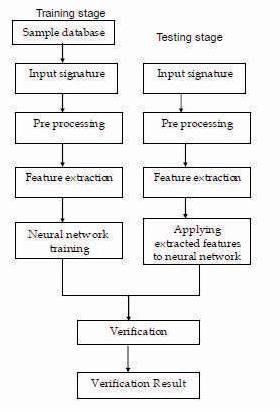
Figure 1. Flow Chart of Proposed System
Signature has been a distinguishing biometric feature through ages. Signature verification finds application in a large number of fields starting from online banking, passport verification systems, online exams etc. Human signatures can be handled as an image and recognized using computer vision and neural network techniques. This paper, proposes an off-line signature verification system using neural network. The system consists of three stages: the first is preprocessing stage, second is feature extraction stage and the last is verification stage using neural network. The objective of the work is to reduce two critical parameters, False Acceptance Rate (FAR) and False Rejection Rate (FRR).
Signature verification is not only a major area of research in the field of image processing and pattern recognition, but also widely used in the fields of finance, access control, contractual matters and security. A signature verification system and various techniques for signature verification are categorized into two separate classes, namely On-line method and Off-line signature verification method. On-line signature verification focuses on capturing and analyzing the signature in real time, as the person is signing it. Off-line signature verification deals with analyzing images of a person's signature.
On-line signature verifications system records the motion of the stylus (which is also part of the sensor) while the signature is produced, and includes location, and possibly velocity, acceleration and pen pressure, as functions of time. Off-line method uses an optical scanner to obtain handwriting data written on paper, deals with a 2-D image of the signature. Off-line method is complex due to the absence of stable dynamic characteristics. The non-repetitive nature of variation of the signatures, because of age, illness, geographic location and perhaps to some extent the emotional state of the person, accentuates the problem.
This paper is organized as follows: Section 1 discusses the overview of signature verification, Section 2 describes review of related work, Section 3 Proposed Approach, and Section 4 introduces Methodology, Section 5 Results. Finally, conclusion section is given.
The problem of personal verification and identification is an actively growing area of research. There are numerous methods based on different personal characteristics; voice, lip movement, hand geometry, face, odour, iris, retina and fingerprint are the most commonly used authentication methods. All these psychological and behavioral characteristics are called biometrics.
The biometrics have a significant advantage over traditional authentication techniques due to the fact that biometric characteristics of the individual are not easily transferable are unique of every person and cannot be lost, stolen or broken. However, despite the novelty and perceived security of the above techniques, the longest standing and most natural method for verifying one's identity is through the use of a handwritten signature. Handwritten Signature Verification (HSV) is an automated method of verifying a signature by capturing features about a signature's shape (i.e., static features) and the characteristics of how the person signs his/her name in real-time (i.e., dynamic features). HSV is more generally accepted by the public and is less intrusive than other biometric authentication techniques.
Neural Networks (NNs) have been an important part of computerized pattern recognition tasks for more than half a century. The two main reasons for their widespread usage are: 1) power (the sophisticated techniques used in NNs allow a capability of modelling quite complex functions); and 2) ease of use (as NNs learn by example it is only necessary for a user to gather a highly representative data set and then invoke training algorithms to learn the underlying structure of the data).
The SV process parallels this learning mechanism. There are many ways to structure the NN training, but a very simple approach is to firstly extract a feature set representing the signature (details like length, height, duration etc.), with several samples from different signers. The second step is for the NN to learn the relationship between a signature and its class (either “genuine” or “forgery”). Once this relationship has been learned, the network can be presented with test signatures that can be classified as belonging to a particular signer. NNs therefore are highly suited to modeling global aspects of handwritten signatures [54].
This paper presents a method for HSV by using NN architecture. Various signature features are extracted and used to train the NN. The resulting system performs reasonably well with an overall error rate of 3.7%.
The 1st Signature verification system developed in 1965 but use of neural network for verification has been started in decades of 90s. Mighell et al. in [27] were apparently the first to work on applying neural networks for off-line signature verification. A feed forward back propagation network with both dwell and momentum was trained for a database of 80 genuine & 66 forge signatures for a single person. The network was trained with 10 true signatures and 10 forgeries, until all signatures were classified correctly, and then tested on the remaining 70 true signatures and 56 forgeries. The best results reported were 2% false rejection rate and 2% false acceptance.
Mehdi Dehghan, Karim Faez & Mahmood Fathi proposed an offline signature verification system using shape descriptors & multiple neural networks. The verification was based on the signature shape descriptors such as the skeleton, upper and lower envelopes of the signature and high pressure region of the signatures. Multiple multilayer perceptron neural network module was use to make a decision of verification using fuzzy integral voter. The networks were trained by a modified back propagation algorithm. A database of 1000 signatures from 50 persons was created with random and skilled forgeries, accuracy of 96% for simple and 90% for skilled was obtained. The system verified the signatures with an overall accuracy of 98% [41].
