Figure 1. Proposed Architecture for Image with Data Transmission
The usage of internet is in all aspects like Railway Reservations, Air Ticketing etc. Drastically, there is a lack of security in real time operations. Hackers crack the passwords usually by using few attacks like shoulder surfing attacks, phishing attacks, online guessing attacks, and brute force attacks. To overcome these attacks there already exists image based passwords like captcha technologies pass points and cued recall in providing solutions up to certain range, but it reduces the efficiency by loading huge images while generating the passwords. To overcome this, the authors proposed a new secure and efficient image with Embedding Sensitive Information Transferring Technique using Blowfish Algorithm for Key Generation.
In this digital era, maximum persons active on the Internet for their personal and professional information storing and sharing with others in the internet world grows like “without internet we can't do any work in our daily life”. Nowadays, the data transferring through the internet has a crucial role to reach the sensitive information with safe and secure transaction. Drastically lacking of security in real time, the data could be theived by intruders in the middle. But along evolution there are some threats to access our information such as:
The existing systems provide security for the above mentioned attacks by mathematical cryptography techniques like RSA, ECC, and Deffie-Hellman. These algorithms depend on integer factorization, and the users can easily break the password. Graphical password technique such as captcha techniques like recognition base, recall bias, and cued recall can be a better option.
Recognition based passwords have been designed pass points to pick images from multiple iterations. Recall based passwords made by the user to draw locations on the image, and then it could be encod the sequence of grid cells along the drawing path as per the drawn passwords. Cued call comes when a user selects the sets of cued points on a single image making password. The present captcha technologies used in the real time applications are,
These technologies are used to make the password tough. Image captcha provide images to select a set of images or sets of cued points to make a password for authentication. Text captcha provides a set of characters and images are shown on the authentication image page to pick the password by clicking on that particular text image. Audio captcha, the password is made by a set of audio files to make authentication. Video captcha, the authentication is made by video files to generate a password.
CaRp can be applied on touchscreen devices where typing passwords is cumbersome, especially for securing Internet applications such as e-banking. Many e-banking systems have applied Captchas during user logins. CaRP increases spammer's operating cost and thus helps to reduce spam emails. For an email service provider that deploys CaRP, a spam bot cannot log into an email account even if it knows the password. Instead human involvement is compulsory to access an account. If CaRP is combined with a policy to throttle the number of emails sent to new recipients per login session, a spam bot can send only a limited number of emails before asking human assistance for login, leading to reduced outbound spam traffic.
To overcome the online guessing attack, phishing attack, shoulder surfing attack, and brute force attacks, the author have proposed an embedded sensitive information with image by using Embedded Algorithm and making encryption by using a strong symmetric key algorithm, the Blowfish algorithm. This algorithm has high speed key generation and efficient secure encryption has made to transfer sensitive information. Here the key generated by the Blowfish algorithm is robust and secure compared to other symmetric key algorithms like DES, AES, and 3DES. The data can be sent in a two way authentication like our sensitive data can be embedded in an image, then after that the image will be sent to the destination through a well encryption technique to protect from intruders.
Bin B. Zhu, et al., [1], proposed a new security primitive based on hard AI problems, which we call Captcha as graphical passwords (CaRP). CaRP is both a Captcha and a graphical password scheme. It also offers a novel approach to address the well-known image hotspot problem, but it offers reasonable security and usability and appears to fit well with some practical applications for improving online security.
G. Sudheer Reddy, et al., [2], proposed a new Password Guessing Resistant Protocol (PGRP), derived upon revisiting prior proposals designed to restrict such attacks. It analyzes the performance of PGRP with two real-world data sets and finds it more promising than the existing proposals.
Brijesh Kumar Singh, et al., [3], proposed a block-based transformation algorithm based on the combination of image transformation and a well known encryption and decryption algorithm called Blowfish. The results showed that the correlation between image elements was significantly decreased by using the proposed technique.
Vinay Sahu, and Kamlesh Lahore [4], proposed a method of embedding the original image with patient information before encryption by using the lossless watermarking method. When the message is arrived on the receiver side, the inverse methods are applied in reverse order to get the lossless original image and patient information compared to other methods. They have applied and showed the results of their method to medical images.
Prerna Parmar, and Neeru Jindal [5], proposed an algorithm for image security comprising watermarking in spatial domain along with encryption. The secret image is finally decoded at the receiving end. Robustness is also checked by extracting the secret image perfectly without any degradation in the quality of the original image.
Gurmeet Kaur and Aarti Kochhar [6], proposed a comparative analysis to demonstrate the effectiveness of the proposed methods which has been estimated by computing Mean Square Error (MSE), Peak Signal to Noise Ratio (PSNR), Processing time, and security. The analysis shows that the BER and PSNR is improved on the LSB Method, but security sake DCT is the best method.
Israa Tahseen and Shatha Habeeb [7], The steps are: proposed a new approach to generate a random number using image. Read the picture by pixel, select the specific location randomly by picking any two colors, apply XOR between two selected colors and then specify the length of the key. This key is used to encrypt or decrypt the plaintext. They apply this key generation method in to Blowfish algorithm. Finally, they suggest that this type of key generation is suitable for short keys in symmetric system.
