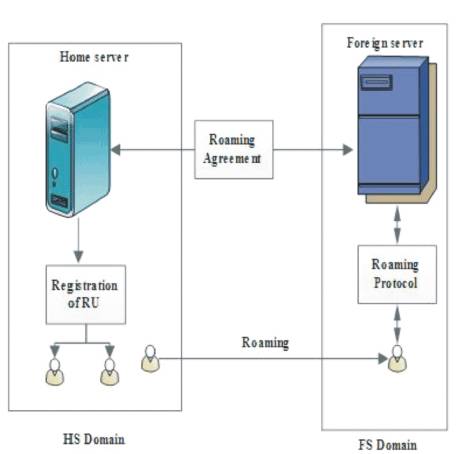
Figure 1. System Architecture
The secure roaming service, the foreign server must authenticate the roaming User, who originally subscribed to the home server. Hence, an authentication mechanism is currently important in the requirement for providing secure roaming services and protect the location privacy of users on anonymous authentication. The anonymous authentication process is without participating the home server on efficiency communication for existing work. The process of authentication causes high computation costs and huge revocation lists. So the authors proposed a novel three-round anonymous roaming protocol. The proposed protocol uses a pseudo-identity-based signcryption scheme and using CK-model to perform efficient revocation with a short revocation list and efficient authentication. The use of a signcryption algorithm minimizes the storage in a Subscriber Identification Module (SIM) card with limited storage capacity. The authentication efficiency is also higher than that of existing protocols.
With the event of wireless technologies, mobile services have dramatically exaggerated to produce a lot of convenient life to individuals. Among these services, the roaming service permits mobile device users to use network services even after they reside in foreign domains. The fundamental roaming service involves a home server, a foreign server, and a roaming user. For secure roaming service, the foreign server should manifest the roaming user, United Nations agency originally signed to the house server. Hence, an authentication mechanism is a crucial demand for providing secure roaming services. Roaming services ought to be secure, i.e., offer authentication to identify legal roaming users. Similarly as security, location privacy ought to be provided to guard trajectories of roaming users, analysis studies on privacy-preserving methods for shielding location information are carried out [1]. Above all, varied anonymous authentication strategies are projected to realize secure authentication and site privacy at the same time. According to [2], anonymous authentication may be classified into 2 types: weak user namelessness authentication and strong user namelessness authentication. The former hides the user's identity solely from third parties, such as general communication nodes (e.g., neighbor's mobile phones) or malicious nodes (e.g., eavesdroppers), whereas the latter hides the user's identity even from foreign servers, i.e., communication service suppliers that exist in foreign domains. Roaming protocols can be divided into 2 types: three-party protocols involving a home server and twoparty protocols that don't involve a home server. In recent years, varied three-way protocols are planned for anonymous authentication [3]. These protocols need at least four rounds of communication since 2 rounds are needed for an overseas server to amass authentication information on a roaming user from a home server. It is also obvious that Associate in nursing authentication method within the three-party type is influenced by the state of the house server, which can be a bottleneck and one purpose of a failure. Additionally, these protocols ought to open a communication connection between an overseas server and a home server without Associate in nursing authentication method whenever a roaming user requests roaming services, that can be exploited by associate in nursing adversary to eat up resources of the foreign server.
Recently, two-party roaming protocols that don't need the assistance of a home server throughout roaming are proposed. Yang et al. [2] projected 2 two-party roaming protocols. The primary protocol fails to produce robust user anonymity, whereas the second involves high procedure costs once generating the cluster signature that is predicated on bilinear pairing operations. Additionally, the second protocol does not offer backward unlinkability, which suggests that the past protocol logs of a revoked user ought to stay anonymous and unlikable, as a result of an overseas server who will trace the users’ past info once a revoked user's revocation secret is delivered to the foreign server.
To remedy these issues, He et al. [3] projected a roaming protocol which supported a bunch signature with backward unlinkability [4] that incurs a high roaming authentication value for the roaming user. For backward unlinkability, it provides every roaming user with N secret keys, wherever N is the system parameter in [3]. As N increases, the property of backward unlinkability becomes stronger. However, during this protocol, the revocation value and revocation list size increase with the quantity of revoked users and N. This serious checking operation can be exploited by associate degree person to launch a resource depletion attack on the foreign servers. He et al. [3] also proposed a pseudo- identity based roaming protocol victimization bilinear pairing operations to produce foreign servers and roaming users with economical cryptanalytic operations. Unfortunately, this protocol doesn't shield each non-public keys associate degreed session keys of roaming users from a person since the non-public keys and session keys will be computed from messages which will be obtained from easy eavesdropping. The complete description on the way to calculate a private key and a session key's shown in [5].