H. Baltzakis and N. Papamarkos [10] proposed system was based on global, grid and texture features. For each one of the feature sets a special two stage Perceptron OCON (one-class-one-network) classification structure was implemented. In the first stage, the classifier combined the decision results of the neural networks and the Euclidean distance obtained using the three feature sets. The results of the first-stage classifier feed a second-stage Radial Base Function (RBF) neural network structure, which made the final decision. FAR was 9.81% and FRR was 3%.
Stephane Armand, Michael Blumenstein and Vallipuram Muthukkumarasamy proposed an Off-line Signature Verification based on the Modified Direction Feature. The system uses a database of 2106 signatures. MDF employs a hybrid of two feature extraction techniques, Direction Feature (DF) and the Transition Feature (TF). The feature vector was extracted by zoning and computing the most representative direction values in a given zone. Two neural network classifiers were used to classify the signatures: the resilient back propagation (RBP) neural network and the Radial Basis Function RBF) network. For RBP, verification rate of 86.08% and for RBF a verification rate of 89.61% was achieved. The highest accuracy obtained was 91.12%.
Bradley Schafer, Serestina Viriri presented an offline signature verification system based on global features and transition features. During testing, a claimed signature is compared against our template file using the Euclidean distance and if it is below a certain threshold value, then the signature is declared valid, otherwise it is a forgery. The first approach is to use a global threshold to do all the comparisons against. Using the global threshold correct classification rate of 73% and a false acceptance rate of 18.5% were obtained. Using the second approach, the localized threshold, a correct classification rate of 84.1% and a false acceptance rate of 17.8% was obtained [43].
Abbas used a back propagation neural network prototype for the offline signature recognition. He used feed forward neural networks and three different training algorithms Vanila, Enhanced and batch were used. He reported FAR between the ranges of 10-40 % for casual forgeries. A neuro-fuzzy system was proposed by Hanmandlu, they compared the angle made by the signature pixels are computed with respect to reference points and the angle distribution was then clustered with fuzzy c - means algorithm. Back propagation algorithm used for training neural network. The system reported FRR in the range of 5-16% with varying threshold [42].
O.C Abikoye, M.A Mabayoje & R. Ajibade proposed an offline signature recognition & verification system using neural networks. The verification was based on various global mask and grid features. A back propagation neural network was trained. The recognition system exhibited 100% success rate by identifying correctly all the signatures that it was trained for. However, it exhibited poor performance when it was presented with signatures that it was not trained for earlier.
This paper proposes a system for off-line signature verification using a set of global, geometrical, texture & transition features and Feed Forward Back Propagation Neural Network is used as a classifier.
The overall architecture of our signature recognition system follows: Signature acquisition, Preprocessing, Feature extraction, and Classification. Initially a set of signatures are obtained from the subject and fed to the system. These signatures are preprocessed. Then the preprocessed images are used to extract relevant global, geometric, texture & transition parameters that can distinguish signatures of different persons. These extracted features form a feature vector set that are used to train the system. The neural networks are trained until the performance goal is met.
In the next step the scanned signature image to be verified is fed to the system. It is preprocessed to be suitable for extracting features. It is fed to the system and various features are extracted from them. The trained network is then simulated with this test signature features and the output is obtained. Depending on whether the input signature satisfies the threshold condition, the system either accepts or rejects the signature. A flow chart illustrating the various steps that have been used in our proposed signature verification system is depicted as follows.

Figure 1. Flow Chart of Proposed System
The methodology used in the proposed system is described below
The pre-processing stage includes seven steps: Resizing, RGB to gray, Contrast Adjustment, Binarization, Thinning, Finding the location of the signature image in the figure and Finding the minimum bounding box across the image. The purpose in this phase is to make signatures standard and ready for feature extraction.
3.1.1 ResizingEach signature image is resized to [128,128] format. Resizing is done using a predefined matlab function. This function computes the number of rows or columns automatically to preserve the image aspect ratio.
3.1.2 RGB to Gray conversionComparing and verifying an image having multiple colour strains is pretty complex. Moreover it is unnecessary to compare the colour as it has no known effect on the signature pattern. So, we have extracted the gray scale format of the scanned image. We use gray scale for further analysis. The gray scale image is obtained by using predefined functions of image processing available in the MATLAB implementation.
3.1.3 Image Contrast EnhancementContrast enhancements improve the perceptibility of objects in the scene by enhancing the brightness difference between objects and their backgrounds.
3.1.4 BinarizationImage Binarization or thresholding is an important step in image processing and computer vision, to extract the object pixels in an image from the background pixels. Binarization is performed using a predefined matlab function.
