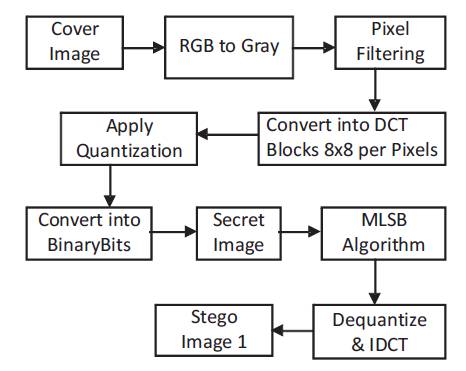
Figure 1. Block Diagram of Steganography Process of First Level
Steganography is the process of hiding information in a carrier in order to provide the secrecy of text, music, audio and images. It can be defined as the study of imperceptible communication that deals with the ways of concealing the existence of communicating messages. For hiding secret information in various file formats, there exists a large variety of Steganographic techniques where some are more complex than others and all of them have respective strong and weak points. The aim of the paper is to provide the user, a comparative analysis of the first and second level steganography using the MLSB embedding technique in various types of file formats as the cover image like JPEG, BMP, PNG, etc. With the help of results obtained, the best format for both the levels of hiding can be concluded. The secret image used is also taken of all different formats so that a conclusion can be drawn that which type of format is suitable for the cover as well as secret image.
Digital images have become an important part of the internet and major communication media as it connects different part of the world. In this era, everyone wants secrecy of the data and uses many secure ways to protect the information while transferring and sharing it, but it is not safe [1]. There are two techniques which share the information over the digital images in a concealed manner, viz. Steganography and Cryptography [7]. Steganography is a powerful security provider, particularly when it is combined with some digital images, it hides the existence of the image itself, which is hidden, however cryptography is a technique which focuses on keeping the existence of a message secret [13]. Image Steganography is the technique of hiding the information over cover image [12]. There are many types of image file formats in which data can be concealed by various hiding methods of Steganography. The objective of paper is to provide a graphical analysis of different file formats of image with MLSB hiding method. The paper also gives a comparison between the results of image obtained at the first and second level and the whole work is performed on transforming domain.
Various papers have been studied based on Steganography over digital images, and on the basis of the papers reviewed, it is obtained that ELSB, MLSB are better to hide secret image as compared to RLSB and simple LSB technique as they are easier to detect [12] . Edge adaptive scheme can be applied which can select the embedding regions according to the size of secret image which helps to enhance the security [3]. A method is proposed which uses two cover images as host images with one secret image to increase the security in the receiver side when sending each host image alone in different times one after one [11]. Secret data bit is very small size in 8*8, 32*32 bits giving poor results in value of PSNR [6]. Most commonly used file formats are BMP, JPEG, but both the formats are not suitable for hiding in each other [5].
To overcome the secrecy problems, the new algorithm is implemented based on the least significant bit embedding algorithm (LSB) for hiding secret messages in the edges of the image with random selections. A comparative analysis is made by using other file format of images like, .tiff, .png, .tiff. Level of security is increased by hiding the secret image at 2 levels with increased PSNR of more than 60Db. Size of the secret image is not limited. The block diagram of the 1st level is shown in Figure1, where firstly, the cover image is converted into gray color image and after that the pixel values of the cover image are filtered and the pixels are converted to their DCT coefficients in 8*8 matrix form per pixel. The values are then quantized and the coefficients are converted into binary values. The negative coefficients are given as “0” while the positive are given as “1”, now the secret image is hidden in LSB of the cover image binary bits by the help of MLSB algorithm and again the inverse DCT and dequantization is applied to get back the coefficients of cover image back and thus finally, the stego image of the 1st level Steganography is obtained.

Figure 1. Block Diagram of Steganography Process of First Level
In the second level of Steganography, the stego image1 obtained at the first level of Steganography is taken as cover image and the same technique of embedding is applied again as done in the first level where RGB to gray conversion is done followed by filtering and quantizing the pixel values and this is converted to binary coefficients. The second secret image is embedded in it by applying the MLSB technique and atleast the second level of Steganographic image as the stego image2 is obtained as shown in Figure 2.
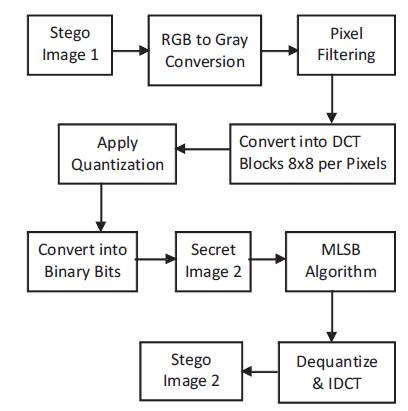
Figure 2. Block Diagram of Steganography Process of Second Level
Steganography techniques are broadly classified on the cover image file used and the secret information embedded in it either by lossless or lossy compression. The types of Steganography techniques used in the proposed method are mentioned below.
One of the best techniques in substitution is to hide information in the Least Significant Bit (LSB) of the digital image. In this method, the embedding is done by replacing the least significant bits of image pixels with the bits of secret data. The LSB is a kind of STO (Security Through Obscurity) which is defined as a belief that a system of any kind can be secure as long as none outside the implementation group is allowed to find out anything about its internal mechanism [9].

