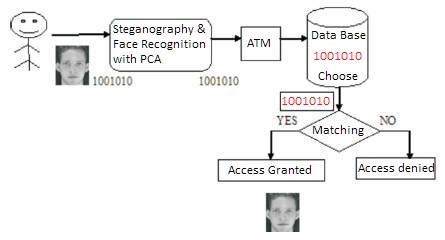
Figure 1. Block diagram of Proposed Framework
Automated Teller Machine allows the banks customers to carry out banking transactions like, deposits, transfers, balance enquiries, and withdrawal. Criminal activities at ATM's have become a nationwide issue. In order to certify safe and secure transactions banks has to meet certain standards. This paper focuses on preventing such activities and enhancing the level of security at ATMs. Biometric authentication technique is proven to address the problems of traditional methods which are presently used in ATMs. Face recognition has received substantial attention from researchers in biometrics. In this approach, a face recognition system for personal identification and verification can be done using Principal Component Analysis (PCA). To enhance the level of security user's biometric data itself hidden with steganography measures. Spatial based LSB Steganography methods is used for hiding biometric data into another covered image and then receiver can detect the secret message.
Today's global market automated teller machine, ATM cards, credit card etc are the financial services embedded in the accounts and records of a banking institution. The deployment of ATM becomes more and produces the imperative result. On this note the crime at ATM's has become a nationwide issue that faces both customers and bank operators [1]. Some of the popular ATM frauds are listed below:
The Biometric authentication system has proven to be a practical alternative to address the attacks in conventional methods used in present banking systems. A biometric system is essentially a pattern recognition system that operates by acquiring biometric data from an individual, extracting a feature set from the acquired data, and comparing this feature set against the template set in the database. Biometric system can operate in verification mode or in identification mode depending upon the application. Biometric systems make use of fingerprints, hand geometry, iris, retina, face, hand vein, facial thermograms, signature, voiceprint, gait, palm print, etc. With the wide spread utilization of biometric identification systems, establishing the authenticity of biometric data itself has emerged as an important research issue. Basically biometric data is not secret and it is transparent may affect with several types of attacks.
Some of the attacks are listed below:
With wide spread utilization of biometric techniques in various applications, an increased security of the biometric data is necessary. Encryption, watermarking, and steganography are possible techniques to achieve this. Steganography is the branch of information hiding. In image steganography [2], the information is hidden exclusively in an image which is called the cover image. After embedding the secret message, the cover image is called the stego-image. At the end of receiver side stegoimage extraction provide meaningful information. In general, image hiding can be done with two approaches: Spatial domain techniques and Frequency domain techniques. The primary focus of this paper is to developing a Spatial domain Stego based Face recognition system to enhance the security features of the ATM for effective banking transaction. The rest of the paper arranged thus: section 1 examines related work section 2 presents Proposed framework for ATM Security section 3 presents Implementation section 5 provides Experimental results, and finally conclusion section is given.
An interesting application of steganography and cryptography developed by M.S.Sutaone, M.V. Khandare where a steganography system is designed for encoding and decoding a secret file embedded into an image file using random LSB insertion method. G. Sahoo and R. K. Tiwari in 2008 proposed a good method [3]. In their method works on more than one image using the concept of file hybridization. Han Shuihua and Yang Shuangyuan proposed scheme is especially useful for encryption of large amounts of data, such as digital images. A new idea is presented by Chander Kant, Ranjender Nath & Sheetal Chaudhary [4] to make system more secure by the usage of steganography, where the secret key will be merged in the picture itself in encoding method and at decoding method the authenticated user will be allowed to decode it. Mohit Soni, Sandesh Gupta, M.S. Rao, Phalguni Gupta [5] applied Euclidean Distance based matching technique for making the decision for feature extraction. Maleika, Naushad and Raja [6] applied Principle Component Analysis (PCA), with Cholesky decomposition and Lanczos algorithm to extract the vein features which decreases the number of computation and the processing time. Prof. S.Sivasubramanian, S. Pandiarajan [7] presented the method in which the secret message encrypts with the receiver's public key along with the stego key and embeds both messages in a carrier using an embedding algorithm. Fridrich and Goljan [8] have surveyed more number of techniques for detecting LSB substitution. Among those one of the popular methods is histogram analysis [9].In that method an image is processed with LSB substitution and then the histogram of the image will be showed. To improve LSB substitution a similar idea called LSB matching [10] has been proposed. Later in 2006 a revised version of LSB matching is proposed by Mielikainen [11] by performing expected number of modifications per pixel, from 0.5 to 0.375. A novel approach of image embedding was introduced in [12]. The method consists of three main steps. First, the edge of the image is detected using Sobel mask filters. Second, the least significant bit LSB of each pixel is used. Finally, a gray level connectivity is applied using a fuzzy approach. Later Sun et al. [13] proposed a data hiding scheme based on arranging the position of pixels and then retains the host image histogram profile perfectly. Wu and Tsai [14] utilized the difference between the two consecutive pixels in the cover image to determine what size the secret message is to be hidden. An Adaptive data hiding method was proposed in [15].In this method Pixels located in the edge areas are embedded by a Kbit LSB substitution method with a larger value of than those of the pixels located in smooth areas.
