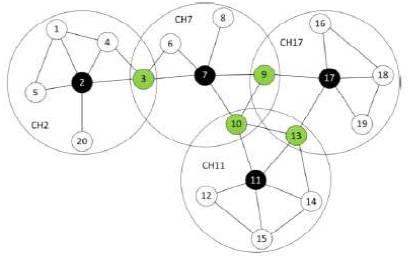
Figure 1. Clustering in MANET
In recent years, there has been a lot of interest in Mobile Ad hoc Networks (MANET). Mobile ad hoc networks are groups of mobile nodes. These nodes send and receive messages, and can communicate with each other. Thus, the network builds its own network structure, that is not dependent on the infrastructure central administration. MANET has been used in environments of poor communication, such as those in which the infrastructure cannot be built like, disaster areas, and war zones. In addition to its key characteristics, MANET node contains various attribute information, such as mobility, velocity, and energy. However, the MANET has constraints, such as transmission band and energy consumption. These constraints cause disconnections between the nodes and rerouting. Most of the researchers in MANET focus on the clustering based routing protocol which can sufficiently enhance performance, scalability, and energy efficiency of sufficient routing protocol for mobile adhoc network. In this paper, performance analysis of cluster based energy efficient routing protocols such as Low Energy Adaptive Clustering Hierarchy (LEACH) and Hybrid Energy - Efficient Distributed (HEED) protocols has been carried out for MANET through network simulation. The HEED protocol provided better performance compared to LEACH protocol and also increased throughput with number of nodes, transmission range, and mobility.
Mobile Ad hoc Network (MANET) networks are ad hoc networks which consists of a collection of nodes that communicate with one another over wireless links and do not have a hard and fast infrastructure (Pu and Shen, 2010). Another feature within the MANET is that the quality of nodes may leave or be a part of the network. Consequently, parameters like transmission rate and delay varies this kind of network (Oh and Lee, 2017; Movahedi et al., 2016). The nodes within the adhoc network have the chance to act as emitters, receivers or forwarders. This characteristic is extremely vital, since the routes or routes to succeed in the destination will have many leaps (Xie and Pan, 2016; Prabu and Subramani, 2014). MANETs are a sort of wireless ad hoc networks that as a rule type, is a routable mesh within the sort of an information link layer. On different hand, a mobile ad hoc network may be a style of decentralized wireless network that does not depend upon a pre-existing infrastructure, like routers access points (managed wireless networks) (Kumar et al., 2015). During this approach, every node participates within the routing through the forwarding of knowledge to different nodes and handling the knowledge dynamically. These networks offer flexibility and autonomy with none central administration, all nodes being equal. The connections are attainable by the multiple nodes that these networks present, that lead the North American nation to constant changes of topology by the quality that they present (Prabu and Subramani, 2014; Brar et al., 2016). Associate reconciling clump formula improves the performance, by increasing the measurability of the network, economical band breadth usage and additionally decreases the management overhead of the routing protocol (Ahmed and Hussain, 2016; Ravi and Jayanthi, 2015). Additionally it sustains the quality dearth and maintains the soundness and hardiness of network. In clustered structure, the total network is split into self-managed teams of nodes known as clusters. These clusters are dynamically reconfigured with modification in topology of the network. Cluster head is the node that represents the whole cluster as one entity and carries bound additional responsibilities. The dearth of associate economical, climbable and sensible methodology for ad hoc networks, within the field of routing integrated with clump, galvanized a study during this space by Oh and Lee (2015).
Clustering means a way to reconfigure all nodes into small virtual groups according to their regional vicinity and is defined as Cluster Head (CH) and Cluster Member (CM) that are determined with the same rule (Xu et al., 2015). Every clustering algorithm consists of two mechanisms, cluster formation, and cluster maintenance. In cluster formation, cluster heads are selected among the nodes to form clusters. In cluster maintenance, when cluster head and cluster member go for threshold, the routing will be affected (Figure 1).