Ratinder Kaur and V.K. Banga [8], proposed a security of image using the Blowfish algorithm. They divide the original image into a random number of blocks and then the blocks are transformed into new locations. For better transformation, divide the blocks into a smaller number of blocks because fewer pixels keep their neighbours and is difficult to predict neighbours pixels. After that transformation, encrypt the block of images using Blowfish algorithm. Finally they analysed that the combination of transformation and encryption provides better security for the image.
B. Geethavani, E.V. Prasad and R. Roopa [9], proposed a new approach for securing the data, and transferring the audio signals using discrete wavelet transform. They derived a new hybrid technique from the combination of cryptography and stegnography for transmitting the message in a highly secured manner. The plaintext is encrypted using Blowfish algorithm and the resulted cipher text is embedded into an audio file using discrete wavelet transform. Finally, they suggested that this method is an efficient method for hiding text in audio files such that the data can reach the destination in a safe manner without any modification.
Monika Agrawal and Pradeep Mishra [10], proposed the enhanced security level of Blowfish algorithm and decreases the time for encryption and decryption. They generate the random number within the range 0 to 65535. Set the flag value to zero. Convert random number into 16 bit binary form and find the positions that are holding 0 entries, and then set the flag value to one, otherwise the flag is zero. If the flag is 1 then the F-function will not work, and if the flag is 0 then the F-function will work. They analysed that the encryption time and decryption time is reduced compared to the original Blowfish algorithm.
The detailed process of the proposed system design is shown in Figure 1. Firstly, we have to load an image file as a captcha a password to perform authentication and to avoid guessing attacks for securing sensitive information. After loading the image file, perform embedding technique using one of the specified algorithms, LSB (Least Significant Bit). It defines to replace the least significant bit with alternative bit like 0 as in the place of 1 and 1 as in the place of 0. It generates a visible embedded watermark image with secret information. In this phase, we can apply a highly efficient symmetric key encryption algorithm to generate cipher file. The received cipher file is decrypted by using a secret key and alternate reverse embedded processes are performed that includes swapping technique to get clear secure information without loss of data.
Step 1: Read the original image.
Step 2: Read text message which is to be hidden in the original image.
Step 3: Convert color image into gray image.
Step 4: Convert message into binary format.
Step 5: Calculate LSB of every pixel of the original image.
Step 6: Replace LSB of the original image with each bit of secret message one by one.
Step 7: Generate watermarked image with a secret message.
The most secure and simplest method used for watermarking in this project is the LSB (Least Significant Bit) algorithm for the embedded sensitive information on image by embedding the least significant bits. The sensitive information can hide without accessing the intruder by applying embedded least significant bits of the message. In this LSB algorithm replacement flips the last bit of each data value to reflect the message that needs to be hidden. The sensitive information passed from source to destination by embedding that sensitive information in a user specified location on the image has to be selected by the sender on an image without any message loss. To convert the sensitive message into binary format like 0 and 1's, after the conversion is applied to flip or replace the least significant bit by an alternative bit like in place of 0 is 1 and vice versa. This way finally the sensitive information is hidden on the image.
Step 1: Take the watermarked image generated in the embedded algorithm process.
Step 2: Divide the image into blocks containing 64-bits in each block.
Step 3: For each block,
Divide the block into two 32-bit halves XL, Cr.
For i = 1 to 16:
xL = xL XOR Pi
xR = F(xL) XOR xR
Swap xL and xR
Next I
Swap xL and xR (Undo the last swap
xR = xR XOR P17
xL = xL XOR P18
Recombine xL and xR to get the cipher block
Step 4: Repeat step 3 for each block and finally we get the encrypted image.
Blowfish is a variable-length key, 64-bit block cipher. The algorithm consists of two parts a key-expansion part and a data-encryption part. Key expansion converts a variable-length key of at most 56 bytes (448 bits) into several sub key arrays totaling 4168 bytes. Data encryption occurs via a 16-round Feistel network. Each round consists of a key-dependent permutation, and a key- and data-dependent substitution. The additional operations are four indexed array data lookups per round. Implementation of Blowfish requires the fastest speeds to unroll the loop and to ensure that all sub keys are stored in cache.
Blowfish is a variable-length, a new secret-key block cipher. It is a Fiestel network, iterating a simple encryption function 16 times. Its main features are Block cipher 64-bit block, Variable key length is 32 bits to 488 bits. It is much faster than IDEA and DES. It is unpatented and royalty free and requires no license. Blowfish uses a large number of sub keys. These keys must be pre computed before any data encryption or decryption.
1. The P-array consists of 18 32-bit sub keys:
2. P1, P2,..., P18.
3. There are four 32-bit S-boxes with 256 entries each:
S1,0, S1,1,..., S1,255;
S2,0, S2,1,..,, S2,255;
S3,0, S3,1,..., S3,255;
S4,0, S4,1,..,, S4,255.
