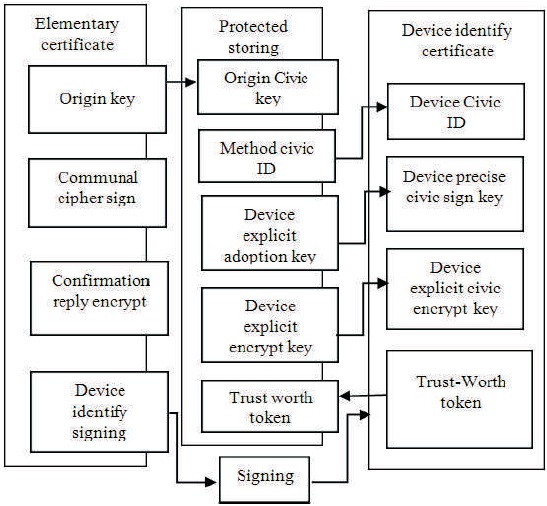
Figure 1. Enslavements among Basic Set, Device Uniqueness Certificate and Protected Storage Subjects (Rantala & Kylänpää, 2015)
The nodes are an important prerequisite for a trustworthy network. Low cost and simplicity are initiated through consecutively trustworthy code, which can help easy attestable node into the network. A close cooperation between the System-on-Chip (SoC) software producer and device producer is needed, as unbreakable trust chain among hardware and software with Trust Anchor module (TAm) that lives in SoC for a demonstrable trusted boot. The root public signing key inside a One Time Programmable (OTP) block makes up the physical trust anchor. For instance, the device producer needs to verify and recognize the SoC manufacturer, which is not practically possible for small device producers in each and every case. A small expedient producer can yield products with safe boot using the standard procedure. With huge producers, they are capable of ordering huge count of SoC using the means of self-programmed trust anchor. TrustZone by ARM, which is a Trusted Execution Environment (TEE), gives enough protection to local verification software, as the software performed in TEE need to be appropriately signed in such a way the software comes through the producer of SoC or through any authorized producer. A study of dissimilar approaches on above topic and their pros and cons are discussed in the paper. As an outcome, this paper gives the results of each methodology and suggests better procedure to overcome the existing drawbacks.
Embedded Computing Systems (ECS), which chiefly comprehends hardware, real time operating system and application software are typically designed to perform approximately definite tasks by means of real time performance constrains, relatively than being a all purpose computer for numerous tasks. The market for embedded computing systems raises at about 14 percentage world wide. Since, the ECS will be accountable for 92% of entire automation innovations, such as autonomous vehicles, automated medical equipment, avionics systems, smart household appliances, military systems etc. Enforcing trusted boot by implementing solitary code signed by an official entity dictates protected preliminary startup code and the source of trust. In order to conquest restrained hardware pony-trek these mechanisms are characteristically combined with the similar SoC as CPU core itself. The early startup code is steady and over all sufficient to be stowed on ROM. Similarly, it does not smear to the root of trust since here is a danger that the top most ratification key pair converts cooperated and distinct clientele might want to use their individual root trust. For this reason, the root trust is frequently stored in OTP memory, whereas the contents can be set once typically in the direction of the end of SoC manufacturing process, but occasionally the constituent has left the producer's grounds.
Design of embedded systems necessitates application of software and hardware components in similar combined strategies. On the commencement of 2000's, certain Field-Programmable Gate Array (FPGA) corporations predicted the developments in strategy by assimilating microprocessor cores in FPGA fabrics. One and half decades in to the future, utmost FPGA corporations will offer FPGA grounded SoCs, which are sturdier than ARM processors and FPGA fabric amalgamated. The connotation permits designers of embedded systems to advance authoritative and effective software and hardware systems that can advantage from software flexibility and hardware performance. Furthermore, ARM processors with embedded security topographies are proficient of dependably performing sensitive software applications. The ARM safety arrangement is recognized as TrustZone technology.
