Figure 1. Twofish Cryptographic Architecture
In today's information technology world, cloud computing plays a major role. Cloud computing is dynamically flexible as well as sizable and cost-efficient including important virtual tools. Data security is the main concern in cloud computing. Different encryption techniques have been introduced to secure cloud computing, but the data is constantly under threat due to security exploits. This paper presents a hybrid Crypto method using updated RSA and TWOFISH algorithms to protect data integrity and security in cloud computing. The proposed technique is robust, fast and demonstrates better performance results. This research also highlights many security risks and solutions in cloud computing.
In recent years, Cloud Computing has captured a significant part of the virtual world with its productivity and effectiveness. Cloud networking is an extremely flexible way of computing, which is exceptionally adaptable as per the need of user. The primary purpose of choosing cloud computing is to limit the use of resources and reduce the cost. Despite being so resourceful, cloud networking has plentiful security issues. One of which is an invasion of the client's private resources by Denial of Service (Malik & Om, 2018).
Cloud computing is not only beneficial for everyday users but also for large originations, as it is capable of sharing large data in different forms. This makes sharing so risky and almost impossible to trust the client.
The term cloud computing came from "on-demand computing" where data is shared over the internet. Since cloud computing is based on open network environment, security issues arise now and then, mostly concerned with privacy and trust (Kaur, 2012). Thus, it makes important for us to do this research and apply new techniques to prevent security problems. Flooding attacks cause both direct and indirect denial of service (DoS). Usually, when a cloud finds a lot of requests for a particular server, it accounts for additional computing power for that service to handle all the requests. This is the general idea of cloud computing. However, in the real situation, this would provide an advantage to the “hacker”. After that, the hacker should only focus on his flooding attack on a single server so that he can gain access to cloud account services. This service is known as direct ' Denial of Service' because the hacker focuses on a particular service to get it down. (Wu et al., 2007).
The cryptographic algorithms such as Symmetric, Asymmetric and Combination key algorithms are used for data encryption and its key will make the secure cloud network and maintain data privacy. Encryption is the process in which one can encode a message or data into an unreadable format so intruder cannot read it. The user has plain text when it is encoded into an unreadable format using one of the encryption technique, This it is called as ciphertext. After being received by the correct receiver, he can decrypt it into the original plain text. The purpose of encryption is to attain data confidentiality (Bhise & Phursule, 2017).
Each of the encryption techniques has its own strong and weak points. In order to apply a suitable cryptography algorithm to an application, we should know the performance, strength, and weakness of the algorithms. While reviewing a scheme, we listed the algorithms and techniques used in that scheme and the merit and demerit of that scheme are also specified Symmetric key cryptography algorithms are AES, DES, 3DES, IDEA, BRA and blowfish. The main issue is to deliver the key to the receiver in a multi-user application. These algorithms require a low delay for data encode decode but provides low security. The public key cryptography algorithm is RSA and ECC algorithm. Public and private keys are manipulated into public-key cryptography algorithms. These algorithms accomplished high-level security but increase delay for data encode and decode.
In Ramesh and Suruliandi (2013), the selected encryption algorithms namely DES, AES, and BLOWFISH were used for performance evaluation. Blowfish consumes less memory compared with AES and DES. However, AES showed poor performance results compared to other algorithms.
The RSA algorithm (Ramesh & Suruliandi, 2013) is a typical asymmetric encryption algorithm, which is widely used not only for user data encryption but also as a digital signature. However, considering that, the encryption and decryption efficiency of the algorithm is low, it is not suitable for the encryption of large amounts of data.
