
Figure 1. Passface Scheme
Authentication is the mechanism in which the system checks the identity of the user who access it. Traditional alphanumeric passwords are used. Due to the limitation of human memory, most users try to choose short-term or simple passwords which are easy to remember. Surveys show that frequent passwords are personal names of family members, birth date, or common words. In most cases, these passwords are easy to guess and vulnerable to dictionary attack. In an attempt to create more memorable passwords, graphical password systems have been devised. In these systems, authentication is based on clicking on images rather than typing alphanumeric strings. This paper presents a survey on some graphical password authentication systems.
A graphical password is an authentication system that works by having the user select from images, in a particular order. For this reason, the graphical-password approach is also called as Graphical User Authentication (GUA). A graphical password is easier than a text-based password for most people to remember. Authentication is the principal method to guarantee information security and the most common and convenient method is password authentication. However, there are several inherent defects and deficiencies in alphanumeric passwords, which easily evolve into security issues. Due to the limitation of human memory, most users tend to choose short-term or simple passwords which are easy to remember. Surveys show that frequent passwords are personal names of family members, birth date, or common words. In most cases, these passwords are easy to guess and vulnerable to dictionary attack. Today users have many passwords for personal computers, social networks, E-mail, and more. They may decide to use one password for all systems to decrease the memory burden, which reduces security. Moreover, alphanumeric passwords are vulnerable to shoulder surfing attack etc.
Motivated by the promise of improved password usability and security, the concept of graphical passwords was proposed in 1996. Alphanumeric passwords, graphical passwords are knowledge-based authentication mechanisms. The main goal of Graphical passwords is to use images or shapes to replace text, since numerous cognitive and psychological studies demonstrated that people perform far better when remembering pictures than words.
A large number of graphical password schemes have been proposed. They can be divided into three categories according to the task involved in memorizing and entering passwords: recognition, recall, and cued recall. A recognition-based scheme requires identifying among decoys the visual objects belonging to a password portfolio. The techniques in recognition-based scheme are Passfaces, Déjà Vu, Story etc. A recall-based scheme requires a user to regenerate the same interaction result without cueing. The techniques in recall-based scheme are Draw-A-Secret (DAS), Pass-Go, BDAS etc. In a cuedrecall scheme, an external indiction is provided to help memorize and enter a password. The techniques in cuedrecall scheme are Pass Points, Cued Click Points (CCP), Persuasive Cued Click Points (PCCP) etc .Among the three types, recognition is considered the easiest for human memory, whereas pure recall is the hardest.
In this paper, various graphical password schemes are studied. Each of the methods have their own advantages and disadvantages. Many of the methods are enhancement of previous method. For Example Persuasive Cued Click-Points is the enchancement of passpoints and cued click point.
This paper is organized as section 1 contain Recognition Based Scheme, section 2 contain Pure Recall Based Scheme and section 3 contain cued Recall Based Scheme.
In this scheme, users will select pictures, icons or symbols from a collection of images. In authentication process, the users need to recognize their registration choice among a set of candidates.
This method was developed in 2000. In this technique, faces are used as an object for password. The set of images contain male and female images. During registration procedure, the users select whether their Passface set consist of male or female picture. After that they choose four faces from four set of grid in four steps as their future password and this was stored in database. On the next step, a trial version is carried out in order to learn the real login process. During trial, the users take two times through the Passface login. The enrolment will be completed by correctly identifying their four Passfaces in this two trials.
During login phase which is been shown in Figure 1, contain 9 pictures grid which is given to the user. This grid only contains one of the user's passwords, and the other eight pictures are selected from the database. As the user's password contain four faces, the grid is shown four times. User need to select four faces from four set of grid in four steps. However, no grid contains faces found in the other grids, and the order of faces within each grid contain randomized image. These features help secure Passface combination against detection through shoulder-surfing and packet-sniffing attack [1].

Figure 1. Passface Scheme
This method was developed in 2002. Figure 1 shows triangle scheme. This scheme presents a set of N images to the user. User needs to select a subset of K images from the set. This selected subset is the password of the user.
During login, the system will randomly select the N objects, then the user must find atleast three of his password objects, that is the K subset images. Then the user clicks inside the invisible triangle created by those three objects or click inside the convex hull that are displayed. In addition, for each login, this challenge is repeated a few times more using a different display of N objects. Hence, the probability of randomly clicking in the correct region in each time is very low [2].
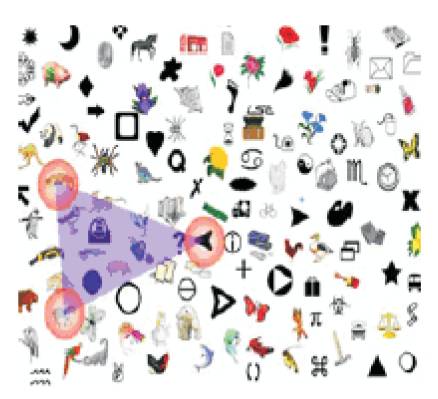
Figure 2. Triangle Scheme
This method was developed in 2004. This method categorizes the available picture into nine categories which contains animals, cars, women, food, children, men, objects, nature and sport. Figure 3 shows the story scheme technique which contain all the nine categories images.

