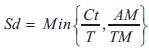
The cognitive behavior based on the cognitive science model for the network nodes to benefit the Quality of Service rerouting is designed. A Quality of Service rerouting protocol oriented to cognitive network is proposed. Rerouting is a distributed protocol where the route search is in a hop by hop way. Inspired by the small-world phenomenon, the experiential route information is collected and stored at each node to benefit the future route selection. The authors implement and evaluate Quality of Service rerouting in NS2 platform. Its performance is compared with another two popular routing protocols. The results show that Cognitive Rerouting has achieved remarkable performance improvements over the protocols where no cognitive behaviours are exploited.
Nowadays, the users have high-end demand of the network services which are far beyond the scope of the traditional data service. The spatial and temporal complexity of the network has worsened due to the everlasting expansion of the Internet. With the rapid development in networking technologies, the next generation networks are expected to provide real-time, secure, reliable, and high-quality services to the users. The connections to the Internet should be available anytime anywhere. Since the network is not aware of its own states and requirements, the network management becomes an extremely difficult task. However, if the network elements can intelligently adapt to the operations, the increased complexity can be alleviated without much extra resource consumption. Reliability, security, scalability and Quality-of-Service have become key issues as we envision the future Internet. In recent years, the cognition concept has been applied to various network and communication systems. Two new terms were created to reflect the new technologies, i.e., cognitive radio and cognitive network. In papers [1], [2], [3], authors have proposed new network architecture called Cognitive Packet Networks (CPN). CPN makes use of adaptive techniques to seek out routes based on user defined Quality-of-Service criteria. Smart packet routing is carried out using a reinforcement learning (RL) algorithm [4]based on Random Neural Networks. In 2005, the research on cognitive radio was greatly pushed forward by integrating it into the wireless communication system [5]. The cognitive network originated from the concept of knowledge plane [6]. The cognitive process makes decisions by analyzing the incomplete information. The cognitive network aims to eliminate the constraints imposed to the current network. It can sense the conditions of the current network, and then plan, decide, and act on those conditions [7]. The cognitive science has brought new features to the renovation of traditional network protocols. In the cognitive network, we should exploit these features to design meaningful cognitive behaviors for enhancing the scalability, self-adaptivity and self-protection of the network. In this paper, we investigate the Quality-of-Service routing and rerouting problem [8]in the context of cognitive network environment. Referring to the brain model [9], the research on the cognitive network mainly focuses on cognitive radio which deals with dynamic management of spectrum resources. The cognitive radio has been applied to the practical wireless communication system. Research interests have been drawn on the cross-layer optimization and design in cognitive radio network. In the cross-layer approach, the information is shared among multiple layers instead of only between two neighboring layers as in the traditional layered approach. In [11], a distributed cross-layer optimization algorithm is proposed for a multihop cognitive radio network with joint consideration of power control, scheduling, and routing at three different layers. The cognitive cycle has been integrated into the design of novel network architecture to improve the network capabilities in self-adaptation, selfmanagement and self-optimization. In [12], a new concept of reconfigurable node is developed by applying the cognitive cycle to the node design. Crosslayer design is achieved by the stack manager which collects the information of the current configuration and the configurable free components. In [13], the system architecture of cognitive network is designed based on the cognitive cycle. Distributed learning and reasoning is used to optimize the network operations. The island genetic algorithm is applied to optimize the channel assignment in the dynamic spectrum access. The primary objective of Quality-of-Service routing [14] is to select the transmission path which satisfies the Quality-of-Service requirements of the application. A few works have been done to address Quality-of-Service routing with the help of artificial intelligence or cognitive science. In [15], the reinforcement learning approach is integrated into the cross-layer design to improve the Ad hoc On-Demand Distance Vector protocol in wireless mesh networks. The protocol has the learning capability. However, how to process the Quality-of-Service information has not been considered. In [16], a nature-inspired Quality-of-Service routing algorithm is proposed, which uses artificial agents to search the best routing paths and optimize the resource utilization of the whole network. In [17], intelligent optimization methods are employed to find Quality-of- Service routes with diverse objectives and constraints. In [18], inspired by chemotaxis, reaction-diffusion and quorum sensing biological processes, survivability-related routing algorithms are developed. In the Internet, the topology also exhibits the small-world phenomenon mainly due to the degree variability and the local connection preference of nodes [19]. In the autonomous system level topology, the small-world phenomenon is caused by the highly variable node degrees. In the router level topology, the local connection preference of nodes contributes significantly to the small-world phenomenon. In the Internet, the small-world phenomenon has revealed two findings, i.e., the short chains exist and they can be identified. When the network exhibits certain topologies, the local information can help find the short chains efficiently. The findings have inspired the distributed routing in the message delivery from the message holder to its direct interactors The message holder needs three kinds of information [20]. The information about the local interactors, the information about the destinations, and the information about long-distance interactors and their location. The above information provides guideline for the design of the routing protocol. In this paper, the authors use the small-world phenomenon to optimize the distributed routing design. They design the cognitive behaviors for the network nodes in the proposed protocol named as Cognitive Rerouting. Performance evaluation shows that the new rerouting mechanisms have remarkable advantages over the current routing mechanisms. The cognitive network model is designed by exploiting the idea of knowledge plane. The model can be represented as a directed connected graph G(V, E) where V is the set of nodes representing the routers in the network and E is the set of edges representing the links in the network. For each router, an additional knowledge plane is added into its protocol architecture. We utilize the cognitive behaviours derived from the cognitive cycle and the layered reference model of brain to design the knowledge plane, thereby improving the network performance.
