
Figure.1 Tactically Equipped Armed man
Today's military voice radio systems were not designed to provide the bandwidth required by today's multimedia data flows, particularly video. Worldwide, armies are looking for broadband radio access solutions to their tactical needs, and are testing Commercial-Off-The-Shelf (COTS) solutions such as WiMAX. Wireless Sensor Networks which is a type of wireless network consist of small nodes with capabilities of sensing physical or environmental conditions, processing related data and send information wirelessly. These WSN Dense deployments of disposable and low-cost sensor nodes make WSN concept beneficial for battle fields. In Military Applications, the literature discusses WSNs usage for tracking missiles and other possibilities include using WSNs as a military monitoring network for surveillance purposes to monitor large areas against intruders and send alerts and information about intruders using NS2. Some military applications of WSNs are:
Tactical military sensor network systems have been researched for the Network Centric Warfare (NCW) in many military forces around the world. As NCW is a highly orchestrated dynamic autonomous digital battlefield communications command/control and situational awareness network, commander can see, decide and shoot the target in advance due to preoccupying the highly advanced situation awareness.
The advantages of the sensor network in military applications, Commercial-off-the-shelf sensor network systems cannot offer the solution due to the tactical constraints and requirements, especially in remote largescale environments. There have been large amount of research on tactical military wireless sensor networks (WSNs) and significant progress has been achieved. The authors propose a design approach for the military WSN in remote large-scale environments based on the military requirements. Since WSNs in remote large-scale environments cannot be managed manually, after being distributed, sensor nodes have to organize and heal themselves in an energy-efficient manner while guaranteeing the network connectivity, low probability of intercept (LPI) and low probability of detection (LPD) for security.
In the information age, tactical military sensor network systems have been researched for the Network Centric Warfare (NCW) in many military forces around the world. As NCW is a highly orchestrated dynamic autonomous digital battlefield communications command/control and situational awareness network, commander can see, decide and shoot the target in advance due to preoccupying the highly advanced situation awareness.
The US Army's Future Combat System also uses the Unattended Ground Sensor network to detect, locate and identify enemy targets with lighter armor protection on the battlefield. These sensors can be deployed statically by hand or randomly in remote area by Unmanned Aerial Vehicles (UAVs) and artillery. Despite the advantages of the sensor network in military applications, Commercialoff- the-shelf sensor network systems cannot offer the solution due to the tactical constraints and requirements, especially in remote large scale environments. There have been large amount of research on tactical military wireless sensor networks (WSNs) and significant progress has been achieved. Nevertheless, most of the developed and designed military sensor models are not operated in the remote large-scale with thousands of nodes but in the static deployment environment with several nodes.
The authors propose a design approach for the military WSN in remote large-scale environments based on the military requirements. Since WSNs in remote large-scale environments cannot be managed manually, after being distributed, sensor nodes have to organize and heal themselves in an energy-efficient manner while guaranteeing the network connectivity, low probability of intercept (LPI) and low probability of detection (LPD) for Security. They defined the various requirements, and finally proposed the cluster-tree based multi-hop sensor network with the optimized cluster head election.

Figure.1 Tactically Equipped Armed man
Fact Finding is the methods of gathering the information required about the existing system. Some of them are as follows.
Observation of the current work situation will provide clues to problems and atmosphere.
Record searching, special purpose records and sampling will give quantitative information about the system which facilitates sizing of the proposed system and may also point the areas of difficulties which are being experienced.
Questionnaires can be used to collect the quantifiable data about the system. All of the techniques need to be supplemented by more detailed discussion of the interview situation. The identification of the user requirements are decision areas, objectives and responsibilities for certain procedures can only be achieved for interviewing.
Based on the above fact finding techniques, it is observed the current situation of the existing system. It is very helpful in finding the areas of difficulties, which are being experienced in the existing system. Thus it helps to develop the proposed system with the quantifiable data.