To provide potency, light-weight roaming protocols based on many techniques have additionally been projected. In the protocol of [6], roaming users use solely a centrosymmetric encryption algorithmic rule and a hash algorithmic rule for roaming. However, though this protocol is economical as a result of the use of lightweight algorithms, it's a many-sided protocol that requires the participation of a home server and uses one pseudoidentity per roaming user; that's, this protocol depends on the state of the house server and does not give unlinkability. Another light-weight protocol based on an additive pairing operation was projected in [6] that additionally depend on the house server since it is a many-sided protocol. Recently, economical protocols that use the chameleon hash operate were projected in [7] and [8]. In these protocols, a remote server computes a chameleon hash operate on a message sent by a mobile node to evidence the node. However, these protocols have subsequent security issues. The protocol of [7] does not support namelessness for roaming users since a mobile node sends its own certificate as well as identity to a foreign server within the protocol of [8], anyone will link messages sent from a mobile node by mistreatment of the chameleon hash function since, though the mobile node sends completely different messages all the time, the results of chameleon hash operate on the messages are invariably identical. Thus, the protocol of [8] doesn't guarantee the unlinkability of roaming users.
The planned roaming protocol includes a Home Server (HS), a Roaming User (RU), and a Far off Server (FS), as shown in Figure 1. In this structure, every server (HS and FS) performs the role of a non-public Key Generator (PKG). Before connection roaming services, every RU is registered with its HS. We tend to additionally assume that the HS and FS create an agreement for roaming services and make a roaming key. Every server and roaming user additionally possess a signing/ verification key to be used in a very typical digital signature formula (e.g., ECDSA [9]) and that they have info regarding the general public parameters of all servers, they are assumed to be synchronic at Greenwich Mean Time (GMT).

Figure 1. System Architecture
We assume that the HS could be a sure entity since it will trace the real identity of the ruthenium to supply it with mobile services and to request services charges. There's a secure channel between the HS and ruthenium to shield the registration method of the RU. The secure channel is established victimization secure protocols like TLS or SSL. Additionally to the higher than assumptions, we have a tendency to assume a polynomial time opponent WHO that has the aptitude to manage the communication, for example, modifying, injecting, monitoring, and deleting messages over the air. The goal of the opponent is to penetrate anonymous authentication of a roaming protocol by compromising needs for the roaming protocol described below.
A roaming system ought to contemplate not solely on security, however, also privacy. To produce secure roaming atmosphere, mutual authentication, key institution, and the CK model ought to be used. Anonymous authentication that supports namelessness and unlinkability ought to even be designed for location privacy.
Authentication is needed to make sure that roaming services area unit is offered to legitimate entities. Thus, roaming protocols ought to give mutual authentication between associate metal associated an FS. To produce secure authentication, the signature algorithms employed by roaming protocols ought to be unforgetable by associate individual.
After roaming authentication, the metal and FS ought to establish a random session key that solely they share. This means that the shared key ought to be inaccessible to third parties and also the HS. Moreover, the roaming protocol ought to be secure within the CK model.
In a roaming system, the identity of the metal will frequently be overheard, thanks to the system's wireless nature. If the roaming system uses a normal digital signature, the signature leaks the RU's identity info [2]. This info may be used to trace the metal. Thus, no entity aside from the HS and metal ought to understand the identity of the metal throughout an authentication method roaming service (anonymity). Moreover, solely the HS ought to be capable of linking any past or future protocol runs of associate metal (backward unlinkability).
The HS ought to be capable of getting the RU's real identity from its pseudo-identity once the signature used on the roaming system is in hand or once the message contains false contents.
If the RUs area unit is nonfunctional, the roaming system should be ready to exclude them from the system to maintain its lustiness.
In this section, the authors have proposed a signcryption based roaming system, that principally consists of 2 phases, i.e., an initial method section Associate in Nursing and an anonymous roaming system phase.
HS initial performs the initial method section that consists of Associate in Nursing HS setup step, a roaming agreement step and a registration of metallic element step for preparation of roaming service. In the HS setup step, HS generates its own public parameters and secret values. Upon finishing the HS setup step, the roaming agreement step and also the registration of metallic element step are conducted to issue secret values of FSs and RUs. The anonymous roaming system section consists of a roaming protocol step and a revocation step. Within the roaming protocol step, the projected roaming protocol satisfies requirements. In the meanwhile, the revocation step supports the roaming protocol step to exclude malicious RUs from the projected roaming system. The entire process has been shown in Figure 2.