To address Quality-of-Service routing comprehensively, we consider as many Quality-of-Service parameters as possible in our model. For each link, we consider its total bandwidth, available bandwidth, delay, and error rate. For each node, we consider its delay, delay jitter, error rate, and stability degree. To simplify the problem, a node's delay, delay jitter, and error rate are combined with the related Quality-of-Service parameters on its adjacent links. In the search of Quality-of-Service routing paths, we should consider the current load status of the nodes. The stability degree Sd is a novel Quality-of-Service parameter to represents it. If the load of one node is too heavy, the routing path should bypass it. The stability degree Sd of the node is defined as:
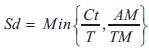
Where Ct is the available CPU cycles, T is the toal CPU cycles, AM is the available memory, and TM is the total memory. Large values of Sd are expected. The user's requirements refer to the Quality-of-Service parameters specified by the user. The authors classify the network applications into different categories based on the DiffServ model [21]. Each application category is supported by a certain set of Quality-of-Service parameters. The mapping relationship is formulated by ITU-T G.1010 [22]. Since in practice the Quality-of-Service requirements could not be a fixed value, they represent them by intervals. Consider the set of application types as:
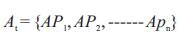
Each application type is associated with a set of Qualityof- Service requirements. For example, for APi, the set of Quality-of-Service requirements is denoted as:
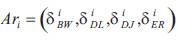 "
"
Among Ar , bandwidth, delay, delay jitter, and error rate i requirements are represented by intervals
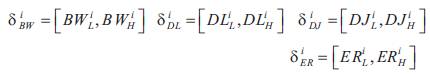
respectively. Four different service levels are provided for each application type such as for level-1, bandwidth
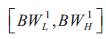 Delay
Delay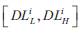 , Delay Jitter
, Delay Jitter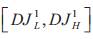 ,error rate
,error rate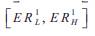
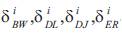
Each Quality-of-Service parameter requirement is represented by an interval value instead of a single value.
In terms of the bandwidth, the user always expects to get the largest value. Consider the bandwidth requirement
interval as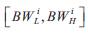 When the actual bandwidth of a routing path is BWp , the user's bandwidth satisfaction degree function BWsd is defined as in equations (2).
When the actual bandwidth of a routing path is BWp , the user's bandwidth satisfaction degree function BWsd is defined as in equations (2).
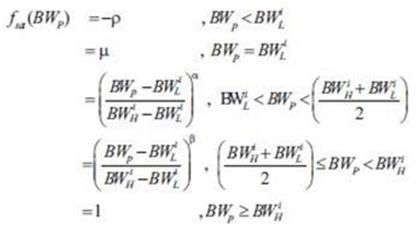
Where α > 1 , 0 < β <1, μ is a very small positive integer, and ρ is a penalty value. The penalty value will be applied only when the user's Quality-of-Service request cannot be satisfied even at the lower bound of the interval. With the increase of BWp , the user's Quality-of-Service satisfaction degree also gradually increases.
In terms of the delay, the user always expects to get the
smallest value. We denote the delay requirement interval
as 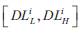 When the actual delay of the routing path is DLρ , the user's delay satisfaction degree function is
defined as in equations (3).
When the actual delay of the routing path is DLρ , the user's delay satisfaction degree function is
defined as in equations (3).
