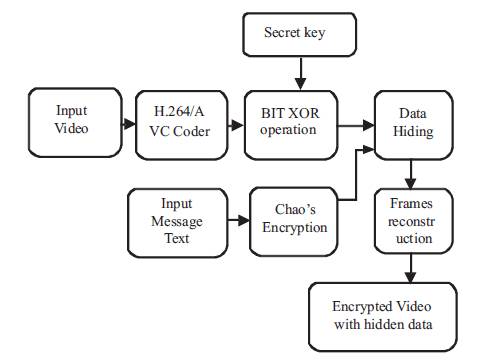
Figure 1. Block diagram of the Video Encryption and Data Hiding
The large size of video data makes it desirable to be stored and processed in the cloud. To provide security and privacy for the data in the cloud, the video data must be stored in encrypted form. It is also necessary to perform data hiding to avoid the leakage of video content. This paper proposes a novel method of embedding additional data in H.264/AVC video bit streams to meet the privacy preserving requirements of cloud data management. This method proposes three processes namely: H.264/AVC video encryption, Embedding of encrypted data and extraction of original data. Depending upon the property of H.264/AVC codec, the code words of I- frames and P-frames are encrypted with stream ciphers. The data to be embedded into the encrypted video is also encrypted by Chaos encryption technique and hidden into the video by bit replacement method. Data extraction is done both in encrypted domain and in decrypted domain. Experimental results show that the proposed method preserves file size, whereas degradation in video quality caused by data embedding is less.
With the rapid development of the Internet, the security of information has become one of the most important matter of concern in communication and information technology. Due to the large size of video data and high computational requirement for processing the video content, it is necessary to store and process the videos in the cloud. But, the cloud services are prone to many attacks and are vulnerable to untrustworthy system administrators. so it is desirable to access the data in the encrypted domain. Data hiding is performed in videos to avoid the leakage of video content and to verify the integrity of the data.
Cryptography was created to provide security for communication. In order to keep the message content secret, a number of methods have been developed for encryption and decryption of the data. But sometimes, keeping the contents of a message secret is not enough. It is also required to keep the existence of message secret. Steganography is the art of hiding the information in other information to provide invisible communication. The purpose of steganography is to hide the very presence of communication where as the purpose of cryptography is to make communication unintelligible to those who are not intended for the communication. The strength of steganography can be increased by combining it with cryptography.
For applying encryption and data hiding techniques to videos, it is needed to know the research issues and challenges in secure video processing [1]. The state-ofthe- art algorithms for analysis, retrieval and protection of multimedia content are described in [2]. Erkin et al [3] provided an overview of related cryptographic primitives and some applications of secure signal processing in data analysis and content protection. Sadeghi presented a solution to the problem of privacy preserving face recognition in [4]. Recently, some reversible data hiding techniques in encrypted images have been presented in [5]-[8] and these techniques work on uncompressed images only. These methods mainly focused on data hiding in images. Obviously, it is not possible to implement the existing data hiding algorithms to videos. No report on implementation of data hiding in encrypted H.264/AVC video streams exist. Only some joint data hiding and encryption techniques that work on videos have been reported.
A commutative video marketing and encryption scheme based on H.264/AVC codec is presented in [10]. The Intra- Prediction Mode (IPM), Motion Vector Differences (MVD) and Discrete Cosine Transform (DCT) coefficients' signs are encrypted and DCT coefficients' amplitudes are watermarked during compression process. This process is not suitable for real time applications as it is a time consuming process. A novel scheme [11], which combines encryption and watermarking techniques, to provide access right and authentication of video content is reported. The IPMs of luminance block and sign bits of MVDs are used for encryption and IPM is used for watermarking. The watermarked stream is not format compliant and it may result in system crashing. A method to embed data into H.264/AVC bitstream directly is proposed in [14]. But it can't be implemented in the encrypted domain.
