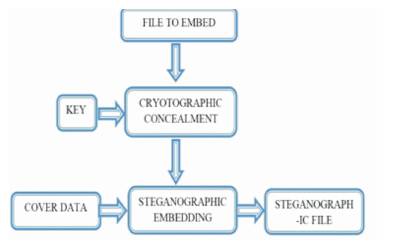
Figure 1. Steganography System Architecture
Audio steganography is a security technique by which a secret data to be transmitted over a public insecure channel is embedded into an audio cover object that hides it in such way that third party cannot detect the presence of the message. In this proposed system, DES cryptographic encryption algorithm is used to encrypt data before hiding it into the cover object for additional security. For the purpose of data encoding into audio samples, LSB coding algorithm is used. The overall system gives a relatively secure system that hides the secret message, a feature is provided by steganography, beside deformations the structure of the message, a feature provided by cryptography, which together leads to prepare the message travel through public channels.
Audio steganography is the scheme of hiding the existence of secret information by concealing it into another medium such as audio file. Steganography does not alter the structure of the secret message, but hides it inside a cover audio so that it cannot be seen. A message in a cipher text, for instance, might arouse suspicion on the part of the recipient while an “invisible” message created with steganographic methods will not. In other word, steganography prevents an unintended recipient from suspecting, that the data exists. In addition, the security of classical steganography system relies on secrecy of the data encoding system. Once the encoding system is known, the steganography system is defeated.
The basic model of Audio steganography consists of Carrier (Audio file), Message and Password. Carrier is also known as a cover-file, which conceals the secret information (Jayaram P. Ranganatha H. R. and Anupama H. S., 2011). Message is the data that the sender wishes to remain it confidential. Message can be plain text, image, audio or any type of file. Password is known as a stego-key, which ensures that only the recipient who knows the corresponding decoding key will be able to extract the message from a cover-file. The cover-file with the secret information is known as a stego-file.
The information hiding process consists of following two steps:
For data extraction: After reading the stego-object, the information bits can be retrieved from the stego-object according to the algorithm used in data hiding.
Many researchers studied the field of Steganographic audio files of different methods and principles. In 2011, Bimbi Koduru Summer proposed an application Using Audio Files. Steganography is a form of science that deals with cryptic information. It is the art of writing in cryptic text that is unrecognizable to a person who doesn't hold the key to decrypt it. Steganography is not a new form of science. In fact, Steganography is derived from the Greek word “steganos”, which means hidden or secret and “graphy” means writing or drawing. Thus steganography means secret writing. In contemporar y terms, steganography has evolved into a digital strategy of hiding a file in any form of multimedia such as an image, an audio file or even a video file (Bimbi Koduru,2009).
In 2015, R. Udayakumar, K.P. Kaliyamurthie, Khanaa and A.V. Allin Geo proposed Modeling of Steganography with Audio Files Using Matlab. The main objective of their project is to enable secure sending and receiving of secret data without a third party reading it. In their project, the authors hide data contents of a file in to a wave audio file. The audio file does not have change in its quality before and after this technique in implemented. The stego-audio file is send to the destination without any detection from any of external sources. Even if it is detected, the secret data meant for the receiver cannot be read or understood as it is encrypted (D.Bhavana, D.Ravi Tej, M.Puneeth, A.Harini, Y.Mani Shankar, and T.Sai Madhuri, 2015).
The growing possibilities of modern communications need the special means of security. The network security is becoming more important as the amount of data being exchanged on the Internet is increasing. Security requirements are necessary in both at the final user level and at the enterprise level, especially since the massive utilization of personal computers, networks, and the Internet with its global availability. Throughout time, computational security needs have been focused on different features: secrecy or confidentiality, identification, verification, non-repudiation, integrity control and availability. This has resulted in an explosive growth of the field of information hiding. In addition, the rapid growth of publishing and broadcasting technology also requires an alternative solution in hiding information (Bendalam Vijay, and Jallu Swathi, 2014).
There are a number of ways for securing data. One is cryptography, where the sender uses an encryption key to scramble the message. This scrambled message is transmitted through the insecure public channel, and the reconstruction of the original, unencrypted message is possible only if the receiver has the appropriate decryption key.
Second is Steganography, the steganography itself is not a new technique. However, it experiences a renaissance due to the ubiquitous use of computers and multimedia; especially when graphical and audio data are involved. Consequently, most available implementations of steganographic algorithms work on graphics or sound. Figure 1shows steganography system architecture.

Figure 1. Steganography System Architecture
Cryptography is an important element of any strategy to address message transmission security requirements. Cryptography is the study of methods of sending messages in disguised form so that only the intended recipients can remove the disguise and read the message. It is the practical art of converting messages or data into a different form, such that no-one can read them without having access to the 'key'. The message may be converted using a 'code' (in which case each character or group of characters is substituted by an alternative one), or a 'cypher' or 'cipher' (in which case the message as a whole is converted, rather than individual characters).Cr yptology is the science underlying cryptography (Z. V. Patel, and S. A. Gadhiya, 2015).
