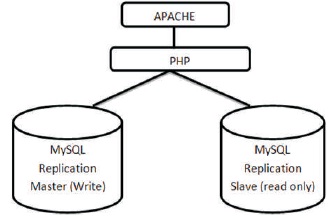
Figure 1. Architecture Diagram of Web Technology (Web Wire Technology, 2018)
The important of any research is to address fundamental problems combating society. Research shows that the average student misplaces one item or the other, during their stay in any institution. Challenges encountered by individual and security bodies to find the lost item tends to rise and becomes more tedious. The lost item can cause depression to the student and finding the identity of the individual when the lost item is found is also challenging. The objective of this study is to develop an online lost item recovery application, that can assist students to easily search the lost items via any internet enabled device, and also the students who help to find the items can help to upload details of the items found via the internet. Thus, it is important to find an approach through the use of information technology to find the solution for issue related to misplace item in higher institutions, which in turn can foster integrity, transparency and good character among students.
Students often misplace their gadgets or other items and people who help to find these items can sometimes find it hard to got it to the owner; some place notices on faculty and departmental notice boards, but the notices do not stay long as a result of update and some students ignore such notices or treat it with levity. Now, with the wide use of internet, students can easily search the items via any internet-enabled device, and students who help to find these items can help to upload details of the items found via the internet.
The online lost and found framework incorporates a webbased database to monitor lost and found things for the whole grounds (Bolu-Steve et al., 2015). It produces a dynamic rundown of found and lost things, where it tends to be seen and looked online by the clients (Bataineh et al., 2015). The database will be overseen, kept up and refreshed by the lost and found officer (security department). Along these lines, the college network can pick up a ton of advantages by having such an online lost and found framework. This framework is open online to all students, workforce, heads, and staff. The framework is straightforward and simple to utilize and learn UI (user interface), which is computerized; with the normal manual strategy, the individual should put the additional physical exertion to visit the lost and found officer to scan for their lost thing. This framework will decrease the workload of the staffs, who are in charge of overseeing lost and found the officer. This website will help foster integrity amongst student (Ogundokun et al., 2019 a,b) and staff within the university will help to make awareness among the users the usefulness of search engine in solving issues related to lost item retrieval (Awotunde et al., 2019).
OLX and Konga are online platforms where students can search for products to buy and upload products to sell, this platform helps to connect the sellers to the buyers (Lashkari et al., 2009). Research shows that a good percentage of student make use of the internet daily, even some institutions make internet access readily available for their students and staff, which helps to ease information passage and retrieval, which can be useful in the item lost recovery application approach.
iFound is a platform to bridge issue related to misplaced or stolen item and how it could be retrieved, it will enable the student to have a sense of being their brother's keeper by doing little thing that count. It will foster integrity, transparency and good character among students.
The significance of this study is that the website developed will help foster integrity amongst student and staff at the university, it can also help users know the usefulness of search engine in solving problems related to recovering a lost item.
There are so many applications that have been developed to make one's life easy using technology, which has become a part of human life (Gandal, 2001). These days, several systems (which make use of search engine techniques and information retrieval process) have been developed to allow users to carry out several activities with ease. To mention a few, online shopping system etcetera (e.g., Konga, OLX, Jumia).
Azad and Deepak (2019) examined query expansion methods in information retrieval since 1960 to 2017 with regards to principal methods, data sources used measuring and positioning approaches, client involvement, and presentations, which brings out resemblances and differentiation.
Agboola and Shaibu (2019) examined the impact of Information and Communication Technology (ICT) on an information retrieval system in educational archives. The study findings deduced that ICT has affirmative effects on information retrieval system in educational archives. The system was developed for the intention of recovering credentials of materials vital to the communities and this makes correct and accurate information available to the appropriate individual. All of these can be accomplished through information and communication technologies.
Brandsen et al. (2019) presented the findings of client requirement solicitation for a quest system of grey literature on archaeology, particularly Dutch excavation descriptions. The quest system utilized named individual identification and information recovery methods to generate an operational and uncomplicated pursuit experience. The systems established could be effortlessly modified to further dialects and regions.
Njuguna (2018) established an online capability that increased simple recuperation of misplaced individual credentials. They produced a resourceful, collaborative approach to recuperate missing credentials exclusive of unwarranted expenses and deferments, to consider how a successful response structure effects the recuperation of misplaced credentials. Kenya was used as a case study. Bachchhav (2016) concentrated on the diverse information recovery procedures and methods, which assist clients to get the necessary materials as well as prevents them from wasting precious time. For Individuals to acquire appropriate and accurate information from the web, clients need to understand the operative methods and approaches.