3.1.5 ThinningThinning is a process that deletes the dark points and transforms the pattern into a “thin” line drawing called skeleton. This filter aims to reduce the width of the signature from several pixels to a single pixel. This process is performed on binary image.
3.1.6 Finding the location of the Signature image in the figureThis is performed to extract only the signature image from the entire scanned figure, i.e. to remove the excessive blank space around the signature image. The resulting image matrix will be other than [28], depending upon the size of the individual signature.
3.1.7 Finding the bounding box of the image and cropping unnecessary parts (edges) of the imageA function has been created to calculate the minimum bounding box. The image is traversed from left to right and top to bottom and the location of the extreme top, bottom, left and right pixels are determined and a bounding box is created just big enough to accommodate Processed Image. The bounding box of the image was found and the image was cropped out, thereby eliminating blank areas from the sides of the image. Thus, now each image consists only of the signature part.
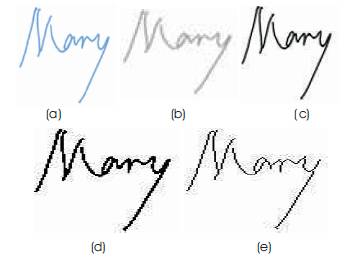
Figure 2. Preprocessing Stages: (a) Resized Image, (b) Gray Image; (c) Intensity Enhanced Image, (d) Binary Image & (e) Thinned Image

Figure 3. Signature Bounding Box
The choice of a powerful set of features is crucial in signature verification systems. The features that are extracted from this phase are the inputs in the training phase. We use a feature vector of dimension 20 to uniquely characterize a candidate signature. These features are global, geometrical, Transition & texture features, which mean they are based on the shape and dimensions of the signature image.
3.2.1 Global featuresThe signature is viewed as a whole and features are extracted from all the pixels confining the signature image. Based on the style of the signature, different types of Global features are extracted. Normalized area, aspect ratio maximum Histogram, Tri surface feature, no. of edge points, no. of cross points, no. of branch points are some of the global features that are extracted. These features are extracted as follows
Normalized Area of the Signature: The Normalized Area (NA) of the signature is the ratio of the area that makes up the signature to the area occupied by that signatures bounding box. This feature will provide us with information about the signature density. Equation (1) shows how the area is calculated.
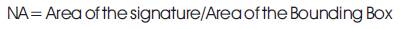
Aspect ratio: The Aspect Ratio (AR) is the ratio of the width of the image to the height of the image. The width and height measures are obtained from the width and the height of the signatures bounding box. This is done because the width and height of a person's signature may vary but the ratios of a person's signature will be approximately equal. Equation (2) is used to calculate the aspect ratio of each signature.

Maximum histograms: This feature is comprised of the maximum horizontal histogram and the maximum vertical histogram. The horizontal histogram is calculated by going through each row in the signature and counting the pixels in the row. The row with the highest number of pixels is the maximum horizontal histogram. For the vertical histogram the same concept applies. It is calculated by going through each column and the column with the most pixels is the maximum vertical histogram.
The Tri surface feature: Two visually different signatures may have same surface area. The tri surface area was implemented in an attempt to increase the accuracy of a feature describing the surface area. This is achieved by splitting the signature into three equal parts and obtaining the area for each of the three parts. Equation (1) can be applied to this feature. We apply it to each of the three areas the image has been split into. Each area is considered a bounding box and therefore we apply Equation (1) three times thus giving us three features.
Number of edge points: An edge point is a pixel which has only one neighbouring pixel in the 8- neighbour region. The feature that is added is the total number of edge points present on the signature. One step of preprocessing must be done in order to accurately obtain the edge points. An edge point is classified as having only one neighbour, therefore we must make sure the signature image is one pixel thick otherwise the edge points, in most cases, will be rounded and have more than one neighbour. This process is called Skeletonization. Once the image has been thinned, the obtaining of the edge points is a formality.
Number of cross points: Cross point is a signature point that has at least three 8-neighbors.
No. of Brach Points: Branch points are points where on Signature stroke bifurcates into two strokes.

Figure 4. The tri surface area
These features describe the characteristic geometry and topology of a signature and preserve their global as well as local properties. Geometrical features have the ability to tolerate with distortion, style variations, rotation variations and certain degree of translation. The following geometrical features are extracted
Perimeter
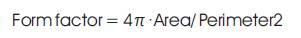
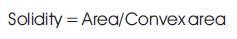
Major Axis length
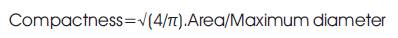
Texture analysis refers to the characterization of regions in an image by their texture content. Texture analysis attempts to quantify intuitive qualities described by terms such as rough, silky, or bumpy in the context of an image. In this case, the roughness or bumpiness refers to variations in the brightness values or gray levels.
