric keypad input. In the first example, the display is utilised to show the user a 6-digit numeric code, which he or she subsequently types on the keypad. In the second situation, each device's user inputs the identical 6-digit number. Both of these scenarios provide MITM protection.
To exchange data packets, traditional Bluetooth devices enter the connection state. The connection status is divided into three modes: active, SNIFF, and HOLD. The master and slave actively interact on the channel in the active mode, but the SNIFF and HOLD modes may be employed to minimise the slaves' activity. A slave may lower the number of slots it has to listen on the channel in SNIFF mode, and in HOLD mode, a slave can gain capacity to perform other tasks such as scanning, paging, querying, or attending another piconet (Bluetooth Specification, 2010d). The PARK state is useful for minimal power consumption and implies that a slave is not required to participate in the channel. However, the parked slaves maintain channel synchronisation by occasionally waking up. Slave parking and unparking may be used by the master to connect to more than seven slaves in a piconet. However, only seven slaves may be in the connected state at the same time (Bluetooth Specification, 2010c). In Bluetooth Core Specification version 5.0 (Bluetooth Specification, 2016), the PARK state was theoretically dropped. Figure 5 compares the device states of both Bluetooth technologies. Explicit low power modes are not required for BLE devices. If no data has to be transferred, devices will enter the Standby state, which may be accessed from any other state. Furthermore, entering the connection state is not always needed in order to interact.
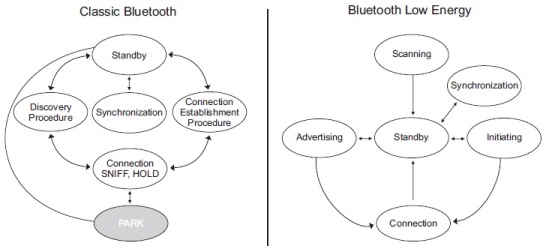
Figure 5. Classic Bluetooth and BLE
To participate in a piconet, however, a link must be established (Bluetooth Specification, 2010b, 201a). Since Bluetooth Core version 4.1 for traditional Bluetooth (Bluetooth Specification, 2013) and Bluetooth Core version 5.1 for BLE (Bluetooth Specification, 2019), the synchronisation state has been specified.
Figure 6 shows the different levels of the architecture of BLE 5.0:
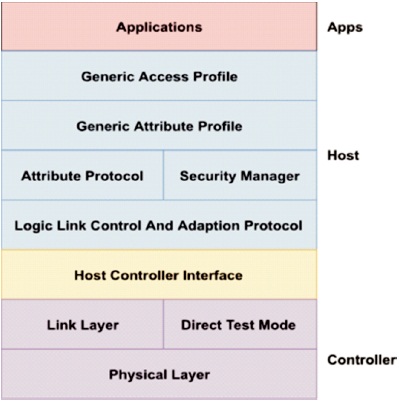
Figure 6. Architecture of BLE
These are the layers:
It refers to the physical radio that is utilised for communication and data modulation/demodulation. It runs in the ISM band (2.4 GHz spectrum), which is open to the public.
This layer communicates with the Physical Layer (Radio) and offers abstraction and a means for higher levels to interact with the radio or PHY. It is in charge of controlling the radio's status as well as the time requirements for conforming to the SIG, the Bluetooth Low Energy standard.
The goal of this mode is to verify the physical functioning of the radio (PHY layer) (such as transmission power, receiver sensitivity, etc. of Tx and Rx).
This layer serves as a protocol, allowing the host layer to interact with the Controller layer. These layers might reside on distinct chips or on the same chip, depending on the requirements.
This Layer functions as a protocol multiplexer. L2CAP converts several protocols from the higher levels into standard BLE 5.0 packets that are then transmitted down to the lower layers.
The BLE Mesh Profile is built on a complete BLE stack. The mesh idea makes advantage of Bluetooth Low Energy's core wireless communication characteristics. The BLE mesh network is a possible topology for BLE devices. Each device in a BLE mesh network may interact with every other device in the network (Woolley, 2019) provided the physical architecture permits it (Bluetooth Mesh Profile, 2019). The BLE mesh network was built to enable large-scale multi-hop networks, making it excellent for automation, sensor networks, asset monitoring and any other use case requiring the secure communication of tens of thousands of devices (Kolderup & Marcel, 2017). The BLE mesh idea is a paradigm change that extends the traditional Bluetooth features to fully allow multi-hop networks (Woolley, 2019).
Figure 7 shows the sample BLE Mesh Profile multi-hop network topology: Nodes A to H are BLE mesh nodes without a special feature whereas nodes I to M are BLE nodes with the Low Power feature activated. Their corresponding Friend nodes are nodes O and P respectively. Node N also has the Friend feature enabled but currently, no Low Power node uses it. The nodes Q and R relay messages and thus, the Relay feature is enabled. The Proxy node S transforms messages received from the non BLE MeshProfile node T and relays them subsequently (Bluetooth Mesh Profile, 2019a).
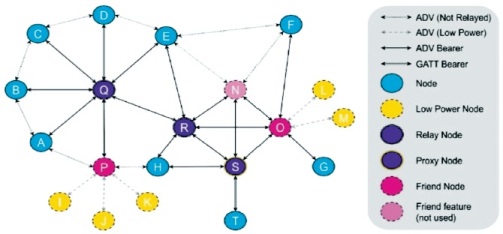
Figure 7. Mesh Profile
The purpose of this paper is to present Bluetooth requirements, and it also introduces the architectural layers of Bluetooth 5.0. The Bluetooth Specification can be improved beyond Bluetooth 5.0. Every technology has advantages and disadvantages, and this technology is no exception. We may enhance the connection device and other constraints in a subsequent specification.