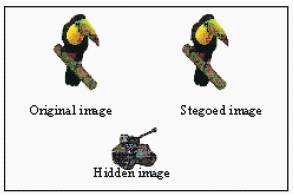
Figure 1 Steganography using image
Many steganographic techniques are extremely vulnerable to attacks, and even detection of the information in the image file is quite easy. So a microcontroller is used for the sake of security where it transmits a pre-programmed password at the beginning of each process. The steganalysis algorithm continued only if the received password is correct at the destination, otherwise retrieving the secure information from the cover image is impossible.
Steganography is the art and science of communicating in a way which hides the existence of the communication. In contrast to cryptography, where the "enemy" is allowed to detect, intercept and modify messages without being able to violate certain security premises guaranteed by a cryptosystem, the goal of steganography is to hide messages inside other "harmless" messages in a way that does not allow any "enemy" to even detect that there is a second secret message present. Steganography is in (especially military) literature also referred to as transmission security or short TRANSEC.
A good steganography system should fulfill the same requirements posed by the "Keirckhoff principle" in cryptography. This means that the security of the system has to be based on the assumption that the "enemy" has full knowledge of the design and implementation details of the steganographic system. The only missing information for the "enemy", is a short easily exchangeable random number sequence and the secret key. Without the secret key, the "enemy", should not have the slightest chance of even becoming suspicious that on an obser ved communicat ion channel , hidden communication might take place.
The word steganography derives its origin from the Greek word “steganos”, which means covered or secret, and “graphy ” which means writing or drawing [4]. Steganography is also called stego in short. It is also known as data hiding or information hiding. Modern day steganography can be defined as hiding one message into another. The word steganography, unfortunately, could not yet admit itself to most English dictionaries; the latest version Microsoft® Office Word 2003 does not have steganography in its dictionary.
The concept of steganography has existed for thousands of years. Greeks used to pass secret information by writing in wax-covered tablets: wax was first scraped off a tablet, the secret message was written on the tablet, and then the tablet was covered again with the wax [4]. Another technique was to shave a messenger's head, tattoo a message or image on the bald head, and let hair grow again so that the tattoo could not be seen. Shaving the head again revealed the tattoo [4]. The use of invisible inks was also used extensively during the World War II [4]. An innocent letter contained secret information written between the lines in invisible ink, made with lemon juice, milk, urine, or some other chemical compounds. The invisible secret message gets revealed when heated. During the same time, the Germans invented the microdot technology [4]. The microdots were photographs of the size of a printed period, containing text, drawing, or photograph [4]. Large amounts of information could be transmitted with this technology.
Computer technology and the Internet have made a breakthrough in the transmission of information. It has also opened a whole new way of applying steganography using computer technology. Secret information can be hidden in computer image files (jpeg, gif, bmp), audio files (wav, mp3), video files (mpeg, avi), or even text files. To the person who do not have the knowledge about the file containing hidden information, it looks perfectly normal. A stegoed image, even along with the original image, if given to an average person, he would be unable to tell any difference between the two.Provided the steganographic algorithm is good enough, and the original image is not available, even an adept steganography expert would be unable to tell if an image contains hidden information. Making use of the Internet, secret information hidden in the carrier can be transmitted quickly, secretly, and securely.
Steganography is not an alternative to cryptography. In cryptography, data is turned into unintelligible form. However, it can be easily detected, even though the data itself cannot be turned into intelligible form easily without the encryption keys and the encryption algorithm. Cryptographic text easily raises suspicion that some secret information is being transmitted. Steganography, rather than obfuscating the data, hides the data itself. A message, encrypted and then stegoed, gives two layers of security instead of one. The sender can deny the transmission of any cryptographic text at all.
The practice of steganography is termed a dark art and illegal by some people. Allegations are made that stego, coupled with crypto, are the perfect technologies for terrorists exchanging information for planning activities similar to the 9/11 incident. It must be realized that technology can be used for both good and bad. Dynamites can be used to blow up buildings killing innocent people, or it can be used to blow up a wall to rescue someone trapped behind the wall. If steganography is illegal, so is an M-16 or AK-47.
Figure 1 shows three images, the image labeled stegoed image contains the hidden image. It is impossible to tell the difference between the original image and the stegoed image by looking at the images.

