
Table 1. Year Wise Summary of Phishing Incident Handled by Cert-In
When a hacker sends a phishing email or host a phishing website, investigators must locate the source of the communication, they must trace the electronic trail leading from the email or the web server back to the perpetrator. Traceability is a key to the investigation of the cyber crime such as phishing. It is impossible to prevent all internet misuse but may be possible to identify and trace the user, and take appropriate legal action. Different phishing detection mechanisms have been addressed in research papers, but with little being focused on open proxy usage rather, misusages. This paper addresses the security concern for mushrooming of open proxy servers in the globe. This work highlights how anonymity provided to the phisher by an open proxy is becoming a major roadblock for cyber crime investigating agencies in India. We conducted personal interviews with various law enforcement officers involved in Cyber crime cases mainly, Phishing and prepared a flow chart of how all these cases are getting stalemate because of the open proxy servers. Helpless condition of these investigating agencies proves that easy availability of free and easy anonymous proxy servers motivates phisher to plan the attack knowing very well that they will not be traced back. In our solution framework we propose two dimensional approach combining technical solution and legal cooperation among international law enforcement agencies. Our technical solution will be able to flag all emails that are using an open proxy, also it will be able to locate any website usage or update through an open proxy.
The Internet is rapidly transforming the way we communicate, educate, buy and sell goods and services. As the Internet's potential to provide unparalleled benefits to society continues to expand, however, there has been an increasing recognition that the Internet can also serve as a powerful new medium for those who wish to commit unlawful acts such as phishing. Life is about a mix of good and evil, so is the Internet or cyberspace. For all the good it does to us, cyberspace has its dark sides too. Unlawful conduct involving the use of the Internet is just as intolerable as any other type of illegal activity. The rapid growth of Internet has shrinked the globe in such a way that cyber crime is now recognized as a major international problem, with continual increases in incidents of phishing, hacking, viruses, and other forms of abuse having been reported in recent years. Although the problem of computer crime has been apparent since the early days of computing, the difference today is the increased scope available to would-be attackers, largely due to the popularity and numerous benefits offered by the Internet.
To understand the sinister implications of phishing, one needs to understand how internet works and the growing dependence on Internet in modern life. In a day and age when everything from the water heater in the bathroom to nuclear power plants of the country are being run on computers (Hill, 2009), phishing has assumed rather evil role in the modern society. The reason as to why phishing is posing a serious threat is because of the fact that it is usually very hard to track the phishers as they operate from far and different places, sometimes even from different countries, making it harder for the law enforcers to track and find them. Individuals or groups who wish to use a computer as a tool to facilitate unlawful activity may find that the Internet provides a vast, inexpensive, and potentially anonymous way to commit unlawful acts, and the list of such acts is huge. In this paper the author has tried to highlight the nuisance of phishing, and the hurdle faced by the investigating agencies to identify the phisher who takes the benefit of anonymous usage of the Internet.
The Methodology of Phishing is very similar to fishing, when bait is thrown, it is anticipated that an unsuspicious user will latch on to it and bite it just like a fish does, thus it is also known as bait and hook method (Emm, 2006). In most cases, the bait is either an email or an instant messaging site (Shein, 2011), which will take the user to hostile phishing websites which in most cases would be a clever replica of credible financial institution's website. The fake website will have similar look and feel as of the original one and will be asking for the sensitive information like user name, password, credit card details etc (Hinde, 2004). When the victim (user) enters the information, the data is sent to the phisher who thereby uses the same for his personal gain. Phishing has become the most common channel for thieves to acquire personal information to aid them in identity theft (Mercuri, 2006; Brody et al., 2007; Anderson et al., 2008; Eisenstein, 2008).
Studies show a steady increase in phishing activities as well as the related cost. APWG in their annual report published in October 2012, reported 93,462 Phishing attacks from the period of January to June 2012 (APWG, 2012). PhishTank the online website which collects data on websites engaged in phishing activities received 22,581 valid submissions of phishing websites solely for the month of July 2012 (PhishTank, 2012). In April 2009 Gartner group [7] published results of a survey showing more than 5 million U.S. consumers who lost money to phishing attacks in the 12 months ending in September 2008, a 39.8 percent increase over the number of victims a year earlier (Gartner, 2009). Table -1 below gives a year wise summary of phishing incident handled by Indian Computer Emergency Response Team (Cert-In) in India (CERT-IN, 2013).