In addition to the existing hardware platforms, wireless sensor networks have a new software framework. Since traditional network abstractions are usually not suited for wireless sensor networks the embedded software must have precise control over their hardware and be able to implement application specific networking protocols. Furthermore, wireless sensor network operating systems must allow high level applications direct and efficient control over low level hardware when necessary. In NS2 designed for wireless sensor networks, a specialized component model, which is enabled by advanced compiler technology, is used to simultaneously provide efficiency and reliability. These same concepts are now being brought into more traditional operating systems for use in gateway class and high-bandwidth nodes.
One of the critical requirements for robust, low power sensor mesh networks is the routing protocol stack. It covers the whole range of layers of the OSI (Open Systems Interconnection) reference model for networks. Because NS2 is an open source, all of its layers can be modified to meet the needs of an application. A flexible mesh networking protocol in NS2 called Mesh has been developed new Framework.
The Mesh protocol stack is an open architecture, flexible, and powerful embedded wireless networking and control platform built to support NS2 applications. Mesh combines proven high performance with interoperability through the support of ZigBee [2] protocol.
The Mesh stack dynamically forms a reliable mesh network between nodes using proven Ad hoc routing techniques. Mesh's routing techniques are based on scientific research done within the NS2 community that characterized and tested many Ad hoc multi hop protocols and strategies for performance platform. The minimum transmission, minimum cost technology developed optimally reduces the total number of radio messages throughout the network, there in maximizing the bandwidth, battery-life, and reducing network traffic and latency. Even without the use of any of Mesh's advanced QOS (Quality of Service) features, Mesh forms a reliable deterministic network, and the performance is shown to be superior to other techniques including DSDV (Destination Sequenced Distance Vector), AOMDV [3] (Ad hoc On Demand Multipath Distance Vector), and other proprietary routing schemes.
Input Design is part of overall system design, which requires very careful attention. If the data going into the system is incorrect then the processing and output will magnify these errors.
The inputs in the system are of three types:
The above input types enrich the proposed system with numerous facilities that make it more advantageous in comparison with the exiting normal system. All the inputs entered are completely raw, initially, before being entered into a database, each of them available processing. The input format in this system has been designed with the following objectives in mind.
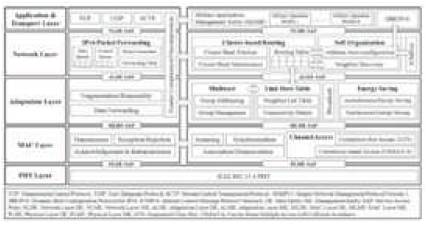
Figure 2. Tactical WSN Protocol Architecture for Sensor Nodes
Sensor nodes that are randomly distributed in remote wide areas first self-organize their own network. After a sensor node turns on its power, the node tries to perform an address auto-configuration (AAC) through two stages, the cluster-tree formation and the stateless AAC. Beginning from the sink node, which performs as a personal area network (PAN) coordinator and a mesh coordinator (MC), sensor nodes gradually join the network and the cluster-tree structure is formed. In the first stage, only the sensor node within the transmission range of a sink node receives a beacon frame. The sensor node then sends an association frame to the sink node and is confirmed from the sink node . After the association, the cluster head election is performed to support a multi -hop cluster-based hierarchical network topology. Figure 3 shows a cluster head election algorithm used for our scenario. Based on this algorithm, a cluster head is selected and sends a beacon frame to perform the duties as a coordinator. The cluster head election is repeated until no more nodes wait for joi ning the network and completed when the sink node no longer received any children number report [4] from cluster heads after a specified period of time.
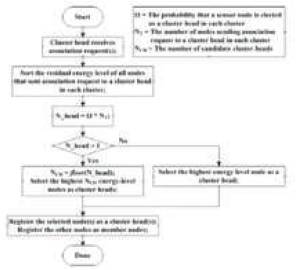
Figure 3. Cluster head election algorithm
The cluster head election scenario is shown in Figure 4. After all sensor nodes complete joining the network, the sink node receives information from all the branches. By using the received information considering required address spaces of sensor nodes, the sink node sends a route advertisement (RA) message to cluster heads. The message contains prefixes that identify the subnets associated with each cluster. If each cluster head has received the RA message, a stateless AAC starts to be performed in each cluster. Two AAC schemes are generally used in IPv6 networks. One is a stateless AAC that uses Internet control message protocol version 6 (ICMPv6) and the other is a dynamic host configuration protocol version 6 (DHCPv6) [1]-based stateful AAC. Because of the randomly distributed characteristic in our target scenario, the stateless AAC is considered to be a better solution than the stateful AAC. The stateful AAC can also be used as a supplementary method. ICMPv6 is also used as an error recovery/diagnostic scheme in unattended environments.