Figure 1 Steganography using image
Steganography is closely related to the problem of "hidden channels" in secure operating system design[6], a term which refers to all communication paths that cannot easily be restricted by access control mechanisms (e.g. two processes that communicate by modulating and measuring the CPU load). Steganography is also closely related to spread spectrum radio transmission, a technique that allows to receive radio signals that are over 100 times weaker than the atmospheric background noise, as well as TEMPEST, techniques which analyze RF transmissions of computer and communication equipment in order to get access to secret information handled by these systems.
Most communication channels like telephone lines and radio broadcasts transmit signals which are always accompanied by some kind of noise. This noise can be replaced by a secret signal that has been transformed into a form that is indistinguishable from noise without knowledge of a secret key, and in this way, the secret signal can be transmitted undetectable.
This basic design principle of steganographic systems, i.e. replacing high entropy noise with a high entropy secret transmission, is quite obvious. There have been a number of simple software tools published, for e.g. hiding files in the least significant bits of digital images or for transforming PGP messages into files resembling pure random byte sequences.
However really good steganography is much more difficult and usage of most of the currently available steganographic tools might be quite easily detected using sufficiently careful analysis of the transmitted data. The noise on analog systems has a large number of properties very characteristic to the channel and the equipment used in the communication system. A good steganographic system has to observe the channel, has to build a model of the type of noise which is present and has then to adapt the parameters of its own encoding algorithms so that the noise replacement fits the model parameters of the noise on the channel as well as possible. Whether the steganographic system is really secure depends on whether the "enemy" has a more sophisticated model of the noise on the channel than the one used in the steganographic system.
Common communication systems have a huge number of characteristics and only a small fraction of what looks like noise can actually be replaced by the statistically very clean noise of a cryptographic ciphertext. Noise in communication systems is often created by modulation, quantization and signal cross-over and is heavily influenced by these mechanisms and in addition by all kinds of filters, echo cancellation units, data format converters, etc. Many steganographic systems have to work in noisy environments and consequently require synchronization and forward error correction mechanisms that also have to be undetectable as long as the secret key is unknown.
To implement a good steganography that prevents the hacking of secure information by the “enemy” from the steganographic image, a new technique is applied that gives two ways security (two passwords) before the steganography process begin. So that even if the “hacker” or “enemy” knows the steganography algorithm, he would be unable to detect or retrieve the secure information hidden in any carrier media. The steganography and desteganography process is controlled by a programmed microcontroller such that the user who is having the microcontroller device can only perform encryption and decryption operations of the steganography. It needs two passwords; one of the passwords is query from the computer, and the second one is from microcontroller. If both the password matches exactly, then only the encryption and decryption of the steganography is possible.
The use of the microcontroller has made the system secure, so that it is essential to have the hardware for steganography and de-steganography process. The microprocessor is connected to the computer through the serial port using UART, and then the UART internally in the computer communicate through a level converter (MAX 232) to the USART of the microcontroller, through asynchronous mode of operation.
The microcontroller is connected to the computer by a D-type 9 pin connector to the COM port. The overall block diagram is as shown in the Figure .
As shown in the figure 2.1 above, the microcontroller block consists of PIC microcontroller, along with the power supply unit and the level converter IC. The microcontroller is programmed as to send the password whenever required through USART to the computer. The power supply unit consists of a 9v transformer, and a bridge rectifier, to convert AC to DC along with a capacitor (to avoid ripple). Using a voltage regulator (IC 7805) the 9v is reduced to constant 5v supply, which is fed to the microcontroller (Vcc). The output of the level converter (here max 232 level converter IC) is fed to one of the communication port of the computer.
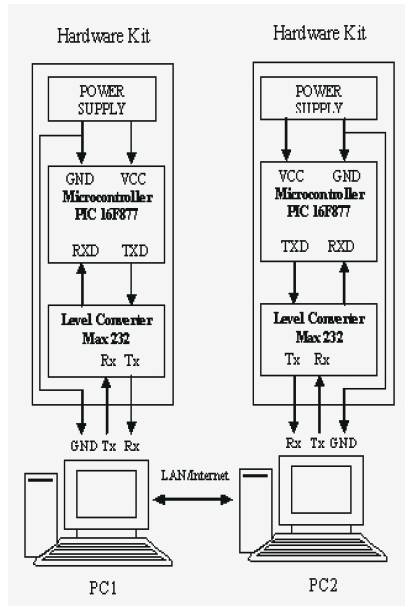
Figure 2.1 Microcontroller And Computer Interfacing
The main objective of the use of the hardware is only the person who is having the above mentioned hardware can de-steganize.
