Figure 1. Watermarking System
In this research work, an algorithm has been developed for robust image processing using Discrete Cosine Transform (DCT) in Fuzzy Inference System (FIS) system. By altering the watermarking coefficient, a value is ascertained which has a better PSNR value leading to the development of a robust algorithm. The same algorithm can be applied universally to various images, whether they are in colour or black and white. The sensitivity of the perception of the eye towards light and colours in an image are narrowed down to three fields namely, luminescence, edge and contrast, which are used as inputs to the Mamdani type FIS subjected to a knowledge base. The watermark created is inserted over the weighted output received from the FIS output. High value of PSNR and low MSE brings out that the algorithm used for inserting the watermark is robust in nature. Using the Cox's algorithm, the watermark is taken out from the watermarked image. The watermarked image has been successfully transmitted over the VHF radio set held with the Indian Army. Due to the implementation of DCT for image processing, the original image has been compressed to a few kilobyte size for it to be successfully transmitted over the radio frequency.
Digital image processing (DIP) entails modifying the image characteristics in digital format through a computer. Digital image processing is primarily focused on developing a computerized system that can subject the image through various processes for various applications. The image is the input signal that is analysed by the system using effective algorithms giving output as an image. DIP has been firstly used in newspaper industry and it has been initially transmitted via submarine cables between London and New York (Shinde & Dani, 2012). Space applications, medical imaging, and industries are the most popular avenues of DIP. In colour image processing, each image consists of quadrants and each colour is specific to a particular position, i.e., single point in that quadrant. The characteristics modeled in the Hue Saturation Value (HSV) are similar or very close to the human interpretation (Agarwal et al., 2011; Agarwal & Mishra, 2010; Gonzalez et al., 2004; Jiansheng et al., 2009; Su et al., 1998). The work carried out in the literature has certain limitations associated with its application to only one single image in grey scale and the quality of the watermark extracted has been not of good quality.
Human Visual System (HVS) attributes are demonstrated utilizing Fuzzy back propagation (Fuzzy BP) system with the end goal of image watermarking (Agarwal et al., 2011). The Fuzzy BP system is prepared by inference rules containing three info HVS highlights specifically luminance sensitivity, edge sensitivity computed using threshold and contrast sensitivity computed using variance (Agarwal et al., 2011; Agarwal & Mishra, 2010). The Fuzzy BP system produces a solitary yield weighting element which is utilized to insert two unique watermarks:
The high figured estimation of PSNR parameter shows that the marked image has great discernible quality. The watermark is extricated from the marked image utilizing Cox's calculation. The existing algorithms used for embedding the image and extraction of watermark can be applied only to the single image resulting into a low quality of the extracted watermark. This paper will bring about the changes that have been made to the algorithm, thereby, resulting to a robust image processing using DCT in FIS system. The same has also been processed by subjecting the image to an artificial neural network and finally a comparison of both techniques has been done (Abraham, 2005; Mazandarani & Li, 2020; Meenpal et al., 2020; Ram, 2013; Van Viet & Van Hai, 2017).
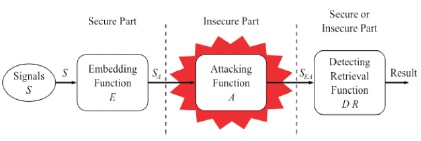
Watermarking using the computing process works by grouping of data containing the originators authorship for the sight and sound information. The watermark may be a logo, name or an arbitrary group. The plan is to keep the embedded signature extremely strong under any assault to the authenticity of the image. Inserting of the watermark in the picture could be performed in different ways for the basic watermarking system as shown in Figure 1 (Agarwal et al., 2011; Gonzalez et al., 2004; Su et al., 1998).

Figure 1. Watermarking System
The watermarking system comprises of two modules, i.e., inserting module and discovery and extraction module as shown in Figure 2 and Figure 3 (Agarwal & Mishra, 2010; Su et al., 1998).
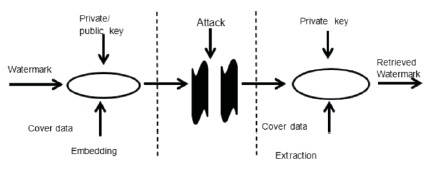
Figure 2. Process of Watermarking
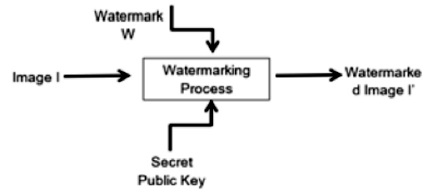
Figure 3. Simple Digital Watermarking
Watermark insertion and retrieval module is utilized to figure out if the information contains specified watermark or the watermark can be extracted. The module is shown in Figure 4 (Agarwal & Mishra, 2010; Cox et al., 1997; Singh & Chadha, 2013).