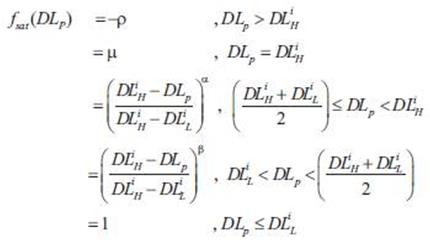
Where 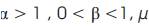 ,is a very small positive integer,
and ρ is a penalty value. With the increase of p dl , the
user's Quality-of-Service satisfaction degree gradually
decreases.
,is a very small positive integer,
and ρ is a penalty value. With the increase of p dl , the
user's Quality-of-Service satisfaction degree gradually
decreases.
The cost refers to the resources spent by the network service provider on the service provision. It is a relatively stable value which can be calculated easily. The bandwidth cost is not only associated with the amount of bandwidth occupied but also related to the number of links occupied. Therefore, to further save resources, the network service provider prefers selecting the routing path with fewer links. The authors denote per unit time per unit bandwidth cost as cb The actual bandwidth assigned to a link is denoted as ubw. The total bandwidth cost of the routing path is calculated as shown in equation (4).
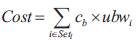
Where Setl represents the set of links belonging to the routing path. Pricing refers to the procedure of setting charge rules for the usage. By considering the time and application factors, they propose the following pricing strategy as shown in Table 1.

Table 1. Pricing Strategies
Equation (5) shows the price of leve j service in type i application within time slot t .
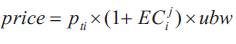
Equation (6) shows the user utility and equation (7) shows the network service provider utility, respectively.
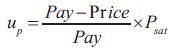
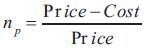
The path evaluation standard is to maximize both the user utility and the network service provider utility. the path evaluation metric is shown in equation (8).
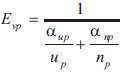
Where αup ,αnp represent the weights of the user utility and the network service provider utility to the path evaluation metric, respectively. 0< α up, αnp< 1, αup,+ αnp =1. Large value of Evp is always expected.
Consider the Quality-of-Ser vice routing request as 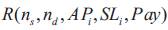 .
Where ns is source node nd is
destination node, APi represents the application type
requested by the user, SLi represents the service level
requested by the user, and Pay represents the upper limit
cost that the user is willing to pay. The Quality-of-Service routing request aims to find a routing path Psd from ns to nd . The path should support Quality-of-Service at service level
SLm iof application type Api . The path cost should not be
greater than Pay. The objective of Quality-of-Service
routing problem is to maximize the user utility, the network
service provider utility, and their summation under the
Quality-of-Service constraints. The mathematical model
of Quality-of-Service routing problem is described as
below equations (9 -16).
.
Where ns is source node nd is
destination node, APi represents the application type
requested by the user, SLi represents the service level
requested by the user, and Pay represents the upper limit
cost that the user is willing to pay. The Quality-of-Service routing request aims to find a routing path Psd from ns to nd . The path should support Quality-of-Service at service level
SLm iof application type Api . The path cost should not be
greater than Pay. The objective of Quality-of-Service
routing problem is to maximize the user utility, the network
service provider utility, and their summation under the
Quality-of-Service constraints. The mathematical model
of Quality-of-Service routing problem is described as
below equations (9 -16).
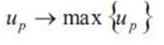
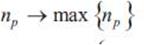
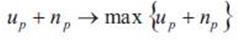
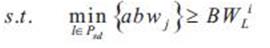
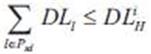
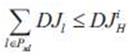
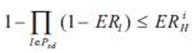
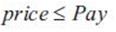
To design a cognitive network, we need to design cognitive behaviors for the network nodes. These behaviors are reflected in the newly added knowledge plane and supported by the memory. The memory stores both the topology information and the experiential information accumulated during the protocol running. In the following, the authors develop primary cognitive behaviors for routing and rerouting.
Through the sensation behavior, each node maintains two tables, i.e., the table of neighbour information and the table of link information. They are shown in Table 2 and Table 3, respectively.

Table 2. Neighbour Information

Table 3. Link Information
To adapt to the dynamic changes of the network, the routing protocol should work in a distributed way. During the protocol running, the path probing procedure exchanges the control messages which contain partial topology information. The sense of spatiality is a procedure mainly for collecting useful topology information from the probing packets. The collected topology information is stored by the format shown in Table 4.