The word steganography is derived from the Greek words “stegos” meaning “cover” and “grafia” meaning “writing” defining it as “covered writing”. Steganography is one such pro-security innovation in which secret data is embedded in a cover. The notion of data hiding or steganography was first introduced with the example of prisoners' secret message by Simmons in 1983.
Steganography and cryptography are closely related. Cryptography scrambles messages, so they cannot be understood. Steganography on the other hand, will hide the message so there is no knowledge of the existence of the message in the first place. In some situations, sending an encrypted message will arouse suspicion while an “invisible” message will not do so. Both sciences can be combined to produce better protection of the message. In this case, when the steganography fails and the message can be detected, it is still of no use as it is encrypted using cryptography techniques. There exist two types of materials in steganography: message and carrier. Message is the secret data that should be hidden and carrier is the material that takes the message in it. There are many types of steganography methods. In this paper, the authors are going to take a short look at different steganography methods. Figure 2 shows the different categories of file formats that can be used for steganography techniques.
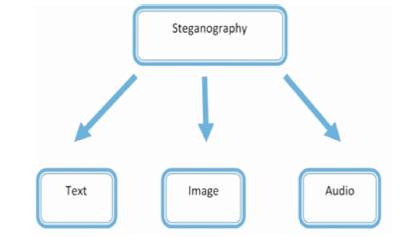
Figure 2. Different Categories of File Formats
An audio file is read from computer libraries or by recording a voice from the user is an analog signal which needs a conversion to digital signal in order to allow performing processing and modifying on it. Conversion from analog to digital is done in the following steps.
Sampling is the reduction of a continuous signal to a discrete signal as shown in Figure 3. A common example is the conversion of a sound wave (a continuous signal) to a sequence of samples (a discrete-time signal).
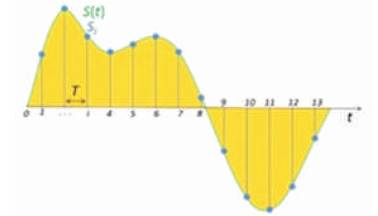
Figure 3. Sampling of an Analog Signal
A sample is a value or set of values at a point in time. A sampler is a subsystem or operation that extracts samples from a continuous signal. A theoretical ideal sampler produces samples equivalent to the instantaneous value of the continuous signal at the desired points.
It is the process of mapping a large set of input values to a (countable) smaller set – such as rounding values to some unit of precision. A device or algorithmic function that performs quantization is called a quantizer. The simplest way to quantize a signal is to choose the digital amplitude value closest to the original analog amplitude. Figure 4 shows the original analog signal (green), the quantized signal (black dots), the signal reconstructed from the quantized signal (yellow) and the difference between the original signal and the reconstructed signal (red).
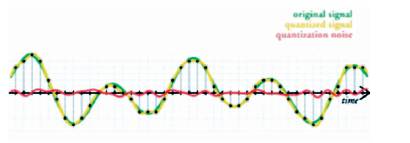
Figure 4. Quantization of an Analog Signal
The primary goal of steganography is to reliably send hidden information secretly, not merely to obscure its presence. Steganography in today's computer era is considered a sub-discipline of data communication security domain. Lately, new directions based on steganographic approaches started to emerge to ensure data secrecy. Rather than as a substitute to existing solutions, these approaches could achieve better data secrecy if combined with conventional security techniques. Modern techniques of steganography exploit the characteristics of digital media by utilizing them as carriers (covers) to hold hidden information. Covers can be of different types including image, audio, video, text, and IP datagram. An example of audio steganography is depicted in Figure 5, where the cover file in use is a digital audio file (Fatiha Djebbar, Beghdad Ayad, Karim Abed Meraim, and Habib Hamam).
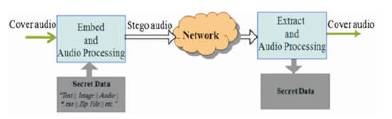
Figure 5. Example of Digital Audio Cover Object
The sender embeds data of any type in a digital cover file using a key to produce a stego-file, in such a way that an observer cannot detect the existence of the hidden message. At the other end, the receiver processes the received stego-file to extract the hidden message. An obvious application of such steganographic system is a covert communication using innocuous cover audio signal, such as telephone or video conference conversations.
