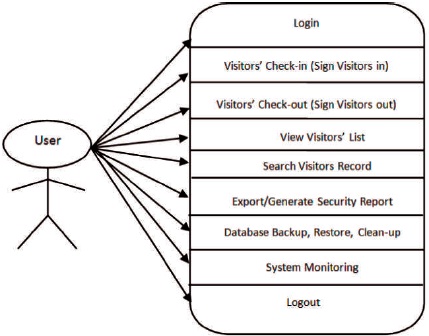
Figure 1. Use Case Diagram for the User
Records are pieces of information created or received by an organization or business establishment that provides evidences of business decisions or transactions. Record management is a vital part of any organization including the daily records of visitors in the organization. Types of records include vital and non-vital records, essential and nonessential records, active and non-active records, etc. Some of these categories of records are needed almost immediately to resume back the running and operation of an organization in case of an emergency, thus, they should be securely stored and managed. Interestingly, these records could be stored in paper-based format or in a computerbased system. This research work is focused on the design and implementation of a computer-based visitors' records management system for Niger State House of Assembly Complex, Minna. It is a software application designed using JAVA programming language and MySQL database at the back end, used for storing visitors' information. The software handles all necessary operations regarding visitors' check-in and check-out in the Niger State House of Assembly Complex. Furthermore, the receptionist can capture visitors' bio-data, such as: name, gender, email, phone number(s), address, fingerprint data, and an instant picture snapshot with a digital camera. It also incorporates features of generating security reports and statistics for crime investigation, as a means of providing security for lives and properties of the members/staff of the house of Niger state house of assembly complex, Minna, as well as adequately managing the visitors' records for posterity.
Record management is an integral part of any organization, whether the records are paper-based or electronic. Record keeping is essential to the running of any organization, in fact, it is a fundamental activity in public administration. Records represent a crucial source of information and they provide a reliable, legally verifiable source of evidence of decisions, and actions (World Bank, 2000). Thus, there are essential and vital records that are needed within 24-72 hours after a disaster to get an office up and running again.
These records, regardless of format (i.e., paper, electronic, magnetic tape, microfilm), must be protected and secured in the event of an emergency or disaster because of severe consequences to the organization as a whole if the records are lost or destroyed (FEMA, n.d.). Saka (2017) opined that “records are pieces of information created by or received by an organization or business establishment that provides evidences of business decisions or transactions.” Similarly, Michigan State University (n.d.) defines record as “information created, received, and maintained as evidence and information by an organization or person, in pursuance of legal obligations or in the transaction of business”. Government Records Service (2011) posit as “any recorded information or data in any physical format or media created or received by an organization during its course of official business and kept as evidence of polices, decisions, procedures, functions, activities, and transactions. According to World Bank (2000), records can be described as documents that institutions create or receive in the course of administrative and executive transactions. Furthermore, it covers all document regardless of form or medium created, received, maintained, and used by an organization (public or private) or an individual in pursuance of legal obligations or in the transaction of business, of which it forms a part or provides evidence. Holistically, according to Washington State Legislature (2017), a record is “any paper, correspondence, completed form, bound record book, photograph, film, sound recording, map drawing, machine-readable material, compact disc meeting current industry ISO specifications, or other document, regardless of physical form or characteristics, and including such copies thereof, that have been created by or received by any agency or organization in connection with a transaction or business, and legislative purposes.”
Records are created/received by an organization in routine transaction of its business or in pursuance of its legal obligations (World Bank, 2000). Generally speaking, records function as evidence of activities (Government Records Service, 2011), whereas documents function as evidence of intentions. In any organization, records must be well managed and preserved in order to prolong their lifespan and make them readily available to support essential functions under the full spectrum of all-hazards emergencies and critical elements of a successful continuity plan and program in an organization (FEMA, n.d.). It should be added that, records exist in different phases or cycle. The life cycle of a record is simply the repeated events in the existence of that record, covering the time it was created till the time it is eventually discarded or disposed (Saka, 2017). The various phases in the life cycle of a record are: record creation, record distribution, record storage, record control, record protection, record maintenance, and record disposition (Saka, 2017). Moreover, according to Government Records Service (2011), a complete record must have its content, context, and structure – these three elements is what makes record an evidence. The content of a record denotes the information, facts, or ideas in it. The context refers to the information about the circumstances in which the record was created, transmitted, maintained, and used, these include, the creator of the record, the time it was created, whom it was created for or sent and why. Lastly, the structure of a record means the physical and logical format of the record and the relationships between the different parts of the records (e.g. an electronic mail record covers its header, body, attachments, and corresponding reply) (Government Records Service, 2011).