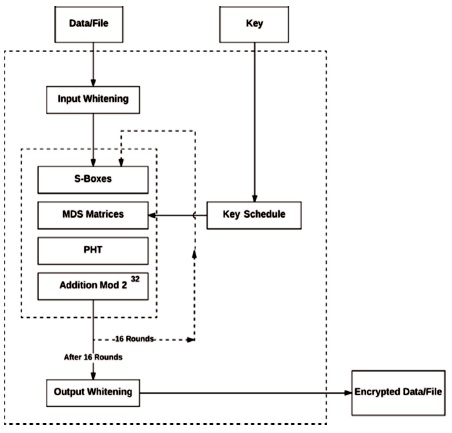
The Twofish algorithm approach is the replacement of the Blowfish algorithm based on AES framework standards. It is pre-calculated and has more speed than AES. The main length can be 128 bits, 192 bits, also 256 bits. No feeble keys exist in Twofish encryption. It is also extremely adaptable in the model and can easily be used as a portion of an extensive variety of applications while working at a protuberant speed. Twofish has 128-bit plaintext (divided into four parts of 32-bit each) for the input whitening where it is XOR-ed with four keys followed by the function g PHT, which are explained under the heading Twofish functions and modules. Twofish cryptographic architecture is shown in Figure 1 (Rane, 2016).

Figure 1. Twofish Cryptographic Architecture
Twofish additionally depends on the Feistel structure. After developing Blowfish, Bruce Schneier created developments to his cipher which resulted in Twofish that may be a symmetric cipher, having a block size of 128 bits and a key of any length upto 256 bits. The plain text is broken into two 32-bitwords and fed into the F-boxes. The two words are additionally broken down into four bytes among these F-boxes and sent through S-boxes, every smitten by totally different keys. The four output bytes are combined into a 32-bit word using the Maximum Distance dissociable (MDS) matrix. The Pseudo Hadamard Transform (PHT) is employed to mix the two 32- bit words. This can be then XOR-ed with the opposite half. Certain 1-bit rotation operations also are performed before and after the XOR operation (Rane, 2016).
There are different security risks in cloud computing like Poor Cloud security, Denial of service, Lock-in effect, Downtime. The other security risks like Resource exhaustion, Confidentiality and the Integrity of data in the cloud results in financial, economic and reputational losses and can make an organization inoperable. So there is an important need to study cloud computing security issues and find methods to minimize these risks and their impact.
So to mitigate the security threats in cloud storage, we must first understand trust issues linked to cloud computing storage. Generally, cloud computing users don't have full control over the available assets in the cloud and there is always the risk of data exposure. Our research is dedicated to address the common as well as rare issues that continue to in cloud computing and also to present effective technique (the combination of updated RSA and Twofish algorithm) to a vertany security concerns.
The idea behind cloud computing is to provide innovative data sharing services over the network, changing the way we used to share data resources before. Many enterprises want the minimal cost and effective benefits of cloud computing, without losing control and security. The security that is generally applied at the network border tends to disappear in cloud built computing, where networks without robust firewalls are connected by many types of cloud consumers with private and public data hubs (Kumar et al., 2011).
The authors describe the process of AES and RSA in their encryption and decryption process. They think the hybrid algorithm will improve the speed of RSA encryption and decryption, and also solve the key management problem in the AES algorithm (Liang et al., 2016). Fang presented an overview about the AES algorithm, and then the significance of security in the cloud storage system, and they proposed an approach to the security mechanism of users' files when uploading and downloading using AES algorithm (Fang et al., 2013). Any organization's or individual's data is stored in cloud storage and is accessible from multiple distributed and connected resources that comprise a cloud. To provide secure communication over distributed and connected resources, the encryption algorithm (Fang et al., 2013) plays a vital role. It is a fundamental tool for protecting the data.
The comparative study by Faung presented a different encryption algorithms such as; Asymmetric and symmetric, block cipher and stream cipher. These EA are AES, IDEA, DES, RC4 and RSA. At the conclusion, he found from the experimental results that RSA has least performance efficiency as compared to DES, AES, IDEA and RC4 algorithm. Also, conclude that the performance of RC4 algorithm is best compared to all other algorithms discussed in this paper (Fang et al., 2013). The author (Kouchay, 2017) introduces the combination of RSA and improved blowfish algorithm for encryption and decryption of cloud data. Although the combination is robust and secure, it affects overall encryption speed. Thus, we propose a better hybrid of updated RSA and Twofish algorithm to overcome the encryption delay and security issues in the previous technique.