Existing PCs has TPM chip for remote attestation and ARM intimate processors are broadly rummage sale in embedded and mobile structures. It typically comprise the TrustZone feature provided that a functional TEE for software implementation (Yu et al., 2016). On considering the large mobile or embedded device producer, it is comparatively informal to partake its code accurately signed by collating a huge consignment of SoC's with the client's root of conviction programmed in the OTP memory through chip building or having the software certified by SoC producer's keys. As these methods need close cooperation between SoC & device creators, they are not exposed to minor mobile or embedded device producers who produce petite sets of devices. One prospect is to use SoC's distributed with programmable OTP memory in which the circumstance of device producer programs root trust to the OTP memory and signs entirely coded by means of its individual keys.
SoC is flattering progressively complex as it assimilate numerous functionalities together by means of third party IPs (Internet Protocols), which increases consciousness of essential to defend the SoC from a security failure. Nowadays, one of the important intimidation is the pebbledash SoC, which is a secret channel broadcast of treasured data. Security attack permits the assailant to handover data between processes, that are not authorized by security policy to communicate. In over all, a secret channel broadcasting custom is an interloper method that transmits valued data to a receiver progression that decodes and practices for spiteful determinations. Several approaches to generate the secret channels can be found in literature, nevertheless they use shared resources like cache memory.
Recent research on hardware Trojans mainly engrossed on conviction authentication for identification of malevolent reason by structural and activation characteristics, for example, location of unused circuits and nets, design points that are generated underneath occasional situations. Though, such methods have characteristically beleaguered stand alone demeanor of IP block and are tough to acclimatize or measure to trojans by affecting system level performances, swaying other IP's in the SoC design.
Consequently, SoC-FPGA is employed as the embedded computing platform. To upsurge the sanctuary of the ECS, diverse booting sequences has been instigated and assessed. A prognostic algorithm is implemented platform to analyze the health complaints of Lithium ion batteries and forecast the residual suitable lifespan of the batteries. The proposed safe embedded computing systems is climbable to foresee the health disorders of larger scale engineering systems to manage optimum and uphold the engineering systems before system’s failure.
Every single engineer must have talent and idea for evolving any method in his peculiar way and is essentially be contingent on the kind of predictable result. Technology can be authenticated and certified based on several parameters. The method may be effectual in security point of interpretation, but may nose dive in upholding the cost control. At this time, we bounce up some challenges confronted by current methodologies through security point of sight.
The security of heterogeneous SoC is obligatory to allow embedded system originators to advance secure implementation environment for subtle applications. The leeway of the ARM trust Zone technology in SoC appears to be a virtuous result, if security is certain. Though, the leeway of the ARM trustZone is formerly not secure. The current works affords proof that various intimidations are occurring and it is possible to use bout system security, perhaps with melodramatic significances. These current approaches defines 6 bouts that were efficaciously carried out in a archetypal software and hardware systems, but additional bout routes are probable. Subsequently, the design engineer who desires to advance sensitive applications on such heterogeneous SoC have receipt the security of entire-system into account as initial as probable in the design flow. This paper presents some new security solutions and design commendations for designer engineers. Inappropriately, utmost designers are not familiar to security glitches, but CAD tools would offer cohesive and automatic solutions.
With rising dependence on third party IP blocks during SoC design process, unsecure IPs are hastily flattering foremost security apprehensions for SoC producers. The architecture delivers low cost and vigorous run time protection in contradiction of unsecure IPs. Forthcoming work will comprise additional evaluation of architecture and automatic synthesis of security strategies.
A system on chip is an integrated circuit that assimilates entire components of computer or other electronic system. All these components naturally comprise a CPU, memory, input or output ports and secondary storage all on solitary substrate or micro chip, the magnitude of a coin. It might comprise digital, mixed-signal, analog and radio frequency signal dispensation functions, contingent on application. As these are cohesive on a single substrate, SoC's consume a lesser quantity of power and occupies lesser area than multi chip proposals with equal function. Since, these SoC's are collective in mobile computing and edge computing marketplaces. SoC are usually used in embedded systems and Internet of Things. SoC in contrast to mutual traditional mother board built PC architecture, which split up components based on function and links them over a central interfacing circuit board. The SoC assimilates a microcontroller or microprocessor with innovative peripherals like Wi-Fi module, graphics processing unit, or with one or multi co-processors like a microcontroller assimilates a microprocessor with peripheral circuits and memory.
