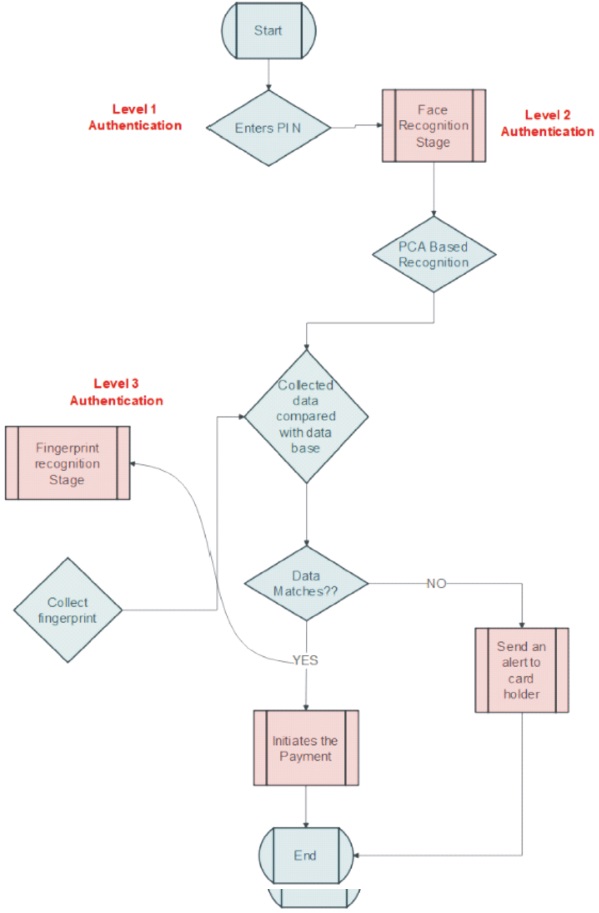
Figure 1. Block Diagram of Proposed System
Application of biometrics in computer security is nothing new and with the advancement of new age technologies, time has come that we make our ATM transactions more secured through biometric security processes. Currently, security of ATM transaction is based on card punch and PIN combination. This paper proposes a 3 layered security measure for ATM which may replace carrying today's plastic card. Starting with a PIN the proposed ATM system will apply face recognition as level two security measure and fingerprint recognition as level three security measure. Face recognition is the task of creating an identification of a face during a photo or video image against existing database. It begins with detection, then distinguishing human faces from other objects within the image, and then works on identification of the detected face. Fingerprint recognition is the process of determining a person's identity by examining their dermal ridges. It is economical technique and unique feature. This will help in making more informed choices, whether it's about determining motive, promoting deals, or avoiding security threats. The aim of this research is to develop an automatic face and fingerprint recognition system to reduce frauds while transacting with an ATM. The end result is an improved biometric ATM system, which will be a defensive strategy in the coming year and will increase consumer trust in the banking sector.
For several decades, banking has been done inside the bank which is difficult to both the customers and the bankers. Long queues, paper-based data and even the time taken to perform minor transactions can be exhausting. This is now been a thing of the past with the advent of the internet or having automated teller machines (ATM) in many places. The information age is quickly changing the way transactions are being completed. Everyday actions are increasingly being handled electronically instead of pen and paper or face to face communication. This growth in electronic transactions has resulted in a greater demand for quick and accurate user identification and authentication (Peter et al., 2011) and increase in security. Security has become a primary concern in order to provide protected transaction between the customer and the bank. With the introduction of ATM, banking became a lot easier in spite of having its own troubles of insecurity. Due to rapid increase in the number of cyber crimies, the ATM has become insecure (Dumbre et al., 2016). A customer holding a bank account can access the account from ATM by getting a PIN or password confidentially from bank or receive OTP (One Time Password) card holder mobile for a transaction. By inserting the ATM card into the machine and entering PIN number one can easily perform a transaction, (Malviya, 2014). Security has become a primary concern in order to provide protected transaction between the clients and the banking system. To overcome these security problems, we propose novel research idea. At level 1, cardholder need to enter their 6 digit PIN to start their transaction process and if the number matches with database then person will have access to level 2 authentication. The basic face recognition process can be defined as follows: A database consisting of the many captured images of known people, one inputs a current captured image, and therefore the main process is to verify or determine the identity of the person within the input image. Database holds information about a user's account details, mail-ID, images of his/her face and a mobile number which will improve security to a large extent. Fingerprint process can be stated as: Capturing the fingerprint and comparing it against data within database (Rathod et al., 2015).