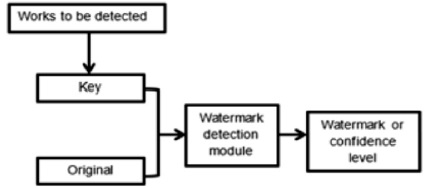
Figure 4. Watermark Insertion and Retrieval Module
Fuzzy inference is the process by which the input is subjected to a knowledge base used to make decisions or discern patterns and the output is mapped using fuzzy logic. Figure 5 depicts the entire process at once, from fuzzification all the way through defuzzification of the aggregate output (Gonzalez et al., 2004). Figure 6 shows the basic architecture of a Fuzzy Inference System (Abraham, 2005; Mazandarani & Li, 2020; Meenpal et al., 2020; Mohanty et al., 1999, 2000; Ram, 2013; Ramamurthy & Varadarajan, 2012; Van Viet & Van Hai, 2017).
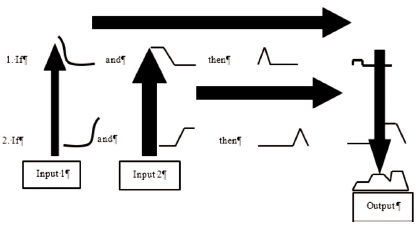
Figure 5. Fuzzy Flow Process
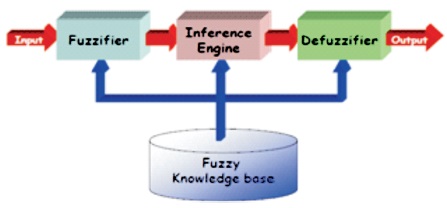
Figure 6. Architecture of FIS
Artificial Neural Network commonly known as neural networks has been developed using the human brain as the base model. The brain is a highly complex, nonlinear, and parallel computer (information-processing system). It organizes its structural conductors, known as neurons, to carry out certain computations at a faster rate. Artificial neurons are similar to the brain in two ways: they learn on their own to build up a knowledge base, and they have synaptic weights. The interneuron connection strengths of the neural network are employed to store the acquired knowledge (Gonzalez et al., 2004). Figure 7 shows the architecture of ANN consisting of the layers of ANN and Figure 8 shows how back-propagation in the hidden layers is used to reduce the error at the output.
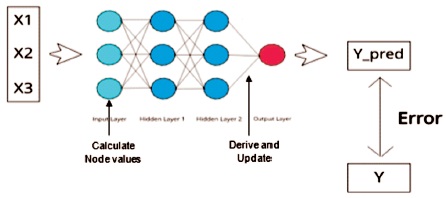
Figure 7. Architecture of ANN
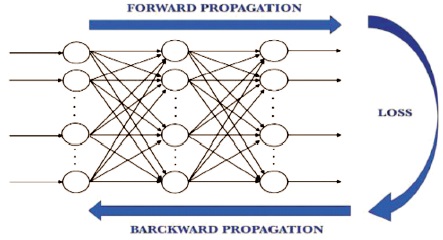
Figure 8. Back-Propagation in Hidden Layers
The methodology obtained has been finalized by developing different processes for insertion and extraction of the watermark from the image and the same has been simulated over MATLAB. The methodology of the proposed work is classified into the following categories. First is the processing of host image, secondly computing the HVS characteristics of the image and finally evolving the Fuzzy Inference System (FIS) (Cox et al., 1997).
Three HVS characteristics are calculated over these blocks as follows:
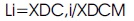
where XDC, i is the DC coefficient of the ith block and XDCM is the mean value of the DC coefficients of all the blocks.
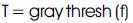
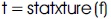
These three characteristics are fed as input to the Mamdani Fuzzy Inference System (FIS) readily available in the MATLAB tool box as shown in Figure 9 (Cox et al., 1997).
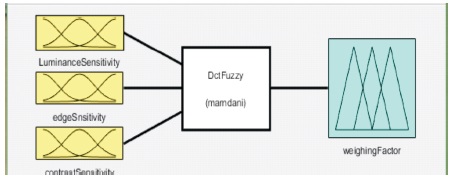
Figure 9. Mamdani FIS Tool Box in MATLAB
As per Table 1, the knowledge base used consists of set of 9 rules to get the weighted output, which is shown in Figure 10 in the form of a graph (Cox et al., 1997; Mohanty et al., 1999, 2000; Ramamurthy & Varadarajan, 2012).