Figure 3. Block Diagram of MLSB Technique
In Transform technique, the secret message is embedded in the frequency coefficients of the cover image. An extra work added to this technique as compared to substitution is that after changing the values of binary frequency coefficients, Discrete Cosine Transformation are also calculated and then the secret information is embedded [2]. Figure 4 shows the steps involved during the transform technique.
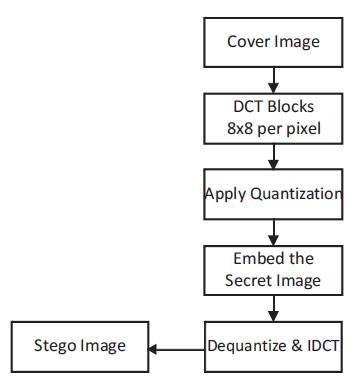
Figure 4. Block Diagram of DCT Technique
Steganography can be classified into different types based upon the cover medium used. In ancient times, the data or information was protected by hiding it behind wax, stomach of rabbits, the scalp of the slaves, etc, but in today's era due to rapid growth in technology, people can transmit data by hiding it in the form of a text, image, and video, or audio [10]. In this project, the authors consider image as a secret file.
It is one of the most popular techniques used in Steganography, which uses pixel intensity values for hiding of the information [14]. In digital Steganography, the secrecy of data is more in case of images as the person can notice only the transmission of image, but cannot guess the existence of any hidden data over the image [8]. There are several types of images with different file formats like BMP, JPEG, TIFF, GIF, and PNG. The difference between their properties can be understood by the help of comparison table given in Table 1.
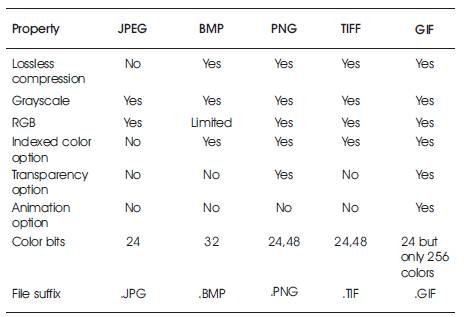
Table 1. Comparison of Different File Formats of Digital Images
The Images are of different file formats like JPEG, TIFF, BMP, PNG, GIF and all formats differ from one another in different aspects. Parameters have been calculated by taking each individual format with one another. So that it can be concluded that which is the best format to hide our information by giving a better quality of result. Table 1 shows the Comparison of Different File Formats of Digital Images.
In this project work, the results shown in Figure 5 are obtained using Matlab software by hiding the image over an image for all formats by using LSB replacement technique together with the cosine transform coefficients obtained after applying quantization.

Figure 5. Image Hidden Over an Image (a) Stego Image of 1st Level, (b) Secret Image for 2nd Level, (c) Stego Image of 2nd Level
The results of MSE shown in Figure 7 conclude that the .BMP, .JPEG and .PNG formats of stego image as a cover image are better to hide in the 2nd level as they are having the lesser value for MSE. & .BMP & .GIF and this can be concluded as the best format taken for the 2nd secret image.
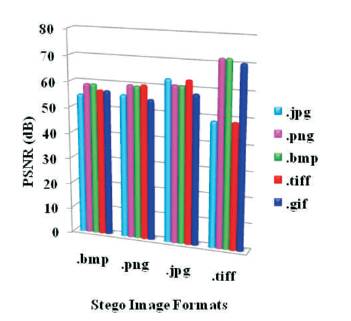
Figure 6. Comparison of PSNR of Different File Formats of Digital Images in 2nd level
The results of PSNR shown in Figure 6 conclude that the .TIFF, .JPEG formats of the stego image are better cover images to hide in the 2nd level as they are having the higher value for PSNR. &. BMP and can be concluded as the best format taken for the 2nd secret image.

Figure 7. Comparison of MSE of Different File Formats of Digital Images in 2nd level
Overall from both the graphs, it can be concluded that the bmp and png formats as a cover image in all types of file formats of secret image except the jpeg in bmp file is better to hide the data as its PSNR & MSE ratios are good, that is, PSNR are having higher values than the MSE lesser st value. The future work will on comparison between the 1st level and the 2nd level results & trying if the 3rd level of Steganography is possible or not.