Table 1. Year Wise Summary of Phishing Incident Handled by Cert-In
Billions of dollars are lost each year due to unsuspecting users entering personal information into phishing websites, more than monetary loss, users may lose their confidence in the system and on their banks (Altintas and Gursakal, 2007). As concluded by Parno et al. (2006) phishing is a significant and growing problem which threatens to impose considerable monetary loss in businesses and to shatter consumer confidence in e-commerce. As highlighted by authors, Phishers will become more active and their attacks will become more sophisticated, making user-based protection mechanisms fragile given the user population of non-experts. As stated by (Bielski, 2004; Bielski, 2005; Wang et al, 2009) the increase of phishing poses severe threats to legitimate e-mail communications between both business houses and customers.
As discussed by Medvet et al. (2008) the idea of tricking people for financial profit is an old idea, but the easy availability and popularity of Internet allowed criminals to mount phishing attacks very easily against multiple users with a single attack (Furnell, 2008). They also highlighted that the Phishing attacks are not only problematic for Internet users, but also for organizations that provide financial services online. The reason is that when users fall victim to phishers, the organization providing the online financial service, such as an online bank, suffers an image loss as well as a financial damage (Furnell, 2004; Furnell, 2004a; Singleton, et al., 2006; Bose and Leug, 2008; Featherman, et al. 2010; Chen et al. 2010).
Network managers and administrators face a steep uphill battle in effectively monitoring and managing network resources and controlling unwanted traffic (Eggendorfer, T. , 2005). Organizations are ever vigilant in keeping their network safe, for which they have invested time and resources and they are constantly developing appropriate network usage policies and implementing firewalls, URL filters and intrusion detection solutions. With proliferation in security systems on daily basis the closing of one gap in the ever vulnerable network leads to an opening of a new one. Open proxy servers and its applications act as one of the most ominous threats to security and performance of a network. The firewalls and filters of an organization's network are unable to detect any intrusion when users take help of open proxies which help them bypass the usage policies of those networks easily. And constant availability of New open proxies make it extremely difficult for an organization to thwart these constant intrusions.
The prospects of gaining access to improper, banned or illegal websites rise when users take help of open proxies and this leads to the organizations being exposed to legal or regulatory consequences (Adinolfi, 2003). The security and privacy of users and their data are vulnerable when open proxies are used, as it creates a security hole and allow the incoming of malicious traffic, which may constitute malware and Trojans, to enter the network. These proxies may downgrade the network performance and slowdown the response times for vital applications. The organization can be in jeopardy if unwanted applications are permitted to outwit usage policies and consume bandwidth meant for genuine business applications which may in-turn result in the hampering of productivity as well.
A proxy server acts as an intermediary between a client computer and the Internet serving as a buffer between the client computer and the Internet resources one is accessing. When a client makes a request for an Internet resource through a proxy server, the proxy makes a connection to the requested resource on the client's behalf to get the resource and delivers it down to the client (see Figure 1). By this process, it is able to hide the internal address of the client to the Internet and the IP address of the proxy only becomes visible on the Internet. A Proxy Server can be used to enforce security, administrative control, and caching.

Figure 1. Working of an Authorized Proxy Server
A Proxy Server should accept requests from only its own network or clients by either forcing a client to connect from a range of IP addresses, or by using authentication. Any proxy server that doesn't restrict its client base to its own set of clients and allows any other client to connect to it is known as an open proxy (see Figure 2). An open proxy will accept client connections from any IP address and make connections to any Internet resource. Open Proxy Servers act as blind intermediary to any other network addresses without any authentication (CERT-IN, 2013).

