Figure 1. Illustrates the Cloud Deployment Model
Cloud service providers offer cost-effective, scalable data storage for a fraction of the cost of alternatives. Cloud resources are often shared by a large number of people, but they are also dynamically reallocated based on demand. Due to human error and hardware/software problems, cloud data integrity is questionable. Several methods have been developed by data holders and public verifiers to effectively verify the integrity of cloud data without retrieving all of the data from the cloud server. However, using these current methods, the general public may check the integrity of shared data. This technique for protecting privacy allows for a batch audit of cloud-stored common data. Using group signatures to ensure shared data correctness while calculating metadata. The identity of private information is unknown to public verifiers. Public verifiers in each shared data block preserve the identity of the signer using this privacy method. This protects the sensitive user data very well. Cloud storage audits may be loaded using this technique with ease, and it is also very cost-efficient and effective in its auditing.
Cloud computing is part of every Internet user without being aware of it. When a query is typed in Google, the query hops several connected computer servers, before fetching the information into the browser; all these servers are connected seamlessly without being exposed to the user. With public data, security is not a big concern. If the data happened to be private and is sensitive in nature, belonging to an individual or a corporate, inappropriate usage or accessed by miscreants, the data is at risk. The cloud provider stores information by different organizations and there are several protocols and standards available to secure the data. But technology is always vulnerable and therefore, data security in crucial in cloud data servers and in cloud computing.
Using pooled resources, software, statistics, computer systems and other devices may access them as an application via a network, known as cloud computing. In order to achieve coherence and economies of scale in cloud computing, it is necessary to share resources throughout the network. The core of cloud computing is the concept of an interconnected infrastructure and shared services.
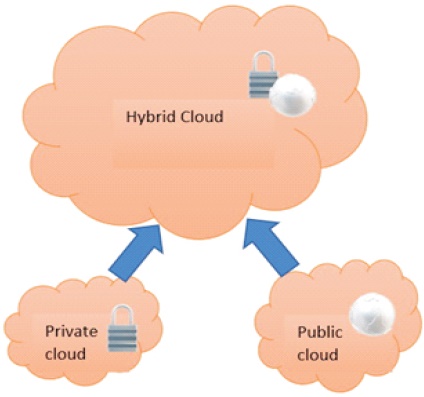
The different deployment models are shown in Figure 1. Public, private, and hybrid clouds are the three types of cloud deployment. Numerous companies use multiple methods and create a multi-cloud environment.

Figure 1. Illustrates the Cloud Deployment Model
Private Cloud: In a private cloud, services are stored on a private network protected by a firewall. One may build a private cloud inside their own data center. Private clouds provide the highest degree of security and control.
Public Cloud: A public cloud provides services to customers via a network that the clients may access. Public clouds are efficient and cost-effective, and they are often multi-tenant, which means the service is hosted in a shared environment.
A hybrid cloud is a cloud computing environment that combines public and private clouds, as well as onpremise equipment. Hybrid cloud allows the user to keep sensitive data on-premises or in a private cloud while using public cloud services.
The three different types of service provision are shown in Figure 2.
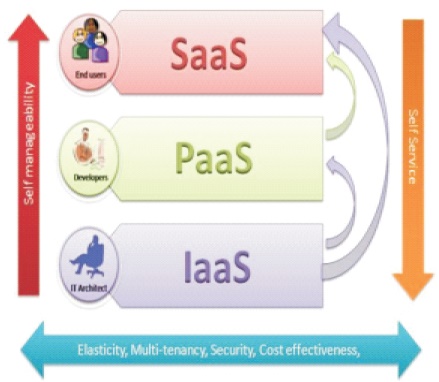
Figure 2. Types of Cloud Services (Jain & Chouhan, 2021)
Software is housed on a distant server, and clients may access it via any web browser or conventional web interface at any time, from any location. Backups, maintenance, and upgrades are handled by the SaaS provider.
PaaS offers utilities and enhancement environment needed for the client to develop and distribute software. Developers might also additionally make use of PaaS to choose the capabilities and cloud offerings they need on a subscription or pay-per-use basis.
Allows businesses to "rent" computer resources including servers, networks, storage, and operating systems on a pay-per-use basis. Customers do not need to invest in infrastructure (hardware, software, etc.) as they tend to get updated sooner with upgrade in technology.
It is a collection of control-based technologies and policies designed to adhere to regulatory compliances and standards while also protecting data applications and cloud technology infrastructure. Since the nature of the cloud is to share resources, cloud security places a premium on identity management, privacy, and access control. As a result, data saved in the cloud should be encrypted. With the increased use of cloud technology for data operations, adequate security and other potentially susceptible areas became a priority for companies contracting with cloud providers. Cloud computing security is the processing of security controls in the cloud and the provision of client data protection and confidentiality.