Record management on the other hand, can be seen as the planning, organization, controlling, coordinating, and directing functions that are concerned with the creation, distribution, control, maintenance, protection, retention, and disposition of records in an organization (Saka, 2017). According to McDonald and Levine-Clark (2017), record management is that administrative system that covers the control of record and information from their creation to their ultimate disposal. It covers the whole range of activities which an organization should perform to properly manage its records (Government Records Service, 2011). There are various types of records, these include: (1) essential records, which are necessary for the continuity and/or resumption of operations of an organization during and following a disaster (King, 2015) and are mostly required within 72 hours or less after a disaster (Texas State Library and Archive Commission, 2010); (2) non-essential records, which have little or no value to the office or organization and probably should never have been retained (Michigan State University, n.d.); (3) active record, frequently used and referenced often (daily or weekly) in the operation and functioning of current organization's activities; (4) inactive records, that do not need to be maintained on site for day to day use, but must be retained by an organization for administrative needs or legal compliance (TAB, 2012); (5) vital records, which are needed in anywhere from a few minutes to 24 hours after a disaster to get an office or organization up and running again; lastly (6) archival records, which merit permanent value (Saka, 2017). Organizations need to carry out analyses of their records in order to identify under which category each record falls so as to ensure their proper storage and safety accordingly. This is necessary for planning record management programmes as well as arranging for their protection prior to a disaster (California Records & Information Management, n.d.).
Ensuing from the increasing rate of insecurity in our society, with terrorism at an increasing rage: bombing, kidnaping, theft, and sabotage of public and private infrastructure; this is a great challenge/threat in our society and nation. It is worthy of note to assert that in every organization be it governmental or private, visitors come to visit the staff of the organization; so do spies come also, but with an interior/undisclosed motive to spy the environment against a plan attack to the organization. In most cases, it is when the event has occurred that people reflect back, but without any concrete evidence to reference. In other organizations, such as governor's offices, hotels, senates, house of assemblies, etc., visitors' information are collected manually, that is, using the paper-based visitors' record management system. In such case, the building including the records might get destroyed when there is a bomb blast, explosion, or fire disaster. As such, the paper-based system is inadequate to accommodate such occurrences. Furthermore, the paper-based system is limited in scope as regards the necessary information required for visitors' identification in crime investigation, such as picture, fingerprint data, etc.
It is against this backdrop that the researchers deem it fit to carry out this research work to develop a computer-based visitors' record management system and implement it in Niger State House of Assembly Complex, Minna. The computer-based visitors' record management system is designed to overcome most of the challenges and limitations or inadequacies of the pen and paper-based visitors' record management system.
The general objective of this research work is to develop/design a software application that would manage and keep track of the information of visitors coming in and out of the Niger State House of Assembly Complex, as a means of providing security and creating a secured environment for the members, staff, and infrastructure of the House of Assembly Complex.