Figure 2. Working of an Open Proxy Server
Any web site (Programmed correctly) can track user's movements through its pages and monitor users browsing habits using IP address. Users visit can be registered and used later to gather some personal information about the user. Using information about users operating system and the IP address of the system, a Web site can automatically exploit security holes in users system using some not-very-complex, ready-made, free hacking programs. Some of the programs can do basic harm of just hang the machine or reboot it, but there are harmful ones as well that may access sensitive information directly from the hard-drives as well. Using these anonymous proxies in one's own network, can prevent intrusion as it hides the clients IP Address so that no one can connect to the network. Users' surfing interests can be effectively concealed as anonymous proxy servers do not transfer the information about clients IP Address.
Anonymous Proxy can be used in the countries where government agencies monitor and record citizen's activity on the internet (Denvpn, 2013). Employee of a company can also use anonymous proxy to bypass the company internet filters (see Figure-3) which is used to restrict and monitor internet usage in company network.

Figure 3. Open Proxy to Bypass Local Proxy Filter
A malicious user can effectively hide his own IP address by using an open proxy server for a cyber crime. In such scenario instead of the IP address of the criminal appearing in the log files of the attacked server, the IP address of the open proxy server will appear. Criminals routinely chain through several such open proxy servers making it difficult to trace back to the origin of the perpetrator. In worst case scenario a criminal can use open proxy servers from various countries before attacking the victim (see Figure-4). In such case it will be very difficult to catch the criminal, as the case has to be routed through Interpol and various other International organizations.
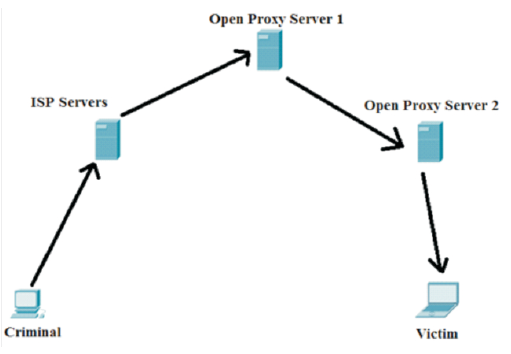
Figure 4. Multiple Open Proxies used to Attack the Victim
open proxy servers are widely prevalent on the Internet and are being misused by malicious users to route traffic bypassing network controls. CERT-IN, Indian Computer Emergency Response Team is regularly tracking open proxy servers hosted in India (CERT-IN, 2013) (see Figure 5).

Figure 5. Open Proxy Servers being Identified by CERT-I.
The rest of the paper is organised as follows. In Section 2 we discuss the related work on anti-phishing and problem related to open proxy. Section 3 investigates the problems faced by the investigating agencies (Cyber Cell, West Bengal Police). Section 4 presents our lab experiments and results. In Section 5 we discuss the solution framework. We conclude and motivate for future work in Section 6.
Open proxies have recently emerged as very effective tools for Internet misuse ranging from activity and online information abuse to criminal and cyber-sexual internet abuse. The ease with which existing proxies can be found and accessed, and new ones can be quickly set up poses an increasing difficulty to identify them. Previous work on open proxy highlights the nuisance value of the Open Proxy, Web Proxy or Anonymous proxies. In a recent work Canini et al., (2009) provides a detailed understanding of web proxy and highlights the easy availability of open software which can be used to create home proxy to mount an anonymous attack on any network. They also propose a method to detect web proxies. Their method, based upon measurement of simple flow characteristics and server profiling, does not rely on packet payload inspection.
In another study researchers (Pai et al., 2004) discuss their experiences with undesirable traffic on CoDeeN (Content Distribution Network) proxy networks (Codeen, 2013) and the mechanisms they developed to curtail it. Some of the security mechanisms they proposed are suitable for Internet Service Providers (ISP) to deploy on their own networks to detect misbehaving customers before problems arise.
Boneh (2004) discusses the feasibility of successfully tracing the origin of spam email by following the electronic trail. The main question addressed is whether investigator can identify the source of spam email, particularly in cases where spammers conceal their identities through open proxy. The report also discusses the use of Honeypot to keep a watch on the cyber criminals who are using open proxy for cyber attacks.