The PC0 and PD1 pins of the microcontroller are the transmit and the receive pins from the USART[5]. The output from the microcontroller is in the range of 0 volts and 5 volts for logic 0 and logic 1 respectively. But according to the hardware specification of the computer the optimum range should be 10v and +10v for logic 0 and logic 1 respectively in the serial port, and vice versa, i.e. converting back to the microcontroller range from the COM port range.
The circuit diagram for the hardware is given in Figure 2.2. The 4 capacitors in the MAX232 act as the charge pumps.
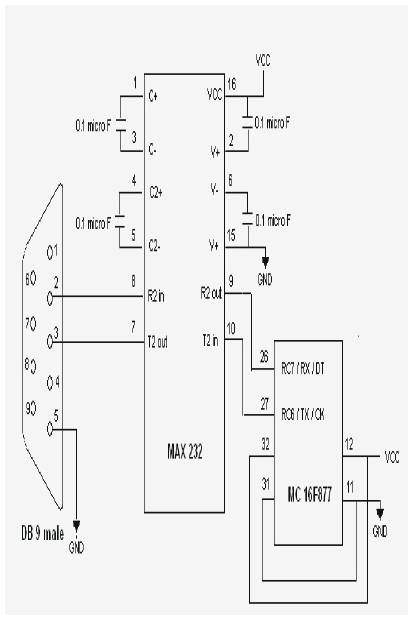
Figure 2.2 circuit diagram for the hardware
The Vcc and ground to the microcontroller are provided from the power supply.
The DB 9 is fixed to the communication port of the computer. Care should be taken to know to which port we are connecting the pin. If we connect to COM0 port, then in the SETCOM function, in the C editor, we have to change the base address to 3F8, else if connected to COM1 port, it should be changed to 2F8.
Image steganography is about exploiting the limited powers of the human visual system (HVS). Within reason, any plain text, cipher text, other images, or anything that can be embedded in a bit stream can be hidden in an image. Image steganography has come quite far in recent years with the development of fast, powerful graphical computers, and steganographic software is now readily available over the internet for everyday users.
When applying LSB techniques to each byte of a 24-bit image, three bit can be encoded into each pixel (as each pixel is represented by three bytes). Any changes in the pixel bits will be indiscernible to the human eye. For example, the letter 'A' can be hidden in three pixels. Assume that the original three pixels are represented by the three 24-bit words below:

Figure 2.3 Three pixels of an Image represented by three bytes
The binary value for the letter A is [10000011]. Inserting the binary value of 'A' into the three pixels, starting from the top left byte, would result in:

Figure 2.4 Three pixels of an Image represented by three bytes after embedding the binary value of 'A’
The emphasized bits are the only bits that are actually changed. The main advantage of LSB insertion is that data can be hidden in the least and second to least bits and still the human eye would be unable to notice it. The below figure shows the block diagram of embedding the data inside an LSB of a 24-bit Pixel.
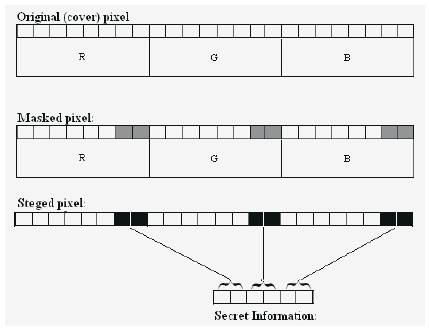
Figure 2.5 The block diagram of embedding the data inside an LSB of a 24-bit Pixel.
Steganography can provide all the aforementioned entities with increased protection for security information. Here the hardware kit with microcontroller gives external security for steganize and de-steganize algorithms. So once we steganize the secure information into a cover media using this hardware kit, to de-steganize the same cover media at a destination, the user must have the similar hardware kit to retrieve the secure information. And the user must know the two passwords, one which is stored in the microcontroller and another one used during steganography. User without having this hardware kit can't proceed to steganography application and hence gives better security not only to the information hiding but also for steganography algorithm.