Walson and Millie (2014) recognized the point that none of the two approaches of acquiring information from an archive could be self-determining the exclusive of entire association of the two as essential methods to operators.
Madankar et al. (2016) presented most selected significant extents of information re-trieval and these include Cross Lingual Information Retrieval (CLIR), Multi- Lingual Information Retrieval (MLIR), Machine translation methodologies and procedures. It was discovered in the study that CLIR is concerned with requesting inquiries in one language and requesting for recovering documents in alternative languages. MLIR is concerned with enquiring issues in numerous languages and retrieving them in several distinctive languages. Finally, it was deduced that machine conversion performances a significant function in accomplishing the CLIR and MLIR systems.
Suseela (2015) discussed the features or elements that influence the retrieval of information and developments in associated technologies, which describes the importance of Information recovery/pursuit instruments advanced from a modest virtual catalog to pursuit devices, meta-search devices, bibliographic search databanks, and modern detection facilities. The pursuit services delivered by IGM library of Hyderabad University was examined in this study.
Onwuchekwa and Jegede (2011) considered the thought of information retrieval and the several information retrieval methods. This study surveyed the operators of the information techniques discussed and their comportment. The authors concluded by highlighting the necessity for a constant assessment of information retrieval approaches to create an operational and resourceful information retrieval scheme.
Zipate (2014) developed a web application that provides a solution to lost and found item to the entire community. His application was linked to Facebook, which discloses the details of the person who have posted and there is no option for claiming the posted items in his app because his web application has limited content. The loophole of his application is that there is no method of determining the legitimacy of available data.
Lost and Found Kenya (2014) discussed that this lost and found medium does not have a module to post lost and found items, everything is posted in one section of the Facebook platform. There is no search function and personal information available for claiming the posted item.
Githinji (2016) developed a lost and found web application, which was limited to businesses and customers. The application was developed based on a trusted third-party model that helps businesses to share data on found items, customers to search for found items. For reviewed works, there are still limitations to the existing lost and found item recovery. This research work provides efficiency and integrity in recovery of lost items by making anonymous the person that post the found item and take series of security measure before the item will be handed over to the student who claims it.
The components and architecture part provided in this research work is the webserver, which receives a request from the user and then it passes to the search engine, which normally operates as a module within the server.
Figure 1 shows that the Architecture diagram of Web Technology. Figure 2 shows the data flow diagram module for the Users' registration in the system. Figure 3 shows the data flow diagram for the user activity process module for the system. Figure 4 displays the data flow diagram for the system administrative module.

Figure 1. Architecture Diagram of Web Technology (Web Wire Technology, 2018)
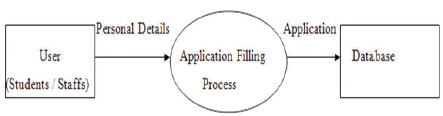
Figure 2. Data Flow Diagram of the Registration
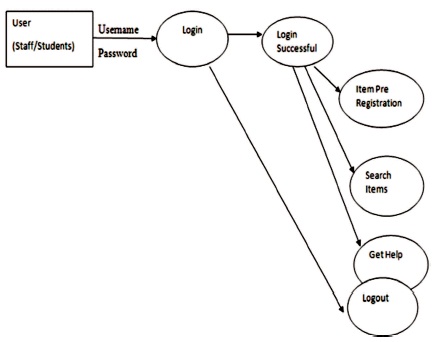
Figure 3. Dataflow Diagram for Users Activity Process
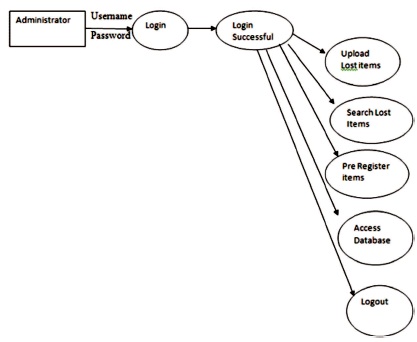
Figure 4. Dataflow Diagram Administrator Module
The application is web-based. The platform is called “iFOUND”, which involves developing a website and creating a detailed database through an individual who lost or misplaced his/her item, searching for the item using a keyword related to the item he/she lost. The website will be linked to the security department, where any individual who finds an item can go there to report and the security department will helps to upload the details for retrieval purposes, Also it gives a platform for honest individual to find the genuine owner of the item. The website has a navigation menu for the categories of items, and enable administrative user registration. Before an item can be claimed there would be a need for the fellow that lost the item to answer some identity related questions for safe retrieval.