Specifically, the objectives of this study are:
This study is directed towards visitors' record management in an organization (Niger State House of Assembly Complex, as a case study), moreover, it can be applied to any of such organization be it governmental or private that takes interest in managing the records of the visitors in the organization. This study will assist ministries, organization, and establishments in adequate management of their visitors' record against the pen and paper-based system in place; and in the case of an emergency, it will assist the police/security in crime investigation via:
According to The Receptionist (n.d), visitors' record management is the process of tracking and documenting everyone who enters an office building. LobbyGuard (2013) opined that a visitors' record management system documents the usage of the facilities by specific visitors and provide information of visitor's whereabouts. A visitor may be a customer, a delivery person, a job applicant, a contractor, a consultant, or the relative of a staff in the office. Essentially, anyone who is not a regular full-time employee is a visitor. The method, technique or technology used to tract or document and manage the records of visitors in an organization is referred to as visitors' record management system (The Receptionist, n.d). Many methods have evolved over the years on how to manage the records of visitors in an organization; among these include: (1) pen and paper visitors' record management system, (2) computerized or computer-based visitors' record management systems or visitor management software (LobbyGuard, 2013; VisiPoint, 2018). Succinctly, according to The Receptionist (n.d) and LobbyGuard (2013), the pen and paper visitors' record management systems records basic information about visitors to a public building or site in a log book. Typical information found in an entry includes the visitor's name, reason for the visit, date and check-in and check-out times. A pen and paper visitors' record management system's main positive feature is low up-front cost. Training to use the system is minimal, and the equipment required to implement this visitors' record management system is cheap and readily available. Some systems use a simple book format, where visitors simply enter their details on marked rows. Furthermore, (LobbyGuard, 2013) submitted that, a pen and paper visitor's record management system have some negative points from a security point of view. Visitors must write entries by hand, creating a logjam (holdup) effect in public entryways. A security personnel must check each visitor's credentials and manually initiate any further security checks (for example, a call for a background check or other action) (Kat Technologies, 2017). Visitor badges rarely have photo identification and can easily be swapped from person to person (LobbyGuard, 2013). Kat Technologies (2017) reported that documentation in a pen and paper visitors' record management system requires either manually re-entering logbook information in a computer or keeping the logbook itself in storage. Other shot-comings of the pen and paper visitors' record management system as outlined by LobbyGuard (2013) and Kat Technologies, (2017) include the following:
Consequently, LobbyGuard (2013) and Kat Technologies (2017) opined that a computer or electronic visitor' record management systems use a computer network to monitor and record visitor information. Furthermore, it can capture all relevant visitor's information, including photo, signature, fingerprint, name of the visitor, reason for the visit as well as entry and exit times. An electronic visitors' record management system improves upon most of the negative points of a pen and paper system (Kat Technologies, 2017). Visitor's ID can be checked against national and local databases against fugitives, as well as in-house databases for potential security alerts. A computerized visitors' record management system can be customized to print visitors ID cards for one-time only or continuing use. Moreover, several desktop-based visitor management software applications are currently available. These applications typically consist of three fundamental components: (a) visitor registration, (b) visitor badge printing, and (c) reporting functionality. Some of the applications are capable of automatically capturing visitor information directly from a visitor's driver license, passport, or other government issued identification document (VisiPoint, 2018; Kat Technologies, 2017).
According to Virtual Galaxy (2010), visitor management is more than just optimizing the flow of visitors in your buildings. It provides you with a way to implement your company's security policy and to obtain reliable information on your visitors and visits. With a good visitors' management system module, one can manage a company's flow of visitors in a simple and effective way. Optimizing visitor management process can significantly reduce costs, improve safety and security, and generate valuable visitor data. Each day scores of visitors pass through the entrances to your facility. Having the ability to screen and track them can contribute substantially to the safety and protection of your personnel and property. With a computer-based visitors' record management system, one can improve security desk productivity by scanning business cards or driver's licenses to quickly register visitors, and provide voice coaching to guide visitors during the registration process (Virtual Galaxy, 2010; Wikipedia, 2017).
Nedap (2008) submitted that visitors' management systems can also have the functionality that ensure visitors are only granted access if their visit is approved by an authorized person present in the building. This gives you much tighter control over the visit. The system gives the possibility to set a maximum presence time for each visit. If the visitor does not handover in his badge on time, it will be automatically blocked. One can also set a limit on the number of badge movements that can be made in and out of a zone. If the maximum number of movements has been exceeded, an alarm is generated. A computerbased visitor record management system has distinct advantages when it comes to registering and monitoring visitors. According to Virtual Galaxy (2010), the ability to automatically screen and track visitors is an essential part of a complete security plan. A computer-based visitors' record management system should have the following functionalities:
This system was designed using the JAVA programming language and MySQL database server. According to David (2007), MySQL is a relational database program that is used to enter/insert, edit/update, delete, alter and analyze lists of data. MySQL, being a relational database management system, minimizes redundancy of data stored in the database. Furthermore, the design of the system incorporates features for an automated visitors' record management and security system. The design and modelling for this application include:
The visitors' record management system is operated mainly by the receptionist of the organization. The usecase model diagram in Figure 1 below shows the various interfaces, which the user interacts with the system.

Figure 1. Use Case Diagram for the User
The input for the application varies from entering text directly from the keyboard, selecting sets of options from a menu using the mouse, picture snapshot / upload from a camera/webcam/file, uploading files from storage devices, and fingerprint enrollment from a fingerprint scanner/reader. The output on the other hand could be in the form of printed outputs (reports), screen display and audio / sound outputs. Both the input and output for the application undergoes some kinds of validation and testing to avoid error before the actual processing as shown in the design model in Figure 2 and Figure 3.
