Figure 1. Pictorial Form-Real and Fake Webpage
Today websites are used for various purposes. There is a crime named website phishing which comes under Cybercrime. A website phishing tries to steal your account password or other private information by misleading you into believing that you're on a legitimate website. Several conventional techniques for detecting phishing websites have been suggested to cope with this problem. One could even land on a phishing site by mistyping a URL. In this study, a Multilayer Perceptron Learning approach is used after applying 10-fold cross validation as a preprocessing for website phishing classification which gives almost 100% accuracy. The experimental results show that the performance of the multilayer perceptron learning classifiers improved the results up to a greater extent.
The problem of Websites phishing has grown considerably in recent years, and phishing is considered as one of the most hazardous crimes, which may cause great and adverse effects on online business. It is used to obtain user-sensitive financial and personal information. In a Website phishing attack, the phisher creates a similar webpage which forces one to believe that it is a legitimate website. The phishing problem is considered as a vital issue in industry especially in the field of e-banking and e-commerce, because huge number of online transactions involving payments are made. Website phishing is considered to be a huge problem in web security as well (Dedakia and Mistry, 2015).
Most internet resources such as search engines, email services, social network sites, gaming services, banks, financial organizations, and telecommunication operator websites are highly favored by cybercriminals, and website phishing is one of the major cybercrimes among all the cybercrimes happened (Tan and Chiew, 2014).
Since today all the information are shared online. This gives chances for criminals to hack personal or financial information such as usernames, passwords, account numbers and national insurance numbers. In website phishing, the hacker creates a similar website which forces people to believe that it is the original website, and when the user perform some action on it, they will steal that information.
Several techniques were used for the classification of website phishing. In this study, a Multilayer Perceptron algorithm is used which shows a great increment in the accuracy (Panchal et al., 2011) . Phishing is a fraud technique that uses a mixture of social engineering and technology to gather sensitive and private information, such as passwords and credit card details by masquerading as a reliable person or business in an electronic communication. The fake websites are designed to mimic the look of a real company webpage. The phishing attackers use the trick by employing different social engineering tactics such as threatening, to append user accounts if they do not complete the account update process or provide other information to validate their accounts or some other reasons to get the users to visit their fake web pages.
Detecting fake websites is a critical step towards protecting online transactions. Website Phishing has a huge effect on the financial and other online commerce; detecting this attack is a significant step towards protecting against website phishing attacks. The inspiration behind developing this system is that people nowadays heavily depend on E-commerce websites for buying anything, and for sharing the information, they use private information like username, password, credit card details, and social security number.
To detect whether websites are Legitimate, Phishing or Suspicious, this system has been developed. Hence there is need for efficient mechanism, for the detection of website phishing. Website phishing is a very complex issue to understand and analyze, as it is a mixture of technical and social dynamics in which there is no known single silver bullet to solve it entirely. Despite the great quantity of applications available for website phishing detection, there are solutions that utilize machine learning mining techniques in detecting phishing websites. It increases the safety level but not fully, hence Multilayer Perceptron techniques is used which shows a great result and increases the accuracy.
Website phishing is a cybercrime attack which targets the user rather than the computer system. It is a slightly new Internet crime in contrast with other forms, such as, virus and hacking. The website phishing problem is a hard problem because of the fact that it is very easy for an attacker to create a fake website similar to the original one (Kadam and Dawar, 2013).
There are some techniques which use a pictorial form of dataset to detect phishing as shown in Figures 1 and 2 (Fatt and Chiew, 2014).
Several approaches were applied for the classification of website phishing, so far. The method proposed by Ali (2017) used a feature selection method with Supervised Machine Learning algorithm. The method proposed by Zhuang et al. (2012) used an ensemble classification algorithm which combines the predicted results from different classification algorithms of website phishing.
The method proposed by Singh et al. (2015) used feature selection techniques and dimensionality reduction approach for the classification of website phishing and obtained as accuracy of 97.5, by using Random forest. The method proposed by Blum et al. (2010) used a Lexical Feature Based Phishing URL Detection Using Online Learning. The method proposed by Basnet et al. (2008) used various types of machine learning classification techniques and achieved AUC of 98.13%.
The method proposed by James et al. (2013) also used machine learning algorithms. The method proposed byNaresh et al. (2013) use a Link Guard Algorithm for website phishing detection and prevention. The method proposed by Nguyen et al. (2013) used a Heuristic URLBased Approach for classification. The method proposed by Afroz and Greenstadt (2011) described profiles of trusted websites' appearances to detect website phishing.
The method proposed by Jo et al. (2010) in addition to blacklists, white lists and classifications used in the systems, considered websites' identity claims. In that, their phishing detection system mimics this human skilled behavior. Given a website, their system learns the identity that this website claims, and figures out the textual relevance between the claimed identity and other features in the website. Their phishing detection system then uses this textual relevance as one of the features for classification of the websites.