Figure 5 shows the process involved in the User Module of the system developed.
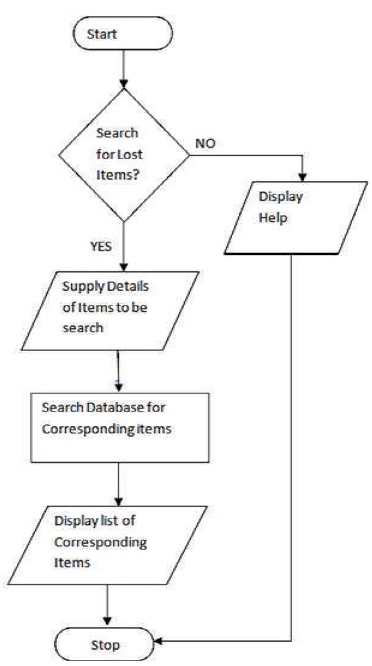
Figure 5. Flowchart for the User Module
Figure 6 displayed the process involved in the Administrative module of the developed system.
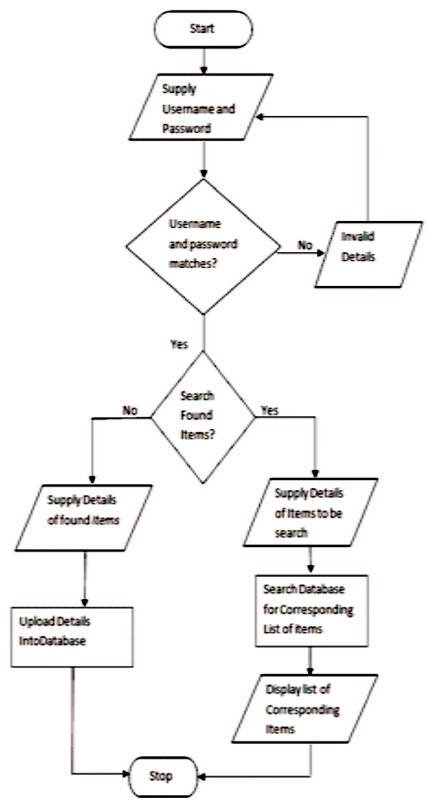
Figure 6. Flowchart for the Administrator Module
The home page is an index page where all users, especially students, visits search for lost items. This page is not authenticated as anyone can search for items. To search for items, the user need to enter keywords related to their search, and they can narrow their search with location or name. Figure 7 is a search page that is also present on the home page and is used by all users of the application. This is the page where you enter the item you are trying to retrieve and the system searches to locate it from wherever it is located.
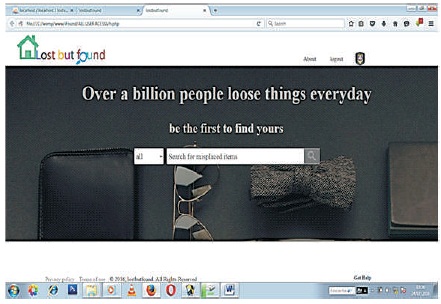
Figure 7. Search page (home page) for all Users
Figure 8 is the interface displaying the searched item found. After you have entered the item (s) you are trying to find, the system will runs once you press enter and display the item you are trying to find.
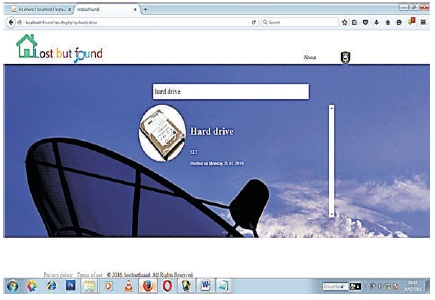
Figure 8. Search item Display
After displaying the searched and located item (s), more information about the item can further be displayed as shown in the interface in Figure 9.