Figure 1. Clustering in MANET
Classification of Routing Protocols in MANET square measures self-organized and self-configurable systems, whose nodes establish and maintain property between them, supports the functionalities and characteristics of the nodes, and the classification calls discovery routes. This classification is the best glorious one and, is completed in keeping with, however the routes in MANET networks’ square measure discovered. Cluster Head is the node that manages the cluster activities likes managing cluster method, change routing table, and discovery of recent routes. The nodes square measure apart from the cluster head within the cluster square measure referred to as Ordinary Nodes (ON). Nodes having inter-cluster links, might communicate with over one clusters’ square measure referred to as Entry Nodes (EN) or Gateway Node (GN) (Totani et al., 2016). If the destination is within the cluster, normal nodes send the packets to their cluster head that distributes the packets within the cluster, or if to be delivered to alternative cluster, then forward them to a gateway node. In such method, solely cluster heads and gateways participate within the propagation of routing update or management messages. This considerably reduces the routing overhead and conjointly solves quantifiability drawback in dense networks. Consequent part of cluster maintenance comes into image, once there's the node movement. So, it has to do re-affiliations among normal nodes and cluster heads. To avoid excessive computation within the cluster maintenance, current cluster structure ought to be preserved the maximum amount as potential (Lee and Ra, 2015).
Clustering in MANET networks has more advantages compared to the classical networks by Abderezak Touzene et al. (2015). They are as follows:
Low-Energy Adaptive Clustering Hierarchy (LEACH) algorithm is enabled for efficient energy consumption routing path. The LEACH algorithm is performed in rounds. Each round is divided into two steps: a setup step and a next step. The setup step is the start of the round; the next step is the steady state that marks the end of the round. In the setup step, the network sets the cluster and network for communication. In the steady state, the cluster member sends the packet to the cluster head node, and the cluster head node sends the packet to the base station (Hussain and Ahmad, 2014). Figure 1 shows a round in the LEACH algorithm. To select the cluster head node, the LEACH algorithm calculates the probability of the selection of the cluster head node. The cluster member node which performs the role of the cluster head node, has a probability of 0 for the energy efficiency cluster. The cluster member node that does not perform the role of the cluster head node has a probability that is calculated by following equation.
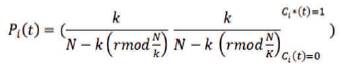
where, Pi(t) denotes the probability of the cluster head node exchange and N denotes the number of nodes in the network. In addition, k represents the number of clusters in the network and r refers to the rounds. Ci(t) is the case in which the cluster head node performs. When the cluster head node does not perform, the probability of the cluster head node is 1. Otherwise, Ci(t) is 0. The cluster member nodes send the data from their own time slot by Time Division Multiple Access (TDMA) method. At other times, the cluster member nodes remain; thus, the energy is used efficiently and the network lifetime is increased. However, the cluster head node is always awake because it receives the data sent to the cluster member nodes and sends the data to the base station. In addition, the cluster head nodes are located out of the coverage area; thus, the energy is not used efficiently (Prabu and Subramani, 2012) .
The Hybrid Energy-Efficient Distributed (HEED) clustering algorithm uses density according to the number of nodes for energy-efficient communication. For initializing the cluster head node, the node calculates the selection of probability of the cluster head node using the energy of the nodes. The equation is shown as CHprob =CprobEresidual Emax where, CHprob means the selection of probability of the cluster head node and Cprob denotes the constant of the probability of the initializing cluster head node. Eresidual refers to the residual energy of the node, while Emax is the max initializing energy of the node (Hussain and Ahmed, 2016). The network compares the selection of probability of the cluster head node and random constant values. The network selects the cluster head node based on the probability. The cluster member node selects the cluster head node and calculates the Average Minimum Reachability Power (AMRP), which is given by the following equation,
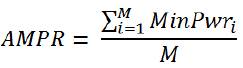
where, M means the number of cluster member nodes in the coverage area and MinPwri means the minimum energy consumption when node sends a message to the cluster head node. Each node compares the AMRP of the cluster head nodes and joins the cluster head node with the minimum AMRP value. The cluster head node forms a coverage of approximately 2.7 times, the transmission range of nodes for efficient communication. In addition, the cluster head node sends the packet to the base station. Figure 1 depicts the coverage set for forming clusters and communication. Cluster head node sets the coverage, and the network forms the energy-efficient cluster. The HEED algorithm forms the cluster in accordance with properties such as cluster size. It thereby manages a distributed network and the energy consumption is decreased. Furthermore, it maintains the number of clusters and the overflow is thus decreased.