ARM, earlier advanced reduced instruction set computing Machine, formerly Acorn RISC Machine, is a family of RISC architectures for computer processors, organized for various environments. ARM holdings advances architecture and licenses it to further company who enterprise their own goods, that contrivance one among those architectures including SoC and systems on module includes memory, radios, and interfaces. Processors that has RISC architecture archetypally necessitate few transistors than complex instruction set computing architecture, which advances cost, heat dissipation and power consumption. These physiognomies are required for light, battery powered devices, portable including smartphones, tablet computers, laptops and other embedded systems. The Security extensions are advertised as TrustZone technology, which is in ARM v 6KZ and far ahead application profile architectures. It affords low cost substitute to accumulation alternative steadfast security core to SoC by providing 2 virtual processors assisted by hardware based access control.
ARM TrustZone generates a secluded, secure world and can be used to provide secrecy and veracity to the system. It is rummage sale on billions of applications, processors to guard high value code and data for various use cases as well as authentication, content protection, payment and enterprise. It is regularly used to afford a security boundar y for Global platform reliable implementation environment. It also provisions contemporary Cortex-M23 and Cortex-M33 systems, lot of appreciations for release of Armv8-M-architecture, satisfying the marketplace need for effective secure embedded solutions.
The potential solution is that the SoC producer delivers an appropriately signed generic code package, which initializes the SoC, sets up TEE and starts a appropriate setup Device producer's software exterior the TEE and eases its following remote attestation. For device producers, it is enough to setup their code rendering to the rubrics enforced by this code package, no explicit dealings are required between SoC producer and device producers.
Later, reset the start up code it first verifies and starts further parts of the SoC producer's code package. Subsequently the TEE is setup correctly and the start up code checks the public side software by the device producer:
Above generic boot strap and corroboration context facilitates practically reliable boot strapping as well to small device producers who are incapable to obtain large batches of components with modified root trust and who find it tough and slow to get signing certificates or code certified by SoC producers. By using the defined remote attestation service perhaps even with a modified trust worthiness token. This system provides minimum as trustworthy security than just a symbol of “big name” producer on the device. In such cases attestation component will be beneficial. When small device producers able to setup their individual root trust and certificate grading by using SoC's with adaptable OTP root trust, nevertheless it is tough to determine for their clienteles if their devices are truly genuine (Figure 1).

Figure 1. Enslavements among Basic Set, Device Uniqueness Certificate and Protected Storage Subjects (Rantala & Kylänpää, 2015)
A protected ECS on System on Chip FPGA through regulatory boot arrangement is premeditated. The application of prognostic and handling health situations of Li-ion batteries have been instigated on SoC-FPGA grounded ECS. Precisely, to upsurge security of embedded computing system. Diverse booting sequences has been instigated and assessed. The predictive algorithm has been instigated on System on Chip FPGA grounded ECS dais to analyze health disorders of Li-ion batteries and forecast the residual beneficial lifespan of these batteries. The anticipated secure embedded computing system is climbable to forecast the health disorders of larger scale engineering systems to optimally manage and uphold engineering systems formerly systems fail.
Linear mixed effects model comprises immobile and random effects, which were used to compute manifold inconsistencies in interrelated measurements. Defined as z=β0+β1xε, where, z is reliant on variable determined by x- independent variable. β1 is slope of line, β0 is intercept and ε is random variable, it is out of control in this milieu or arbitrary variations. The norms to e are E(ε)=0 for all conditions and Var(ε)=σ2. The proto is assumption determined by β1 and β0. The approximation of β0and β1 is grounded on the value of z and x.
The paper presents our work in progress. We have estimated and evaluated 2 dissimilar boot sequences on SoC-FPGA. We will keep investigating further booting sequences to secure embedded computing system on SoC-FPGA. The linear regression grounded prognostic algorithm have been investigated in embedded C on Xilinx ZC706 SoC-FPGA based embedded computing system to forecast the enduring valuable lifespan of batteries (Nikolaenko et al., 2013). Nevertheless, ZC706 SoC-FPGA does not provision reverse boot. Hence, we drive test the similar algorithm on Intel DE1-FPGA, which supports reverse boot and associate the performance. Formerly, more erudite prognostic algorithms we have proposed will be executed on the podium to advance a secure, portable prognostic and reliable device. And the device is accessible to foresee the health disorder of larger scale engineering systems to optimally accomplish and sustain the engineering systems.