Table 4. Topology Information
The memorization behavior adds the experiential route information into the memory. The experiential route information is used to speed up the path probing procedure. Once a path satisfying the user's Quality-of- Service requirements has been found, the control packets will travel back to the source node along the discovered path. Meanwhile, all the intermediate nodes are recorded. Each visited intermediate node memorizes the indicated experiential route from itself to the destination. The experiential route memorized by the source node is actually the complete path discovered between the source node and the destination node. The rationale is that these paths can be directly used when the same routing requests arrive next time. The experiential routes have the format shown in Table 5. The table is updated when new information arrives.

Table 5. Information of Experiential Route Section
When links or nodes become invalid, the maintenance procedure is triggered to update the topology information. In our design, the learning focuses on the maintenance of the experiential routes. The variation intervals of their Quality-of-Service parameter values are estimated and provided as reference for future use. The authors use the interval estimation method in the standard normal distribution to estimate the variation intervals of bandwidth, delay, delay jitter, and error rate. Before an experiential route is used, a probing procedure is triggered to obtain the actual Quality-of-Service parameter value of this routing path. The actual value helps estimate the variation interval of the corresponding Quality-of-Service parameter. Formula 17 shows the calculation method.

Where 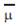 is the expectation of the parameter value, S is the
standard deviation of the parameter value, and t1-α/2 is
the value of t distribution with confidence level α . The
above estimation method applies to the bandwidth,
delay, delay jitter, and error rate. Due to the dynamic
changes of the network topology, only the most recent
records are kept and used for the interval estimation to
avoid the influence of the outdated information. In
addition, for each experiential route they two counters,
i.e., ExpSN and ExpFN, to record its successful times and
failure times, respectively. They set a threshold value for
the failure times. If the probing of an experiential route
returns satisfactory Quality-of-Service information, ExpSN
is increased by one; otherwise, ExpFN is increased by one,
ExpSN =0 . When the failure threshold is reached, the
experiential route is deleted.
is the expectation of the parameter value, S is the
standard deviation of the parameter value, and t1-α/2 is
the value of t distribution with confidence level α . The
above estimation method applies to the bandwidth,
delay, delay jitter, and error rate. Due to the dynamic
changes of the network topology, only the most recent
records are kept and used for the interval estimation to
avoid the influence of the outdated information. In
addition, for each experiential route they two counters,
i.e., ExpSN and ExpFN, to record its successful times and
failure times, respectively. They set a threshold value for
the failure times. If the probing of an experiential route
returns satisfactory Quality-of-Service information, ExpSN
is increased by one; otherwise, ExpFN is increased by one,
ExpSN =0 . When the failure threshold is reached, the
experiential route is deleted.
In this cognitive network, reasoning is used to perform two tasks. First, statistically summarize the usage of all the links in the network. The statistical results are used by the network administrator to reconstruct and optimize the network topology. Second, speculate on the possible causes when the exceptions occur. The two tasks are directly related to the routing protocol. Each node senses the usage of both adjacent links and experiential routes. The links, which have not been used for a long time, will be deleted by the network administrator. The frequently used experiential routes will be replaced by direct links. To implement the above topology reasoning, we create two statistical counters, i.e., NF sm and NS sm, to record the times that the neighbour interfaces have been used and the times that the experiential routes have been used, respectively. Each time the routing protocol updates the routing table, NF sm is increased by one for each used neighbour interface. If a certain interface has not been used for a long time period, its link will be deleted and its NF sm is set to 0. When the routing protocol is running, a procedure is triggered to probe the Quality-of-Service information in the experiential route. The returned probing result will decide whether to use the path or not. If the experiential route can be used, NS sm is increased by one.
The emotion behavior exploits the history routing
requesting information to aid the next hop selection. The
network traffic follows a time-dependent pattern.
Statistical method is used to calculate the probability that
a certain neighbour node is selected as the next hop by a
certain application type arriving at a certain destination
node within a certain time period. The probability of
selecting a certain neighbour may be often high. This
information can be exploited to optimize the routing
search. The probability of selecting neighbor Neibbk as
the next hop by application type APbk arriving at
destination node Vbk, within time period TZbk is denoted as 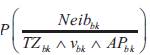
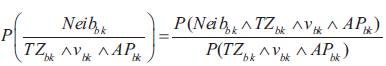
For each node, all its successful routing requests are
stored by the format 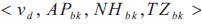 .
