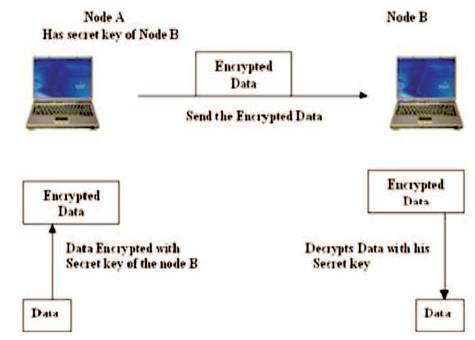
Figure 1. Symmetric Key Cryptography (Balakrishna and Rajesh, 2011)
In the recent years, a lot of research has been carried out in Mobile Ad-hoc Networks (MANETs). The main goals and challenges of security are which characterizes the routing protocol of MANET. Any node can join and leave the network routing protocol which is addressed for only efficient path formation, making the same network vulnerable to various attacks. Associativity-based Routing (ABR) is an on-demand routing protocol, i.e., routes are created only as and when needed. Normally, the routes will be available immediately and the routing tables will be updated constantly among the routes. On-Demand routing is chosen here, because it reduces the control packet traffic which is suitable for wireless network due to limited bandwidth. Protocol's dynamic nature enables MANET operation ensuring deployment in extreme/volatile circumstances. This paper proposes an Extended Public Key Cryptography (EPKCH) system. This cryptosystem is mainly designed for securing data during packet forwarding operation and also to detect malicious and selfish nodes during network initializing and packet forwarding operation. Confidentially is the basic feature provided by the public key cryptography, which also provides authentication, non-repudiation and integrity. The protocol is designed to protect the network from malicious and selfish nodes. An extended public key cryptography mechanism is implemented in ABR, in order to achieve security goals for the following parameters Path-Division Routing (PDR), Routing overhead, delay, on-demand routing, packet loss and throughput. The proposed model is stimulated using Network Simulated (NS2).
MANETs provide high mobility and device portability that enables nodes to connect to the network, and to communicate with each other. It allows the devices to maintain connection to the network as well as easily adding and removing devices in the network (Tirthraj and Verma 2009). User has a great flexibility to design such a network at cheapest cost and minimum time (Pushpneel, 2017). Mobile ad hoc network consists of large number of nodes; it forms temporary network with dynamic topology. In this network, each node communicates with each other through radio channel without any central authority. In MANETs, each node operates in a distributed peer-to-peer mode, serves as an independent router to forward messages sent by other nodes. In ad hoc network, nodes try to disrupt the proper functioning network by modifying packets, injecting packets or creating routing loops. In this case, Security is an important task. There are large numbers of secure routing protocols proposed by many researchers. They fulfill different security requirements and prevent specific attacks (Balakrishna and Rajesh, 2011). They are divided into three categories: Reactive routing protocol, Proactive routing protocol and hybrid routing (Royer and Toh 1999; Kumar et al., 2010 and Mehdi 2016).
No secure mechanism has been proposed, that can be addressed to detect malicious and selfish nodes collectively. The Extended Public Key Cryptography (EPKCH) protocol is able to detect the malicious nodes and selfish nodes collectively in order to achieve security, as it has authentication, integrity, confidentiality and non-repudiation (Nachammai and Radha 2016; Pal, 2013).
Cryptography can be used to protect sensitive and valuable information from malicious hackers. The fundamental goals of cryptography are confidentiality data integrity, authentication and non-repudiation. There are mainly two categories of cryptography mechanisms that are used for designing security based system. One is Symmetric Key Cryptography and the other is Public key (Mawada et al., 2013).
This cryptosystem uses same key for both encryption and decryption. It is also known as Secrete Key Cryptography. Both sender and receiver have the same key, when communicating with each other.
This crypto-system uses two keys, one key for encryption called public key, and other key for decryption called private key or secrete key also known as asymmetric key cryptography (Babu 2013).