Nowadays, utmost embedded systems use Dynamic Voltage and Frequency Scaling (DVFS) to minimize energy consumption and performance. The DVFS method works on regulating the significant limits that rule the quantity of energy consumed in system, voltage and frequency. For execution of this method, the Operating System (OS) comprises software applications that animatedly governs a voltage regulator or frequency regulator or both. we demon strata for the first time a malevolent usage of the frequency regulator in contradiction of a TrustZone enabled System on Chip. We demonstrate the use of frequency scaling to generate covert channel in a TrustZone enabled heterogeneous SoC. We present 4 proofs of perception for transmission of sensitive data from secure entity in SoC to non secure entity. The first proof of perception is from a secure ARM core to exterior of SoC. The second is from secure ARM core to a non secure core. The third is from non trusted third party IP embedded in the programmable logic part of SoC to non secure ARM core. The last proof of perception is from secure third party IP to non secure ARM core.
Figure 2 displays the prototype system castoff for experiment. In this prototype, SoC is segregated into a Processing System, and Programmable Logic. The Processing System assimilates a dual ARM core that shares the similar clock source. Two cores share an external memory with the programmable logic.
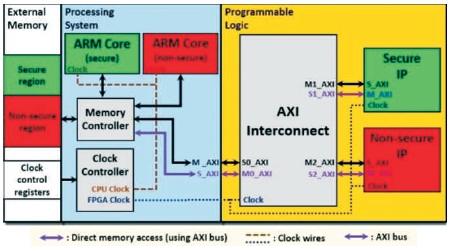
Figure 2. Model Arrangement with Xilinx-Zyn-7012 SoC (Zhou et al., 2019)
The TrustZone technology supports partition the programmable logic, external memory, and Processing System into secure and non secure memory. The secure ARM core of processing system runs a custom trusted OS, which is stored in secure region of the external memory. The second ARM core runs a general OS, which is stored in non secure region of external memory. Both ARM cores share the similar clock source from SoC clock controller. The Programmable Logic comprises a secure IP and non secure IP. Both IP's partake direct access to the whole external memory with no control by ARM processor.
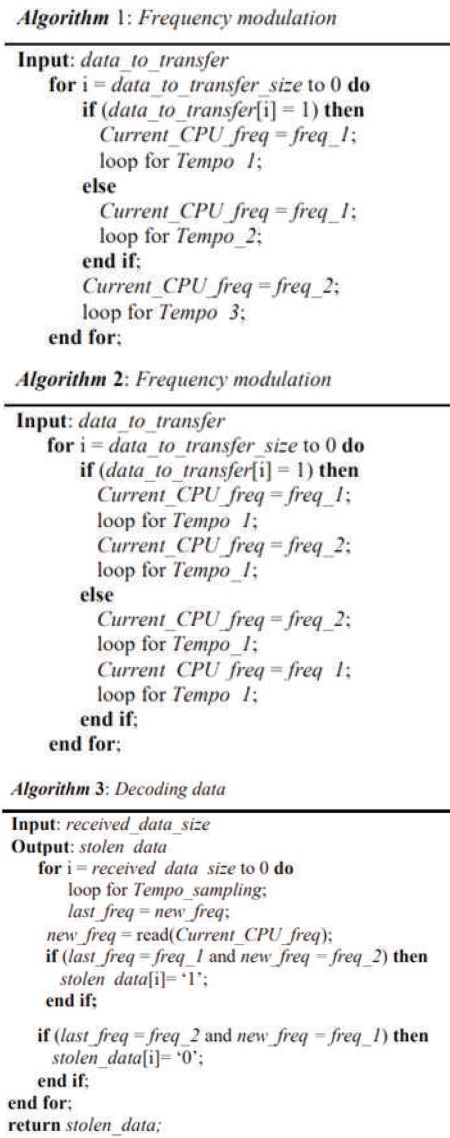
This paper presents despite the security isolation provided by TrustZone method. We establish the viability of using frequency scaling used in modern SoC to allow covert channel transmission. The 4 proof of concept presented here demonstrate the transfer of a sensitive data in TrustZone enabled SoC between an intruder process and a receiver process over malevolent control of frequency regulator. These proofs of perception is used to contrivance a comprehensive attack situation that target mobile device with android and complex trusted OS. The paper also highlights the importance of clock isolation in SoC.