First, the user will swipe the ATM card. At level 1 starting with entering PIN, a live image will be captured automatically through a webcam installed on the ATM. Image will be compared with the database in which card holder's images are stored. If it matches, it asks for person's fingerprint, if it also matches with database, ATM initiates the transaction. Or else an alert will be sent to the corresponding registered mobile number and even image will be sent to their respective email ID. Therefore, due to this proposed objective there are less chances of committing fraud and even this system increases confidence in customers regarding banking operations.
Benefits and limitations of biometric technology in banking sector has been discussed. Objective of the paper is to limit the frauds happening in banking. Security is a major concern in today's banking sector with the advent of technology such as internet and ATM. Principal Component Analysis (PCA) is used in face recognition system (Hemery et al., 2008), i.e. it captures variations in collection of images and use them for feature extraction or to compare individual faces images. Fisherface algorithm is used to separate one individual from the other so that no individual feature can dominate other person's features (Hemery et al., 2008).
In today's world face recognition technology is a very costly top secure applications. But still there are some issues like pose variance and false positives due to recognition algorithm which might make a mistake. So, to overcome these issues Peter et al. (2011) proposed a 3D head tracking technique i.e., the head will be represented as a 3D ellipsoid, which is tracked with a hierarchical particle filter based on colour histograms and shape information (Peter et al., 2011).
Face recognition technique is an enhanced safety approach for ATM. ATMs are more comfortable in accessing bank account from anywhere but even with the rapid growth of these electronic devices, a rise in insecurity is developed. There are no proper authentication methods in security during ATM transactions or in withdrawing money. Thus the research paper proposed a method in which security approaches of ATM are focused, biometric technique has been improved, i.e., face recognition from three angles have been proposed which can build customer confidence with the bank (Malviya, 2014).
Facial recognition helps in identifying faces captured in live webcam and chances of theft will be reduced. OTP helps users to free their mind in remembering their PIN as this random OTP acts as PIN (Karovaliya et al., 2015).
A model for user enrolment and authentication with an intrinsic character, i.e., fingerprint, is discussed in Fingerprints used for security enhancement of online banking authentication process. As a result, security will be improved (Lupu et al., 2015). A survey on fingerprint biometric recognition system discussed advanced techniques used by various authors in fingerprint recognition along with their performance improvement (Rathod et al., 2015).
Automated teller machine system with a combined RFID card, PIN, and electronic facial recognition using Raspberry pi to handle multiple accounts with same card was proposed. This system will solve the problem of account safety and make possible that the actual account holder alone could access the accounts (Dumbre et al., 2016).
Face recognition features saves every individual face captured and and uses it to make netbanking systems more secure for authentication purpose in banking-based security systems. By this proposed system cybercrimes can be brought under control and safety can be increased (Tambol et al., 2016).
Face recognition software identifies and authenticates the image of authorized user using MATLAB and then it stores image of a person who enters into unrestricted zone and compares it with the data of valid existing users. Iris scanner uses characteristics present in a person which is more secured in places like hospitals, immigration, etc. Palm vein technology recognizes palm vein pattern of an individual and compares it with data stored in database for authentication. This is the most accurate technique and hence we can say it is most secured for security purposes (Gusain et al., 2018).
The biometric authentication method is reviewed, as well as potential possibilities in the area. Options such as comparison and distinction between various methods, as well as their specific advantages and drawbacks, are highlighted (Bhattacharya et al., 2009).
Increased security at ATMs was briefly addressed, with the first level of authentication being PIN authentication and the second level being fingerprint authentication (Madara et al., 2017).
The review of biometric authentication systems covered all current biometric technologies as well as the difficulties that each one faces, such as pin authentication, passwords, and identity cards (Dharavath et al., 2014).
Over the last decade, there is a rapid growth in banking sector over internet or multimedia contents. Customers are more comfortable to initiate their transactions anywhere as it reduce the time. Due to this rapid growth, there is a chance of increase in frauds in banking sector. To overcome this problem biometric technology is introduced and this research focuses on multi factored biometric approaches.
Level 1 security PIN (Personal Identification Number) is the major and important source for anyone to complete their transactions successfully. As it is Level 1 security, it is recommended to choose a PIN which is longer and harder to guess. Level 2 authentication is face recognition, and it makes customers feel free as if any individual lost their card there is no need to worry about money in their account due to this biometric system. It stores every individual's image captured in database and only initiates the payment if it matches with cardholder. If any person forces cardholder to get into ATM and do payment, payment will not be initiated as only one person need to be present in ATM while making the transaction. With face recognition, there will be no passwords that hackers could hack. Even if hackers stole your photo database, it would be of little use, as there will be unique nodal points and they cannot be same in face masks. Coming to next level security, i.e., fingerprint recognition, as dermal edges of individual person are unique. The results of fingerprint recognition will be accurate. It is one of the most economic technique and widely used in digital forensics. Compared to other biometrics fingerprint recognition, this requires less storage space.
