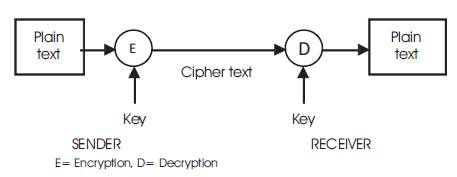
Figure 1. General Figure of Public Key Cryptography System
The objective of this work is to develop Biometric based sender authentication in public key cryptosystems to overcome the man-in-the-middle attack or hacking issues and provide a high level of security. Biometric Technologies are automated methods for verifying or recognizing the identity of a person based on physiological or behavioural characteristics. In public key cryptosystems, authentication is provided either by HASH function, MAC (Message Authentication Code) function or Digital Signature. In this work, the authors have used a Biometric based sender Authentication using Speech Feature in public key Cryptosystem. Here the public key cryptosystem uses Diffie Hellman (DH) algorithm. DH generates a shared secret key between two parties over an insured communication, but DH does not provide Encryption/Decryption and authentication. The man-in-the-middle attack or Hacking is possible in DH, because it does not authenticate the participants. In this work, the authors overcome the authentication and the man-in-middle attack problem by using Biometric based sender authentication. Also the speech encryption and decryption are performed with the message for high security.
With the evolution of information technology, more and more facilities and services are being offered over the electronic devices and the internet. These include daily messaging, e-mailing, banking, transaction, e-shopping and many more. The proper use of these facilities only by the genuine or authorized users and avoiding misuse by the imposter or unauthorized users are made sure. Thus, Security has always been a major concern for authentication over networking. Now-a-days personal identification approaches such as Personal Identification Number (PIN), text passwords, bar codes, identity cards (ID card) are not sufficiently reliable to fulfill the security necessities of communication and transaction by digital devices and the internet. Because they lack the capability to distinguish among a genuine individual and an imposture who fraudulently acquires the entry to get privileged. The opportunity that provides relief from most of these disadvantages is by using biometric features for authentication of a person. Cryptographic methods and biometric authentication solve the problem of security and authentication by implementing various public key cryptosystems method.
Cryptography is the art of science or collection of tools or techniques used to secure or protect the data and information during its transmission over the insecure network. It contains various abstraction levels of security mechanism and it builds the discipline of data encryption and decryption. Network administrator provides an authorized access over the network by implementing network security and adoption of its provisions and policies to prevent the unauthorized access. Authorization has always been an integral part of the security mechanism.
Any physiological and/or behavioral characteristics of human can be used as a biometric feature. Biometric system of identification uses the unique feature of face, Speech, iris, fingerprint, and retina to identify a person with a unique characteristic that differentiates the concerned person from others. The system of using speech as a parameter for authorization provides an enhanced security for data transfer, communication and transaction over the networks.
DH algorithm is a method of generating a shared secret key between two different people in such a way that the secret key can't be intruded through observing the communication over an insecure communication channel. The unique characteristic is that you are not sharing information during the key exchange, you are generating a key together. Figure 1 shows the basic public key cryptography system.

Figure 1. General Figure of Public Key Cryptography System
Figure 2 shows the basic setup of DH key exchange algorithm. In Diffie Hellman algorithm, initially there will be one private key and public key. On combination of these two particular keys, a shared key is generated. In the generation process, two common variables are used. The two common variable used are α and q.
Constraints for the variable α & q:
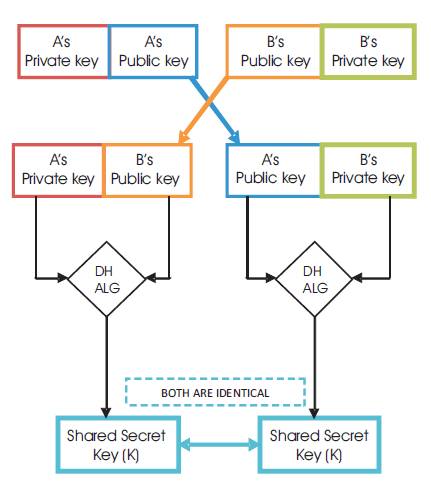
Figure 2. DH Mechanism of Key Exchange
The mechanism of this algorithm is that we use two common variables in a way that one is a prime number and the other is the primitive root of that prime number. Using these two common variables, the private key is selected for both the sender and receiver. In this algorithm, the public key is generated for both sender and receiver using the private key and the two common variables.
In Diffie Hellman algorithm, the shared key is generated by combining the sender's private key and the receiver's public key in the sender side and in the receiver side decrypt the data by using sender's public key and its own private key. The shared key generated by both the parties are same. The key generation and its setup are described in Figures 3 and 4 respectively.
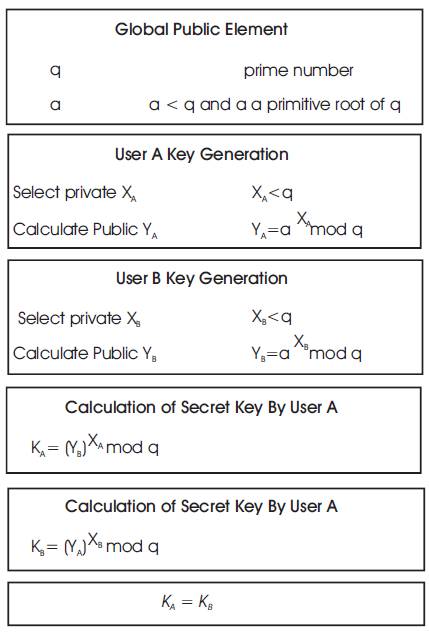
Figure 3. Key Generation
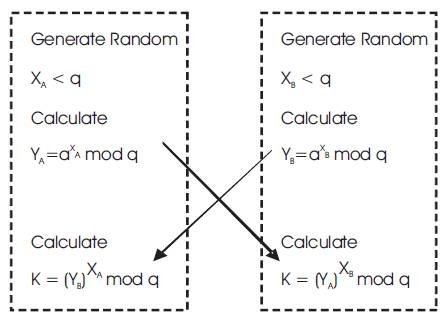
Figure 4. DH Algorithm and Setup
These are the Calculations Performed by the Sender A.
K= (YB)XA mod q
The public key of the receiver is used to generate the shared key by the sender.
= (αXB mod q)XA mod q
Now the value of YB is substituted in the above equation,
= (αXB)XA mod q
= αXBXA mod q
= (αXA)XB mod q
= (αXA mod q)XB mod q
The shared key generated by the sender which is identical
= (YA)XB mod q
The Calculations Performed by the Sender B are given below.
K = (YA)XB mod q
= (αXA mod q)XB mod q
= (αXA)XB mod q
= α XAXB mod q
= (αXB)XA mod q
= (αXB mod q)XA mod q
= (YB)XA mod q
The above calculation performed by the receiver B is similar to that of the sender for the generation of the shared key for encryption.
Some research carried out by professionals in the field indicates that there could be some gaps such as the Man-in-the-middle attack and Hacking over the medium that need to be filled in the area of cryptography, so as to attain a better security of information and data. Random number and other techniques for the authentication can be easily misused or forgotten.
In Diffie Hellman algorithm, Man-in-the-middle attack or hacking are possible [1], [2] because it doesn’t provide encryption, decryption and authentication [3], [4].
Figure 5 shows that the hacker H is trying to find the key to know the data that is being transferred between A and B. But H can get only the two common variables and the public key but not the private key inorder to get the shared key. This is the advantage of the Diffie-Hellman algorithm.
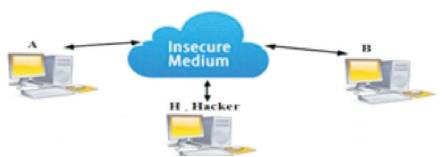
Figure 5. Man-InThe-Middle Attack
Suppose A and B wish to exchange keys and H is the Hacker. The attacker’s process is as follows
At this point, A and B think that they share a secret key but instead B and H share a secret key K1 and A and H share a secret key K2 .
This Man-in-the-Middle attack and non authentication problem has been overcome by this work.
Speech is probably the most efficient way to communicate with each other. This also means that speech could be an useful interface to interact with machines. Thus speech is one of the main features used by humans for person authentication. The other reason for the selection of these biometrics are as follows.
Speech from the same text or arbitrary text can be used for identification of the speakers for which text dependent and text independent modes of operation are available [5]. In this work, the authors uses text dependent speaker identification approach, where exactly the same word is pronounced differently by different people. The sender authentication process shown in Figure 6.
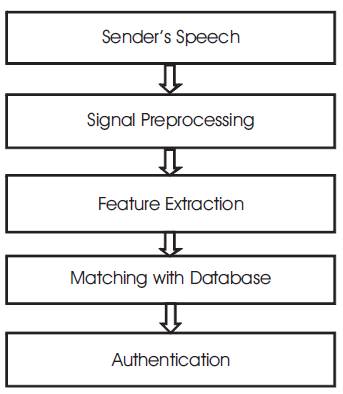
Figure 6. Process of Speech Authentication
The first block i.e. Sender's Speech block which includes the acoustic surroundings plus the transduction device as microphone. It will have a robust impact on the generated speech representations. As an instance, we are able to have an extra effect generated from additive noise or room reverberation.
The second block i.e. Signal Pre-processing block is the filter block. It is very essential to feed the system inputs with relevant records. Signal pre-processing has a large effect on the overall performance of the speech classifier. Recorded samples by no way produce same waveforms; the duration, amplitude, background noise may vary. Noise and difference in amplitude of the signal can distort the integrity of a word while timing variations can cause a large spread amongst samples of the same word [6], [7].
Therefore, we need to carry out signal pre-processing to extract only the speech related information.
The third block i.e. Feature Extraction block should be able to extract speech unique features of the pre-processed signal. The Feature Extraction techniques include,
In this, the authors are using MFCC technique for feature extraction.
