Figure 1. Data Gathering Process
Wireless Sensor Networks have begun as an effective solution for a wide range of applications. Mobile data gathering is an important operation in sensor network. Most of the traditional sensor network architectures consist of static nodes that are deployed over a sensing area. However, a location service is considered, where each sensor essentials to maintain its location information by normally updating its location information within its neighboring set of polling points in the network. There is a moving path planning with multihop relay networks. The source node and the sink node communicate with each other either in single hop or multi-hop network. The existing approaches fail to deliver a guaranteed reliable network in terms of traffic, end-to-end connection and mobility. To overcome the problem of these failures, a Delay Aware Secure Multihop Routing (DASMR) protocol is proposed. In this protocol, sensor networks are first defined with mobile sink and then an overview of the data gathering process is presented in such a scenario based on the role of a mobile sink. Data can be gathered by its own or neighboring node by visiting each polling point through the cluster heads. Here, mobile data gathering is mainly focused on path selection problem. The node is travelled through the path, which is dynamically gathering the information at each cluster head. This DASMR scheme achieves over 70 percent of energy saving per node and 80 percent of energy saving on cluster heads comparing with previous works. Although, the number of polling points are also minimized by visiting the new polling points, which also extends the network lifetime. DASMR reduces the overall energy consumption and optimize the data collection tour to minimize the delay by the sink. Simulation experiments based on GloMoSim is shown to validate the high efficiency of the presented formulations and algorithms.
In a Wireless Sensor Network (WSN), sensor nodes consist of communicating, sensing, data processing components and storage resources. It consists of nodes organized to sense environmental or physical conditions for an extensive range of applications such as, scientific observation, field surveillance, environment monitoring, structure monitoring, and emergency detection. By using these applications, extending the network lifetime and ensuring packet delivery delays are critical for achieving acceptable Quality of Service (QoS).
Numerous sensing applications share in common that their source nodes deliver data to sink nodes through multiple hop relay, leading to the problem on how to find routes that enable all data to be delivered in required time frames, whereas simultaneously taking into account the factors such as, load balancing and energy efficiency.
Several previous research efforts have tried to achieve trade-offs in terms of load balancing, delay, and energy cost for such data gathering schemes. Here, a cluster based topology can be used for data gathering in WSNs. The cluster head selection is done by several methods like distributed (i.e., random method, residual energy, election phase, centralized and probabilistic) method.
This paper deliberates how to plan the moving trajectory of a mobile sensor based on the load balancing among sensors and distribution of sensors to extend the lifetime of network and how the new physical layer multiple packet transmission techniques can be applied to increase data throughput and decrease the energy consumption in sensor networks.
Here, the main objective of this paper is to understand the fundamental scalability of wireless sensor networks used for data-gathering process, then also to develop an integrated data gathering mechanism which utilizes a non-conventional energy model and new physical layer techniques for data gathering in wireless sensor networks. Such understanding is crucial in the deployment of these networks and also the development of efficient protocols. This proposed DASMR protocol increase the network lifetime by reducing the consumption of sensor nodes such as energy and bandwidth.
Meanwhile, a distributed network has multiple nodes and facilities many messages, and each node is a shared resource, and various decisions must be made. There may be multiple paths from source to destination. Hence, message routing is an important issue. The main performance measures affected by the routing scheme are quantity of service (throughput) and average quality of service (packet delay). Routing techniques must also avoid both livelock and deadlock. Routing schemes can be centralized, broadcast, adaptive, distributed, fixed (i.e. pre-planned), etc. Perhaps the simplest routing method is the token ring (Smythe, 1999) Here, a straightforward fixed protocol and a simple topology results in very good reliability and precomputable Quality of Service (QoS). A token passes continuously around a ring topology. While a node needs to transmit, it captures the token and attaches the message. As token passes, the destination reads the header, and captures the message. In some techniques, it attaches a 'message received' alert to the token, which is then received by the original source node. Later, the token is released and can receive additional messages. The token ring is a completely decentralized method which efficiently uses Time Division Multiple Access (TDMA). However, this scheme is very dependable; one can see that it results in a waste of network capacity. The token must pass once everywhere the ring for each message. Consequently, there are various changes of this scheme, including using several tokens, etc.