Due to the increasing demand for providing security and privacy to video content, it is desirable to develop a new data hiding algorithm that works on encrypted videos. There are some challenges for hiding the data in compressed and encrypted bitstreams. The first challenge has been to find out the best steganographic technique so that the bitstreams after encryption should maintain format compliance. Second challenge is to make sure that the decrypted videos with hidden data look like original video. Third challenge is to preserve the file size. Fourth challenge is to extract the data correctly from both the encrypted video bit stream and the decrypted video bit stream, so that the proposed system can work for two different practical applications.
This paper proposes a system with a novel method to embed encrypted data into encrypted compressed bitstreams. At first, the code words of IPMs and the code words of MVDs are encrypted, by using the property of H.264/AVC codec. Here the secret data is not embedded directly into the frame. The secret data is encrypted by Chaos encryption scheme and then it is embedded into the frame by bit replacement technique
The rest of paper is organized as follows. Section 1 describes about the proposed scheme that includes the explanation about H.264/AVC encryption, embedding of encrypted data and extraction of secret data. Experimental results are discussed in Section 2 and conclusions are drawn in Section 3.
At the sender side, the input video is compressed and encrypted by H.264/AVC codec. Then the secret data is hidden into the selected frame, after encrypting it by Chaos encryption method. One can embed the data without knowing the video content. At the receiver side, the hidden data is extracted by applying the key and then the video is reconstructed after decrypting the frames. The video encryption and data hiding is shown in Figure 1 and data extraction and video decryption is shows in Figure 2.

Figure 1. Block diagram of the Video Encryption and Data Hiding
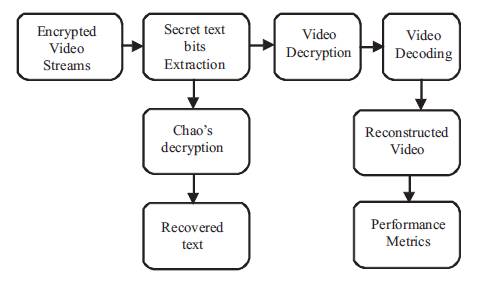
Figure 2. Block diagram of the Data Extraction and Video Decryption
Frame separation is the first step in any video processing algorithm. The frame separation purpose is to make the video into consecutive images, so that image processing tools can be applied easily. This can be processed by subsequent steps. Initially, an input video is converted into still images for processing and to detect the moving objects. These sequences of images are collected from video files by finding the information. These frames are converted into images. The converted frames from an input video are shown in Figure 3 and Figure 4. Then the video frames are encrypted using the properties of H.264/AVC compression standard and the data is encrypted using Chaos encryption method. Finally, the encrypted data is embedded into the encrypted video frames.

Figure 3. Separated frames for Input Man Walking Video

Figure 4. Separated frames for Input Air Craft Video
H.264 divides the sequence of video frames into several group of pictures (GOPs). The coding process of H.264 is shows in Figure 5. The video frames are labeled as Intra (I), Predicted (P) and Bi-directionally predicted (B) frames. At the source end, each frame is divided into non overlapping blocks of uniform size (i.e.16×16 pixels) called macro blocks. These macro blocks are handled uniquely depending on their types. Each macro block can be further divided into smaller blocks with 4×4 being the smallest possible block size. These macro blocks are subjected to wavelet transform, quantization, and entropy coding. First, the pixel values in a macro block are used in the wavelet transform and quantization process. The quantized coefficients are further utilized for dequantization and inverse wavelet transform process for prediction and motion estimation purposes.
