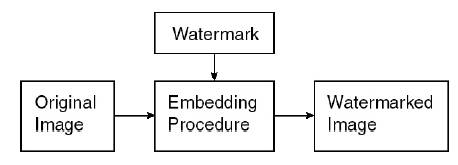
Figure 1. General watermarking method
An adaptive visible/invisible watermarking scheme is done to prevent the privacy and preserving copyright protection of digital data using Hadamard transform based on the scaling factor of the image. The value of scaling factor depends on the control parameter. The scaling factor is calculated to embed the watermark. Depending upon the control parameter, the visible and invisible watermarking is determined. The proposed Hadamard Transform Domain Method is more robust again image/signal processing attacks. Furthermore, it also shows that the proposed method confirm the efficiency through various performance analysis and experimental results.
With the popularity of Internet communications and the development of multimedia technology, digital media can be easily duplicated, distributed and tampered. Copyright protection and content authentication are the problem faced by the digital media. Digital watermarking technique provides an approach to deal with these problems. Watermarking is the process of inserting data into a multimedia element such as an image, audio, or video file. The embedded data can be identified or extracted from the multimedia for identifying the copyright owner. An effective watermarking scheme should meet certain requirements including transparency, robustness, security, un-ambiguity, adequate information capacity, low computational complexity, etc. Figure 1. shows the General watermarking method Watermarking can be of two types, Visible Watermarking and Invisible Watermarking.
A visible watermark is a visible semi-transparent text or image overlaid on the original image. An invisible watermark is which that cannot be perceived with human's eyes when the image is embedded.

Figure 1. General watermarking method
Digital Watermarking mainly involves two phases- Watermark embedding, and Watermark extraction. Digital watermark can be classified into two classes depending on the domain of watermark embeddingspatial domain and transform domain. In the transform domain the properties of the underlying domain can be exploited.
The transform domain scheme has typically more robustness towards noise, common image processing, and compression when compared with the spatial transform scheme. The two most commonly used methods are Discrete Cosine Transform (DCT), Discrete Wavelet Transform (DWT), Discrete Fourier Transform, Hadamard Transform etc., Hadamard transform is considered as the one of the best method, because transformation matrix is always represented in + 1 and -1. The processing time is reduced in this method since it uses only addition and subtraction operation. It has a good energy compaction property and its transformation matrix could be generated using fast algorithms and hence it is called Fast Hadamard Transform (FHT).
In proposed system, adaptive visible/invisible watermarking scheme for digital images is done through hadamard transform by calculating scaling factor. The value of the scaling factor is based on control parameter. It can be adjusted to make the watermark scheme as either visible or invisible.
This work consists of four modules,
The Hadamard transform (also known as the Walsh–Hadamard transform) is orthogonal transformation that decomposes a signal into a set of orthogonal, rectangular waveforms called Walsh-Hadamard transform(Figure 2). It is a non-sinusoidal signal. The 2DHadamard transform is mainly used in image processing and image compression applications.
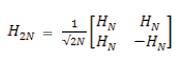
The advantages of Hadamard transform include
(i) Its elements are real.
(ii) Its rows and columns are orthogonal to each other. Let [I] represent the original image and [I’] is the transformed image then the 2D – Hadamard transform of [I] is given by
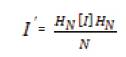
After the Hadamard transform, watermark is embedded based on the scaling factor of the cover image Table 1 gives the calculated scaling factor for sample cover images. The cover image to be protected or to be watermarked is transformed into frequency components using Hadamard transform technique.
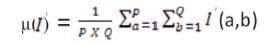
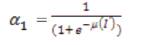
The α can be acquired by multiplying it with inverse multiples of 10 as given in α. The watermarking scheme is determined by the controlling parameter m and it can take the values from 0 onwards and controls the strength of scaling factor.
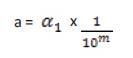
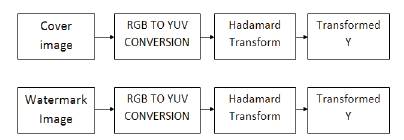
Figure 2. Process of Hadamard Transform
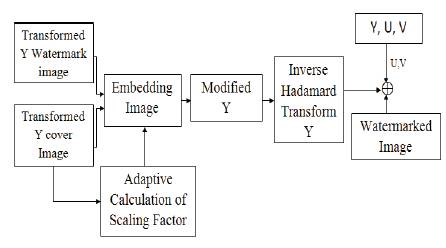
Figure 3. Watermark embedding process
Figure 3 shows the Watermark Embedding Process. For m=0 the watermark dominates the cover image and destroys the underlying image quality heavily(Figure 8). For m=1 the visibility of the watermark is good without destroying the underlying content(Figure 9). For m=2 the watermark becomes invisible without degrading the quality of underlying digital image(Figure 10).
An attack can be defined as unauthorised modification or seizing of confidential information on an image. These are different types of watermarking attacks.
The noise attack is implemented by changing the density of salt & pepper noise and Gaussian noise. Salt and pepper noise is a form of noise that is present in images. White and black pixels appear randomly. It is also called as impulse noise. This noise can be caused by sharp and sudden disturbances in the image signals.
The cropping attack is implemented by removing the central portion of the watermarked image because for any image, most of the important information is centrally located.
Rotation operation is considered as geometric attack. In general, an image on rotation increases its size depending on the angle of rotation. In order to keep the size of an image fixed, the rotated image undergoes some loss of data.
Other attacks that are performed are jpg compression, median filtering, translation low and high pass filtering. The various attack results of NCC values are tested with the extracted watermark, and it is shown in Table 3.
The given original cover image and watermarked image are taken as input and converted into YUV color space.Hadamard transformation technique is applied on the luminance channel of cover image and watermarked image. Hadamard transformed cover image is used to calculate the scaling factor and watermark is extracted. Figure 4 shows the Watermark extraction process and Figure 5 shows the Watermark image.
The performance for an adaptive visible/invisible watermarking scheme have been evaluated and compared on the basis of two measures: Peak Signal to Noise Ratio (PSNR), Normalized Correlation Coefficient (NCC),and they are computed as follows
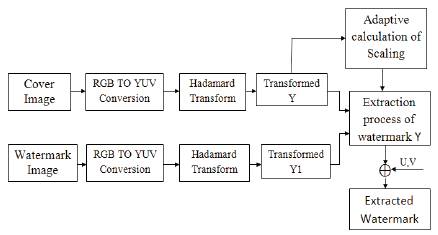
Figure 4. Watermark extraction Process
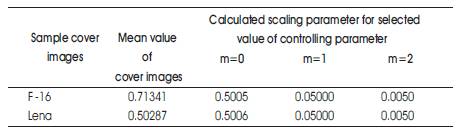
Table 1. Calculated scaling factor for sample cover images
The Peak Signal-to-Noise Ratio (PSNR) is a statistical measure of the ratio between the original image and the modified or distorted image in decibels. The root mean square error (RMSE) between original image I and watermarked images I’ is calculated using RMSE and substituted in PSNR to calculate peak signal to noise ratio.
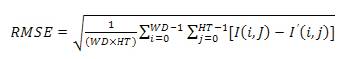
Where, WD and HT are width and height of the cover image respectively.
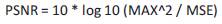
For the different sample cover images PSNR value is calculated and compared with yang et al.'s method (Figure 6). Table 2 gives the comparison of PSNR values for Lena image with existing work.
In order to show the similarity between the extracted watermark and the original watermark, the NCC is used as a metric. The equation to calculate NCC is given by NCC in which W (i, j) and W (i,j) represent the original and extracted watermark respectively. The value of NCC ranges between 0 and 1. For two identical images, NCC value is equivalent to 1 indicating the perfect similarity between them, whereas 0 indicates no similarity between them. Figure 7 shows the comparison of NCC values
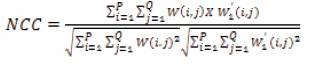