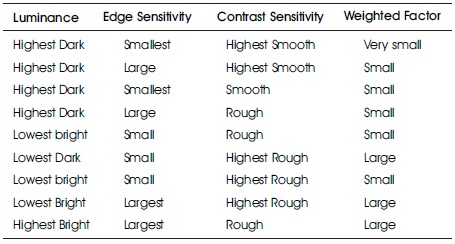
Table 1. Fuzzy Inference Rules used for Coding in MATLAB
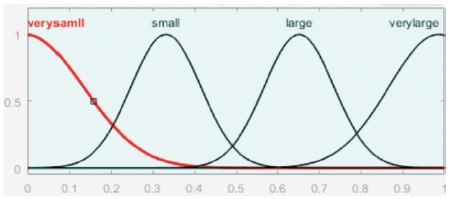
Figure 10. Weighted Output Result
The implementation process of digital watermarking is shown in Figure 11 and Figure 12.
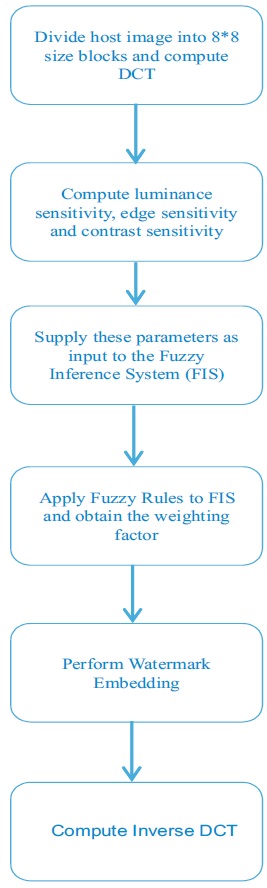
Figure 11. Watermark Embedding Process
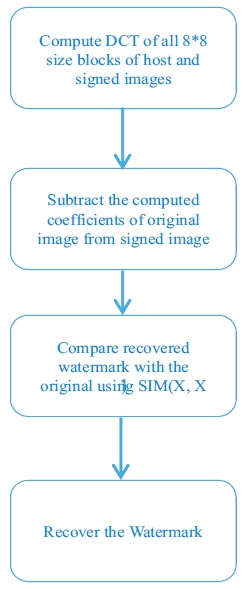
Figure 12. Watermark Extraction Process
The hardware components consist of rugged laptop computers at both the receiver and transmission end and the VHF radio sets used to transfer the image is as depicted in Figure 13. The image is compressed and watermarked using the algorithm designed and is then loaded onto the VHF radio set through external cables between the computer and the radio set. The size limit for transmitting images through the radio set is 1 MB, which is overcome by the compression technique of the algorithm to reduce the size to a few KBs. Both the receiver and the transmitter radio sets have been assigned individual IDs for setting up the communication link and the watermarked image is transmitted using a baud rate of 9.6 kbps. Successful transmissions and retrieval of the image fully validates the technique being used.
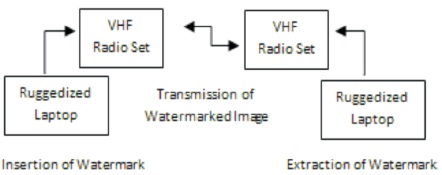
Figure 13. Hardware Setup for Transmission of Watermarked Image
As shown in Figure 14, SIM plot in MATLAB indicates a 46% similarity between the reference image and the image received after transmission.
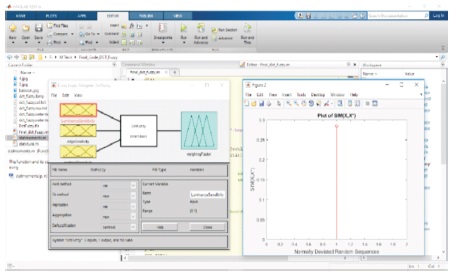
Figure 14. SSIM Plot
Figure 15 shows that the watermark retrieved and the watermark inserted before transmitting the image are the same. It can also be seen that both the random sequence corresponding to the watermark inserted and retrieved are the same.
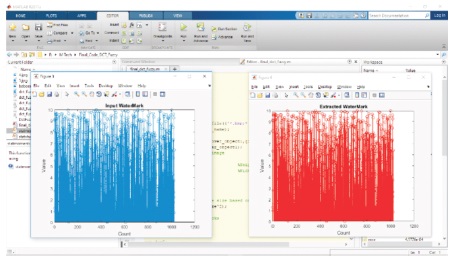
Figure 15. Input and Extracted Watermark
Figure 16 shows that the PSNR value of the watermarked image processed through the algorithm developed is better than the one that has been used in the base paper. Figure 17 and Table 2 gives the SSIM comparison between the two techniques.