Security needs of Cloud Computing in numerous domains are (Okuhara et al., 2010):
Domain 1: Cloud computing architectural framework
Domain 2: Governance and enterprise risk management
Domain 3: Legal and electronic discovery
Domain 4: Compliance and audit
Domain5: Information life cycle management
Domain 6: Portability and interoperability
Domain 7: Traditional security, business continuity, and disaster recovery
Domain 8: Datacenter operations
Domain 9: Incident response, notification, and remediation
Domain 10: Application security
Domain 11: Encryption and key management
Domain 12: Identity and access management
Domain 13: Virtualization
Public Auditing: Verify the integrity of data without retrieving the entire data.
Correctness: A public verifier can verify the shared data integrity.
Unforgeability: Only a user in a group can generate shared data.
Identity Privacy: The public verifier does not know who is the signer on each block during the auditing process.
Public auditing system for cloud-based shared information that protects users' privacy. The general public voucher will use to validate the integrity of shared data while not having to urge the complete dataset. Meanwhile, whereas auditing, the identity of the signer on every block of shared data is unbroken hidden from the public verifier. Public auditing mechanisms are extended to verify shared data integrity(Wang et al., 2010, 2013, 2014).
A public verifier may be required to certify the accuracy of many auditing jobs in a short period. It would be inefficient to check these many auditing duties indepe (Wang et al., 2014).
We provide batch auditing using the characteristics of bilinear maps, which can enhance the efficiency of verification on numerous auditing jobs (Wang et al., 2014).
To ensure the integrity of outsourced data, use a thirdparty auditor (TPA). To implement an effective third-party auditor safely, the auditing procedure should introduce no new risks to user data privacy and no more online burden to the user (Ramesh & Revathy, 2017; Wang et al., 2010).
The auditing of cloud storage is outsourced to a thirdparty auditor (TPA) to examine the integrity of the data without accessing the entire file content, therefore protecting the confidentiality of sensitive data at the TPA's end. Furthermore, the user's identity is not given to TPA, maintaining the user's identity (Waykole et al., 2011).
Using the concept of proxy re-signatures, if a user is removed from a group for security concerns, the block of data signed by the revoked user should be re-signed by an existing user. During user revocation, current users are not required to download the revoked user's data blocks. During user revocation, the signatures for all data blocks are recalculated. Furthermore, a public verifier, i.e., TPA, is selected to check the data integrity without obtaining the whole data set from the cloud. The method also allows batch auditing by validating several data blocks at the same time (Wang et al., 2013).
Use homomorphic linear authenticator and random masking in the public privacy audit system for the security of data storage in cloud computing to ensure that the third-party auditor does not learn any knowledge of the content of the data stored on the cloud server during the efficient audit process, which not only relieves the cloud user of the tedious and potentially expensive auditing task. While a third-party auditor can manage numerous audit sessions from various users for their outsourced data files at the same time, this may be expanded to a multiuser configuration in which the third-party auditor can execute multiple audit jobs in batch mode for increased efficiency. Further research reveals that our programs are both safe and effective. A unique privacy-preserving public auditing technique is presented to address the issue of shared data privacy. Use group ring signatures to build homomorphic authenticators, which allow a public verifier to validate the integrity of shared data without having to get the full data while keeping the identity of the signer on each block of shared data hidden from the public verifier.
This public confidentiality control mechanism uses group ring signatures. Ring signatures are used to construct homomorphic authenticators in this scheme, using this public verifier it is possible to verify the integrity/correctness of shared data without completely recovering the original data. In this diagram, the identity of the signer on each block of shared data is kept private/secret by the public verifier. Additionally, this schema needs to be extended to support batch verification. Batch auditing can perform multiple audit tasks at the same time instead of performing a single task. More audit activities are used to improve the effectiveness of audit methods. Meanwhile, this pattern is well associated with the random masking technique. This method has been used by Wang et al. (2010) and can preserve the confidentiality of data from public auditors. Additionally, this schema also affects the index hash tables from a previous public auditing solution to support dynamic data. The proposed design of a novel Homomorphic Authenticable Ring Signature (HARS) scheme.
HARS is extended by a classic ring signature scheme. HARS-generated group ring signatures preserve identity confidentiality and are also able to support less check ability of locks.
The group ring signature scheme is used to protect privacy. This signature is generated using one of the private keys of the members of the group, but the verifier does not know which one. The user can also encrypt the data before sending it to the cloud server using encryption techniques such as symmetric key encryption and attribute-based encryption. Static and dynamic groups are the two types of groups. Membership of a static group is not changed during data sharing because the group is set by default before the shared data is produced in the cloud. In a dynamic group, you can add new users to the group or revoke group access for an existing user.