In another work Martin and Schulman (2002) discusses how the anonymizing services are designed to defeat content blocking by firewalls and to defeat web server attempts to identify users, all without degrading website behavior or requiring users to install specialized software. The paper also highlights the various possible attacks possible on such service anonymizing services which can put individual users at risk.
Krawetz, N. (2004) discussed how spammers are on the constant lookout in the Internet for open proxy relay and by making use of these open relays which can obscure the originating IP-address and stay anonymous. But once these spammers encounter a service on a honeypots, which attributes to collecting information about them, it helps to gain vital information on their true identity and expose them as well. He also discusses how spammers are using anti-honeypot technology to stay out of such honeypots and showing a thumbs-down to the investigators clutch.
In another work Lovet, (2009) highlights the issue of increase in Cyber Crime activity and the huge financial loss for the same. He addresses the technical challenges to catch a cyber criminal also highlights the slow justice process for a cyber crime across the globe. The paper points out the need for increasing the level of involvement of Interpol in the global fight against cyber crime and suggests for multilateral treaties among countries which will enable a smooth legal procedure for any transnational cyber crime in future.
Phishing falls under the category of cyber crime in India (Deity, 2013). The Information Technology (Amendment) Act, 2008, deals with the crimes relating to Internet fraud under section 43, 65 and 66. Cyber crime can be regarded as computer-mediated activities which are either illegal or considered illicit by certain parties and which can be conducted through global electronic networks, its distinctiveness being derived from the versatile capabilities provided by internet. The global connectivity of internet makes it much easier for criminals to cater beyond national boundaries to conduct their illegal affairs. In also makes it possible for existing organized crime to use more sophisticated techniques to support and develop networks for drugs trafficking, money laundering, illegal arms trafficking and the like. For hackers with the requisite computer skills, a large market exists for security and trade secrets which can be accessed and transmitted electronically (Thosmas and Loader, 2000).
“The United States often cannot quickly or reliably trace a cyber attack back to its source, even as rival nations and extremists may be looking to wage virtual war, it often takes weeks and sometimes months of subsequent investigation, and even at the end of very long investigations you're not quite sure, who carried out the offensive”. - Dennis Blair, US Intelligence Director (Blair, 2009).
When a phisher sends an email or host a fake website, cyber crime investigators must locate the source of the communication. Everything on the Internet is communications, from an email to an electronic fund transfer. Finding a cyber criminal means that investigator must determine who is responsible for initiating the communication which caused the crime.
To understand the difficulties faced by investigators to find a Phisher, we discuss a phishing case registered with cyber crime police, State of West Bengal, India.
One Mr. Banerjee (name changed) lost Rs. 30,000/- in a recent phishing attack. The mode of operation of the attack is very academic. Phisher has send an email to Mr. Banerjee asking him to change his login and transaction password immediately stating some urgent security upgrade on the Bank servers due to a virus attack. Mr. Banerjee followed the link given in the email which open the bank site (phishing site), and he changed his password on the same. Very next day while visiting an ATM he noticed that Rs. 30,000/- is transferred to some account which is not authorized by him.
After a written complaint to the respective bank and a subsequent visit to the Police station, Mr. Banerjee understood that he is a victim of phishing attack.
Once the Investigation started it was noticed the money was transferred to a foreign bank operating in India, and currently the bank account is closed. The address given during the bank opening is not a valid address.
Investigating officer started to investigate with the basis of the email received and the website hosted. What he could find is the phishing website is not available any more and the mail was sent using an IP address from one of the open proxy server based in Nigeria.
Case status: Investigation is on
We have prepared the following event flow chart (see Figure-6, normal investigation, Figure-7, investigation for open proxy) after a detailed discussion with the investigating officers from West Bengal Police. This paper only validates the Open-Proxy is a major road block for phishing investigation. As more than 20 phishing cases are pending with West Bengal police courtesy open proxy servers from some of the African countries mainly Nigeria. At the end of the day all anti-phishing toolbars or anti-phishing counter measures are not enough to deter a Phishing attack as the phisher knows, it will be difficult for the investigating agencies to catch them.