The Zynq-7010 FPGA-SoC is segregated into Processing System, and Programmable Logic. The PS integrates dual Cortex-A9, On Chip Memory, central inter connect, programmable logic to memory inter connect, a timer controller, DDR3 controller and I/O peripherals. The PS comprises the TrustZone hardware-set used to defend the memories and peripherals.
The cortex-A9 in the Processing System (PS) is used in several projects to run trusted application running over TEE frame work, such as TOPPERS Project's Safe G and OP-TEE. The cortex-A9 provides 2 virtual cores, 1 secure and 1 non secure escorted with a monitor-mode, which is the gate keeper between two worlds. The security status in SoC is linked to the non secure bit in the secure configuration register of Cortex- A9. The Processing System suggests a set of configuration registers which can be rummage sale from software to control the TrustZone hardware and make secure custom design, they can be dynamically programmed during run time implementation.
The AXI inter connect is a multiplexer based IP connecting single or multi AXI memory mapped master devices to one or more memory mapped slave devices. Using Vivado, the security feature on AXI-interconnect can be statically allowed or restricted and each third party slave- IP cores in programmable logic can be allocated Secure or NS status.
The IP security status is an AXI-Interconnect parameters. The non-secure bit inspection feature is done on AXI-Interconnect or directly on third party-IP.
If N-S master tries to access a secure-slave, a SLVERR or DECERR is elevated by slave or the bus.
The slave-response for a recite transaction is conveyed using RRESP-signal of read data-channel and for write transaction is conveyed by BRESP-signal of the retort channel, if transaction is effective, the slave directs back an OKAY. if transaction is failure, the PS will launch abort exception and will be treated by software.
The AXI-Interconnect and protection signals of AXI -bus are the foremost TrustZone hardware setup in the programmable logic. They spread the technology concept to the programmable logic by separating the hardware into two worlds and prohibit the NS world from using secure resources.
This paper presents the hardware attacks understood on Zynq- 7011 SoC in direction to evaluate the proliferation of TrustZone to the programmable logic. We will not stretch additional details regarding the hardware malicious alteration and the way it is instigated, we will concentrate only on the principle of its applications. We hypothetical for all attacks that the assailant has admittance to RTLcode by means of Xilinx-tools and he can alter it.
Design recommendation #1: The processing system affords a register-configuration that can halts all the NS transaction from broadcasting to the programmable logic through the GP port. The designer engineer can practice those records and the two GP-ports in the Zynq - 7010 in instruction to safely broadcasting the TrustZone notion into the FPGA.
Design-recommendation #2: The Processing System affords also a register configuration that can set HP port to admit only the NS transaction approaching from the Programmable Logic and targeting external memory. The Zynq - 7010 proposes 4 HP-ports. The designer engineer can set 1 among the 4 as NS port and connect all non sensitive memory plotted main interface. This setting will deliver the IP's with direct access to memory from assenting secure-area in external memory. As in Design recommendation #1, the security inspection does not uses not only the AXI-Interconnect corroboration, but also others the PS TrustZone hardware that shield memory access.
Counter-measure #1: The Xilinx memory-protection component is available only on Zynq Ultra-scale+. It affords memory-protection, it can be dynamically configured to segregate a master or specified set of masters to programmable set of address-ranges.
Counter measure#2: Sec bus uses a hardware cipher block between AXI-Interconnect and memory controller. It smears cryptography operation to read and write to the external memory. The team project established a software library to use cipher hardware.
This paper presents a security assessment for the TrustZone technology propagation to FPGA by using the Xilinx Zynq - 7010 SoC. We presented 6 attacks by means of small malicious alteration in to access secure data, or create DoS (Denial of Service). Few of those accessible attacks can be widespread to other kind of SoC, but it needs erudite technique to comprehend.