Figure 3. Story Scheme
The users have to select their passwords from the mixed pictures of nine categories. This mixed picture make a story which helps for easy remembering of password. Some users select images from this grid without defining a story for themselves [3]. The research showed that the story scheme was harder to remember when compared to Passface authentication.
In 2003, this was algorithm designed especially for handheld device like Personal Digital Assistant (PDA). As it is shown in Figure 4, during enrollment, a user selects a theme identifying the thumbnail photos to be applied and then registers a sequence of thumbnail images that are used as a future password. When the PDA is turned on, the user must enter the current enrolled image sequence for verification to gain access to the device. After successful authentication, the user may change the password selecting a new sequence or theme[4].

Figure 4. Picture Password Scheme,
In this scheme, users need to reproduce their passwords without being given any cue, reminder or hints.
This technique was developed in 1999. In this scheme, the system provides a 2D grid as shown in Figure 5 and user needs to create their password by drawning any picture on a grid. The user interface is consisting of a rectangular grid of size G * G [5]. Each cell in this grid is denoted by coordinates (x,y). As it can be seen in the figure, the coordinate generated by drawing is : (2,2), (3,2), (3,3), (2,3), (2,2),(2,1), (5, 5). During enrolment time, user has to draw a design on the rectangular grid and also need to remember the cells. At login user have to draw the design on the same cell in correct order as per the design during enrolment.
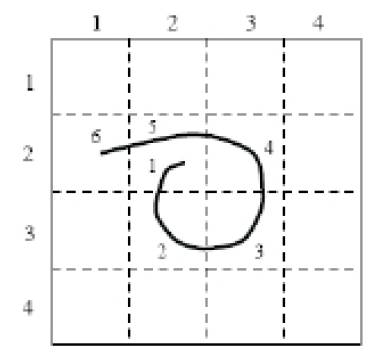
Figure 5. Draw a Secret (DAS)
This technique was developed in 2004. Passdoodle is a graphical password comprised of handwritten designs or text. The password created in passdoodle is usually drawn with a stylus onto a touch sensitive screen. Jermyn et al. prove that doodles are harder to crack due to a theoretically much larger number of possible doodle passwords than text passwords [6]. Figure 6 shows Passdoodle password.

Figure 6. An Example of a Passdoodle
This technique was developed in 2004.Thorpe and van Oorschot proposed this "Grid Selection" method. Initially the grid is very large. From this large grid the user selects a drawing grid is a subset of original grid. This selected subgrid which is a rectangular region to zoom in on, in which the user enter their password (Figure 7). This is the improved version of DAS and significantly increases the DAS password space [7].
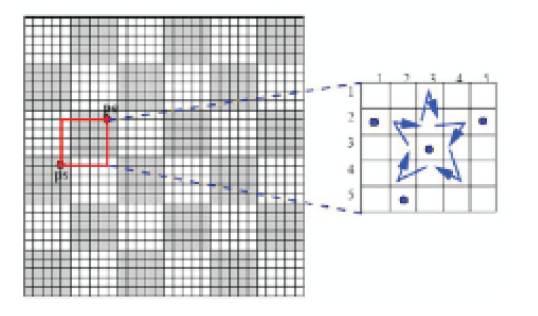
Figure 7. A sample of Grid Selection method
In this category, the technique proposed a framework of cue, reminder, hints and gesture that help the users to reproduce their password.
This technique was developed in 2005.In this technique, user has the freedom to select the image. On the selected image, user need to click some points as their password(Figure 8).This number of points varies according to the system. This selction of image and points over image was done in enrolment phase. At login time, user have to select the same points in the same order on the image. Some system use five click points as the password. These five point password is more strong than eight character password. Also user remember images than text based password [8].

Figure 8. A sample of Passpoint method
This technique was developed in 2007.This method is an alternative for PassPoints. In CCP [9], user need to select five images and click each points on each images as their password shown in Figure 9. Each image acts as a cue for the one corresponding click-point. Each click results in showing a next-image. A wrong click leads to an incorrect path, with an indication of authentication failure only after the final click.
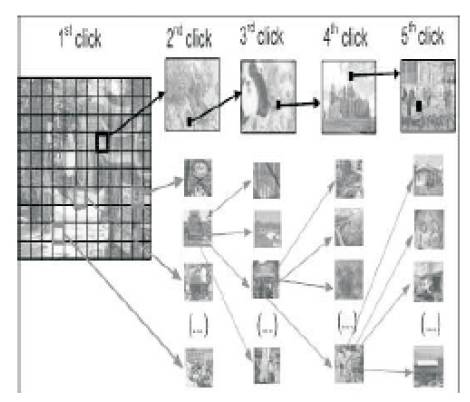
Figure 9. Cued Click Points
This technique was developed in 2007. PCCP [10] is similar to CCP. User need to select five images and click each points on each images as their password. During password creation, a small view port area that is randomly positioned on the image. This view port allows the user to select the point on the specified view port. This view port helps the user to select the point without any hotspot problem. Hot spot is the point in which most of the user may tend to click as their password .Also the system provide shuffling of view port. If the users are unable to select a point in the displayed view port, they may press the Shuffle button to randomly change the position of the view port. Figure 10 shows sample PCCP.

Figure 10. Sample PCCP
In this survey paper, varoius techniques of graphical password was studied. Graphical passwords are an alternative to alphanumeric passwords in which users click on images to authenticate themselves rather than type alphanumeric strings. Different studies show that user remember images than text. Hence graphical passwords allow user to remember their password better than text based password. Studied graphical password authentication techniques are classified into three categories. Also studied different techniques inside each categories. Each methods have both advantage and disadvantage. Some users felt difficulty in some techniques.