From a traditional ring signature method, a novel homomorphic authenticable ring signature (HARS) scheme is developed. HARS-generated ring signatures are capable of both preserving identity secrecy and supporting block less verifiability.
Homomorphic group ring signature contains five algorithms:
The users generate their public/private key pairs.
Many privacy-enhancing cryptographic measures used in cloud services employ group signing techniques. Chaum and van Heyst (1991) introduced group signatures in 1991. Their primary function is to allow members of a group to sign communications on behalf of the group. A group member can sign a communication using the secret key gsk(i) which is generally provided by the group manager. A verifier uses a group gpk public key to verify the signature's authenticity. The verifier can verify that the signer is indeed a member of the group while the identity of the signer is not disclosed. The identities of members are only traceable under certain circumstances, eg. Break the rules.
The cluster manager or a revocation manager with the group manager's secret key gmsk will do the revocation.
Proof gen is managed by the TPA and the cloud server together to generate proof of ownership of the shared data.
The TPA verifies the proof associated sends an audit report back to the user. The group is predefined before the creation of the shared data within the cloud and also the group membership isn't modified throughout the information sharing. Before the first user externalizes the shared data to the cloud, he decides on all the group members and calculates all the initial ring signatures of all the blocks in the shared data along with his non-public key and every one key members of the group. when the shared data is held on in the cloud, when a bunch member modifies a block in the shared data, that cluster member should additionally calculate a brand new ring signature on the changed block.
The authorized user can do dynamic data operation on the file which has been stored by the data owner (Wang et al., 2013). If the user wants to modify the data block the user must know the signature to retrieve the data from the cloud. The user can modify the data by three different types of operations they are,
The user inserts a new block m'j into the shared data. The new identifier for the inserted block m'j is calculated and then uploads it to the cloud server. For the rest of the block, the identifiers of these blocks are not changed. The total number of the block in the shared data increases to n+1. The insertion of a new data block is illustrated in Figure 3.
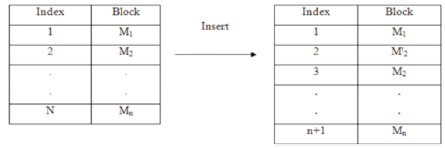
Figure 3. Inserting a New Data Block
Figure 4 simply suggests how the statistics are deleted from the vintage block of statistics. The person deletes block mj, its identifier idj is removed from the cloud server. The identifier and content material of different blocks in shared statistics are last the same. The overall range of blocks with inside the shared statistics decreases to n-1. For deletion operation, the person need not compute a brand new identifier.
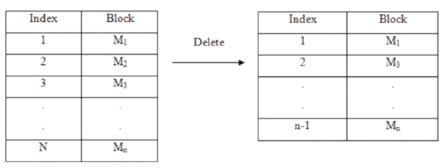
Figure 4. Deleting a Data Block
The user updates the j block in the shared data with the new block m'j. The new identifier of this block is updated and the identifier of the other shared data is not updated. The total number of blocks in shared data-id still would be n. From Figure 5 we understand the update operation after update operation the data block remains the same.
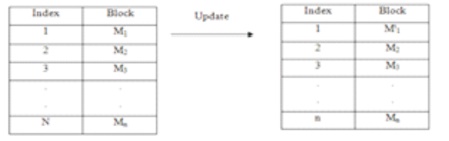
Figure 5. Updating a Data Block
The cloud server is responsible for storing data on the cloud. Any user may access data on the cloud remotely. The database in the cloud server comprises all of the information about shared data as well as information about the complete user group that has access to the data. The cloud server creates a Group ring signature for each group user and delivers it to them.
The public verifier is used to verify the data integrity (i.e., the accuracy of the data saved in the cloud). The identity of the signer on each block of the shared data is kept hidden from the public verifier using a ring signature. The public verifier sends an auditing challenge and response protocol to the cloud server to verify the integrity of the data in the cloud. If the data is successfully stored in the cloud, the cloud server provides auditing proof to the public verifier. The public verifier understands if the data in the cloud is valid or not by utilizing the auditing evidence.