In this paper a new frame work is introduced to enhance level of security to the ATM customers with spatial domain LSB Substitution and Principal Component Analysis. Initially the face image is hidden and then it can be recognized. Once the face is verified then the customer is ready to access the system. The architecture of the framework can be shown in Figure 1. The approach can be expressed with following steps:
Face images are collected from ORL Database provided by the AT&T Laboratories from Cambridge University. It contains images with different subjects like slight variations in illumination, facial expression and facial details with glasses/no glasses. Database is worth of 400 images, corresponding to 40 subjects (namely, 10 images for each class). Each image has the size of 112 x 92 pixels with 256 gray levels. Some face images are trained and tested from the ORL database are shown in Figure 2.

Figure 1. Block diagram of Proposed Framework

Figure 2. Training & test Sets from ORL Data base
In today's global market have seen an increased interest on the usage of the digital multimedia on the web. At presents the commercial software's are using carrier contents of steganography such as images, audio, and video files. A popular digital steganography technique is least Significant Bit (LSB) method. The method can perform operation in two phases: Embedding Phase and Extracting Phase. In LSB embedding phase two parties in share a private secret key in communication and also it can allows high perceptual transparency [17]. The bits of secret message directly embedded into the LSB plane of the cover image. The embedding procedure does not affect the original pixel value greatly [16]. At receiver's side LSB extracting phase take place for retrieving original image from the stego image. The overall idea of hiding biometric data is shown in Figure 3.
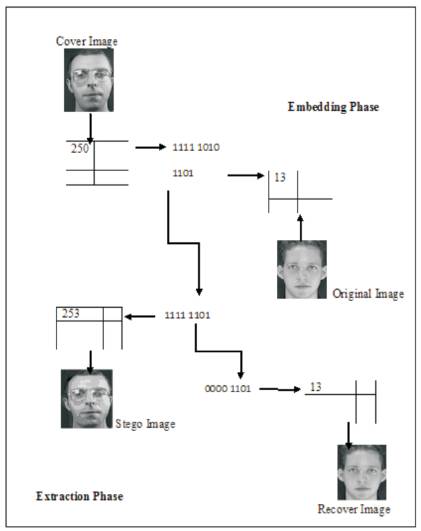
Figure 3. Hiding face data using LSB steganography
Mathematically the embedding message is represented as:
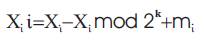
In equation (1) Xi I is the pixel value of the stego-image and Xi represents that of the cover- image. Where mi represents the decimal value of the ith block in the confidential data. k is the number of LSBs to be substituted [17] .The extraction process is to copy the k-rightmost bits directly.
The mathematically the extracted message is represented as:
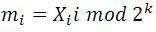
In equation (2) mi represents the original confidential data and Xi I is the pixel value of the stego-image.
Principal Component Analysis (PCA) is a standard technique used in statistical pattern recognition and signal processing for data reduction and Feature extraction. PCA is one of the most successful techniques for face recognition. This method allows to represents high dimension data of images into lower dimensions for reducing the complexity of grouping images. It treats the face images as 2-D data, and classifies the face images by projecting them to the eigenface space which is composed of eigenvectors obtained by the variance of the face images. One can choose to go into depth of one and only one of those methods. The idea of PCA method shown in Figure 4.
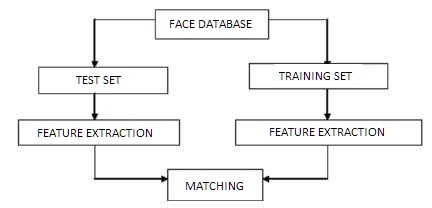
Figure 4. Block Diagram for PCA
Step 1: Select a face database that consists of the face images of known persons.