Kim et al. (2013) proposed a two-phase, score-based approach to detect a phishing website. The first phase checks the format of the requested URL to detect whether it is suspicious. The second phase applies a series of validations to the URL by checking whether the specified domain name exists either in its blacklist or white list.
The method proposed by Ramanathan and Wechsler (2012) used Latent Dirichlet Allocation for extracting the features, and AdaBoost algorithm for the classification of website phishing.
In order to overcome the issue of website phishing, Layton et al. (2009) used a diff which takes the phishing websites and original websites as input and returns the differences between these two. The difference presents a new overview on the data that was previously unused and presents a novel way to increase the capability of clustering algorithms to find good, discrete and separated clusters within the data.
Shahriar and Zulkernine (2011) classified the existing works based on information sources. The classification would not only provide convenient information to develop new anti-phishing approaches or expand existing techniques, but also enable one’s understanding on the limitations of the existing techniques.
Aburrous et al. (2008) used Fuzzy Logic operators to characterize the website phishing factors, and they used indicators as fuzzy variables.
First of all, dataset is collected, then 10-fold crossvalidation is applied on it and then, Multilayer perceptron algorithm is used for pattern classification. The performance measure is then evaluated in terms of accuracy as shown in Figure 3.
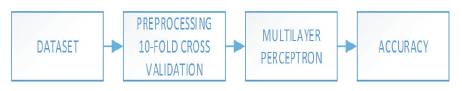
Figure 3. Flowchart of Methodology
The dataset used is taken from UCI repository.1353 instances are collected from different sources as shown in Table 1. The PHP script was plugged with a browser and 548 legitimate websites out of 1353 websites were collected. There are 702 phishing URL's and 103 suspicious URL's.

Table 1. Dataset Representation
Multilayer perceptrons (MLPs) are feed forward neural networks. It is trained by using the standard back propagation algorithm. Since it is a type of supervised network, it requires a desired response to be trained. They know how to transform an input data into a desired response, hence they are widely used for pattern classifications. This is perhaps the most popular network architecture in use today. In most of the neural network applications, MLPs perform very well. Important point to notice in Multilayer Perceptrons (MLP) is the choice of number of hidden layers, and the number of units in these layers and the model of MLP neural network is shown in Figure 4. MLPs are useful in research for their ability to solve problems stochastically. The perceptron equation is given below:
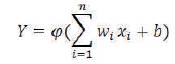
where, w denotes the vector of weights, x is the vector of inputs, b is the bias and is the activation function.
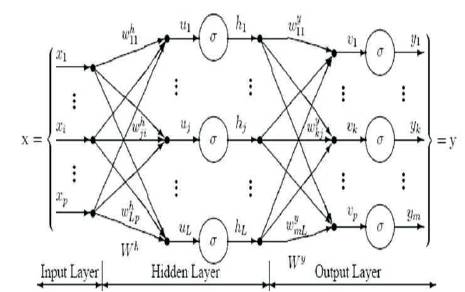
Figure 4. Model of Multilayer Perceptron Neural Network (Sonawane and Patil, 2014)
The dataset contains a lot of features like URL length, URL domain, etc. and they are classified based on that features. In this paper, 10-fold cross-validation is used in preprocessing step and then Multilayer Perceptron algorithm is applied which is trained by back propagation network (Panchal et al., 2011), and an accuracy of 99.9% is obtained, which is far better from the previous methods used. In this work, Number of hidden layers=2, Number of hidden nodes=15, alpha= 0.10, verbose=0 and epoch=10000.
The expressed results show that it performs better than all other previously applied methods, which is tabulated in Table 2. It is also feasible as compared to other approaches. The comparison graph of accurcy is shown in Figure 5.
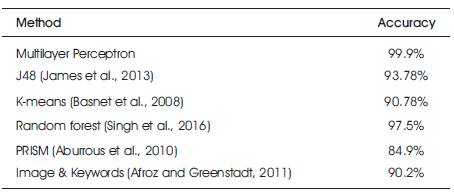
Table 2. Comparison of the Proposed Method with the Previous Methods
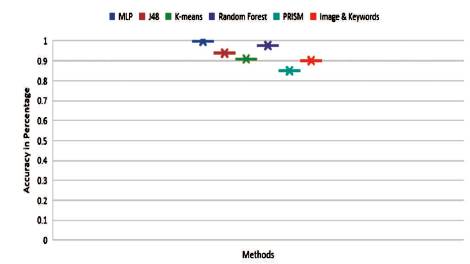
Figure 5. Comparison Graph of Accuracy
In this paper, a computational method is used for the classification of website phishing, and the experimental results show the feasibility of the proposed method clearly. Multilayer perceptron is more useful when number of instances is higher. The proposed method is more significant than the previous methods. Since website phishing is a huge problem, it requires a better technique to perform well on unseen dataset as compared to traditional classification techniques. In this paper, a 10- fold cross validation along with Multilayer perceptron is used, which shows a tremendous result of almost 100% accuracy. So, from this, it is clear that Multilayer perceptron is very much beneficial to that kind of dataset.