Fixed routing schemes often use Routing Tables that order the next node to be routed to given the current message position and the destination node. Routing tables can be very large for huge networks, and cannot take into account real-time things, nodes with backed up queues, or jammed links.
Adaptive routing schemes depend on the present network position and can take into account several performance measures, containing cost of transmission over a given link, reliability of a path, time of transmission and congestion of a given link. They can also account for link or node failures.
Routing has two main purposes: Route discovery and Packet forwarding. The former is concerned with discovering the routes between nodes, and the later is about transferring data packets through the formerly discovered routes. There are different kinds of adhoc routing protocols. One can differentiate proactive and reactive protocols. Protocols of the final category are also called on-demand protocols, then another type of classification distinguishes source routing protocols (e.g., DSR) and routing table based protocols (e.g., DSDV).
The major requirements of a routing protocol are,
In data collection sensor network applications, sensors in normal are randomly scattered and densely deployed over a sensing field and left unattended after being organized, which makes it difficult to replace or recharge their batteries. Later sensors form into autonomous groups; those sensors near the data sink typically exhaust their batteries much faster than others due to more relaying traffic. While sensors around the data sink deplete their energy, coverage and network connectivity may not be guaranteed. Owing to these limitations, it is critical to design an energy-efficient data gathering scheme that consumes energy equally across the sensing field to attain long network lifetime. Additionally, sensing data in some requirements are time-sensitive, and data collection may be required to be performed within a specified time frame. Hence, an efficient, large-scale data collection scheme should aim at low data latency, long network lifetime and good scalability. Several approaches have been proposed for efficient data collection in the literature.
A. Chakrabarti, A. Sabharwal, and B. Aazhang [1] presented a procedure for communication power optimization in a network of distributed sensors randomly through data collector moving on a fixed path. By using a mobile observer, which remains within its range of any sensor for a brief period, and unable to transfer the data in this period leads to data loss is the key challenge. The queuing model is used as a design tool to recognize the combination of system parameters which ensures adequate data collection with minimum power. The results achieved from the queuing analogy take a particularly simple form in the asymptotic rule of dense sensor networks. Moreover, for sensor networks that cannot allow data loss, the authors derive a tight bound on lowest sensor separation which ensures that no data will be lost on mobility. In a mobile observer, data loss occurs once the observer passes over a region of high local node density, therefore not all sensors needs be successful in transfer of data to the observer within the range. This loss is unavoidable, if the sensors are independently distributed over the network. To extend the benefits of mobile data gathering to such applications, a constraint on lowest sensor separation that guarantees zero data loss with a mobile observer was discovered.
B. Kusy, HJ. Lee, M. Wicke, N. Milosavljevic, and L. Guibas [2] presented a protocol for data delivery to mobile sinks in wireless sensor networks. This protocol is based on information potentials, which extend the account for node mobility. It shows that, for local movement beside edges in the communication graph, and then the data potentials can be adapted using easy iterative distributed computation. Conversely, for a non-local movement, the potential field might change importantly, and iterative computation leads to packet loss and packet delivery delays. The mobility graph can be removed from training data and also used to predict future relay sensor nodes for the mobile node. Using the mobility graph, pre compute and efficiently store additional routing states in the sensor network. This enables the protocol to maintain uninterrupted data streams. This proposed method for mobility prediction that computes future relay sensor nodes as well as RSSI traces represents the edges of the graph. The simulation shows that, prediction increases the consistency of data delivery by up to 50% for mobile sensor nodes at walking speeds.