Kumari and Anjali (2018) stated that Secret Group Procedure (SGP), presumptuous into altogether devices proficient of apprehending physiological signs. SGP dodges several pre-delivery of inputting resources. SGP contains of dual deputize procedures: HMAC-FE protocol and SKC protocol. HMAC-FE simplifies an underground piece argument by means of HMAC method. HMAC mechanisms by means of component, consequently through dissimilar HMAC purposes, dissimilar stages of sanctuary be able to attained. When a collective topographies amongst two devices is absolute, SKC procedure yields a clandestine key. SGP proposals certain indispensable possessions similar to plug and play, replaceability, flexibility, scalability and relaxed nourishment of solutions. SGP is associated through Ordered Physiological Feature based Key Agreement (OPFKA) originate through vigor ingesting owing to transportations to reduction.
Li et al. (2018) proposed a hardware reinforced insubstantial regulator movement truthfulness check technique in RISC construction mainframes, that battles code recycle bouts through tiny presentation slide deprived of encompassing ISA or altering accumulate. Key procedure includes dual regulator flow examination apparatuses. One is lining encrypt or decrypt process amongst PUF rejoinder further directions at objective discourses of noise besides jump commands to overthrow Jump Oriented Programming (JOP) bouts. Another one regulates ether reappearance address remained interfered through, thus battling Return Oriented Programming (ROP) bout that is founded on subordinate encrypt substantiation of reoccurrence address by confusion component.
Zhou et al. (2017) represents strategy, employment, besides assessment of reliable figuring atmosphere aimed at mobile presentation, this defends truthfulness as well as discretion of software as of jeopardy un-trusted mobile podium. Apparatus founded on TrustZone on un interactive demonstrable calculating delivers asynchronous cooperative substantiation machinery to runtime demonstrate vigorous organization. TrustZone remains a robust hardware feature founded inaccessible implementation method, nonetheless it cannot guard besides effectiveness aggressive. ACAM can operative avert such types of jeopardy by asynchronous inaccessible substantiation diminishes the above since real period shield. Sanctuar y examination and assessment demonstrations that method partakes chief possible in mobile principal figuring organization.
Saputra et al. (2015), is established an aggressor might counterfeit several objective slant through fault existence additional to 1.3 ppm in indigenous system surroundings. Similarly, it experimental that significance of counterfeit time imprints are exaggerated by period resolve of aggressor's organization clock. Once steadfastness is 1milli or less, a comparatively bulky hurdle amongst successive counterpoises often occurs, and gauge of ever y hurdle is hypothetically the actual time steadfastness of assailant's classification clock. This distinctive therefore espoused to progress riddling technique.
Long and Lin (2017) developed an effectual confirmation besides encryption procedure for internet associated wearable strategies by documented ideals of AES, then SHA can deliver two method verification amongst wearable maneuver and distant attendant with defense of enduring confidentiality alongside numerous system extortions. We partake verified possibility of the procedure on TICC3200 Launchpad, an assessment boarding of CC3200, such as Wi-Fi accomplished micro-controller considered for wearable strategies and comprises an hardware quicker cryptography component for application of encrypt procedure. The microcontroller attends wearable expedient customer and Linux processer attends as server.
Krishna and Rodrigues (2017) anticipated organization categorizes IoT operator nodules besides allocates low equal, high smooth refuge solutions for statistics dealings. Low equal protected solutions are general light heaviness solutions castoff statistics gatherer bulges along statistics aggregator swellings for important communications. TISK GSM component confirms IoT strategies founded on self trust inducement waitron belief inducement stages. High glassy protected solutions are enthusiastic unusual resolution keys exploited by data director swellings besides data skilled bulges for sanctioned dealings. TISK DSM-C component validates diplomas delivered by GSM-C component. DSM-C component additional subject's high equal protected keys for data director swellings.
Based on preceding research, we tool a prognostic algorithm on SoC-FPGA grounded ECS to forecast the residual beneficial lifespan of Li-ion batteries in this unit. Figure 3 illustrate battery testing equipment, which contains of Arbin battery test machine, battery module, environmental chamber, and SoC-FPGA grounded ECS. Part of collected (charge or discharge) battery data revealed in Table 1.