The particular importance of hiding data in audio files results from the prevailing presence of audio signals as information vectors in our human society. Prudent steganography practice assumes that the cover utilized to hide messages should not raise any suspicion to opponents. In fact, the availability and the popularity of audio files make them eligible to carry hidden information. In addition, most steganalys efforts are more directed towards digital images leaving audio steganalys relatively unexplored. Data hiding in audio files is especially challenging because of the sensitivity of the HAS. However, HAS still tolerates common alterations in small differential ranges. For example, loud sounds tend to mask out quiet sounds. Additionally, there are some common environmental distortions, to the point that they would be ignored by listeners in most cases. These properties have led researchers to explore the utilization of audio signals as carriers to hide data.
Steganography must not be confused with cryptography that involves transforming the message so as to make its meaning obscure to malicious people who intercept it. In this context, the definition of breaking the system is different. In cryptography, the system is broken when the attacker can read the secret message. Breaking a steganographic system needs the attacker to detect that steganography has been used and he is able to read the embedded message. According to Kaliyamurthie et.al (2014), Steganography provides a means of secret communication, which cannot be removed without significantly altering the data in which it is embedded. In addition, the security of classical steganography system relies on secrecy of the data encoding system. Once the encoding system is known, the steganography system is defeated (Varsha, and 8Rajender Singh Chhillar, 2015).
However, it is always a good practice to use Cryptography and Steganography together for adding multiple layers of security. By combining, the data encryption can be done by a software and then embed the cipher text in an audio or any other media with the help of stego key. The combination of these two methods will enhance the security of the data embedded. This combined chemistry will satisfy the requirements such as capacity, security and robustness for secure data transmission over an open channel.
The algorithm's overall structure is shown in Figure 6. There are 16 identical stages of processing, termed rounds. There is also an initial and final permutation, termed IP and FP (Wang Tianfu, and K. Ramesh Babu 2011).
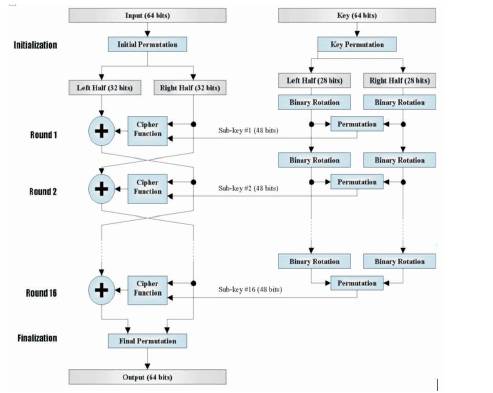
Figure 6. DES Structure
The Feistel (F) function operates on half a block (32 bits) at a time and consists of four stages, as shown in Figure 7.
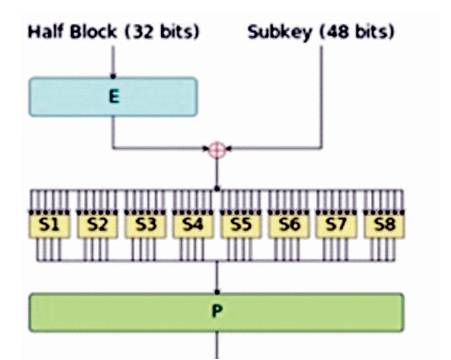
Figure 7. The Feistel (F) Function Structure
The 32-bit half-block is expanded to 48 bits using the expansion permutation, denoted E in the diagram, by duplicating half of the bits. The output consists of eight 6- bit (8 * 6 = 48 bits) pieces, each containing a copy of 4 corresponding input bits, plus a copy of the immediately adjacent bit from each of the input pieces to either side
The result is combined with a sub key using an XOR operation. 16 48-bit sub keys — one for each round — are derived from the main key.
After mixing in the sub key, the block is divided into eight 6- bit pieces before processing by the S-boxes, or substitution boxes. Each of the eight S-boxes replaces its six input bits with four output bits according to a non-linear transformation, provided in the form of a lookup table. The S-boxes provide the core of the security of DES — without them, the cipher would be linear, and trivially breakable
Finally, the 32 outputs from the S-boxes are rearranged according to a fixed permutation, the P-box. This is designed so that, after permutation, each S-box's output bits are spread across 4 different S boxes in the next round.
A very popular methodology is the LSB (Least Significant Bit) algorithm, which replaces the least significant bit in some bytes of the cover file to hide a sequence of bytes containing the hidden data. That is usually an effective technique in cases where the LSB substitution doesn't cause significant quality degradation, such as in 24-bit bit maps. In computing, the Least Significant Bit (LSB) is the bit position in a binary integer giving the units value, that is, determining whether the number is even or odd. The LSB is sometimes referred to as the right-most bit, due to the convention in positional notation of writing less significant digit further to the right as shown in Figure 8. It is analogous to the least significant digit of a decimal integer, which is the digit in the ones (right-most) position (Jayaram P, Ranganatha H R, and Anupama H S, 2011).