Gu Y., Bozda D., Brewer R.W. and Ekici E. [3] presented an effective way of prolonging wireless sensor networks lifetime and relaying data in the partitioned wireless networks. In this work, a partitioning-based protocol is obtainable that schedules the movements of MEs in a wireless sensor network such that, there is no data loss due to buffer overflow. Hence, Simulation outcomes shows that, the proposed Partitioning-Based Scheduling (PBS) protocol performs well in terms of reducing the least amount required for mobile element speed to avoid data loss, providing high unavoidability in inter-visit durations, and reducing the data loss rate while the mobile element is controlled to move slower than the smallest required mobile element speed. The collected data at the sensor nodes are usually broadcasted to the sink node through power efficient multi-hop routing protocols. Even though battery replacement and power/energy harvesting methods are under development, reducing energy/ power consumption of individual nodes still play the most important role in making the most of the network lifetime.
L. He, J. Pan and J. Xu [4] gives the optimal scheduling of mobile nodes limited mobility is of great significance to reduce this latency. Noticing on the on-demand mobile data collection situation, wherever data collection requests appear gradually and based on the fact that, quite a lot of close by requests can be combined and served from the same collection site, proposed a simplified Combine-Skip Substitute (CSS) method, which is shown to be able to reduce the data collection latency greatly. This also analyses the probability for the combination to occur and how many requests can be combined, to gain more approaching in its performance metric. The efficiency of the proposed scheme and then the accuracy of the logical results are proved through extensive execution. The wireless communication range between the mobile node and sensors is considered, then a simple but efficient online system for mobile elements is proposed that combines close by requests at any time possible. To verify its performance, analytical results are provided on how expected combination can occur, and how several requests can be combined. The scheme's complexity is analyzed and it is shown through its extensive simulation.
L. Kulik, E. Tanin, and M. Umer [5] explained about an efficient data collection which plays a vital role in power conservation in Wireless Sensor Networks (WSN). It has encouraged a number of research projects focusing on effective algorithms that decrease power consumption. There are a huge number of queries that in fact select only a subset of the nodes in a Sensor Network. Thus, the selective queries was concentrated that queries request data from a subset of a Sensor Network. Pocket Driven Trajectories (PDT) is presented which optimizes the data gathering paths by approximating the global minimal Steiner tree using solely local spatial knowledge. By measuring the effectiveness of all the algorithms, they also calculate a near-optimal solution, the globally estimated minimal Steiner tree. The PDT algorithm first determines the set of pockets for a given query and also aligns the aggregation tree to the spatially optimal path concerning these pockets. The use of participating nodes maximizes the path in the tree and equally minimizes the number of non-participating nodes. To minimize the number of non-participating nodes in query processing can be demonstrated as NP hard that is known to be a minimal Steiner tree problem. The PDT algorithm is appropriate to the selective queries that often gather data from a comparatively consistent set of nodes over time.
L. Song and D. Hatzinakos [6] presented application specific and energy-limited are the two characteristics that play new challenges in the network design. This research is focused on sparsely deployed networks, wherever the simplified model of single node to sink transmission is deliberated. This simplified model helps us to understand the fundamental rules and facilitates the analysis behind the above mentioned tradeoff. This model does have a practical value, though it may not always be true that one sensor is within the communication range to the sink, it can be assumed that only one sensor in the range has packets of interest to the sink. There are multiple wireless channels available, assuming only one node will transmit in a specific channel. This network model is mostly useful for the previously mentioned traffic surveillance application. Thus, the results in the paper serve as the basis for the study of more sophisticated multiple nodes to sink transmission scheduling issues that rise in the densely deployed networks.