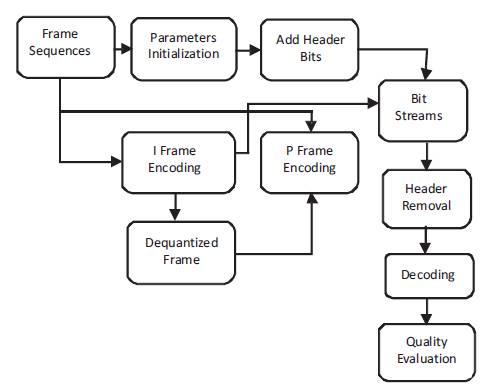
Figure 5. H 264 Coding Process
In I-frame, the pixel values in a block are either coded directly by using coefficients in the transformed domain or predicted (i.e. intra-prediction) using neighboring blocks in the same frame to exploit the spatial redundancies within a frame. In P-frame, motion estimation (i.e. interprediction) between two frames can be implemented to take advantage of the temporal redundancies. For that, the previously encoded frame, which itself is a motion compensated frame, is decoded and its prediction errors, if any, are decoded and added to the decoded frame for motion estimation purposes.
The process of encryption of video bitstreams is shows in Figure 6. The coded pixel values of each block are encrypted by performing XOR operation between the bit streams and a random binary string. The same process is repeated for all the frames to get the encrypted frames. The encrypted compressed frames are shown in Figure 7 and Figure 8. All the encrypted frames are reconstructed to form the encrypted video.
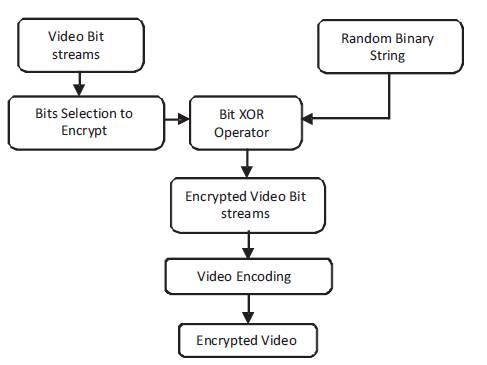
Figure 6. Video Bits Encryption
Figure 7. Encrypted compressed Frames of Man Walking video

Figure 8. Encrypted compressed Frames of Air Craft Video
The data encryption method is one of the advanced encryption standards for encrypting the information to provide secure transmission. This method can facilitate the discovery of some essential information and establish the crucial stage of security. The advantage of chaotic encryption is High level security. A chaotic sequence is generated using the equation Xn+1=u*x(1-x) by taking u = 3.9999; x = 0.40000565. An encryption key value is generated from the sequence using the threshold function (I/255) < Xn+1<(I+1)/255. Bit XOR operation is performed between the ASCII values of the original text and the encryption key value. This method is very efficient to transmit the secret message securely even through the unsecure channels also. It prevents data hacking. The flowchart of Chaos encryption method is shown in Figure 9.
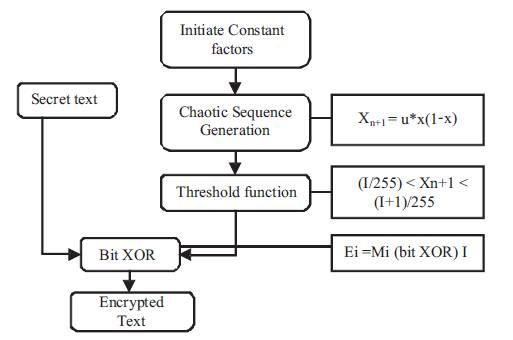
Figure 9. Chaos Encryption Flow Chart
In [12]-[13], the data is embedded directly into H.264/AVC bitstreams. But they cannot work for encrypted domain. Here, the hiding is performed after encrypting the data with Chaos encryption scheme to make second level security during transmission. The bit XOR operation is performed between video bit streams and the chaotic sequence generated by the chaotic process using some threshold function. Bits wrap method is used here to conceal secret text bits under encrypted compressed bit streams. It is performed using logical bitwise operations like 'bit and' and 'bit or' operations. After hiding the data, the encrypted frames are reconstructed to form an encrypted video with hidden data.
At this stage, Secret hidden text messages are extracted from encrypted video streams followed by reconstruction of video frames. Hidden text bits are extracted using bitwise logical operators from the specific bit locations and the extraction of desired number of bits will be performed by using logical bitwise operators called 'bit and' and 'bit or'. Finally all extracted message characters are applied to chaos decryption module to decrypt the data with symmetric keys. Then the video bit streams are decoded using H.264 decoder to reconstruct each encoded frame and all the frames are concatenated to form recovered original video. Video quality will be measured using some parameters such as PSNR, MSE and Compression Ratio etc.