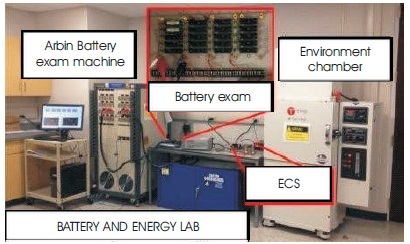
Figure 3. Batteries Testing (Zhou et al., 2019)
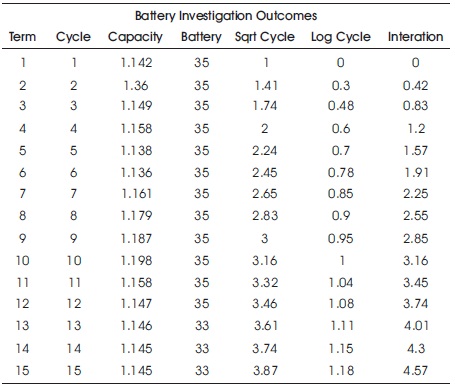
Table 1. Outcomes of Battery Investigation (Zhou et al., 2019)
For remote attestation to be trust worthy, it should be started from other device than the one, which is being attested, if the device are already-penetrated it may connect to fake attestation server instead of genuine one. Some device to link the attestation session in attestation server and the device being attested is required. Otherwise an assailant might re-direct attestation posts to some known to be decent device, which even though being sincere, is in no way linked to functions whose suitable implementation is checked. Hence, attestation server must choice some session pointer like tune, PIN code. To be shown by device actuality attested in command to elect the corporeal device presence attested.
Table 2 lists 4 configurations of the standards used and the connected bandwidth. Table displays the size of bandwidth linked to frequency and activation cycles. Aimed at this proof concept, the highest bandwidth stretched is 125-Mbps.
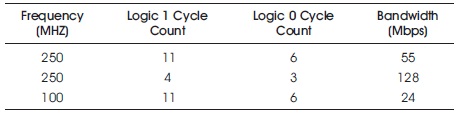
Table 2. Bandwidth as per Frequency Cycle (Benhani & Bossuet, 2018)
The design engineer should not make usage of connection automation or routing automation projected by several design creator tools. Automation tools assist to gain resource and time nevertheless it does not let a mastery of design. Few design references will halt the TrustZone defense feature from broadcasting to PL, nonetheless they allow designer to make a securepropagation of TrustZone concept, which divides the hardware design into two worlds (Table 3).

Table 3. Attacks and Prevention (Benhani et al., 2017)
The accessible general boot strap and attestation outline eases sensibly trust worthy boot strapping and the small device producers who are incapable to obtain large batches of components with modified root trust and who find it tough and sluggish to get code or signing certificates certified by SoC producers. By using the defined remote attestation service perhaps even with modified Trust worthiness Perfunctory. This scheme delivers at smallest amount as trust worthy security than just symbol of “big name” producer on device. The accessible frame work is presently only a plan. But the prevailing open source components alike UEFI Tianocore EDK2 boot loader, Linaro OP-TEE and ARM Trusted Firmware.
Assessed and evaluated 2 dissimilar boot sequences on SoC-FPGA. We will keep on examining further booting sequences to secure embedded computing system on SoC-FPGA. The linear deterioration grounded prognostic algorithm has been executed in embedded C on Xilinx ZC706 SoC-FPGA based embedded computing system to foresee the residual useful lifespan of batteries. Though ZC706-SoC-FPGA does not support reverse boot. So, we test same algorithm on Intel DE1-SoC-FPGA, which provisions reverse-boot and associate the performance.
Inspite of security segregation provided by TrustZone technology, we prove the viability by means of frequency scaling rummage sale in contemporary SoC to allow secret channel transmission. The 4 proof concept presented prove transmission of sensitive information in TrustZone enabled SoC between intruder process [secure] and receiver-process (NS) through malicious control of frequency controller.
Presented 6 attacks by means of small-malicious alteration to access secure data or create DoS. Few of those accessible attacks can be comprehensive to other type of SoC, but it needs urbane technique to understand. Also, few counter measures and design references in order to assistance designers to avert some of the 6 attacks and protect system.