M. Zhao, Y. Yang and C. Wang [7] presented a three-layer framework used for mobile data gathering. Firstly, the sensor layer, which is a distributed protocol used to organize sensors into clusters, whereas each cluster can have multiple cluster heads. Clustering techniques proposed in previous works this protocol in contrast to balance the load of intra-cluster aggregation and allows dual data uploading between the mobile collector and multiple cluster heads. Secondly, the cluster head layer can have Multiple cluster heads within a cluster may cooperate with each other to perform energy well organized inter-cluster transmissions. Cluster heads do not transmit data packets from other clusters that effectively alleviate the burden of each cluster head different from other existing hierarchical schemes in this protocol. Instead, forwarding paths among the clusters are simply used to route small sized identification information of cluster heads to the mobile collector for improving the data gathering tour. Third, a SenCar Layer i.e. a mobile collector is deployed with two antennas called SenCar to allow simultaneous uploading from two cluster heads by using MU-MIMO communication. The SenCar gathers data from the cluster heads by visiting each cluster. It selects the end locations inside each cluster and concludes the sequence to visit them such that data gathering can be done in a minimum time. In this framework, meanwhile it is not difficult to deploy two antennas on the mobile collector, while a compatible pair of transmitting nodes and the locations of the mobile collector are specified, MU-MIMO uploading enabled to the mobile collector to significantly decrease data gathering latency.
R. Sugihara and R.K. Gupta [8] presented a different traditional multiple hop forwarding among uniform static nodes, use of wireless devices for data collection. In this work, focus on the drawback of finding an optimal path of a wireless device called “data mule” which is to achieve the smallest data delivery delay in the case of low energy consumption at each sensor node that is each sensor node only sends its data directly to the data mule. These formally define the routing path selection difficulty and show the difficulty is NP-hard. Numerical execution demonstrate that, approximation protocol successfully finds the paths that outcomes in 10%-50% shorter delay compared to earlier proposed approaches, suggesting that controlled mobility can be exploited much more efficiently. Routing path selection is to determine the trajectory of the data mule in the sensor field. Towards collecting data from each node, the data mule desires to go inside the node's communication range atleast once. There can be some restraint depending on the mobility capability of data mule on the routing path, such as the low turning radius. Forbidden mobility for data collection in sensor network provides flexibility in the exchange between energy/power consumption and data delivery delay. In this work, improving the delay in pure data mule method with the low energy consumption is focused with the goal of optimizing this tradeoff.
S. Chen, A. Dunkels, F. Osterlind, T. Voigt, and M. Johansson [9] presented a secure time synchronization service. Based on the time synchronization service, time slotted data gathering is implemented and results are presented that show that this way we can provide a predictable data collection service. Furthermore, time synchronization enables among further things ordered event classification as well as the probability to organize a TDMA schedule. Towards this end, they have designed and employed a secure time synchronization service. As TPSN, the time synchronization protocol figures a tree structure which is used to perform a pair-wise synchronization mechanism. The security services exploits the hardware based AES security operations supported by the CC2420 radio is implemented. Time synchronization protocol results that has a low overhead in terms of message exchanges and also achieves a predictable data collection service and low latency.
X. Li, A. Nayak, and I. Stojmenovic [10] explained about the essential tasks to gather sensor readings from the sensory field at data sinks. Investigation has shown that sensor nodes near a sink node deplete their battery power quicker than those far apart due to the heavy overhead of relaying messages. Power consumption/non-uniform energy rate causes corrupted network performance and the shortened network lifetime. Power-aware routing has been considered to avoid energy scarce sensor nodes and attain network lifetime improvement. Energy efficiency by actuator mobility may be classified as controllable or uncontrollable in common. The previous work is commonly attained by attaching an actuator sensor node on some mobile entity node such as, human or shuttle bus, which already exists in the placed environment and is out of control of the network. To make the most of energy saving, direct-contact data collection scheme is the best option. In this method, a mobile actuator node visits data source nodes and obtains data's directly from them by one hop communication work. It will actually carry collected data to sink if it itself is not a sink node. Its important concern is computation of the best actuator node tour that covers all data sources and reduces travel distance.