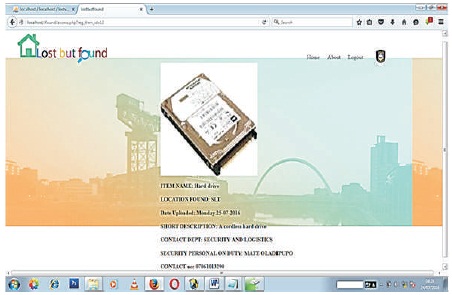
Figure 9. Further Details of item Found upon Search
As an administrator, some one is asked to login details or register as a user.
Figures 10 and 11 shows the administrator's pages, where the administrator has total control over the de-veloped system. Here the administrator has access to the backend of the system and can make modifications and maintenance on the system at any time.
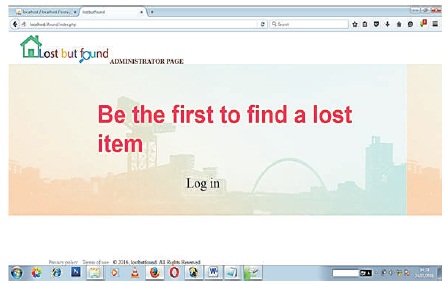
Figure 10. Administrator's Page
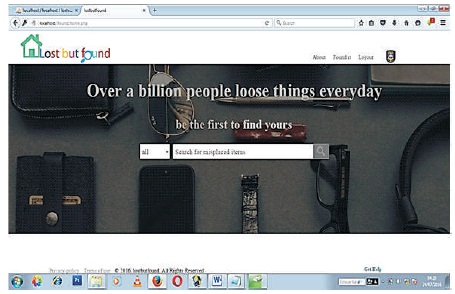
Figure 11. Administrator Page
This module allows administrator authentication before access to the admin privileges.
Figure 12 shows the login page for users. This is the page where users can put their credentials such as username and password in order to gain access to the system for use.
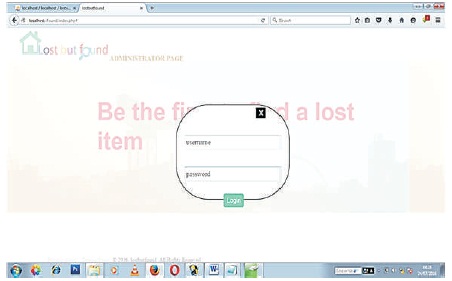
Figure 12. Login Page
Administrator uploads details of item found by filling the required fields.
Figure 13 is the page displaying the uploaded found items page, that is the page where the lost and found items are being uploaded.
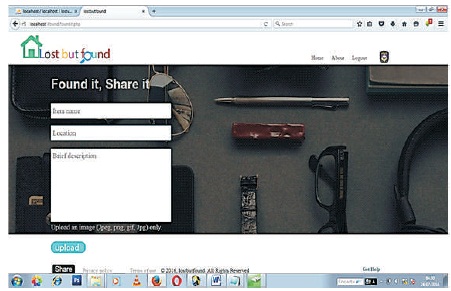
Figure 13. Found Items Uploading Page
Lost Item Recovery Application is very useful for the recovery process of lost items. For the past few years, the numbers of educational institutions are increasing rapidly. Thereby the numbers of cases of students losing their personal belongings. Hence there is a lot of strain on the person involved in the manual process. This particular study deals with the problems of managing such and avoids the problems that occur when carried out manually. Identification of the drawbacks of the existing system leads to the designing of a computerized system that is compatible with the existing system, which is more user friendly and more Graphical User Interface (GUI) oriented.
The system developed is a web based application, which is called “iFOUND”. It involved developing a website and creating a detailed database through an individual who lost or misplace his/her item, searches for the item using the keyword related to the item he/she has lost. The website is linked to the security department, where any individual who finds an item can go there to report and the security department will helps to upload the details for retrieval purposes, Also it provide the platform for honest individual to find the genuine owner of the item. The website has a navigation menu for the categories of items, and enables administrative user registration. Before an item can be claimed there would be a need for the fellow, that lost the item to answer some identity related questions for safe retrieval.
This research work has pointed out several benefits to be gotten from a web-based lost item. These benefits include efficiency and effectiveness, fostering integrity, reduction in man-power employed, etc. Therefore, it is recommended to employ the services of a qualified computer operator, who can perform a regular update and routine check. Or better still, exposure and training of the security personnel to the operation and handling of a web-based system.
Future research work as suggested by the authors is that the android based or mobile application of this ifound could be implemented where the users can use and access the system at their own convenient period of time.
This research is fully sponsored by Landmark University Centre for Research and Development, Landmark University, Omu-Aran, Nigeria.