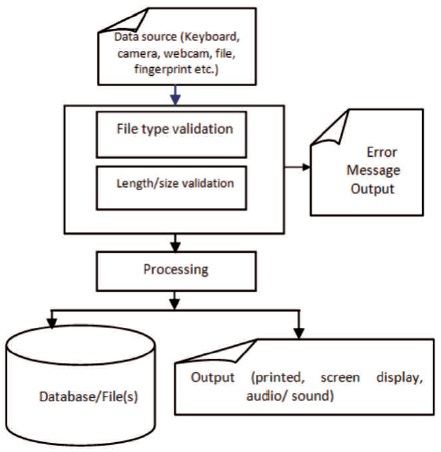
Figure 2. Activity Diagram for Input Model
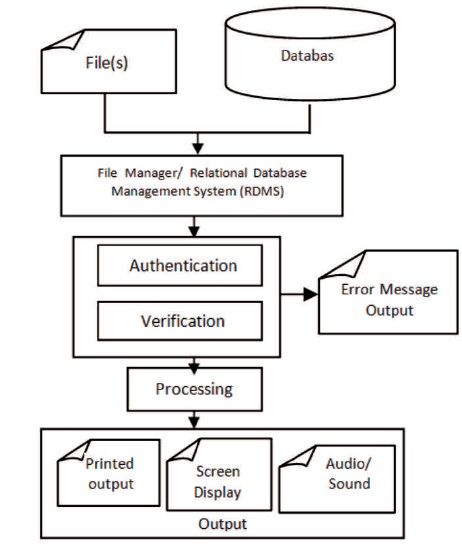
Figure 3. Activity Diagram for Output Model
The general theme behind a database is to handle information as an integrated whole. A database is a collection of interrelated data stored with minimum redundancy to serve many users quickly and effectively. The database designing specifies the structure of the database' tables, fields' types and length and how data should be organized around user requirements (David, 2007). The general objective is to make information access easy, quick, inexpensive, and flexible for all users. During the database design, the following were put into considerations: controlled redundancy, data independence, accuracy and integrity, large information at low cost, backup and recovery from failure, privacy and security, performance, efficiency and effectiveness of the system. The database design is shown in Table 1. Figure 4 shows the system flow chart.
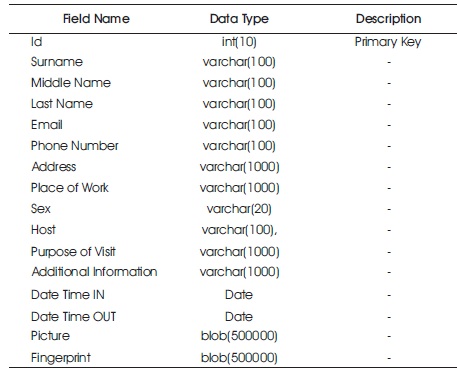
Table 1. Databases Table Design
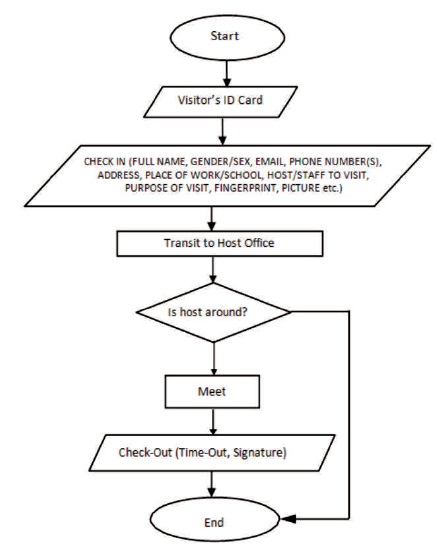
Figure 4. System Flow Chart
The visitors' check-in display output as in Figure 5 shows the interface for registering a visitor into the House of Assembly Complex, Minna. The information collected include: name, e-mail, phone number, location/address, place of work/school, gender, host, purpose of visit, instant picture snapshot, fingerprint data, and other additional information. Figure 6 is a sample successful visitor's checkin slip.