In Wireless Sensor Network, data gathering is the fundamental function. In data gathering, the sensed data is collected by some of the sensor nodes and are forwarded to the central Base Station (BS) or Sink for further processing. Data gathering methods has dissimilar strong and weak points about data gathering energy consumption and delay. Mobile Data Collectors are neither sources nor destinations; they simply act as intermediate nodes to gather data. All the collected data can be reached to a Sink. Sinks are the destinations of information that can collect data either directly or indirectly using intermediate nodes. It can move everywhere and gather the data. Their mobile nodes have high energy. Sink connects the sensor network to the user through the internet or some other networks and also it is the responsible for traffic handling and signaling. The path between the sink and node is not stable and changes with time. Path between node and sink is multihop. Figure 1 explains how the data can be gathered from the source to destination.

Figure 1. Data Gathering Process
Mobile data gathering is proposed for multihop communication in transferring data to a sink in Wireless Sensor Networks. Single-hop communication and multihop communication are two basic communication designs that are used in the WSNs. In single-hop communication, where data packets are directly transmitted to the Cluster heads or base station without any relay, the nodes located farther away have greater energy burden due to longer communication, and thus these nodes may die out first. i.e. the member nodes or CHs tend to reduce their battery energy faster than other nodes in a network. To overcome this problem multi-hop communication among member nodes and then their respective CH and also between the Cluster heads and the base station is used. The same communication approach is implemented for both inter-cluster and intracluster communication. Here multihop routing algorithm can be described.
Initialization: The set of all the neighbors of the tagged node, denoted by Ω;
while there is a packet to be forwarded do
Calculate the distances from every neighbor to the destination;
Check the Packet ID in the Transmission Table;
if the Packet ID is duplicated then
Get the next-hop node, denoted by nh, from the Next-Hop Node ID field in this Packet ID record;
Find the neighbors whose distances to the destination are larger than that of nh; these neighbors form a set denoted by Ω_;
Find a neighbor in Ω' which is closest to the destination, denoted by n 'h;
else
Add the Packet ID in the Transmission Table;
Find a neighbor in Ω which is closest to the destination, denoted by n 'h;
end if
Use n 'h as the next hop and update the Next-Hop Node ID field with n 'h in this Packet ID record;
Forward the data packet to n 'h;
When the next-hop node n 'h transmits the packet, the tagged node extracts the value of E1 from the packet header;
if El < E0 then
Remove the node n 'h from the neighbor set Ω;
end if
end while
Trajectory Planning starts from the data sink and visits some location that cover the broadcast range of mobile collector, and finally it reaches the data sink.
Here a moving trajectory can be described as,
i=1
flag= 1;
while (flag==1)
Divide the network into 2l-1 clusters;
for j=1 to 2l-1 do
Find the best turning point in jth cluster from all possible locations of turning points;
Add the best turning point into the moving trajectory;
if the total moving distance/ time cannot satisfy the constraints after the new turning point is added.
flag=0;
Remove the new turning point from the path;
end if
end for
I++;
end while
The problem of data gathering in sensor networks is encountered in many scenarios and the examples include, monitoring the physical environments such as, tracking animal migrations in remote-areas, habitat monitoring on remote islands, weather conditions in national parks, city traffic monitoring, etc. The objective is to gather the data from sensors and deliver it to an access point in the structure. These systems are predictable to run unattended for long periods of time (order of months). The primary constraint is the energy budget of the sensors which is limited owing to their cost and size. Recent study shows that, significant energy saving can be achieved in mobility-enabled Wireless Sensor Networks (WSNs) that visit sensor nodes and gather data from them through shortrange communications.
However, a major performance bottleneck of such WSNs is the significantly improved latency in data gathering due to the low movement speed of mobile base stations. Now large-scale Wireless Sensor Networks, leveraging data sinks' mobility for data gathering has drawn extensive interests in recent years. Modern researches either aims on planning a Mobile Sink's (MS's) moving path in advance to achieve optimized the performance of network, or aims at gathering a minor portion of sensed data in the network.