The accumulation of experiential information may result in
large data size. Therefore, it is not suitable to store the
experiential data in the memory. Instead, we store them
on the hard disc and restrict the maximum number of
experiential data items for each node. When the protocol searches for a routing path, if the selection probability of a neighbour exceeds a specified threshold value, the
neighbour can be directly selected without any further
calculation and judgment.
.
The accumulation of experiential information may result in
large data size. Therefore, it is not suitable to store the
experiential data in the memory. Instead, we store them
on the hard disc and restrict the maximum number of
experiential data items for each node. When the protocol searches for a routing path, if the selection probability of a neighbour exceeds a specified threshold value, the
neighbour can be directly selected without any further
calculation and judgment.
The cognitive behaviors for re-routing include problem solving, reasoning, and interpretation. The problem solving behavior is responsible for calling the exception handler. The reasoning behavior consists of two processes. One is to find out the reason why the exception occurs, and the other is to obtain the exception status. The process for exception reasoning is included in the rerouting protocol. When the system recovers the exception status, the network administrator needs to be notified the reason why the exception occurs. This job is done by the interpretation behaviour. In addition, lots of experiential knowledge was 'memorized' at the nodes through the cognitive behaviours. However, the exceptions in the network are usually caused by the node or link failures, leading to invalidation of the contents in the memory. The interpretation behaviour needs to notify the nodes to update their experiential knowledge in addition to giving the reasons of the exceptions. There are four types of information carried by the interpretation behaviour, i.e., original route, new route, exceptional upstream node, and exception type. The interpretation is an operation following rerouting. The destination node sends back the interpretation information upstream along the feasible partial paths on the original route and the new route, respectively. Each node creates a set of unavailable routes. Upon receiving the interpretation information, each node conducts the following processing (Figure 1)
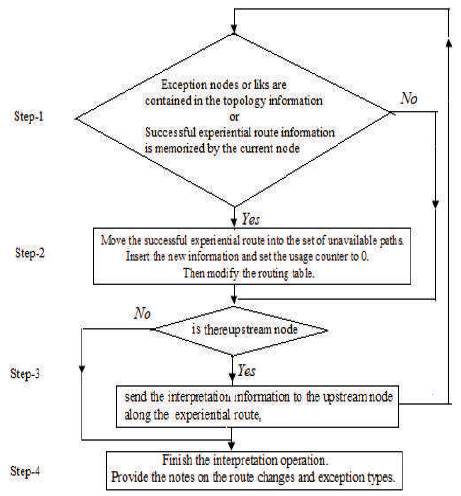
Figure 1. Processing flow of Cognitive Behaviours for Rerouting
The set of unavailable routes are regularly probed. If some routes turn to be available, move them into the successful experiential route set. If they are still unavailable, delete them. Meanwhile, the protocol detects the freshness of the information before using it. Thus, the obsolete information is eliminated. The information inconsistency will not last long between different nodes and no negative effect is caused by the existence of obsolete information.
Based on the aforementioned cognitive behaviours, we develop the Quality-of-Service routing and rerouting protocol oriented to cognitive network, which works on the classic Bellman-Ford algorithm [23]. In the protocol, we have two types of probing packets, i.e., the short distance probing packet and the long distance probing packet. The short distance probing packets are just sent to the neighbour nodes while the long distance probing packets are forwarded along the path set out by the probing packets.
The source node v starts to send the probing packets s which contain the Quality-of-Service requirements in terms of bandwidth, delay, delay jitter, and error rate.
Step 1.1Initialization. For each probing packet, put the source node vs sat the bottom of the Path Stack, and set CurBW ur =0, CurDLur =0, CurDJur=0, and CurERur =0. Set the maximum hop number TTLur to a default value.
Step 1.2If one of the neighbour nodes belongs to the same subnet as the destination node vd and it satisfies the Quality-of- Service constraints at service level SLur of application type APur , short distance probing packet is directly sent to the neighbour node, then go to Step 1.3. Otherwise, look up the local experiential route information, if there exists a path to the destination node and the path satisfies the Quality-of-Service constraints, a long distance probing packet is directly sent to the destination node through an active neighbour node. Then short distance probing packets are sent to all the other neighbour nodes if they meet the following conditions: being active, not present in the Path Stack, satisfying the Quality-of-Service constraints, stability degree above the threshold. If all of them are in the standby mode, they will be activated first and then receive the probing packets, then go to Step 1.3. Otherwise, there is no next hop node which meets the conditions, and the probing packet is discarded.