The proposed method for data hiding in encrypted compressed video is implemented in MATLAB. The quality of the encrypted data and video using the proposed method are validated through the performance parameters like Mean Square Error (MSE) and Peak Signal to Noise Ratio (PSNR). The MSE between the original image 'f' and the reconstructed image 'g' at decoder is defined as:
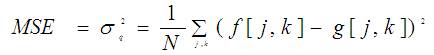
Where the sum over j, k denotes the sum over all pixels in the image and N is the number of pixels in each image. From that the peak signal-to-noise ratio (PSNR) is defined as the ratio between signal variance and reconstruction error variance. The PSNR between two images having 8 bits per pixel in terms of decibels (dBs) is given by:
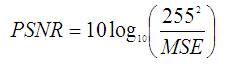
In general, if PSNR is 40 dB or greater, then the original and the reconstructed images are virtually indistinguishable by human eyes. The MSE and PSNR are calculated for the aircraft video and man walking videos with data hidden without encryption and with encryption. The calculated MSE and PSNR values are given in Table 1 and Table 2 respectively.
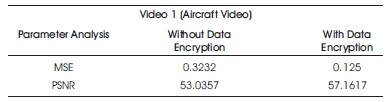
Table 1. MSE and PSNR values for Air Craft Video
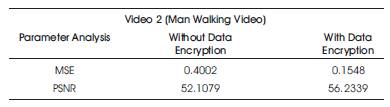
Table 2. MSE and PSNR values for Man Walking Video
The graphical representation of MSE and PSNR of the two video are shows in Figure 10 and Figure 11 respectively. From Figure 10, it is clear that the error is small when the data is hidden in encrypted form. From Figure 11, it is concluded that the PSNR is high for the system with Chaos data encryption. Hence the noise is reduced by hiding the encrypted data.
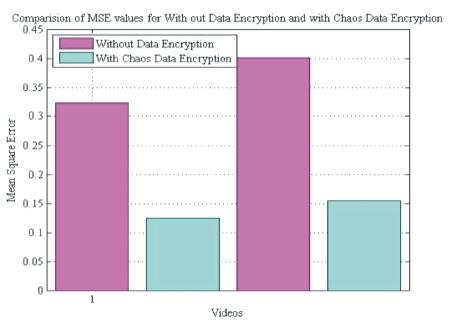
Figure 10. Comparison of MSE without data encryption and with Chaos data encryption
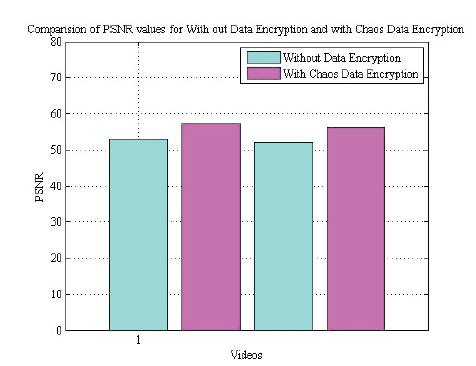
Figure 11. Comparison of PSNR without data encryption and with Chaos data encryption
The paper presents the encryption of compressed video bit streams and hiding privacy information into the bit streams to protect videos during transmission or cloud storage. In the proposed method, H.264 video coding standard is used to compress monochrome video effectively with better reduced bit rates. Chaos encryption was used to encrypt/decrypt secret text data before/after data embedding/extraction. Bits replacement method was used to embed secret message bits with compressed bit streams to prevent the video from being tampered. At the receiver, the secret data is extracted by using the Chaos encryption key, and then the video frames are decrypted and reconstructed to form original video. Finally the simulated results show that the proposed methodologies gives better bitrates, high PSNR and high structure similarity index values with more compatibility.