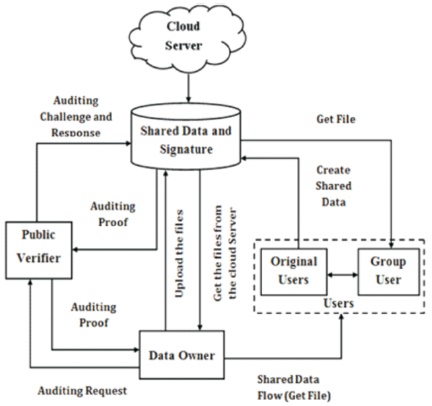
Figure 6. Architectural Design
The data owner logs on the cloud server for uploading the data, associated with checking the integrity of the data that are uploaded within the cloud server. To verify the integrity, the data owner sends an audit request to a public voucher, which publicly verifies the integrity of the data and sends an audit confirmation to the data owner. The data owner can also retrieve the file from the cloud server. The data owner can also be a member in the cloud user group. The data owner can share data with users and find who had downloaded files from the cloud server.
There are two kinds of users: group users and original users. The group user might be either a data owner or a registered user. The original user may be a cloud user. Users in the group can also employ encryption techniques such as the combination of symmetric key encryption and attribute key encryption to encrypt data before sending it to the cloud server. The cloud server may store the data of cloud users, cloud owners, and so on.
Each user in the group can quickly alter the data in the cloud; however, to do so, the user must be aware of the signature. It also provides support for dynamic operations on shared data. Insert, remove, or update actions on a single block are examples of dynamic operations. The user can also download the whole file from the cloud server if necessary.
Any user who wants to access or change data in the cloud must be aware of their specific ring signature for the group. Only after having the ring signature should the user sign the data block on which the dynamic operation is to be performed.
There are four modules for preserving the identity of the user from third-party service providers with public auditing they are
To upload files to the cloud server, the data owner must be a registered user. For that, they need to fill in the details in the registration form. These details are maintained in a database.
In data owner login, any of the registered members can login by giving their user name and password to upload the data. Figure 7 shows the access page of the data owner. Figure 8 illustrates the uploading of the data owner and choosing a public auditor to check the integrity of the data. If the data uploaded by the data owner is modified by any user, the public verifier sends an audit report to the data owner.

Figure 7. Data Owner Access Page
Figure 8. Upload Files to the Cloud Server
If a user wants to access the data which is stored in a cloud, they should register his their details first. These details are maintained in a database.
If the user is an authorized user, they can download the file which has been stored by the data owner. The user can modify the data by three different types of operations.
The user can generate their own private and public key and send both the key to the cloud server to generate a group signature for the particular group. The user signs the data block only by using the group signature. Figure 9 shows the Key Generation.
Figure 9. Key Generation
The third-party auditor (maintainer of clouds) wants to do some cloud offer; they should register first, to do auditing on the cloud data. Figure 10 shows the options of the Public verifier.

Figure 10. Public Verifier Home
Once logged in, a third-party auditor can see how many data owners have uploaded their files to the cloud and to which users the audit request was sent. The TPA batch audit the data in the cloud and verify as shown in Figure 11.
Figure 11. Signature Verification by TPA
The ability of our mechanism to maintain anonymity depends on the size of the group. There is a 1-1/d (where d is the size of the group) chance that a public verifier may miss the signer's identity, if given a block of shared data. Our system performs better in terms of privacy as the number of group members increases. As shown in Figure 12, the privacy performance improves as the group size grows.
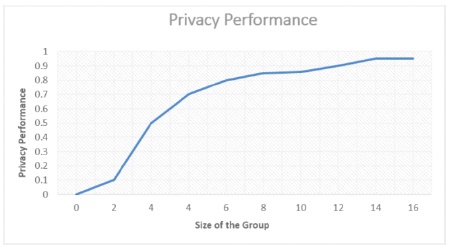
Figure 12. Overall Performance
We use group ring signatures to create homomorphic authenticators so that a public verifier can verify the integrity of shared data without recovering all the data. This scheme cannot differentiate the signer on each block. To improve the efficiency of auditing multiple audit activities, ie., this scheme has been extended to support batch auditing.
The security issue within the cloud is a major concern, so we have proposed a new device that can process the request in group or module mode, which will improve the overall performance and efficiency of the data / device transfer. The set of rules honestly indicates upgrades over its predecessor in numerous methods including safety, information transfer, scalability, and different perspectives.
A public management for privacy protection with a data update verification mechanism for data sharing within the cloud. Checking for the update ought to be very economical for existing filing system operations and supply the lowest latency. To be sure of the update, it is necessary to confirm not only the information blocks, but also their versions.
A version counter is connected with each block, and it is incremented each time the block is updated. This version number is linked to the message authentication code (MAC) of the file block, and the counters themselves must be verified to prevent cloud replay of obsolete file blocks (rollback attacks).
We will continue to research these topics for our future work. The possibility for the group manager (i.e., the original user) to expose the identity of the signer based on the verification metadata in certain specific scenarios is one of them. Traceability is not supported by our design.