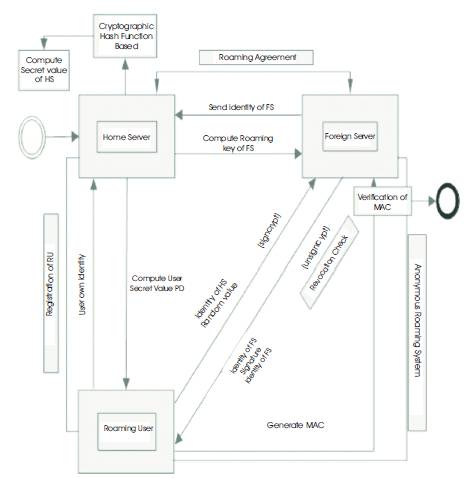
Figure 2. Overall DFD
Algorithm 1:
Update Revocation List
Input : tj , RLtj-1 , RLtj
Output : RLtj
While Processing all elements of RLtj-1 do
Generate revocation value
RevInfoi , tj = H5, rvi (RevInfoi,tj- 1 )
RLtj-1RevInfoi,tj-1
RLtj = RLtj -1 U RLtj
return Rltj
Algorithm 2:
Revocation Check
Input : tj,PIDi,j,Rltj
Output : Result
Parsing TIj and RevInfoi,j from PIDi,j
if TIj – Current time interval = 0 then
if RevInfoi,j ε RLtj then
Result revoked
else
Result legitimate
else
Result expired
return result
The proposed system used a novel three-round anonymous roaming protocol that does not require the participation of home servers. This protocol uses a pseudo-identity-based signcr yption scheme. The authentication efficiency is also higher than that of the existing protocols. The proposed protocol is formally proved in the Canetti-Krawczyk (CK) model.
The home server setup initial process is the cryptographic hash function used to find the key; here the authors used a keyed hash chain to revoke malicious users. Next computed the secret key of Home server. The roaming key of home server is the Home Server secret value. This process is shown in Figure 3.
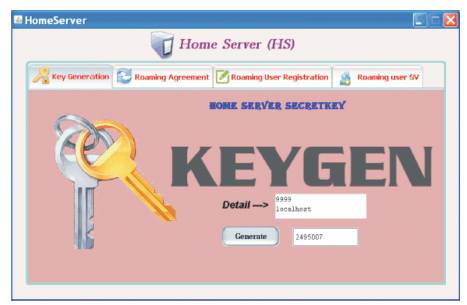
Figure 3. Home Server Setup
The Home Server after completing its setup process, it establishes a roaming agreement to generate the roaming keys of each foreign server. All foreign servers send their identity as request to the home server for secret agreement. Then home server computes a roaming key for foreign server. The next process is that home server sends roaming key to all requested foreign servers through a secure channel. The process of roaming agreement can be shown in Figure 4.
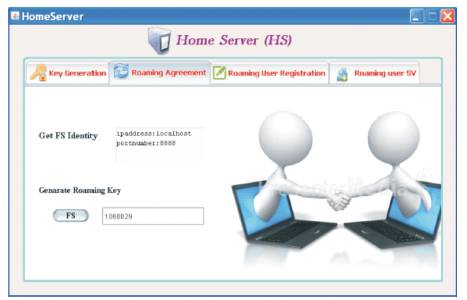
Figure 4. Roaming Agreement
In this module, the Roaming user is going to register their details such as own identity in the home server using secure channel. Home servers get the roaming user identity to compute the roaming user pseudo-identities and roaming user secret value and then sending it to the roaming user. Then secret value is saved as roaming user's private key. This entire process is shown in Figure 5.
Figure 5. Registration of Roaming User in Foreign Server
Roaming user sends request containing identity of HS and newly generated Random values and so on by signcrypt. Then foreign server accepts the request by unsigncrypt. At that time, revocation check process is also carried out. After successful completion, it sends response with identity of FS and Signature. Roaming user finally sends the MAC address for requesting connection then allows them after verification. Hence this proposed scheme is known as an anonymous roaming protocol. The process of Anonymous roaming system is shown in Figure 6.
Figure 6. Anonymous Roaming System
In this section, the authors analyze the proposed roaming system.
When an RU roams from the HS's space to AN FS's space, the RU and FS exchange a signature with one another. If these signatures are square measure verified with success, they're reciprocally authenticated since the signature algorithms [1] used in the proposed protocol square measure are unforgeable. If a polynomial time adversary A will generate the signature σPIDi, j of RUi on a changed message M, this contradicts the results of [8] . Likewise, the unforgeability of the ECDSA signature formula is established in [1]. Hence, if A doesn't recognize the private keys of roaming entities, the signatures utilized in the proposed protocol can't be cast at intervals of polynomial time.