The proposed Delay Aware Secure Multihop Routing (DASMR) protocol construct a mobility-based auspicious network management architecture to exploit the network lifetime, connection time, residual energy, throughput and stable link for mobile sensor nodes in WSNs. Each cluster member chooses the cluster head with better connection time and forwards the data packets to the corresponding cluster head in an assigned time slot. Similarly, the mobile sink elects the one-hop neighbor or polling point with maximum threshold value, connection time and with less network traffic.
The objective of this protocol is to select a cluster head which is near to all other nodes in the cluster, and then minimizes the communication control required to transmit data from a cluster member to a cluster head. Hence, the cluster heads are well-defined as the intermediate nodes in the cluster. These produced data has to be delivered through wireless sensor interface using multihop communication toward a sink. This protocol also reduces the delay of data delivery from the sensors to the sink.
Figure 2 explains the architecture of DASMR protocol that is how the data can be gathered from the Sensors to the Mobile Sink by trajectory planning.
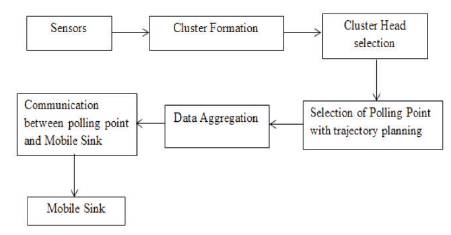
Figure 2. Architecture of Delay Aware Secure Multihop Routing Protocol
The sink node shows an initial data packet to the node located in the networks by a given transmitting power before the cluster formation. When the nodes receive the broadcast packet, the distance between itself and sink can be computed according to the received signal strength. Later, each node broadcasts the information of its identification, the distance and residual energy to the sink node. A sensor being a cluster member; should randomly associate itself with a cluster head among its candidate peers for load balance purpose. Identification is the unique number of neighbor nodes. All the nodes, Cluster heads and the sinks should have proper communication through the network.
After the cluster formation, the base station will select a cluster head for each cluster according to the location information of the nodes. A node to be a cluster head, it has to locate at the center of a cluster. When a node is selected to be a cluster head, it broadcasts a message in the network and requests other nodes to link its cluster.
After some time, the other nodes will select their own cluster heads and then send data according to the power of the several received broadcast messages. Once the cluster head receives the data from its neighbor node, it assigns the node a time slot to transmit data. When the first round is over and the primal cluster topology is created, the sink is no longer responsible for selecting the cluster head. The task of the cluster formation is moved from the sink to the sensor nodes. The decision to become a new cluster head is created locally inside each cluster based on the node's weight value. After the cluster head selection, all the cluster heads can forward the data to the Polling point with multihop techniques. Cluster Head to Cluster Head is multi hop using routing protocol.
In this phase, to optimize the trajectory of SenCar, it is focused for the data gathering tour with the Cluster Head Group information which is referred to as mobility control at SenCar layer. SenCar would stop at some selected polling points within each cluster to gather data from multiple cluster heads via single-hop transmissions. Therefore, finding the optimal trajectory for SenCar can be reduced to find selected polling points for each cluster and determining the sequence to visit them.
To find the optimal polling points among the sensor nodes, tour of the mobile collector and the routing paths are considered. If the mobile collector is available, then the data gathering is divided into two methods. Firstly, the sensors that are selected as Polling Points are capably scattered and be situated near to the data sink. Secondly, the number of Polling Points is lowest below the control of the relay hop bound. The trajectory planning is used for good paths which result in the improved localization coverage and accuracy of the sensor network whereas keeping the path distance bounded.
After the setup formation and selection of Polling point, the data started aggregation process. Data aggregation is a process of aggregating the sensor data. Sensor nodes can aggregate the information from Cluster Head and forward that information to Polling Point. After the data forwarding process, all Polling Point can have data. Then Mobile Sink can collect the data from the assigned or Structured Polling Point and finally reaches the Mobile Sink. Figure 3 explains the process of data transmission in Multihop clustering.