Decryption is exactly the same as encryption, except that P1, P2,..., P18 are used in the reverse order. Sequence of operations to be performed for security & secured data with embedded image transmission are listed below.
The authors gave an image as input, and processed that an image in 2x2 pixel blocks. This allows flexibility in tracking the edges and also achieves high computational complexity. The two processing cases that flipping the candidates of one does not affect the flippability conditions of another are employed for orthogonal embedding.
Watermarking is a technology for embedding various types of information in digital content. In general, information for protecting copyrights and proving the validity of data is embedded as a watermark. Watermarked content can prove its origin, thereby protecting the data.
In this module the data embedded image is encrypted. The purpose of the authenticator watermark of a block is invariant in the watermark embedding process, hence the watermark can be extracted without referring to the original image. The encryption and decryption techniques are used in this module.
An edge pixel in binary images is flipped, which is equivalent to shifting the edge location horizontally one pixel and vertically one pixel. A horizontal edge exists if there is a transition between two vertical neighboring pixels and a vertical edge exists if there is a transition between two horizontal neighboring pixels. We swap a morphological image.
The watermarked image is obtained by computing the inverse for the main processing block to reconstruct its candidate pixels. Use this module, the original watermarked image can be obtained.
A comparative analysis of the original Blowfish and Optimized Blowfish is performed to provide some measurements on the encryption and decryption. The following parameters are used as the performance criteria, such as input size (in bytes), Encryption time, Decryption time and throughput.
The comparison is conducted for the text or message only. Encryption time is one of the performance parameter, which is defined as the amount of time required for converting the plain text into cipher text at the time of encryption. Decryption time is also one of the performance parameters, which is defined as the amount of time required for converting the cipher text into plain text at the time of decryption. Table 1 shows the total execution time.
To improve the accuracy of the timing measurement, the program is executed 10 times. The encryption time and decryption time is measured in milliseconds. The sum of encryption time and decryption time is considered as the execution time of the algorithm and it can be calculated by using equation (1)
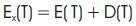
Where, Ex(T) = Execution Time,
E(T) = Encryption Time,
D(T) = Decryption Time.
Figure 2 shows the overall performance of the original and optimized blowfish. From the result, the average execution time of the optimized Blowfish is identified as 7.69 milliseconds and the original Blowfish as 7.96 milliseconds. Figure 3 shows the comparison of the two average execution times, where the optimized Blowfish algorithm is less than an original Blowfish algorithm. An analysis is evaluated for the achievement of decrease in time between the original blowfish and optimized blowfish and to improve the efficiency by loading huge images.
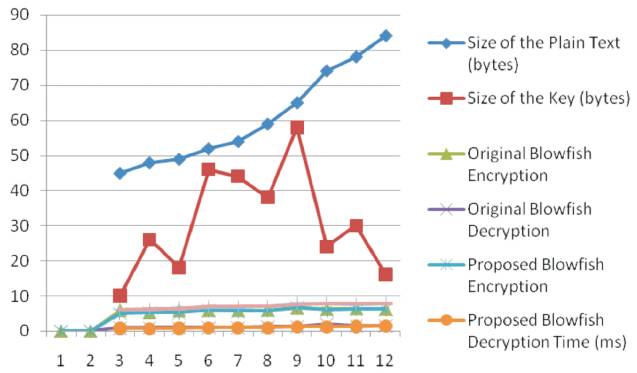
Figure 2. Overall Performance of the Blowfish Algorithm
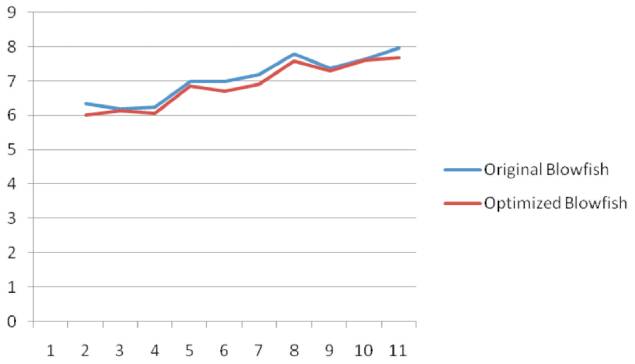
Figure 3. Comparison of Original and Optimized Blowfish Algorithm
In this paper, the proposed work has provided a security for the sensitive information, to transfer these information among authenticated persons by using watermarking techniques like the Least Significant Bit technique and highly efficient symmetric key cryptography technique, the Blowfish algorithm. To transmit secure information from the source to destination by using the best techniques in order to process without any loss of information, embedded algorithm is the one way authentication. After providing a cryptographic technique to that watermarked image to give the second level of authentication by the use of the Blowfish algorithm gives a more secure password by using 16 rounds of key generation with 18 keys. It improves the security and efficiency during online data transmitting, where no one can access the information because it gives the hurdle to crack the information. It gives the better entropy and low correlation rate to give the throughput information. Future work is in progress for further improvement in the sensitive information transferring technique by using blowfish algorithm.