In this paper, the authors have used a signature-based protocol applying the Diffie-Hellman key exchange methodology. In this roaming protocol, a polynomial time person A cannot confirm whether or not the output of a test-session question could be a real session key or a random worth. The protocols in [9] and [8] area unit are insecure within the CK model, since, given the output of a test-session question from these protocols, one will simply tell whether or not it's associate honestly generated session key or at random designated worth by analyzing the flows of those protocols. Within the case of the protocol in [3], associate resister will acquire the output of a test-session question. Mistreatment of this output worth as a decipherment key, the resister will simply confirm whether or not it's a session key by decrypting the third flow of this protocol. Likewise, given the output of a test-session question in the protocol of [8], the resister will simply confirm whether it's a session key by computing the hash perform value, that generated mistreatment the given output and public information, and by comparison the hash per form worth with the authentication data of the second flow of the protocol [8].
In the proposed system, every server will exclude revoked RUs from the roaming method by causing its revocation list to alternative servers. The revocation method is represented in Algorithms one and two.
The first message of the roaming protocol includes RUi's signature. The FS performs additional roaming processes in case RUi's signature is valid. What is more, the FS doesn't need extra communication with the HS since the protocol is composed of RUi and also the FS. The new protocol additionally provides a lot of economical revocation method than do those of [9] and [2] . Thus, the protocol will mitigate the effects of affiliation depletion attacks and resource depletion attacks to a bigger extent than existing two-party roaming protocols.
In this section, the authors tend to measure the performance of the new theme by examination thereupon of existing two-party protocols. The authors compare new protocol in the main with existing two-party roaming protocols [2], [3] as a result of these, protocols assure functionalities that are analogous to those provided by the new protocol. In this analysis, Tmul denotes the time needed to perform associate elliptic curve multiplication on G1, and Tpar denotes the time needed to perform an uneven additive pairing operation. The authors tend to assume that the cost of associate exponential computation is up to that of elliptic curve multiplication, and that we ignore light-weight computations, such as cryptanalytic hash perform computations and map-to-point hash operations. To simulate elliptic curve multiplications and additive pairing operations, the MNT curve with associate embedding degree vi is enforced on associate iPhone 3GS, iPhone4S, and Intel Core i5-2500 using the Pairing-Based Cryptography (PBC) and also the GNU Multiple Precision(GMP). The comparison of authentication costs at roaming users is shown in Figure 7.
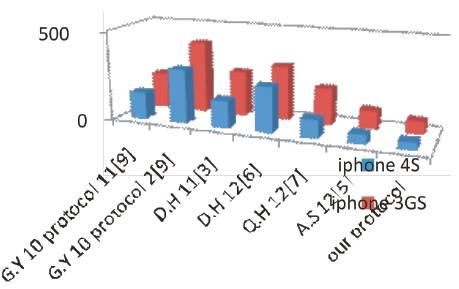
Figure 7. Comparison of authentication costs at RU
Two-party roaming protocols want revocation lists to revoke invalid users. A revocation list contains the revocation info associated with every revoked atomic number 44.The second protocol in [2] and therefore the protocol in [3] use cluster signature algorithms to evidence users anonymously
The revocation list of [3] always includes new revocation values of users who have antecedently been revoked. As an example, although the revocation list of the jth interval has the jth revocation worth of a revoked RUi, the (j + 1) th revocation worth of the RUi ought to be included within the (j + 1) th revocation list, since there is no relation between the 2 values. This means that the revocation list continuously includes R revocation values if there are Rrevoked RUs. However, in this revocation list, the hash component and revocation key of a revoked RUi seem just one occasion since the revocation values in future time intervals are generated by using a keyed hash chain. In terms of the period of a revocation list, this revocation list size is constant regardless of the period, whereas the revocation list size of [3] will increase in proportion to the period.
To evaluate the authentication value, we have a tendency to think about the atomic number 44 and FS. Since the FS ought to check the state of a signature sent by atomic number 44, once it performs signature verification, both the signature verification time and revocation check time are thought of for activity of the authentication value of the FS. On the opposite hand, for the RU, solely the signature verification time is taken into account. During this comparison of authentication prices, public key operations are counted as follows: the Diffie- Hellman key exchange takes two Tmul, and the ECDSA [9] takes one Tmul for sign language and one multi Tmul (1.25 Tmul) for verification.
We tend to compare the metal authentication time of the protocols principally in [2], [3] , [10], [7], and [8] of the new protocol, since these protocols area unit of the two-party sort.