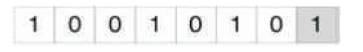
Figure 8. LSB of a Byte
The binary representation of decimal 149, with the LSB highlighted. The MSB in an 8-bit binary number represents a value of 128 decimal. The LSB represents a value of 1. For example, to hide the letter "a" (ASCII code 97, which is 01100001) inside eight bytes of a cover, you can set the LSB of each byte like this:
The application decoding the cover reads the eight Least Significant Bits of those bytes to recreate the hidden byte—that is 0110001—the letter "a", as we realize, using this technique it lets you to a byte every eight bytes of the cover.
Among different information hiding techniques proposed to embed secret information within audio file, Least Significant Bit (LSB) coding method is the simplest way to embed secret information in a digital audio file by replacing the least significant bit of audio sample with a binary message. In this technique, LSB of binary sequence of each sample of digitized audio file is replaced with binary equivalent of secret message. For example, if we want to hide the letter 'A' (binary equivalent 01100101) to an digitized audio file where each sample is represented with 16 bits, then LSB of 8 consecutive samples (each of 16 bit size) is replaced with each bit of binary equivalent of the letter 'A' as shown in Figure 9.
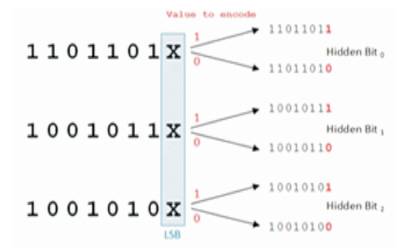
Figure 9. Example of LSB Coding
In this proposed system, a secure system of hiding information by Steganography is implemented, and for additional security, cryptography is used beside steganography.
An audio file is used as a cover object, in which the data would be hiden. Hiding process is done using LSB algorithm, by which, each bit from data to be hiden replaces the LSB of one sample from the audio cover object. As it is discussed, a cryptographic encryption algorithm is used to encrypt data before being hide into the cover object. The algorithm used in proposed system is DES which is a symmetric algorithm of 64 bit key length. In order to compute the minimum number of samples needed to cover the encrypted file, and consequently the minimum length of the cover audio, we must first calculate the length of the text file since it is the constrain of the whole process. First four bytes of the file is reserved for its length. This step is important in the context of two issues, first, to alarm the system about the lower limit of the cover signal length, and second, is for the data extraction, to notice the receiver to which sample of the cover object it should extract data.
For data extraction, the text file length, which concatenated with the original data in data hiding process, is extracted first then the encrypted data extracting begins. Finally, the decryption algorithm is applied to produce the original data.
These steps are done as shown in Figure 10 in following sequence for data hiding:
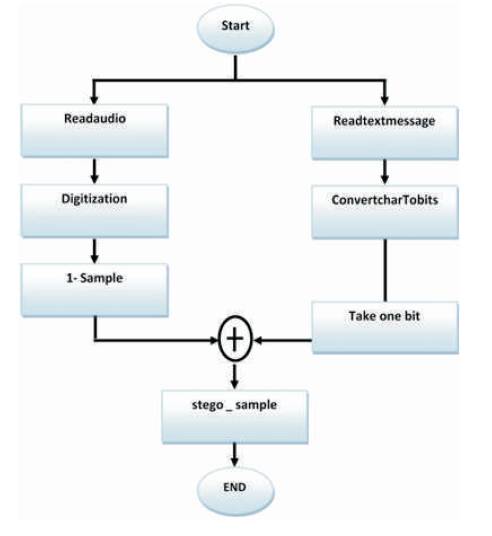
Figure 10. Data Embedding
By completing these steps, stego object is ready to be transmitted to the receiver side.
The following steps are done as shown in Figure 11 for data extracting in sequence:
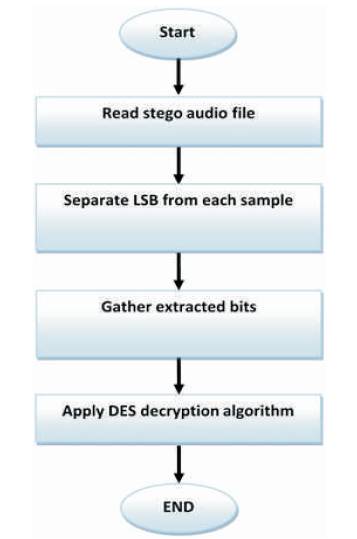
Figure 11. Data Extracting
A secure transmission system is produced by means of pure Steganography, without using stego key in the embedded data distribution. The type of steganography used is Audio Steganography which means that the cover object is an audio file that would carry data bits in LSBs of its samples. For additional security, a symmetric cryptographic algorithm, DES, is used to encrypt the data before embedding it into the cover object.
The following are suggestions for future work on this proposed system to improve its implementation and results: