Table 1. Authentication Techniques
Day-to-day usage of internet is increasing for services like online shopping, online banking, email, etc., where authentication is necessary. Among the authentication techniques most the commonly used are username and password. Using the password, an attacker can crack easily using the guessing method. So, to strengthen authentication more than one factor is used. This paper proposes a two factor authentication scheme which uses speech as the first factor and text password as the second factor. During the login, the user utters the speech (passed as the first factor) and later, user is asked to give index value along with a sentence to form a password (passes second factor). If both the factors match only then the user is authenticated and is allowed access. The usability and performance analysis of the proposed TFA (Two Factor Authentication) is carried out using Morae Tool.
To protect the system against unauthorized users, necessary permissions and rights are verified by authentication process for user access. Passwords are the most common form of authentication used to control the access to information ranging from the personal identification numbers. used in automatic teller machines, credit cards, telephone calling cards and voice mail systems to the more complex alphanumeric passwords that protect access to files, computers and network servers. Passwords are widely used because they are simple, inexpensive and convenient mechanisms to use and implement. At the same time, passwords are also recognized as being an extremely poor form of protection [7]. The Computer Emergency Response Team (CERT) estimates that about 80 percent of the security incidents reported to them are related to poorly chosen passwords.
Today's widespread use of single-factor authentication (Password) is in the midst of change. Both corporate and personal assets are at risk. impersonating users are stealing money and information. Single-factor authentication methods such as the basic username/password combination are no longer sufficient enough. Two-factor authentication provides a significant increase in security. Thus no longer will an un-secured password provide enough information to a hacker to allow a breach of security.
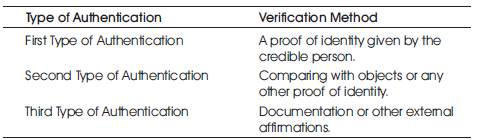
According to the validation or verification method being considered, the authentication techniques are classified into mainly three categories. Table 1 depicts the broad classification.

Table 1. Authentication Techniques
In the first type of authentication, the authentication verification is done by what the user or the particular individual has given at the time of authentication access i.e. textual passwords, PIN.
In the second type of authentication, the validation is done by comparing the image or any other object that has been given at the time of registration.
In the third type of authentication, smart cards and other finger print proof is taken as the validation proof.
Based on these techniques, user authentication can be provided using the factors like the Ownership, Knowledge and Inherence. Table 2 depicts the factors along with their respective identities.
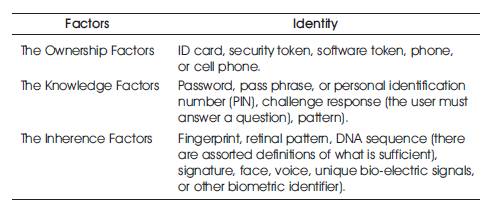
Table 2. Authentication Factors and their Identity
Based on these factors and their identities the authentication can be done in multiple stages
Only one time the validation is provided. The user enters his password, the access is provided for the system or to his account. The security for this type of system is low and the hackers can easily crack the password and access their personal data.
The hacking technologies have become more diversified and advanced [8] [6] [5], there for security offered by single-factor authentication is found to be vulnerable to replay attacks, malware attacks, key logger Trojans, dictionary attacks, offline brute force attacks, etc. In order to increase the security it has now become very common to combine multiple authentication factors. In recent times, there has been an increase in usage of multi-factor authentication. The required number of authentication factors may be decided based on transaction types, risk levels, threats and vulnerabilities.
Two-factor authentication provides a significant increase in security over the traditional username/password combination. In the two factor authentication, [9] [10] the user authentication is carried in two steps. In TFA any of the two factors can be combined viz. To withdraw amount from ATM, by combining two factors like Ownership and Knowledge. The ATM card (ownership) has to be inserted and unique pin (Knowledge) has to be entered to confirm validation.
This paper proposes a TFA scheme that uses speech (Inherence) of a user as the first factor and a text password (Knowledge) generated based on index with a sentence (Pass Phrase) as the second factor.
The rest of the paper is organized as follows: Section 1 describes the related work done earlier. Section 2 explain the techniques used in the proposed TFA scheme. In section 3, the proposed TFA scheme is described. Analysis of the proposed scheme in terms of usability and performance is presented in Section 4 followed by conclusions.
So far, researchers have proposed many remote authentication schemes that combine several factors including simple passwords, one time passwords either SMS- based or time synchronized, Public - Key Infrastructures (PKIs), biometrics etc [4] [11]. Most of the TFA schemes authenticate users based on what they know (Knowledge) and what they have incorporated as token less second factor (mobile) for authentication. Each method has areas to exist, based on design criteria for the overall usage.
In a TFA system, two different factors are combined in order to authenticate a user [3]. It is claimed that TFA generally delivers a higher level of authentication assurance compared with just using one factor. The two classes of factors are distinguished as: personal factors such as user-defined password’s and physical factors such as smart-cards or human factors such as biometric traits. To yield TFA two factors are combined from two different classes where an individual factor is applied independently. ATMs are common example for TFA system, where physical factors are combined with personal factors. TFA only applies to systems which use factors of different classes – authentication schemes based on, for example, two biometric modalities (referred to as multi-modal authentication).
Figure 1 shows the basic operation mode of a TFA system including biometric authentication. At the time of enrollment biometric traits and a second personal or physical factor are presented. During authentication this factor is presented again in order to achieve successful authentication.
With respect to biometric authentication two different modes are distinguished: verification and identification [2]. Due to the variance in biometric measurements, biometric systems do not provide perfect matching as it is easily implemented in password or PIN-based authentication systems. Thus, a fuzzy matching is performed where decision thresholds are set up in order to distinguish between genuine and non-genuine users respectively.
Obviously, TFA increases the security of biometric authentication systems, since potential imposters have to compromise the second factors in order to gain access to the system as a first attack stage. However, if a TFA scheme is constructed where one factor is represented by a biometric trait and additional factors are either personal or physical tokens, both of these factors require a perfect matching. This means a wrong PIN or a wrong smart-card would result in a rejection of the imposters.
If each imposter would be in possession of the correct second factor of the account he wants to gain access to (i.e. the second factor has been compromised), the overall recognition rate of system is expected to remain the same. Applying a sequential check of both factors (regardless of the order), the recognition rate is equal to a system which only performs biometric authentication. That is, additional factors become meaningless with respect to recognition performance since these are potentially compromised by all imposters. By analogy, if no imposter would be in possession of the correct second factor of the account he wants to gain access to, the overall recognition rate is of course expected to increase. This is because imposters who may have tricked the biometric authentication system are rejected at the time the additional factor is checked. Throughout literature several approaches have been proposed where TFA is introduced to biometric systems. In any case, authors claim to introduce personal or physical tokens in order to enhance the security of the system. However, in some cases it is doubtful if the system can maintain recognition rates without the use of a second factor (i.e. in case the first factor has been compromised).
Teoh et al. [15] introduced a technique to generate cryptographic hashes out of face biometrics which they refer to as “Bio Hashing”. Like in generic TFA schemes, in the Bio Hashing approach random numbers are associated with each user. These user-specific random numbers are used as seed in order to generate biometric hashes. These random numbers, which represent the second factor have to be presented to the system in addition to biometric data at authentication. The authors report almost perfect performance rates for the generation of biometric hashes. In order to expose the true performance of Bio Hashing, Kong et al. [16] presented an implementation of Face Hashing. It was found that the reported performance was achieved under the hidden assumption, that random numbers are never lost, stolen, or compromised. This assumption does not hold in general. Physical tokens can be stolen or duplicated while personal tokens can be easily guessed or broken by dictionary attacks. In order to associate cryptographic with biometric data Reddy et al. [3] proposed “fuzzy vault scheme” based on iris biometrics. The authors achieve TFA by embedding an additional layer of security, namely a password.
In recent work Jassim et al. [17] proposed a method of improving the performance of PCA based face recognition system. The authors introduce random projections based on the Gram-Schmidt process which are used to map biometric features onto secret personalized domains. For this purpose a secret permutation matrix is assigned to each user, which represents a second factor. This means, each user is in possession of a unique matrix.
Imran Naseem et al. [4]. proposed physiological biometrics from face that are combined with behavioral biometrics from speech in video to achieve robust user authentication which used the Mel Frequency Cepstral Coeffcients for text-independent speaker recognition and local scale invariant features for video-based face recognition.
This paper presents a two factor authentication scheme which combines speech (behavioral biometrics) and an index password.
This section describes the techniques used for Speaker verification and generation to passwords from the index and sentence provided, as the user is authenticated by verifying his speech and index passwords.
Speaker verification is a biometric system which performs the computing task of validating a user's claimed identity using the characteristic features extracted from their speech samples. Speaker verification is one of the two integral parts of a speaker recognition system with speaker identification being the other one. Speaker verification performs a binary decision which consists of determining whether the person speaking is the same person he/she claims to be or to put it in other words, verifying their identity. Speaker identification on the other hand does the job of matching (comparing) the voice of the speaker (known or unknown) with a database of reference templates in an attempt to identify the speaker [1]. This paper focuses on speaker verification [14]. Speaker verification is further divided into two subcategories, text dependent and text-independent speaker identification. Text-dependent speaker identification differs quite much from text-independent, as the aforementioned identification is done on the voice instance of a specific word, whereas in the latter the speaker can say just anything. This paper considers only the text-dependent speaker verification category.