3.2.4 Transition FeaturesThis is an important feature for the signature. Transition Features (TF) records the locations of transitions between foreground pixels and background pixels in a binary image, the foreground pixels being the 1's and the background pixels being the 0's. The image is traversed in the following four directions: left to right, right to left, top to bottom and bottom to top. Each time there is a change from '0' to '1' or a change from '1' to '0', is recorded, giving a total no. of transition counts.
Thus from the feature extraction phase we have a total of 20 signature features.
The next phase of the signature verification system is to train the neural network with the feature vector set for a given signature.
A set of 20 feature vector is extracted from each signature. This is fed as an input to the neural network. Various types of neural networks can be used for training.
The standard back propagation neural network classifier for verification is used. Standard back propagation is a gradient descent algorithm, as is the Widrow-Hoff learning rule, in which the network weights are moved along the negative of the gradient of the performance function. The term back propagation refers to the manner in which the gradient is computed for nonlinear multilayer networks. Typically, a new input leads to an output similar to the correct output for input vectors used in training which are same as the new input being presented. This generalization property makes it possible to train a network on a representative set of input/target pairs and get good results without training the network on all possible input/output pairs.
A separate network was trained for each individual signer in the database. However, to improve the resulting system's accuracy, negative examples (in the form of forgeries) are introduced into the training set (20 genuine and 20 forge).Without the use of negative examples it is difficult to obtain effective threshold values on the NN output, and the network is less likely to recognize a forgery. Ideally the negative examples would be skilled forgeries.
In this paper, a supervised training is used. For this purpose 'Adaptive Learning Rate (traingda) is used as a training function. Gradient descent with momentum weight and bias learning function (learngdm) is used by default. Mean Square Error (MSE) is network performance function. It measures the network's performance according to the mean of squared errors. All other parameters of the neural network are set as by default including the initial weights. The goal of training is to reduce MSE till the extent that it will meet the reference. The training will stop when either the set goal has achieved or the maximum number of epochs reached.
Multilayer feed forward artificial neural network for verification of off-line digitized signatures is used. The proposed NN consists of 20 input variables which are extracted from signature features, and it is designed to verify one signature at a time. Back propagation algorithm is used for training. A GUI is designed to make the verification result more transparent. The various steps incorporated during testing of the system are as follows
Figures 5 and 6 show test results for a given sample signature. Figure 5 shows the verification result when a genuine sample is presented to the system and figure 6 shows the verification result when a forge signature is presented to the system.
Verification Result when a forge sample is presented to the system.

Figure 5. Testing for Signature with Genuine Sample
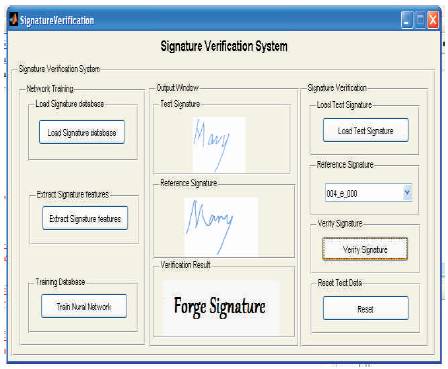
Figure 6. Testing for Signature with Forge Sample
For per formance evaluation of the proposed methodology we have used equal number of genuine and forgery samples for training and 40 numbers (20 Genuine + 20 Forgeries) are used for classification. For performance evaluation some common parameters like accuracy, FAR (False Acceptance Ratio) i.e. the percentage of forgeries accepted as genuine & FRR (False Rejection Ratio) i.e. the percentage of rejecting the genuine signatures are used. The achieved identification rate is 96% considering no noise conditions. The performance comparison of the proposed system with the existing systems is shown in Table 1.
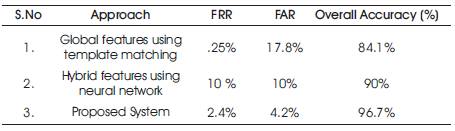
Table 1. Comparison of Proposed System with Existing Techniques
Signatures in offline systems are based completely only on the image of the signature. A novel approach for offline signature verification is proposed and implemented using a Back Propagation Neural Network algorithm. The proposed system is based on global, geometrical, texture and transition features. Features exhibiting good performance are considered, and finally a near-optimal solution using blend of such features in terms of high verification and time efficiency is derived. The system is tested against the genuine and the forged samples. The values of FAR and FRR are observed and these results look very promising. The performance of the system is satisfactory. However the system has to be tested on many more samples (obtained from real-life data from a bank or any other similar organization). Signature verification, on-line signature verification as well as non- English signature verification is required.