Figure 5. Watermark image
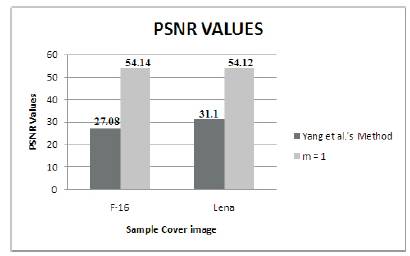
Figure 6. Obtained PSNR value for different sample values and compared with yang et al's method.
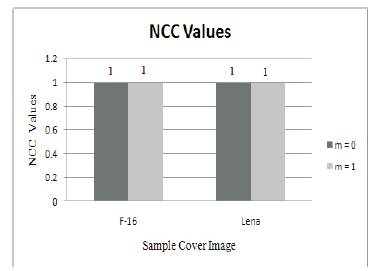
Figure 7. Comparison of NCC values
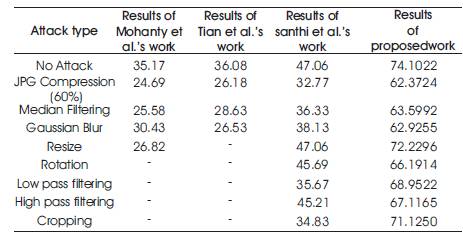
Table 2. Comparison of PSNR values for Lena image with existing work
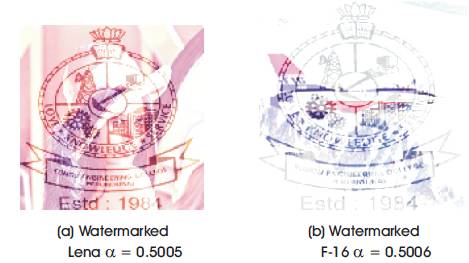
Figure 8. Watermark sample images for controlling parameter for m=0

Figure 9. Watermark sample images for controlling parameter for m=1

Figure 10. Watermark sample images for controlling parameter for m=2
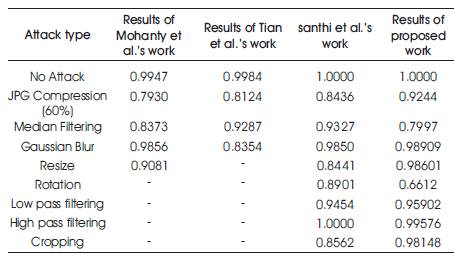
Table 3. Comparison of NCC values between original and extracted watermark from Lena image.
Experimental and performance analysis results are given in detail in Tables 1,2 and 3 and Figures 6,7,8,9 and 10. The proposed work is implemented on Intel dual core with 1GB RAM configured using MATLAB R2012a.The most c ommonly used test images are taken for experimentation.
An adaptive watermarking method based on embedding and extracting a digital watermark into/from an image is done using a hadamard transform. Hadamard transform is mainly used for its robustness against image processing attacks. In this method an adaptive procedure for calculating scaling factor or scaling strength is used in hadamard transform. The scaling factor value is controlled by a control parameter. As per the users' requirements the inserted watermark may be either visible/invisible based on the control parameter. The results are compared with the existing system. The proposed scheme confirms the efficiency by the experimental result and performance analysis.