Automatic speaker identification[12] [13] and verification are often considered to be the most natural and economical methods for avoiding unauthorized access to physical locations or computer systems. Speaker identification refers to the process of finding which registered speaker provides a specified (given) utterance. Speaker verification refers to the process of accepting / rejecting the identity claim of a speaker. Figure 2 and Figure 3 illustrate the basic differences between speaker identification and verification systems.
Figure 3 shows the two main modules of a speaker verification system, feature extraction, and feature matching. The purpose of feature extraction module is to convert the speech waveform into a set of features or rather feature vectors used for further analysis. The feature matching module matches the features extracted from the input speech with the stored template (reference model) and a verification decision is made. Mel Frequency Cepstral Coefficients (MFCC) for feature extraction process and for feature matching, Dynamic Time Warping (DTW) as proposed by Srinivasan [14] has been considered for implementation.
Figure 3. Block Diagram of Speaker Verification System [14]
In the proposed scheme the user is asked to give the password at the time of registration and it is stored as a template. Now, at the time of login, the user is asked to give a sentence along with the index, which forms the password of that particular user. The password is generated by concatenating the first index number of letters in each word of the Pass Phrase Table 3. For example,
Password: INDIAN

Table 3. Pass phrase
As with every authentication scheme, this scheme also has two phases, the registration phase and the verification phase and these are described in this section.
The step by step procedure for user registration is as follows:
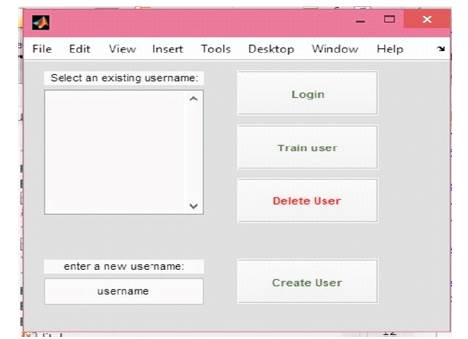
Figure 4. The Main GUI of the Authentication Scheme
1. Proposed Two Factor Authentication Scheme
As with every authentication scheme, this scheme also has two phases, the registration phase and the verification phase and there are described in this section.
Registration Phase:
The step by step procedure for user registration is as follows:
1. User chooses the User Name
2. Train the user voice by stating a password and storing the templates (created after undergoing feature extraction and feature mapping) in the database against the User name
3. Choose a text password and store it in the database along with the user name and voice template.
Figure 4 shows the main GUI of the two factor authentication scheme where the new user can create his own account and the existing user can login or train his voice and can delete the existing user. The user has to choose the User name.
The user can create account by clicking on create user button, which prompts the user to state his password as shown in Figure 5. Clicking on the record button the user is allowed to say a password. Once the statement is completed, the user has to click on stop button as shown in Figure 6.
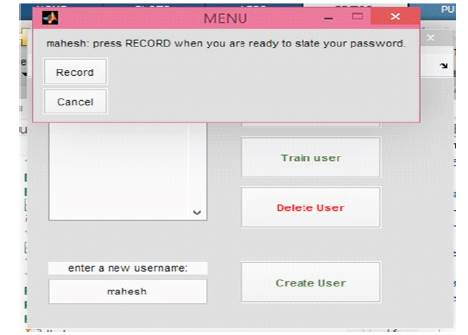
Figure 5. Registration Phase Begins
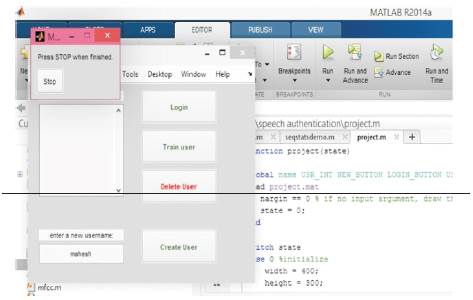
Figure 6. Registration Phase: Recording Speech
After this the user is prompted to repeat the password for two times to train his voice in order to obtain the templates accurately, and they are stored in the database. Then the user is requested to provide his text password as shown in Figure 7.
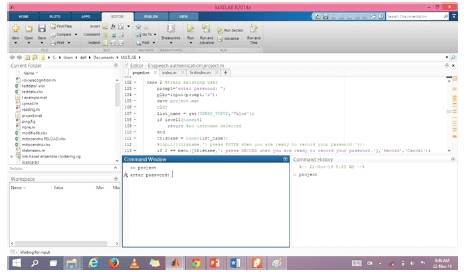
Figure 7. Entering the Text Password
After training the user voice and entering text password, the user completes the registration phase.
In this phase, the user is allowed to state/utter the password provided at the time of registration. Then it undergoes steps of feature extraction and feature mapping and then the decision is taken as to whether the user passed the test or not. Then in the next step of authentication, the second factor (text password) is obtained from the sentence and the index provided by user. The password obtained is matched with the stored one. If they match login is successful otherwise the user is unauthorized and may be prompted to login again. The step by step procedure for login is depicted in Figure 8.