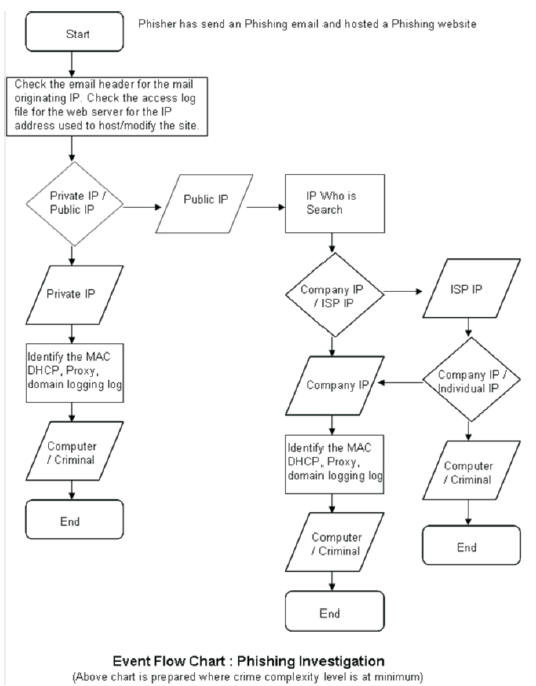
Figure 6. Event Flow Chart: Phishing Investigation

Figure 7. Event Flow Chart: Phishing Investigation – Open Proxy
We simulated an open proxy attack in one of the web server in our lab and also sent spam email using Simple Mail Transfer Protocol (SMTP) server accessing from another open proxy. We also tested previous work of other researchers to investigate the source of phishing attacks, using Honeypot, Honeytoken & Web bugs (Mokube and Adams, 2007; Martin and Alsaid,2003; Huang et al., 2009; McRae and Vaughn, 2007). We give below our testing methodology, steps and results.
We hosted the following servers (see Table 2) in our lab to simulate the attack.

Table 2. List of Servers Hosted for the Lab Experiment
We installed a trap server (Honeypot server tools from download.com) on a Windows XP. We accessed the same through an open proxy server (proxy1). The trap-server recorded the IP address for proxy1, there were no records for our Windows 7 IP address. Second time we used the proxy1 to get connected to proxy2 and then access the trap-server, this time it recorded the IP address for proxy2. Our experiment was successful as it proves that the honeypot is not good enough to trace the IP address of the attacker, though it can record the activity performed by the attacker.
This time we accessed www1 which had web pages which will record the information which is kept as honeytoken for attacker to collect. This time also we used windows 7, through proxy1 to access the site nettech.in hosted on www1. The access log records never recorded the IP address for windows PC, but recorded the IP address for proxy1. Our experiment was a success as it proves that honeytoken or a web bug hosted on a webpage will not have satisfactory results if we access the same through an open proxy.
We did telnet to proxy1 and from there another telnet session to proxy2. From proxy2 we did a telnet to SMTP1 on port 25 (SMTP port) and sent an email to gmail.com hosted on SMTP2 server. After receiving the email we checked the mail header for our windows 7 IP address, which was not there instead we got the IP address for the proxy2 not even proxy3. This experiment proves that we can send email through an open proxy site which will not be able to trace back.
On our last experiment we hosted the web site www.icicibank.com on www2 server. This time we did multiple site updates through FTP on the server. Same as experiment 3 we first opened a telnet session with proxy1 and from there another session with proxy2 and then did FTP to the www2 server. The FTP log file of the www2 only gave us IP address for proxy2. There was no mention about our windows7 in address anywhere in the log.
What we saw in the controlled lab experiment that if we can use open proxy sites and then use any of the services as web, FTP or email there will not be any log of the original pc from where we are working. Thus, we will be able to hide our identity and do all phishing works possible. We tested the same with some of the open proxy available on internet and send few emails to our own email ids to check the header message. There was no mention about the original IP address in the message header. This anonymity gives the phisher the motivation to deploy more and more phishing nets knowing very will they will not be traced back.
In our solution framework we propose a two dimensional solution for this menace, one is technical to deter the phishing attacks from an open proxy, second one is a legal solution which can create a fear among the phisher community.