Step 1.3When node v receives a probing packet, it first performs the sense of spatiality behaviour to get the Path Stack information and then extracts the useful topology information which will be stored in the memory. TTLur = TTLur - 1. If TTLur =0, discard the probing packet. Update CurBW , CurDLur , CurDJur , and CurER ur. If node v is the destination node, then go to Step 1.5; otherwise, go to Step 1.4.
Step 1.4Check PTypeur . If it is a long distance probing packet, update CurNode and forward the packet along the ur path indicated by the packet, then go to Step 1.3. If it is a short distance probing packet, add node v into the Path Stack, then go to Step 1.2.
Step 1.5When a probing packet arrives at the destination node, PTypeur is checked. If it is a long distance probing packet, the actual Quality-of-Service values are returned to the intermediate nodes as acknowledgements. The long distance probing packets with satisfactory Quality-of- Service values are stored at the destination node. All the arrived short distance probing packets are also stored.
Step 2All the paths with satisfactory Quality-of-Service values are sent back to the source node vs along the reverse path in the Path Stack. All the intermediate nodes from vd to vs will memorize or update their experiential route information.
Step 3At the source node vs , among all the paths with satisfactory Quality-of-Service values, the best one is selected by the evaluation standard set out in Section 3.3. If price is not greater than Pay (i.e., the user pays less than the upper limit), the routing succeeds; otherwise, the routing fails. If no path is returned within time interval TSur , the routing fails.
Upon receiving the routing request R(vs , vd , APur , Slur , Pay), the source node vs looks up the successful experiential routes in its local memory. If there are paths to vd with Quality-of-Service at service level SLur of application type APur , then go to Step 2; otherwise, go to Step 3.
Step 2The source node vs sends the probing packets to vd along all the discovered paths. Once arriving at vd , the probing packets return the acknowledgements which contain the actual Quality-of-Service information of the paths. If the probed paths can satisfy the Quality-of-Service requirements, then go to Step 4; otherwise, go to Step 5.
Step 3The neighbour nodes look up the experiential routes in their memories. If there are paths to vd with satisfactory Quality-of-Service values, add the current node as the source node to form new paths, then go to Step 2; otherwise, go to Step 5.
Step 4Among all the paths with satisfactory Quality-of-Service values, the best one is selected by the evaluation standard set out in Section 3.3. If price is not greater than Pay (i.e., the user pays less than the upper limit), then go to Step 6; otherwise, go to Step 5.
Step 5Search the routing path by the extended Bellman-Ford algorithm. If the routing succeeds, then go to Step 6; otherwise, the routing fails.
Step 6Reserve the resources on the selected routing path based on the Quality-of-Service requirements and set up the routing entries.
In the routing protocol oriented to cognitive network, each router maintains the neighbours' state information instead of the global information. Therefore, the rerouting only involves the local routing tables instead of the routing tables in the whole network. The rerouting needs to generate the interpretation information accompanied by the interpretation behaviour. The rerouting exploits the experiential route information in the memory to detect if the next hop node is still available. Thus, the failure type can be determined, i.e., whether it is node failure or link failure. In the cognitive protocol, every node periodically interacts with its neighbours. When one node identifies an unreachable neighbour, it searches its routing table to check if there is a routing entry where the unreachable neighbour is set as the next hop. If so, the rerouting will be triggered. By exploiting the cognitive behaviour and the useful information accumulated during the routing process, the authors have designed a simple but effective rerouting scheme as described below.
Step 1When node er v identifies a routing entry where the next hop is unreachable, it starts to construct the interpretation information. The upperstream node of the unreachable neighbour is denoted as ver and Typep =NULL . Then node ver looks up its memory and get the experiential route which also exists in the routing table.
Step 2If ver = vs , then go to Step 4, otherwise, go to Step 3.
Step 3Send the probing packet to the source node along the upstream node on the experiential route, and obtain the application type APer and service level SLer of the original routing request.
Step 4Set the original route in the interpretation information as a successful experiential route denoted as OPathep .
Step 5Look up the topology information in the memory of ver . If there exists another route to the next hop node, detect if the node is reachable. If it is reachable, set the Typeep as link failure.
Step 6Node vs uses the routing path search procedure to find a new route which satisfies the requirements of service level SL er in application type APer . If the probing is successful, the rerouting succeeds and the new route RPathep is stored at the destination node, then go to Step 7, otherwise, the rerouting fails.
Step 7If Type ≠ NULL then go to Step 8, otherwise, if RPath ep contains the next hop of ver in the original route, then go to Step 9.