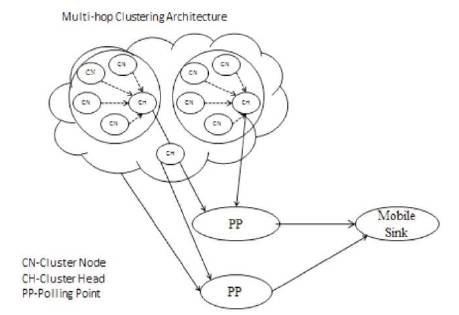
Figure 3. Data Transmission to Mobile Sink
The performance of the proposed protocol is calculated through GloMoSim simulator and assumes that a group of sensor nodes is uniformly deployed in the sensing field. The simulation parameters and values are summarized in Table 1.

Table 1. Simulation Environment Settings
The performance is evaluated mainly according to the parameters, collision, throughput, end-to-end delay and Energy consumption. Figure 4 (a) to (d) show the performance of this proposed protocol.
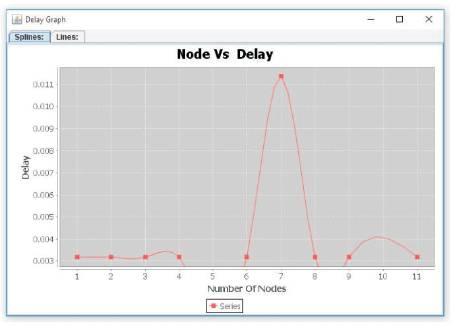
Figure 4(a). Node vs Delay
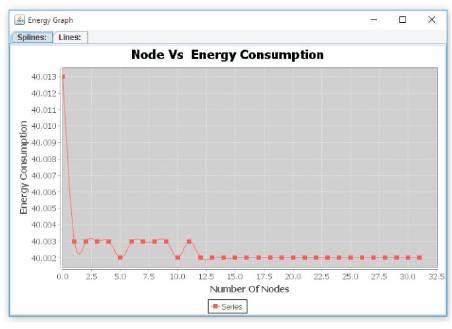
Figure 4(b). Node vs Energy Consumption
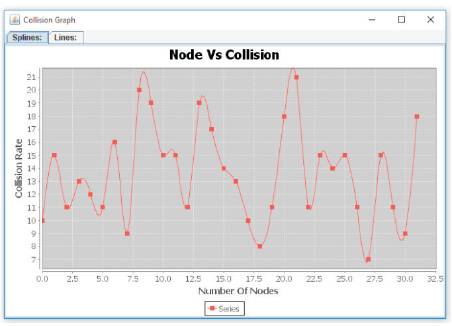
Figure 4 (c). Node vs Collision
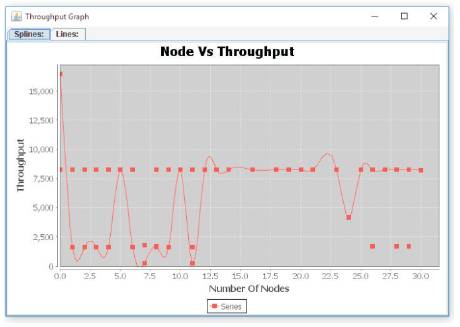
Figure 4 (d). Node vs Throughput
Mobile data gathering is performed using Mobile Collector with trajectory planning. This proposed Delay Aware Secure Multihop Routing (DASMR) protocol is used to find polling points and compatible pairs for each cluster. A discretization scheme should be developed to partition the continuous space to locate the optimal polling point for each cluster. Then finding the compatible pairs becomes a matching problem to achieve optimal overall spatial diversity. This proposed protocol decreases the computational and communication load in the data gathering process. The simulation results demonstrate that DASMR is more reliable, energy efficient and prolong the network lifetime significantly compared with the previous data gathering schemes. An algorithm that adapts to the current MIMO-based transmission scheduling and how to schedule MIMO uploading from multiple clusters should be studied in future.