Figure 4. Cluster head Election Scenario
The survey about existing routing protocols for low power wireless networks shows that there are no routing protocols that can be used without modification in our networks . The IEEE 802.15.5 mesh routing also has a limitation to be applied in our scenario because it does not support inter- PAN communication. In order for the tactical WSN architecture to meet routing requirements of 6LoWPAN and at the same time to satisfy the military requirements, both adaptation and network layers should cooperate with each other. A cross-layer approach to utilize the neighbor list table in the adaptation layer and the routing table in the network layer is applied to our architecture.
For communication inside WSN, routing is based on the link state table (LST) in the adaptation layer. After addresses are assigned to sensor nodes, each cluster head sends several hello messages to its neighbor cluster heads. Upon reception of each hello message, each cluster heads update its LST. A LST consists of a neighbor list table and connectivity matrices. Each entry of the neighbor list table consists of a MAC address, tree level, link quality, relationship, number of hops, and group membership and the number of hops is calculated by the connectivity matrices. For sensor nodes to communicate with backbone networks beyond the sink node, IPV6- based routing is also supported.
Since the maximum transmission unit (MTU) size of an IEEE802. I5.4 frame is 127 bytes, an original IPv6 and transport layer header format cannot be used in WSNs without a header compression mechanism. In the worst case, only 21 bytes are remained for data when IPv6 and TCP are used in IEEE 802.15.4 frame with the advanced encryption standard-counter with CBC-MAC-128 (AESCCM- 128). For utilizing both the header compression mechanism in 6LoWPAN and the mesh topology capability in IEEE 802.15.5, we propose a new mesh header format by modifying the mesh addressing type in 6LoWPAN and the frame control field in IEEE 802.15.5.
Figure 5 shows the proposed mesh header format and its example address format in the multi-hop, fragmented, and header compressed case. Similar to the mesh addressing type in 6LoWPAN, the proposed format starts with a one bit and a zero bit as the first two bits. Required subfields in the IEEE 802.15.5[4] frame control field to be combined with the 6LoWPAN mesh header follow the first two bits. An Inter-PAN communication mode field is created for communication between a sensor node and the entity beyond the sink node.
The fragmentation and reassembly is a basic function supported by 6LoWPAN. If a packet received from the next higher layer needs to be fragmented, the fragmentation header defined in Montenegro et al. is appended and defragmented at the destination sensor node.
An energy saving mechanism is one of the key functions to support low-power and long battery life in WSNs. For sensor nodes to operate power-efficiently at a non-beacon mode in wireless multi-hop communication environments, IEEE 802.15.5 asynchronous energy saving (ASES) and synchronous energy saving (SES) should be supported.
All projects are feasible, given unlimited resources and infinite time. Before going further in to the steps of software development, the system analyst has to analyze whether the proposed system will be feasible for the organization and must identify the customer needs. The main purpose of feasibility study is to determine whether the problem is worth solving. The success of a system also lies in the amount of feasibility study done on it. Many feasibility studies have to be done on any system. But there are three main feasibility tests to be performed. They are
During feasibility analysis operational feasibility study is a must. This is because; according to software engineering principles operational feasibility or in other words usability should be very high. A thorough analysis is done and found that the system is operational.
The system analyst used to check the technical feasibility of the proposed system. Taking account of the hardware it is used for the system development, data storage, processing and output, makes the technical feasibility assessment. The system analyst has to check whether the company or user who is implementing the system has enough resource available for the smooth running of the application. Actually the requirements for this application are very less and thus it is technically feasible.