Open proxy is the server which is not based on IP address filtration or by user authentication. We propose a script/tool which will be able to identify the IP address from where the email is originated (can be done easily from the email header), and then perform a series of test to identify whether the proxy server is open or not. We can design the tool which will try to access services through the proxy server, it should not allow the tool to access the same at the first place, if the tool is able to access without any authentication, and it proves that there is no filtration for the IP address or user authentication. The tool should be able to mark the mail as SPAM and move the same to a SPAM folder.
We can also use the same approach for the web servers kept with the ISP sites. Any connection to the server should be from an authenticated proxy or else the IP address requesting for the service should be blocked. Now any person trying to access web servers through a open proxy site will not be able to update or do any FTP, as the connection will be automatically terminated by the web server. The web server will be able to identify the source of the connection as a open proxy connection and terminate the same.
Banks and other organizations deal with fraudulent phishing websites by pressing hosting service providers to remove the sites from the Internet so that there is nothing there for a misled visitor to see. The procedure is commonly known as take-down (Moore & Clayton, 2007). The same method can also be used to remove open proxy servers with the help of the concerned ISP.
It is clear that phishing has become part of our social and technological reality. Active development of the necessary legislation is desperately required. Bainbridge (2007), Larcom and Elbirt, (2006) in their work stated that the law, however, must take proper notice of current technical risks as well as measures taken to counter them. Granova and Eloff (2005) conducted a detailed study on phishing experience & available legal frame work in both the developing and the developed world. McNealy (2008) in his paper examines the existing state laws in USA aimed at stopping phishing as well as the proposed federal legislation. He concluded that adequate legal solutions would enable severe punishment of those caught phishing, the law also would allow both the victims of a phishing scam and companies whose informations were fraudulently used, to collect damages. Bose and Leung (2009) found that in Hong Kong government advocacy for adoption of antiphishing measures influenced the adoption of two-factor authentication by banks.
Larson (2010) in his paper recommended that courts should consider either large scale damages against individual phishers or secondary liability against Internet Service Providers (ISP) under the areas of either Intellectual Property (IP) or unfair competition law. The addition of secondary liability to anti-phishing efforts might motivate ISPs to become actively involved in anti-phishing efforts since ISPs are best positioned to prevent of phishing schemes (Calman, 2006). Additionally, trademark holders are also well positioned to deter phishing by asserting their IP rights against trademark infringing phishers and those engaging in unfair competition. The trans-national nature of the phishing or the overall cyber crime is the most accepted characteristic. Lovet (2009) in his work highlights the judicial challenges and recommends for expedient international cooperation and harmonization of cyber criminal offences amongst legal systems beyond borders.
As analyzed by Dinna et al. (2007), the legal scaffold of Malaysia, Unites States and United Kingdom and concluded that inadequacy of current legal framework is the main challenge to govern phishing. Nevertheless, until effective anti-phishing strategies are implemented, the cat-and-mouse game is likely to continue, as the law and law enforcement continues to struggle in keeping up with technology and technology-related crimes. As stated by Kim et al. (2011) the security model includes many participants with dissimilar interests: users, browser vendors, developers, CAs, Web server vendors, Websites, regulators, and standards committees. It is not easy to reach to a timely agreement among them.
Phishing costs Internet users billions of dollars a year. Different phishing detection mechanisms have been addressed in research papers, but with little being focused on open proxy usage rather, misusages. This paper addresses the security concern for mushrooming of open proxy servers in the globe. The anonymity provided to the phisher by open proxy is becoming a major roadblock for the cyber crime investigating agencies in India. We explained through a flow chart how all these cases are getting stalemate because of the open proxy servers. In our solution framework we propose two dimensional approach one technical and the second one legal cooperation. Our technical solution will be able to flag all the emails that are using an open proxy, also it will be able to locate any server usage or update through a open proxy. Though there will be question raised for the effectiveness of such filter and the speed of the same, future work is required on the same domain. More testing required is for their work on public network as well as on an ISP setup. Further work is required to identify the scope for a legal co-operation between International Investigating agencies.
Special thanks to Mr. Ranajit Chatterjee, DSP, Cyber Crime, CID, West Bengal Police for his input & valuable time.