Step 8Send the probing packet reversely along OPathep to determine if the next hop of ver is reachable, then set Typeep.
Step 9Execute the interpretation behaviour at the destination node, modify the routing entries, and reserve resources along the new route.
To implement the cognitive Quality-of-Service routing and rerouting protocol, we need to add a knowledge plane to each node and the knowledge plane is responsible for the implementation of cognitive behaviours. We use NS2 [10] for performance evaluation. In NS2, to implement the functions of knowledge plane, we need to add a new protocol called Agent and bind Agent with each node. The Agent protocol inherits the Agent class in NS2. We implement the aforementioned cognitive behaviours based on the extended Agent protocol. According to the generic service Quality-of-Service specified in the ITU-T G.1010 standard [22], we use the following generic service classes in the simulation experiments. They are listed in Table 6. In the experiments, we further classify each application type into four levels and each level represents one service level of the user Quality-of-Service requirements. The user request includes both the application type and the service level. By the mapping, we can get the user's detailed Quality-of-Service parameter requirements.

Table 6. Generic Service Class
The network topologies play fundamental roles in the simulation experiments. To evaluate the protocol performance, we must select appropriate topology examples which can reflect the practical networks. In the following experiments, we have used random topology generated by the Waxman random graph model [24]. The random topology consists of 50 nodes and 80 links. We name the proposed Cognitive Rerouting protocol as CoRp and evaluate its performance in various aspects. In [25], a multi-constraint Quality-of-Service routing protocol is proposed based on a new single mixed metric. It is a novel heuristic Quality-of-Service routing protocol named as SMMQR. It considers multiple Quality-of-Service constraints over the links and integrates them into a single mixed metric. Then the shortest path routing algorithm is utilized to find the Quality-of-Service routing path. Simulation and analytical results show that SMMQR can well solve the multi-constraint Quality-of-Service routing problems with high routing success ratio. In the following experiments, we compare CoRp with SMMQR and DV (Distance Vector) prototocl implemented in Ns2.
Based on the selected topology, we run CoRp, SMMQR, and the standard DV protocol in NS2 to compare their control overhead. The source and destination nodes are randomly selected and routing requests arrive continuously. For CoRp, four different scenarios are designed. First, all the nodes turn off all the cognitive behaviours. Second, the source node turns off all its cognitive behaviours and all the other nodes turn on their memorization behaviour. Third, the source node turns on the search help function and all the other nodes turn on their cognitive behaviours. Fourth, all the nodes turn on the search help function and memorization behaviour. These four scenarios are denoted as CoRp-1, CoRp-2, CoRp-3, and CoRp-4. The comparison results are shown in Figure 2. Since DV does not consider Quality-of-Service and only exchanges connectivity information with neighbour nodes, its control overhead has nothing to do with the number of routing requests. So its control overhead is fixed. SMMQR combines multiple routing metrics into a single one. Its control overhead is increased with the increase in the number of routing requests. For CoRp, since it has used much more control messages than both DV and SMMRQR, its control overhead is also higher than them.
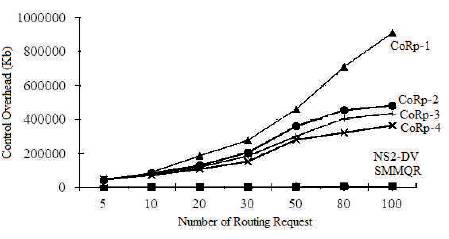
Figure 2. Comparison of Control Overhead
A certain number of traffic flows is generated randomly and classify them into five levels.
The number of dada flows = N×L×T×i
Where N is the number of nodes, L is the number of links, T is a benchmark and (I= 1,2,3,4,5). In the protocol, the source node and the destination node is randomly determine and randomly set the application type of the corresponding routing requests. 100 continuous routing request under each load level is generated and then count the times that the routing requests return successful results. The routing success ratio is then calculated and the results are shown in Figure 3.

Figure 3. Comparison of the Routing Success Ratio Over Random Topology
The results show that for the protocols the routing success ratio decreases when the traffic flow level goes up. CoRp can guarantee the successful routing when feasible routes exist. The reason is that CoRp has considered all the Quality-of-Service constraints and utilized the cognitive behaviours. DV cannot adjust the routing dynamically when there are changes to the link Quality-of-Service parameters. Therefore, with the traffic flow level going up, the routing success ratio decreases significantly. For most of the time, SMMQR can satisfy the Quality-of-Service requirements. However, due to the combination of several Quality-of-Service constraints into a single metric, SMMQR cannot guarantee that all the Quality-of-Service constraints can be satisfied.