Existing methods like DES and RSA algorithms experimented (Nigoti et al., 2013) for cloud storage security is only with single level encryption and decryption. This type of encryption can be easily breached. Several techniques like DSA and RSA and AES and RSA have been proposed by various researchers. But DES is extremely susceptible to attacks, Weak keys is also a big issue and is exposed to brute force attack (Elbaz & Bar- El, 2000). Various studies have emphasized the security and threats for cloud storage and cloud computing in general (Cloud Security Alliance, 2011; Cloud Security Alliance, 2013; European Network and Information Security Agency, 2015; Open Security Architecture, 2015; Kouchay, 2016; Wayne & Timothy, 2011). However, all these studies do not focus on publicly available IaaSbased cloud storage. The modified RSA (Li et al., 2010) confirms higher security by reducing modulus and private exponent in modular exponentiation. The decryption and signature generation enhanced by this method.
The space between implementation and innovation is wide enough to stop cloud computing users, with complete trust. So to remove this gap, we must first understand trust issues linked to cloud computing. Generally, cloud computing users do not have full control over the available assets in the cloud and there is always the risk of data exposure. Various researches have been conducted to address the common as well as rare security issues that arise constantly in cloud computing and also to present effective techniques to prevent such problems in the future (Cloud Security Alliance, 2011). The Schneier (1993) proposed Blowfish, a new secret-key block cipher. Also, this paper discussed the requirements of a standard encryption algorithm. While it may not be possible to satisfy all requirements with a single algorithm, it may be possible to satisfy them with a family of algorithms based on the same cryptographic principles.
The proposed framework uses a hybrid of updated RSA and Twofish algorithm to produce encryption whenever the user uploads data in the cloud storage. Twofish uses a secret key to encrypt the original data and send this key with encrypted data to the receiver. The risk involved in symmetric cryptography is to shift the secret key over the internet. To overcome the risk of symmetric cryptography, an updated RSA algorithm by eliminating the n is used in the proposed framework.
The pattern is reversed of the same algorithms in a decrypted form when the user downloads a file from a cloud network, making it as secure as possible. The technique aims to secure and preserve data.
To improve the security in the RSA algorithm then it can be removed from the original RSA. As an alternative, the newly created replacement for n can be used in both the keys. The architecture of the proposed technique is shown in Figure 2.
We are projecting a hybrid of two different algorithms to abolish any data breach in the cloud storage. Our proposed hybrid of updated RSA and Twofish algorithm overcomes the encryption delay and security issues present in old techniques. If someone tries to breach into an individual's cloud storage and examine it, it can still retrieve data after it has been deleted. This will leave traces on the drive even after the data has been deleted. But using the proposed technique for encryption and decryption, it can be a tough challenge for the cyber criminals to retrieve data.
RSA algorithm is one of the most commonly used asymmetric algorithms. It works based on the private key as well as the public key. It involves multiplication of two large prime numbers and once the key is created, it discards the numbers. RSA uses two keys (Private and Public). Private Key will be used for decryption and public key for encryption. The involved three phases of a public key are key generation, encryption, and decryption (Gehlot et al., 2013).
The updated version of RSA algorithm has enhanced the security. In this algorithm technique, the n can be removed from the original RSA. As an alternative, the newly created replacement for n can be used in both the keys. In Minni et al. (2013), the authors have also stated and confirmed that the security performance of RSA is enhanced by removing n from the original RSA algorithm.
Twofish algorithm is pre-calculated and has more speed than AES. There is a total of 16-rounds in the Twofish algorithm. Some building blocks of Twofish algorithms are as follows (Li et al., 2010)
Twofish algorithm builds up to 4 key reliant 8*8 bit blocks using a secure key authorization. In Twofish, each S-box consists of three 8-by-8-bit fixed permutations for 128-bit and four for 192-bit, chosen from a set of two possible permutations, q0, and q1.