The experimental analysis of the routing protocols has been evaluated with different scenarios such as varying max speed 5, 10, 15, 20, and 25 (m/s), varying pause time 0, 100, 200, 300, and 400 (s), and the use of a different number of nodes, such as 20,40,60,80,and 100. NS-2 simulation is used to compare LEACH and HEED routing protocols. Table 1 illustrates the parameter type and the values.
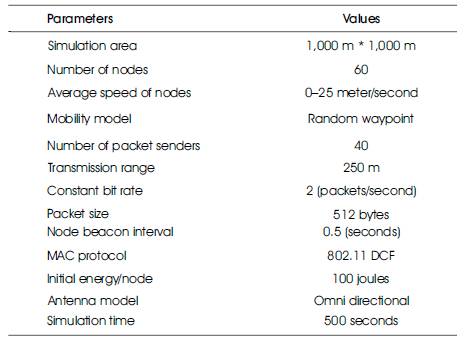
Table 1. Simulation Parameters
In this section, performance analysis of LEACH protocol and HEED protocol for MANET is done through simulation NS2. The following performance metrics are used to evaluate the performance through simulation.
Throughput is the ratio of the total amount of data that reaches a receiver from a sender to the time it takes for the receiver to get the last packet. It is measured in bits/sec or packets per second. A high throughput network is desirable. It is calculated by the given equation.

Figure 2 shows the performance comparison of LEACH protocol and HEED protocol for MANET in terms of number of nodes. Finally, the HEED protocol increased the throughput compared to LEACH protocol, with increasing number of nodes. So the HEED protocol provides better performance compared to LEACH protocol.
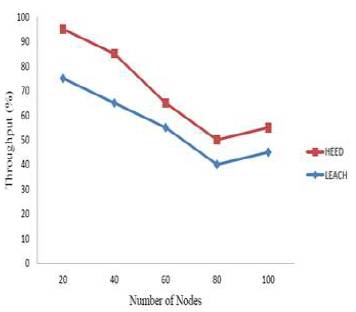
Figure 2. Throughput vs Number of Nodes
Figure 3 shows the performance comparison of LEACH protocol and HEED protocol for MANET in terms of transmission range. Finally the HEED protocol increased the throughput compared to LEACH protocol with increasing transmission range. So the HEED protocol provides better performance compared to LEACH protocol.
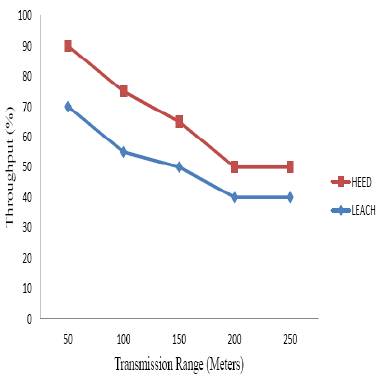
Figure 3. Throughput vs Transmission Range (meters)
Figure 4 shows the performance comparison of LEACH protocol and HEED protocol for MANET in terms of mobility. Finally, the HEED protocol increased the throughput compared to LEACH protocol with increasing mobility. So the HEED protocol provides better per formance compared to LEACH protocol.
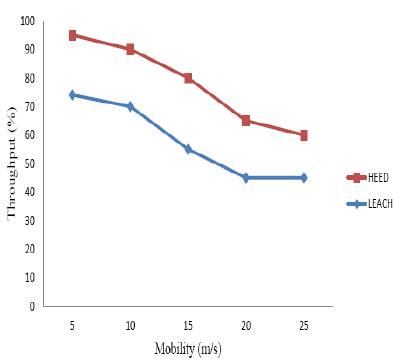
Figure 4. Throughput vs Mobility (m/s)
As MANETs have attracted more attention, in recent years, lots of research have been done addressing all kinds of issues related to them. Among them, cluster based routing is an important research issue, and research associated with routing is always in focus. Dynamic routing plays an important role in the performance of a MANET. This paper discussed fundamental concepts about the LEACH and HEED routing protocols including the definition of cluster and clustering, and then the necessity of clustering for a large dynamic MANET, and its side effects and cost of clustering. Finally, the performance analysis of LEACH and HEED protocols are compared through the network simulation with the parameters of throughput with increased number of nodes, transmission range and mobility.