Step 2: Build the training set that consists of a number of images (M) for each person with and different expressions.
Step 3: Calculate the M x M matrix L, find its Eigen vectors and Eigen values, and choose the M' Eigen vectors with the highest associated Eigen values.
Step 4: Combine the normalized training set of images to produce M' Eigen faces.
Step 5: Store these Eigen faces for later use.
Step 6: For each member in the face database, compute and store a feature vector.
Step 7: Choose a threshold value e that defines the maximum allowable distance from any face class. Optionally choose a threshold f that defines the maximum allowable distance from Face space.
Step 8: For each new face image to be identified, calculate its feature vector and compare it with the stored feature vectors of the face library members.
Step 9: If the comparison satisfies the threshold for at least one member, then classify this face image as "known", otherwise a miss has occurred and classify it as "unknown" and add this member to the face library with its feature vector.
Face images are verified on the basis of distance measures between two points. In this paper closest distance is referred with the Euclidean distance. Euclidean distance is the most common use of distance. This classifier calculates the minimum distance between the test image and image to be recognized from the database. If the distance is small, the images are similar and decided to access the system. We obtain the Euclidean distance, D as follows and shown in equation (3):
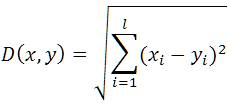
Where x, y in the data set X and xi, yi are the ith coordinates of x and y, respectively. This is a dissimilarity measure on X. The minimum possible distance between two vectors of X is 0 .
In this experiment, security level of enhancement to the ATM Customer can be done with stego based face recognition with different kinds of poses (views), expressions and varying lighting conditions. In this paper prior to matching the face images are hidden with LSB Substitution. After that face image is retrieved from the stego image and then it is matched with the training set with PCA and the resultant matching score is plotted for each test samples which is shown in Figure 5(a-c). The resultant matching score of different test images shown in Table 1 and the robustness of proposed framework in terms of matching score is shown in Figure 6 .
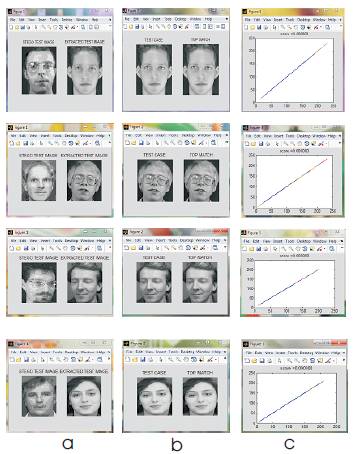
Figure 5. (a) stego image & extracted image (b) test case with top match (c) matching score
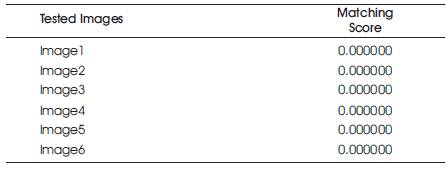
Table 1. Matching Scores of tested image with Euclidian distance the classifier
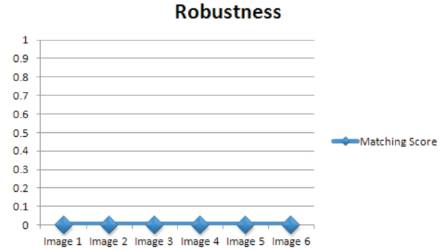
Figure 6. Propose Frame work performance with matching score
To enhance security level to the ATM Customer Stego based Face recognition strategies with the PCA (Principal Component Analysis) were implemented. Principal Component Analysis gave better results for different subjects and it is proven technology for deploying into ATM System. The results are good for the test samples that we have considered. Further, we can improve the system for providing security to other applications like border and security control checkpoints, crime investigation, entrance control in buildings, access control for computers, passport verification etc. Further, we can improve the system by introducing multimodal biometrics with combination of one or more biometrics like finger print, iris, palm, face and retina.
The authors acknowledge the support of the Department of Science and Technology (DST), New Delhi to do this work. They furthermore thanks to Dr.L.Siva Sankar Reddy (Director of Lakkireddy Bali Reddy College of Engineering), Staff and Students of Lakireddy BaliReddy College of Engineering who provided helpful comments and discussions .