Maximum Distance Separable (MDS) guarantees that there several non-zero bytes acting as a dispersion in Twofish apparatus. MDS is a maximum separable matrix. It is a matrix of bytes that multiplies a vector of four bytes. Multiplications are carried out in the Galois Field GF(28) with the primitive polynomial x8 + x6 + x5 + x3 + 1. Each byte is converted into a polynomial in which each power p of x is present, only if the p-th bit is 1. A multiplication in GF amounts to a multiplication of polynomials, followed by a division by the primitive is a reversible transformation of a bit string that provides cryptographic diffusion.
Pseudo Hadamarad Transform (PHT) utilizes a simple and active fickle effect. PHT is a reversible transformation of a bit string that provides cryptographic diffusion. SAFER algorithm uses PHTs extensively for diffusion for the first time. Twofish uses a 32-bit PHT.
The Q-Permutation is at the core of the design of Twofish. The permutations q0 and q1 are fixed permutations on 8- bit values. These permutation functions are the main components of the S-boxes (Liang et al., 2016).
The Feistel function F is a key-dependent permutation on 64 bit values. It takes three arguments, two input words P0, and P1, and the round number r is used to select the appropriate subkeys. R0 is passed through the g function, which yields T0. R1 is rotated left by 8 bits and then passed through the g function to yield T1 (Fang et al., 2013).
The function g forms the heart of Twofish. The input word X is split into four bytes. Each byte is run through its own keydependent S-box. In Twofish algorithm, for encryption, firstly, a 128-bit input plaintext, P is divided into four parts of 32-bit each, P0, P1, P2, P3 and XORed with four 32-bit subkeys, K0, K1, K2, K3, then sixteen rounds of iteration and then the four outputs are XORed with four more keys K4, K5, K6, K6.
Some modules have been modified by keeping delay as the main constraint. All the modules and functions are interrelated, hence after modifying MDS and PHT, function g and function F also got modified. The results show the delay of Twofish algorithm of the 128-bit key (Li et al., 2010)
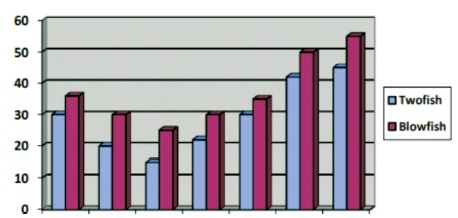
Figure 3. Comparison of the Encryption Speed of Twofish Algorithm, Versus Blowfish
Figure 3 illustrates time comparisons between Twofish and Blowfish. The Twofish takes lesser encryption time than Blowfish. The experimental results have also shown better results for the Twofish algorithm (Rane et al., 2016). Figure 3 shows the encryption speed of the Twofish algorithm, which is more than Blowfish.
The experimental results of the proposed Hybrid updated RSA and Twofish algorithm demonstrates better performance results than RSA and Bluefish technique (Kouchay, 2017) in terms of security and encryption speed.
The security problems are the primary concern in cloud computing, especially privacy and loss of data. The effective techniques are going to provide easily applicable methods to prevent or minimize these security issues. The flow of data being uploaded through the combination of updated RSA and Twofish algorithm crypto system in the cloud, which is shown in Figure 4.
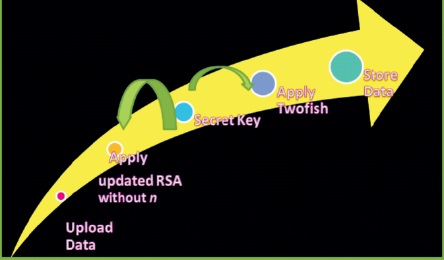
Figure 4. Data Flow in the Proposed Framework
Cloud computing can still significantly improve and can be utilized more efficiently. We have proposed a secured encryption and decryption technique for improving Cloud Data Security. The combination of updated RSA and Blowfish algorithm is a very effective crypto mechanism to mitigate the security risks. Various encryption algorithms and security concerns have been thoroughly reviewed. The primary analysis of the proposed technique demonstrates the better performance results.