Figure 1 shows symmetric key cryptography. Each user has two keys: one, public key and other, private key. The public key of each user is publically available to all other users in public key database. The public key and private key are mathematically linked. Encryption is performed using public key and decryption is performed using private key. To generate the two keys, two large random numbers p and q are chosen which relatively prime to each other. Compute product of two numbers i.e.
n=p*q
Then randomly choose encryption key e, which is relatively prime to (p-1) (q-1). To compute decryption key d, Extended Euclidian algorithms are used, i.e.
Ed = 1 mod (p-1)*(q-1)
d = e-1 mod (p-1)*(q-1)
To encrypt the message m, first it is divided into numerical block smaller than n with binary data. After that, the message (plane text) is encrypted to get cipher text c where, c= me mod n to decrypt the message, to take encrypted block, m= cd mod n.

Figure 1. Symmetric Key Cryptography (Balakrishna and Rajesh, 2011)
The extended public key cryptography is a mechanism that is the modified form of public key cryptography. To generate public key and private key, each node utilized RSA algorithms. This cryptosystem is mainly designed for securing data during packet forwarding operation and also to detect malicious and selfish nodes during network initializing and packet forwarding operation.
Figure 2 shows public key cryptography. The symmetric key cryptography and public key cryptography are limited in their operation; they do not possess the requisite features to secure the MANETs’ operation. Hence, the existing public key cryptography mechanism has been extended to secure the MANET's operation (Dalal and Singh 2012). The extended public key cryptography mechanism is basically suited for MANET environment. But apart from MANET, it is suited well for other environment also. Confidentiality is the basic feature provided by the public key cryptography, but extended public key cryptography provides authentication, non-repudiation and integrity, additionally.
It is a mobile routing protocol invented for wireless ad hoc networks, also known as Mobile ad hoc networks (MANETs’) or wireless mesh networks. ABR was invented in 1993, filed for a US patent in 1996, and the patent was granted in 1996. ABR was invented by Chai Keong Toh while doing his Ph.D. at Cambridge University. In the 1990s, the Internet was largely wired. Toh was working on a different Interne-tthat of a rapidly deployable, infrastructureless, self-organizing, self-configuring mobile Internet (Wikipedia, 2018). The challenges in such a network are mobility of nodes and link dynamics. Toh's prime argument is that there is no point in choosing a node to route, which is unstable or going to be broken soon. So, he introduced a new routing metric (known as associativity ticks) and the concept of associativity, i.e., link stability among nodes over TIME and SPACE.
To achieve anytime anywhere computing, computers must be able to connect to each other wirelessly and automatically. The Internet Protocol at that time did not address mobility, and the formation of a rapidly deployable mobile internet. The underlying protocols for Internet were Transmission Control Protocol (TCP) / User Datagram Protocol (UDP) / Internet Protocol (IP). Those protocols do not support spontaneous network creation, and do not handle dynamics due to mobility of computers. The assumption was, end hosts are static hosts and they do not move. Another assumption was the network is wired (with copper wires or fiber).
Since existing internet protocols cannot support ad hoc mobile computing, a new mobile internet is needed. This calls for a new network layer software that will enable anytime and anywhere mobile computing, while at the same time, retaining compatibility with IP/UDP/TCP protocols already present in the wired Internet. ABR is an on-demand routing protocol, i.e., routes are created only as and when needed. This is in contrast to the existing Internet, where routes are immediately available and routing tables are constantly updated among routers. Hence, on-demand routing is chosen because it can reduce the amount of control packet traffic and this is suitable for a wireless network because the bandwidth is limited (Murthy and Manoj, 2013).
From Figure 3 and Table 1, it is observed that the developed method surpassed the existing performance by above 95%, when there are 10 to 50 of nodes in the network.