Figure 4 show the comparison results of the user's Qualityof- Service satisfaction degree, which exhibits similar trend as the routing success ratio. Under low traffic flow levels, the three protocols have competitive performance. With the traffic flow level going up, the user's Quality-of-Service satisfaction degree of DV decreases as the routing success ratio. DV's performance is much worse than the other two protocols. The user's Quality-of-Service satisfaction degree of SMMQR is slightly worse than that of CoRp also due to the combined single metric.

Figure 4. Comparison of the User's Qualityof- Service Satisfaction Degree
The learning behavior updates the Quality-of-Service parameter estimation intervals according to the feedback from the usage of the experiential routes. The estimation interval of an experiential route is used to judge if it is suitable for use. To evaluate the effects of the learning behaviour, we calculate the ratio of successful usage of the experiential routes. In the experiments, we first generate 100 routing requests randomly over the random topology in order to memorize a number of experiential routes which are prepared for the learning behaviour. Then under each traffic flow level, we randomly generate 100 routing requests again to count the times that the experiential routes have been used. The results are shown in Figure 5.
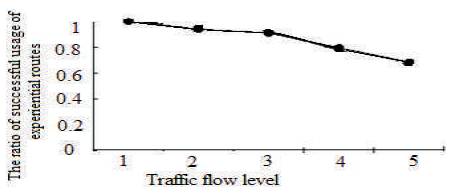
Figure 5. Comparison of the Ratio of Successful Usage of Experiential Routes
From the results, with the traffic flow level going up, the ratio goes down. The reason is that at high traffic flow levels, some experiential routes cannot satisfy the Qualityof- Service requirements of the applications. Therefore, the ratio of successful usage of experiential routes decreases. When an experiential route is identified to be invalid, it will not be deleted immediately. Instead, it will be deleted after a few failure attempts. Thus, the failure times are not reduced. In the topology with good route diversity, new experiential routes can be easily found and memorized and successfully applied. This will help to alleviate the decreasing trend of the successful ratio.
The results are shown in Figure 6. Since DV has the lowest routing success ratio among the three protocols, its usage proportion of experiential routes is also lower than the proportions in both CoRp and SMMQR. For SMMQR, the routes in it are slightly different from the ones in CoRp.
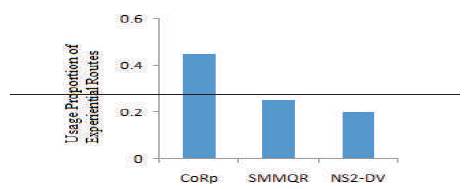
Figure 6. Comparison of Proportion of Usage of Experiential Routes
As CoRp is a distributed routing protocol, the routing discovery time heavily depends on the link delay in the network. The actual running time of the protocol cannot directly reflect the performance of the protocol. Therefore comparing the routing discovery time by mapping it to the relative relation between CoRp with SMMQR and NSDV. The comparison results are shown in Figure 7.
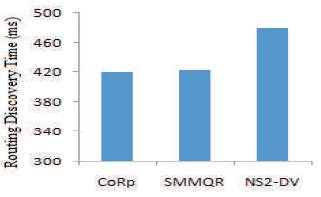
Figure 7. Comparison of the routing discovery time
With the ever-increasing spatial and temporal complexity in the topology, the network administration and maintenance is facing huge challenges. Especially when the users propose different Quality-of-Ser vice requirements, the current network and routing schemes cannot deal with these requests effectively. The incurred problems not only bring inconvenience to the users but also burden the network administrators. The cognitive network is developed to solve the above problems by reducing the human intervention in the network management. It is expected to help enhance the network in scalability, self-adaptation, self-organization, selfprotection, mobility and diversity. In this paper, we have designed a Quality-of-Service rerouting protocol oriented to cognitive network. The design utilizes the cognitive behaviours presented in the cognitive science. The cognitive behaviours in our model mainly consist of the sensation, sense of spatiality, memorization, learning, reasoning, and emotion. The researchers map the behaviours to specific functions at each node for supporting the Quality-of-Service routing and the network fault recovery. We compare its performance with two other popular protocols. The experimental results show that with the help of cognitive behaviours, Quality-of- Service rerouting protocol has greatly improved the network performance in Quality-of-Service provision and fault recovery.