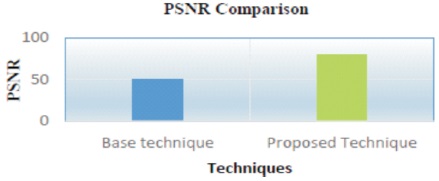
Figure 16. PSNR Comparison of Proposed Technique and Base Technique
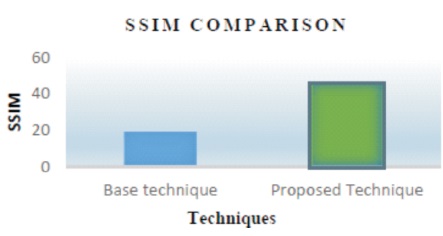
Figure 17. SSIM Comparison of Proposed Technique with Base Technique
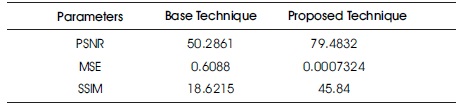
Table 2. Comparison of Base Technique with Proposed Technique on the Basis of Parameters
The algorithm has been subjected to different values of the watermarking scaling coefficient for which the different values are as tabulated in Table 3. It can be observed that for K=0.01 we get the highest value of PSNR.
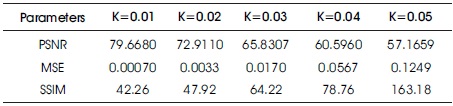
Table 3. Comparison of Different Watermarking Scaling Coefficients
Figure 18 indicates that FIS has a better PSNR value than ANN for the same parameters due to its low MSE value.
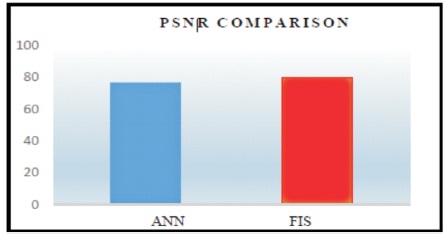
Figure 18. PSNR Comparison between ANN and FIS
During the hardware implementation part, the VHF radio sets at both the transmitter and receiver end are assigned individual IDs for identification during transmission and reception of the watermarked image, as shown in Figure 19.
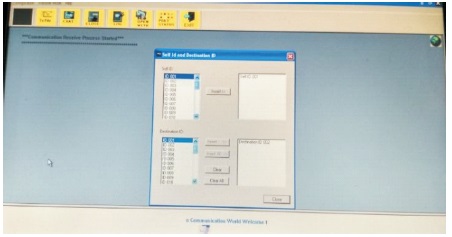
Figure 19. Assigning IDs to Both Transmitter and Receiver
As shown in Figure 20, the modes of transmitting the watermarked image is selected as either adaptive or repetitive mode each having its own unique time out duration.
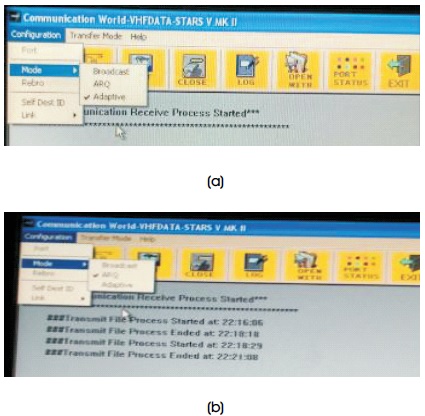
Figure 20. Selection of Transmission Mode (a) Adaptive, (b)Repetitive
As shown in Figure 21, the baud rate of 9.6 kbps is selected for ease of transmitting few kilo bytes size image, which also resulted in faster transmission of the image. Figure 22 shows the successful transmission of image between both, transmitter and receiver of the VHF radio sets.
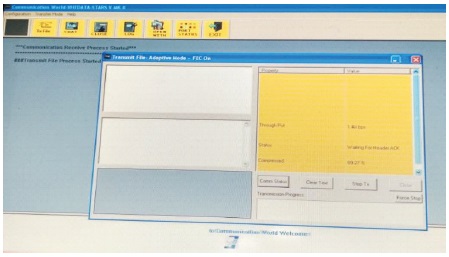
Figure 21. Transmission of File at 9.6 Kbps Baud Rate

Figure 22. Successful Transmission of Watermarked Image
The use of Fuzzy inference technique via the Artificial Neural Network to acquire an extracted watermark that is approximately 47% similar to the watermark transmitted is evident by the results. 9 sets of FIS have been used to compute the PSNR, MSE and SSIM components of the transmitted image. The algorithm proposed in this paper will enable to add another layer of security to the data being transmitted. It is similar to the method used in steganography with the slight modification of the data being imbedded as a stream of bits in the form of digital watermark which when replicated or extracted at the receiver end will yield a similarity of nearly 47% of the image used for insertion and a 100% recovery of the data that is being sent.