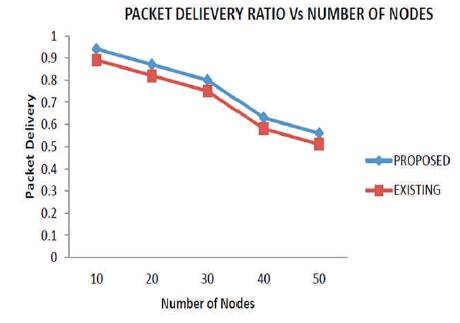
Figure 3. Packet Delivery Ratio vs Number of Nodes
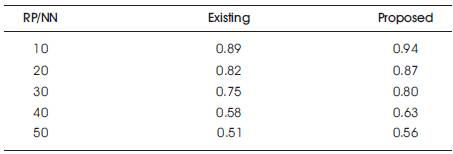
Table 1. Packet Delivery Ratio vs Number of Nodes
Finally routing overhead is analysed using the two algorithms, when the total number of nodes are varied from 10 to 50, and the simulation results are shown in Figure 4 and Table 2. Simulation results reveal that the proposed algorithm reduces the routing overhead than existing algorithm.
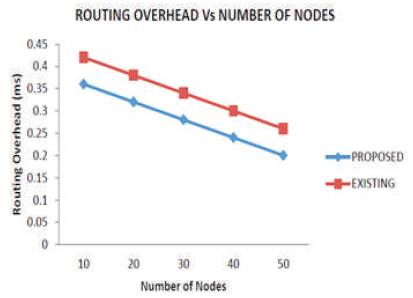
Figure 4. Routing Overhead vs Number of Nodes
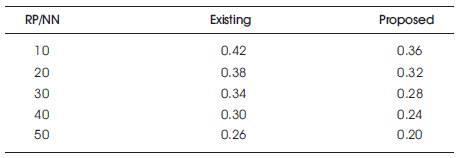
Table 2. Routing Overhead vs Number of Nodes
The impact of packet drop on end-to-end delay is analysed using the two algorithms and the simulation results are shown in Figure 5 and Table 3. Figure 5 and Table 3 describes the decrease in delay obtained by the proposed model, when there are 10 to 50 number of nodes.
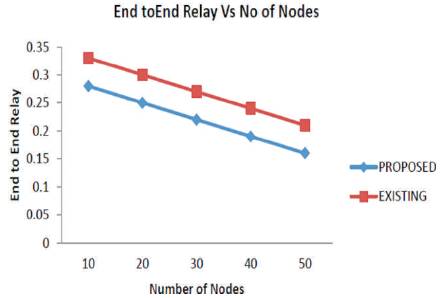
Figure 5. End-to-End Delay vs. Number of Nodes
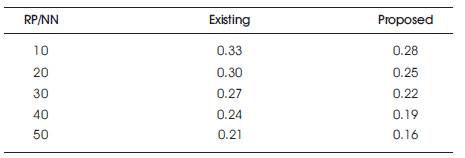
Table 3. End-to-End Delay vs Number of Nodes
Figure 6 and Table 4 shows that the proposed scheme increases the throughput with increasing number of nodes, compared to the existing algorithm.
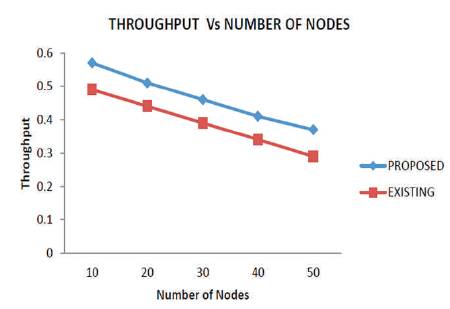
Figure 6. Throughput vs Number of Nodes

Table 4. Throughput vs Number of Nodes
The mode of communication is always a major concern because, anything that moves over the open air medium is susceptible to be picked up by an unauthorized access. The activity nodes are discussed in EPKCH which are grouped into modes while working and these activities are shown in MANET operation. The results show that the proposed work provides higher delivery ratio, throughput and lower routing overhead, end-to-end delay than existing scheme. The public key cryptography algorithm can be extended to enhance the security in MANET.