The computation overhead on the FS is a vital parameter for evaluating the time needed by the roaming authentication system, since RUi ought to anticipate the FS's response to use a roaming service. Within the following comparison, we tend to exclude the protocols in [10] , [7], and [8] as they are not assuring namelessness or revocation for a roaming system.
A human will send several authentication requests as the first step of launching association depletion attacks and resource depletion attacks. The authentication requests will be divided into 3 sorts. The primary could be a valid request containing a valid and unrevoked signature. It need each verification of the signature and a revocation check. The second could be an invalid request containing associate degree invalid signature. In this case, the invalid signature doesn't pass the verification check with success. The third could be a revoked request containing a revoked signature. Since the revoked signature passes the verification operation with success, a revocation check method is critical to see the condition of the signature.
In this protocol, RU is authenticated by FS at the primary spherical as a result of the first message sent by RU includes its own signature. Thus, this protocol doesn't perform in subsequent rounds if there exists a false authentication request (invalid request or revoked request).
Consistent resource exhaustion attack on FS will cause server failure. Associate degree human is ready to send an out sized range of authentication requests to have an effect on the roaming service. Many false authentication requests performed by humans might have a definite impact on the server's resource consumption. Thus, the authors have a tendency to valuate the effects of resource depletion attacks forward that there are an outsized range of false authentication requests. The authors plotted the additional computation time of the FS in terms of Pinv and Prev once the quantity of roaming requests is set to one hundred and also the range of revoked users is set about to 1000.That the protocol needs lower computation time than alternative protocols. The distinction in computation time between our protocol and other protocols will increase because the range of roaming requests and also the range of the revoked users increases. This implies that our protocol needs fewer computation resources within the face of the resource depletion attacks victimization and false authentication requests than alternative protocols do.
In the roaming protocol, RUi stores K pseudo-identities, K personal keys, and public parameters. Suppose that the pseudo-identity (PIDi,j), private key (si,j), and public key (P,Q,Qpub) area unit appointed values of fifty two (4 + twenty + twenty+8) bytes, 20bytes, and sixty (20 + twenty + 20) bytes, severally, since the authors set the order p of the elliptic curve to one hundred sixty bits. K and the interval TI area are the unit variables associated with the storage capacity of the SIM card and also the update interval of pseudo-identities. In line with a SIM card's storage size ranges from 32KB to 128KB. Hence, TI and K are unit can be determined by the subsequent equations. For example, if the SIM card storage size is 128KB and the update interval could be a quarter of a year, TI is set to concerning one.2 h. This implies that the FS links RUi for only 1.2 h.
In roaming protocol, associate degree RUi obtains PID* and s* from the HS. If the assigned roaming periods of the RUi have passed, the RUi should update its PID*i and s*i. The update frequency is reciprocally proportional to the interval TI. The update method will cause transfer delays, however the event of wireless technologies will result in improved transfer speeds within the future. As an example, Third Generation Partnership Project (3GPP) technologies supported the future Evolution (LTE) and LTEAdvanced standards that can provide higher capability with a peak rate of up to 340 Mb/s. In real environments, Verizon Wireless recently incontestibles a mean transfer speed of 5-12 Mb/s. Thus, the update delay for many hundreds of kilobytes isn't a significant burden.
The update frequency and linkability ought to be decreased within the roaming service. However, TI increases if the update frequency decreases. A large TI causes the FS to link RUi for a protracted amount. Thus, the system parameter TI and update interval should be set properly by considering the restricted SIM card storage capability, network setting, and privacy of Rui.
The authors enforced a C library of anonymous roaming protocol that relies on PBC, GMP, and OpenSSL (The Open supply toolkit for SSL/TLS) to visualize the feasibility to be used in Associate in Nursing actual user mobile device. The run-time of Associate in nursing authentication algorithm on a mobile device ought to be but 500ms. To gauge the performance of the library, the authors performed running every perform 50,000 times by victimization iPhone 4S (RU) and Intel Corei 5-2500(HS,FS). Through the performance check of our library, it seems that the total of average period of time of our protocol on a mobile device (iPhone 4S) is one hundred and five.
In this paper, the authors tend to have planned to associate anonymous roaming protocol using signcryption. Existing trilateral roaming protocols require the help of home servers, whereas two party roaming protocols have weak security measures (weak anonymity, insecurity within the CKmodel, backward linkability, and outpouring of the session key) or in efficient operations (high authentication and revocation costs). However, unlike these protocols, our protocol doesn't want the support of the house server, associated includes an economical anonymity authentication method and a quick revocation method. Furthermore, the protocol is secure within the CK model and it provides roaming users with robust erobscurity and backward unlinkability. The authors tend to evaluate the potency of our protocol by comparing it with the existing protocols and by implementing a model of the protocol.