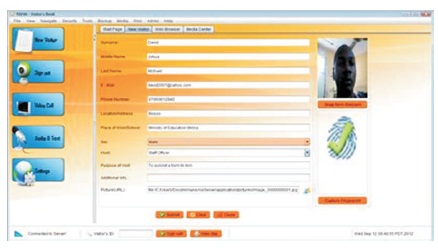
Figure 5. Visitors' Check-in Output

Figure 6. Visitors' Check-in Slip Output
Figure 7 is a screenshot of a sample visitor's check-out slip.

Figure 7. Visitors' Check-Out Slip Output
The screenshot in Figure 8 is a list of visitors registered with detailed information of each visitor.
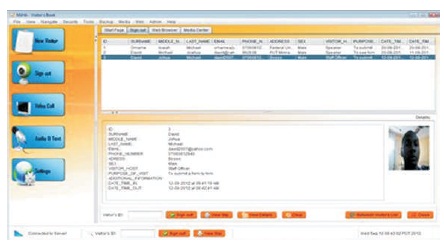
Figure 8. Visitors' List Output
The screenshot in Figure 9 shows the list of visitors for security report. The list could only be a targeted category of visitors who did not sign-out after signing into the House of Assembly Complex or the entire record of visitor for a given period of time.
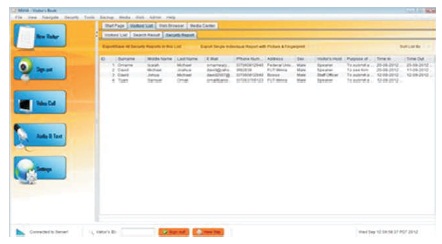
Figure 9. Security Reporting/Tracking Output
The Database manager provides a convenient tool for database backup, restore. You can conveniently backup your database after a certain period of time (daily, weekly, monthly, or annually) and save the backup file to an external storage device for future reference or online to an email host server. In the case of an emergency, when the building is destroyed or the system is damaged, from external backups or online you can conveniently restore that database and view the records of visitors into the House of Assembly for criminal investigation purposes (Figures 10 and 11)
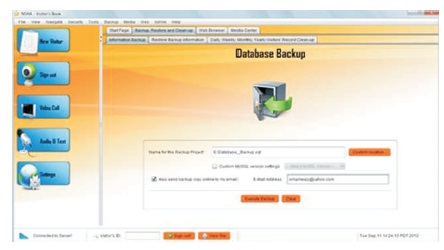
Figure 10. Database Backup Output
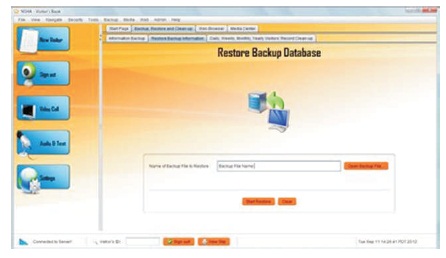
Figure 11. Database Restore Output
The designed visitors' record management and security system is a software application designed using Java Programming Language, which has the capability of checking visitors in and out of the Niger State House of Assembly Complex Minna, and provide security information for checking and tracking down a criminal or suspect in case of emergency. It takes in the relevant information of visitors at the receptionist and/or secretary's desk, such as full name, address/location, the purpose of visit, instant picture snapshot, and fingerprint, which can be easily used to track down a suspect/criminal in case of emergency. It is true that most organization collects such information manually; this cannot guarantee real-time security; if such organization experience fire outbreak or bomb blast, there will be no record to reference during investigation - the record itself would be destroyed. However, this research with bridges this gap via a secured online backup and restore module that one could store backup files externally to the organization and in the case of emergency it would be retrieved without any hitches. Lastly, this software addresses the problems and limitations of the existing manual system such as slowoperations, limited storage capacity, lack of efficiency, and reliability, etc. Some of the challenges that might be encountered with this computer-based system, include availability of uninterrupted power-supply, lack of technical know-how on how to operate the system, inadequate funding to procure, and maintain the system.
Consequently, it is recommended that the organization should source for alternative means of power supply rather than depending on Power Holding Company of Nigeria (PHCN). Among others, solar power, and standby generator with inverters and batteries are hereby recommended. In the same vein, the government should address the problem of erratic power supply more seriously through research and development for alternative sources of renewable energy. Furthermore, the receptionist or secretary that will operate the system should be adequately trained to do so before commencing full operation. Lastly, the stakeholders of the organization should be sensitized on the usefulness of the system so that they can see the need to release funds for the maintenance of the system when the need arises.