A Mel is a unit of measure of perceived frequency or pitch of a tone. Human auditory system does not perceive the spectral components in linear scale, but it will perceive on a nonlinear scale. Thus, we can use the Mel frequency scale i.e., nonlinear scale to extract the spectral information. The relation between the mel frequency and the physical frequency is given by,
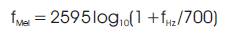
Using the above equation, we construct a spectrum with critical bands which are overlapped triangular banks i.e., we map the linear spaced frequency spectrum (fHz ) into nonlinearly spaced frequency spectrum (fMel ). By this, we can mimic the human auditory system, whose perception of a particular frequency (Ω0 ) is influenced by energy in a critical band of frequencies around Ω0 . Based on this concept, MFCC feature vectors are derived.
The fourth block i.e. Signal Classification/matcher block attempts to categories the extracted features and relates the input sound to the quality fitting sound in a known 'vocabulary set' and represents this as an output. The Matching techniques are,
In this work, the authors have used HMM for classification.
An object of the GMM class defines a Gaussian mixture distribution, which is a multivariate distribution that consists of a mixture of one or more multivariate Gaussian distribution components. The number of components for a given GMM object is fixed. Each multivariate Gaussian component is defined by its mean variance and Mixture weights, and the mixture is defined by a vector of mixing proportions. Figure 7 shows the GMM parameters from the speech signal.
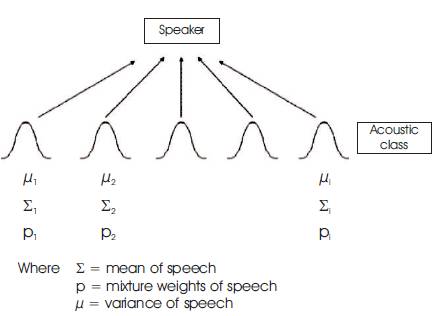
Figure 7. GMM Parameters from the Speech Signal
In almost all biometric authentication systems, a database is required. In the enrollment phase of a biometric authentication system, all users are registered with the system, and references are stored in the database of the system.
In this present work, the speech database contains 15 speech samples of a sentence 'Every Thing Will Be OK' for each of the 20 users. Out of the 15 speech samples, the first 10 speech samples are used for training and the remaining 05 speech samples are used for testing.
Figure 8 shows the message encryption and decryption process.
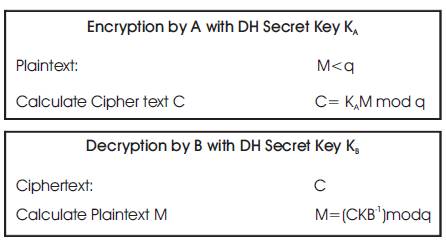
Figure 8. Message Encryption and Decryption Process
For Speech encryption and decryption, the same process is performed as in the case of plain text only keys are changed using KA-1 instead of KA and KB instead of KB-1 .
The speech was hidden within the bubble noise before encryption.
Figure 9 shows the method and experimental setup of this project.
1. The Sender (A) encrypts the plain text/message by using KA key.
2. Then hides the speech within the bubble noise and then performs the encryption by using the KA-1 key.
Encrypted speech Es and message Em are called cipher speech and cipher text respectively.
3. Then the Sender sends an encrypted message Em which is appended with his/her encrypted speech Es.
1. The Receiver (B) performs the decryption only for the encrypted speech sample, B using the K key. Then B removes the bubble noise from decrypted speech.
2. Then matches the sender's speech with speech database.
If sender's speech matches with the speech database, -1 the Receiver, decrypts the encrypted plaintext by using K key B and the original message is displayed, otherwise shows the sender is an invalid or unauthorized sender.
The proposed method has been implemented by the MATLAB software.
By this new approach of Biometric Sender Authentication in cryptography a new direction for authentication and security has been introduced. It overcame the Man-inthe- middle attack or hacking problem and has provide a high security in the Public key cryptosystems or Diffie Hellman algorithm. Thus, as compared to the former one (Figure 1), this experiment (Figure 9) provides a Higher security and Authentication.
Figure 10 and Figure 11 show the results of this work which are performed using the MATLAB software.
The authors have presented an Enhanced Security Mechanism in Diffie Hellman Key Exchange or public key cryptosystems. Using Biometric person Authentication, the Experimental setup and process clearly indicates that the security level has been enhanced by this work. We can add a biometric person authentication technique to any of the public key cryptosystems. As a future work, the authors want to add the face or finger print with speech and message in public key cryptosystem for total security.
The author is grateful to all who have contributed towards shaping in this work. At the outset, He would like to express his sincere thanks to his guide Mr. Vinay Jain for his valuable advice and support. He would like to thank his friends for providing their speech, information in generating the speech database. He also thankful to his Professor Mr. Chandrashekhar Kamargaonkar and Mr. Sharad Mohan Shrivastava for their support and encouragement.