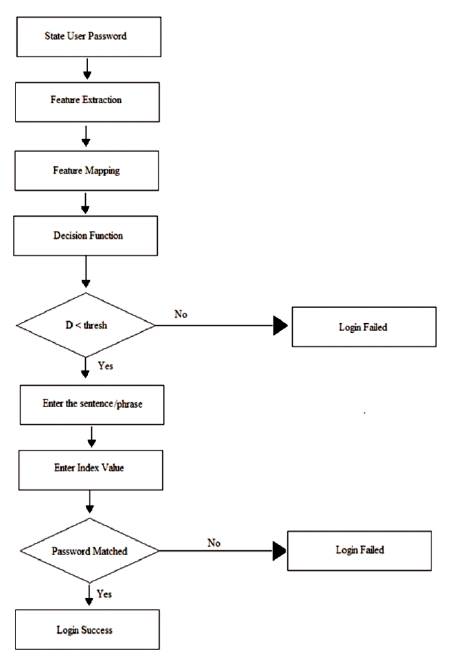
Figure 8. Flow Chart of the Login Phase
Figure 9 shows that the user can login by selecting appropriate username and clicking on the login button then a popup window appears displaying to state the password.
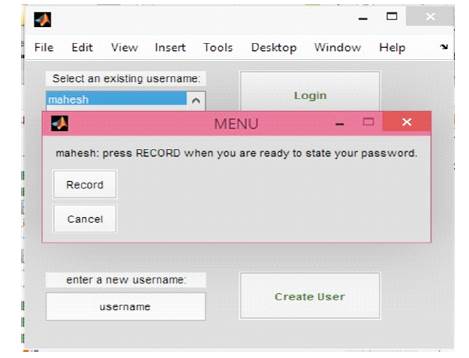
Figure 9. Stating the Password For Login
Figure 9 shows that the user can login by selecting appropriate username and clicking on the login button then a popup window appears, requesting the user to state the password.
If the user voice matches with the stored templates then the user is prompted to proceed as shown in Figure 10. This completes the first factor of authentication that is speech. If the stored templates do not match the user is prompted “login failed”.
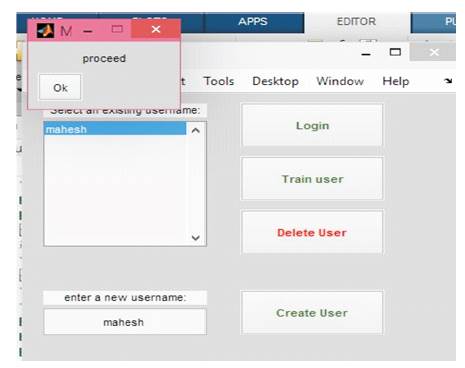
Figure 10. User Prompted password Is Correct
After clicking on 'ok' in Figure 10 the user is requested to enter the phrase/ sentence and index as shown in Figue 11.
The password obtained is compared with stored password given in the registration phase. If both match, then it displays “login success” else the login fails.

Figure 11. Entering Index Value
Usability and performance analysis have been carried on the proposed TFA using Morea Tool and the results are depicted in this section. Security analysis is also carried out.
Usability refers to the ease of use and ability to learn the human–made object. The usability analysis shows up to what extent the user can easily use this authentication system and passwords. Morae tool has been used to check the usability of the proposed schema. The usability analysis using Morae tool involved the process of asking more than 50 people to use the system and answer the questionnaire at the end of authentication session. The System Usability Scale (SUS) is determined by the ease of the users while working on the system. The answer for each question is considered a metric in determining the usability of the proposed scheme. Each user has to rate the system on a scale of 5 based on his level of satisfaction on working with the system. The SUS is calculated based on average answer scores for each question and is represented in the Figure 12. This figure illustrates the level of satisfaction the users got after utilizing the proposed Authentication system. The SUS score can effectively differentiate between usable and unusable system. An SUS score above 68 would be considered as above average. The SUS score obtained for the proposed system is about 75%.

Figure 12. System Usability Score
The Registration Time and the Login Time are measured by taking the average of the registration and login time of 50 users after training them with the system and are tabulated in the Table 4. The user is requested to provide two factors that is speech and text at the registration time. The user is requested to provide the speech and the sentence during login, so the time taken for the proposed scheme is more compared to single factor authentication schemes, but the security level increases enormously.

Table 4. Registration and Login time
Authentication is a process of confirming the identity of the user in order to prove that the user is genuine. This paper presents a two factor authentication scheme using speech and an index password to enhance the level of security. The user can login only when two factors are provided accurately and if any one fails, the user is unable to login. The scheme is analyzed for usability and performance. The proposed scheme offers better security as the two factors used are difficult for an attacker to reproduce.