Before we are going to further in to the development of the proposed system. The system analyst has to check the economic feasibility of the proposed system and the cost for running the system is composed with the cost benefit that can achieve by implementing the system. As in the case of Crypto Media development cost is not high, as it doesn't need any extra hardware and software. Thus the system is economically feasible.
System design is process of planning a new system to document or altogether replace the old system. The purpose of the design phase is to plan a solution for the problem. The phase is the first step in moving from the problem domain to the solution domain. The design of the system is the critical aspect that affects the quality of the software. System design is also called top-level design. The design phase translates the logical aspects of the system into physical aspects of the system.
Intelligent output design will improve systems relationships with the user and help in decision making. Outputs are also used to provide a permanent hardcopy of the results for latter consultations. The most important reason, which tempts the user to go for a new system is the output. The output generated by the system is often regarded as the criterion for evaluating the usefulness for the system. Here the output requirements use to be predetermined before going to the actual system design.
The output design is based on the following:
Figure 6 gives you the graphical design and operation approach of our finally designed network in a large dense forest environment
Nodes(as troops) have been monitored effectively in dense forest. This graphical representation is or understanding purpose. Original system design may vary as per requirements.

Figure 6. Graphical node Representation
Tools: network simulator version-2
Os: Linux
Nodes are distributed evenly among terrain limit 50.
X: 50 mts
Y: 50 mts
Terrain is space limit which is used to allocate space of operation in NS2.X and Y axis here reffered to space where nodes are distributed (Figure 7).
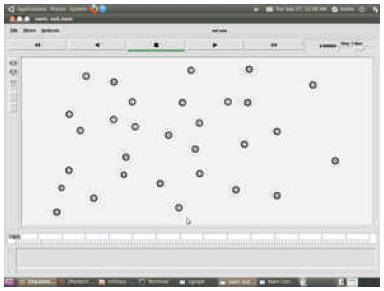
Figure 7. Thirty(30) nodes are created with initial terrain as 50
Nodes 2, 7, 13, 19 and 20 all together forms a cluster. From this cluster it elects an cluster head as per requirements of system. Here the cluster head is node -19 (Figure 8).
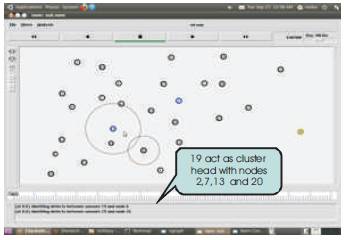
Figure 8. Cluster Formation
Packet transfer within the cluster 19.the packet transfer is clearly indicated by the arrow(cursor). i.e. the data transfer is between the nodes 2,7,13,20 and 19. This five nodes uniquely forms a cluster (Figure 9).
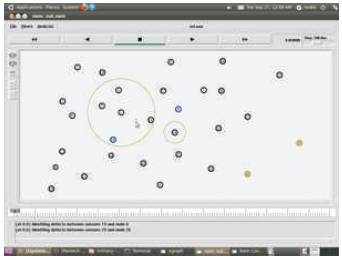
Figure 9. Cluster Based Transmission
Throughput of the system designed. Throughput is increased. Resulted in improving performance (Figure 10).
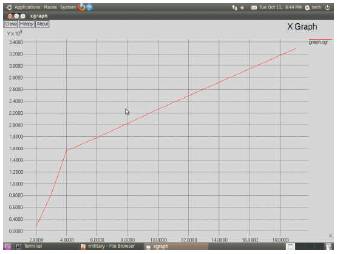
Figure 10. Throughput of the system
As discussed, a tactical WSN architecture with sensor nodes in remote large-scale environments created, to satisfy the tactical WSN needs. This defines the various requirements, and finally proposes the cluster-tree based multi-hop sensor network with the optimized cluster head election. The prediction and recovery mechanisms for maintenance of the network are also designed. Studies are satisfying other tactical requirements (e.g. Security, QoS, inter-working with tactical backbone) are being conducted in order to design more useful tactical WSN System. It can also be used for animal monitoring in dense forest.