The proposed system consists PIN authentication, PCA based face recognition, fingerprint recognition and an ATM. The block diagram of the proposed system is shown in Figure 1. In this system, first it asks person to enter their 6 digit PIN and then if it succeeded at the next level it detects the face of the user who is trying to make any transaction and recognize whether the user is fake or not by matching the face stored in database. Once the face is recognized, further process is carried out which includes fingerprint authentication and further transactions (Dumbre et al., 2016).

Figure 1. Block Diagram of Proposed System
It is a four or six digit number used to unlock bank account assigned to a person. It works as level 1 authentication. The data required for this authentication will be stored in a PVV (PIN verification value) validation file in bank's card processing and management system and during the transactions the PIN which we enter will be checked in server side through PVV.
The first step is capturing face image of a person present before ATM. This can be done using a still or video camera. Then face image is passed to the recognition software for recognition/detection. The work flow of face recognition is given in Figure 2.
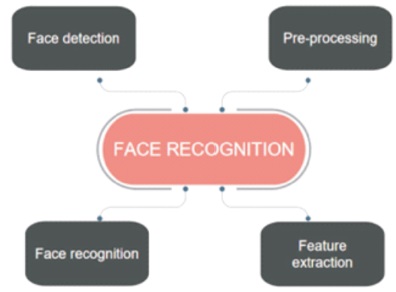
Figure 2. Work Flow of Face Recognition
Image pre-processing is used to improve image data and it ignores the unnecessary information/data and obtains important image features for further processing. Here, the data/image that system captures need to be converted into normalized format, i.e., images collected should be of same resolution, brightness. This would normally involve a number of steps like normalizing the face image, assuring that images are of same brightness, colour and resolution. Then, creating a 'template' of 'print' to be compared to those in the database (Peter et al., 2011).
The steps to be taken are:
Feature extraction is a process that identifies important attributes of the data and divides them into more manageable groups. So, by partitioning this data into groups it will be easier when we want to process them. PCA (Principal Component Analysis) feature extraction is used in our proposed system.
After data pre-processing and extraction completes we move further with either machine learning architecture or deep learning architecture.
This is the actual process of matching unique data features to each individual. The face recognition system locates the head and the eyes of the individual images captured; a matrix is then developed based on the characteristics of the individual's face as shown in Figure 3. There are 80 nodal points on a human face, and also few nodal points (red dots) that are measured by the software (Peter et al., 2011). It compares the collected images with its database and if they are recognized in data base it initiates the transactions.
Face recognition techniques are divided into two types:
Appearance based uses holistic texture features and is applied to either entire face or only to the specific regions in face image. Feature based uses geometric facial features (mouth, eyes, nose, etc.) and geometric relationships between them (Karovaliya et al., 2015).
PCA is a common feature extraction used in image processing/face recognition. It is used to build eigen faces, which ordered from largest to lowest. Eigen faces having larger eigen value finds greater variance and possiblity as compared to those having less eigenvalue.
Time taken for computation is very less as it considers only the essential components from images while it gets training. It considers multiple images of different expressions under different lightening conditions based on given input (Karovaliya et al., 2015).
Fingerprint allows a person to verify their identity by comparing his or her finger dermal ridges. It is one of the oldest and first techniques under digital forensics. As finger prints are unique there is no chance of fraud happening. The work flow of fingerprint recognition is given in Figure 4. Fingerprint recognition requires a fingerprint scanner. It can also be called either as verification system or identification system.
A verification system checks a person's identity by capturing their fingerprint and comparing it with templates stored in the database. It is based on one-to-one comparison to determine and after comparison, claims whether identity is true or not.
An identification system, generally takes place after verification, i.e., verified fingerprints will be compared with individual by searching the entire template database for a match. It is based on one-to-many comparisons and claims the identity of the individual.
The first step is to capture fingerprint of the person and check it with database containing fingerprints of every individual. If fingerprint matches further transaction takes place.
Biometric system provides the high-end security. It relies on the physical characteristics which are unique. Biometric provides a strong security and link between a customer and bank unlike other authentications like passwords or PIN. Frauds can be controlled as ID cards can be stolen or passwords can be hacked but these physical attributes which are unique cannot be stolen or hacked. This paper have reviewed facial recognition techniques and fingerprint recognition work flow. In addition, it also discussed about techniques used in image processing (PCA). Image pre-processing steps are discussed. Enhanced approach of banking through facial and fingerprint recognition can be used to make netbanking systems more secure.