
Figure 1

Figure 2

Figure 3

Figure 4

Figure 5

Figure 6

Figure 7

Figure 8
Steganography is the technique for hiding secret information in any ordinary image. Such image in which secret information is hidden is known as stego image. Whereas Steganalysis is the reverse technique in which detection of the secret information is done in the stego images. In this paper, various visual and statistical attack techniques are implemented for the detection of the secret data in the stego image.
There are two ways of doing visual attack:
With these two techniques the area of hidden data is detected on the basis of the difference in visual texture of the stego image.
Similarly there are two ways of doing statistical attack:
With these two technique based on the difference in statistical parameter of the stego image with cover image detection is done. Further the comparison of the techniques of both the attacks is done on the basis of time, memory requirement and information requirement.
As reported by the USA TODAY AP by Jack Kelley that in 1998, a hardcore terrorist Osama Bin Laden and associates used the steganography technique to hide the information related to the bombing of two U.S embassies in East Africa. The photographs of the terrorist targets and positioning instructions had being sent by hiding in the sports chat room, phonographic bulletin board and other web sites. So, it becomes very essential to work in the area of the detection of the hidden data. Now working as hacker is becoming more important than working in the field of hiding techniques to provide security in the national and international level [1]. Steganalysis is the art of science which deals with the detection & destruction of the secret image. Various approaches are discussed by different researchers in the area of steganalysis. Broadly, there are two approaches to the problem of steganalysis, one is to come up with a steganalysis method specific to a particular steganographic algorithm known as embedding Algorithm based steganalysis Techniques. In this technique for decoding we must know the coding algorithm. Complete recovery of the secret data is possible. The other technique is more general class of steganalysis technique pioneered independently and can be designed to work with any steganographic embedding algorithm, even an unknown algorithm. Such techniques have subsequently been called Universal Steganalysis Techniques or Blind Steganalysis Techniques. A steganalysis technique specific to an embedding method would give very good results when tested only on that embedding method, and might fail on all other steganographic algorithms. But the blind steganalysis is the universal one which can be implemented to any stego image. The image which is containing hidden information is known as stego image and the image in which secret information is to be embedded is known as cover image [2,3,4].
Steganalysis can also be classified based on the detection parameters. If the detection is done in the basis of the differences in the visual texture of the stego image and cover image then it is known as visual attacking whereas if the detection is done in the basis of the variation in the statistical parameters of the stego image and cover image then it is known as the statistical attacking. These attacking technique need the information of cover image and stego image. The universal steganalysis is a better technique in which the technique can be implemented to any randomly incoming images and detection can be done. Any portion of the incoming image may be altered after applying the detection algorithm. If after removing the noise effect the alteration remain. then it is detected that the secret data is hidden in it. If the detection result indicate the presence of hidden information, then the analytic will try to recover the secret data by applying the decoding algorithm in the hit and trial method. Prediction accuracy can be interpreted as the ability of the measure to detect the presence of a hidden message with minimum error on average. The feature should be independent on the type and variety of images supplied to it [5,6,7].
In this paper, an attempt has been made to develop and implement steganalysis techniques. The two steganalysis technique namely visual attack and statistical attack are developed and implemented on the stego images which is obtained from the data base previously generated (Even there is the possibility to change the data base). Under each attacking two detection techniques are implemented. The Enhanced LSB visual attacking is the universal steganalysis technique.
Survey of few research papers in the present field is done [8]. The research in this field started from 1995. A brief introduction is given about the papers in which the steganalysis techniques related to the work in this paper are discussed.
The analysis of the security of LSB embedding for hiding messages in high-color-depth digital images is done. A powerful steganalytic technique is introduced that enables us to reliably detect the presence of a pseudorandom binary message randomly spread in a color image. The probability of both false detections and missing a secret message is estimated. The method is based on statistical analysis of the image colors in the RGB cube. It is shown that even for secret message capacities of 0.l -0.3 bits per pixel, it is possible to achieve a high degree of detection reliability [9].
A new steganalytic technique based on the difference image histogram aimed at LSB steganography is proposed. Translation coefficients between difference image histograms are defined as a measure of the weak correlation between the least significant hit (LSB) plane and the remaining bit planes, and then used to construct a classifier to discriminate the stego-image from the camera image. The algorithm cannot only detect the existence of hidden messages embedded using sequential or random LSB replacement in images reliably, but also estimate the amount of hidden messages exactly. Experimental results show that for raw loss less compressed images the new algorithm has a better performance than the RS analysis method and improves the computation speed significantly [10].
Detection of stego image can be done depending on the distribution of the difference between the current pixel value and its neighborhood average pixel value is statistically modeled, and then the variance of this statistical distribution is defined as a measurement of image smoothness. Based on the analysis of the effects on the image smoothness brought by message embedding and LSB plane flipping, a new steganalytic technique capable of reliable detection of spatial LSB steganography is proposed. The algorithm can exactly estimate the amount of hidden messages and detect the existence of hidden messages embedded in the image simultaneously. Experimental results show that the proposed algorithm is effective [11].
On the basis of universal detection approaches the visual attacking algorithm is designed using the MATLAB software and implemented to the stego image database, where database includes few different images of different size and formats [3,12,13].
In this technique the LSB of the cover image and the stego image is compared by using the logical function. If they are found to be different then, the pixel of the stego image which is containing that bit is highlighted in bright color so that it is visible. If the bits are having the same value then the pixel value of the stego image does not change. If any secret data is there then there will appear unusual changes in some portion of the incoming image when compared with the cover image. This highlighted area may contain the secret data [9,14].
It's going to do the opposite of what a steganography tool generally does. It will eliminate all 7 high-level bits for each pixel except the last LSB. So all bytes are going to be 0 or 1. The problem is that 0 or 1 on a 256 values range won't give any visible color. With enhancement of LSB’s basically, a 0 stays at 0, and a 1 becomes maximum value, or 255. That will give some flashy colors; the LSBs of the original image are going to become very visible, good enough for a visual check. With this method some pattern will change [9,14].
Given a Stego image. To detect whether the stego image is containing any secret data or not.
Assumptions:
Step 1: Read the stego image.
Step 2: Read the cover image .
Step 3:Compare the LSB of the pixel value of the cover image and the stego image.s
Step 4: If they are different then highlight the pixel containing that bit otherwise pixel value is kept same..
Step 5: Calculate the simulation time and the memory space requirement.
Step 1: Read the stego image.
Step 2: Scan the image row wise and check the LSB value.
Step 3: If the LSB is ‘1’ then highlight that bit and rest bits are made zero.
Step 4: If the LSB is ‘0’ then make all the bits zero.
Step 5: Calculate the simulation time and the memory space requirement.
In this technique Statistical properties of the image vary if any information is hidden in it [16].
The images shown from Figures 1 to 4 and Figures 9 to12 are the input stego images and the output attacked images are shown from the Figures 5 to 8 and from Figures 13 to 16. In this method of analysis for the detection of the secret image, the analytic compares the stego image and cover image. The pixel values of the cover image and the stego image are compared and the difference is highlighted.

Figure 1 |

Figure 2 |

Figure 3 |

Figure 4 |

Figure 5 |

Figure 6 |

Figure 7 |

Figure 8 |

Figure 9 |

Figure 10 |

Figure 11 |

Figure 12 |

Figure 13 |

Figure 14 |

Figure 15 |

Figure 16 |
The images shown from the Figures 17 to 20 and Figures from 25 to 28 are the input stego images and the output attacked images are shown in the Figures 21 to 24 and Figures 29 to 32. In this method of analysis for the detection of the secret image, the LSB of the stego image is highlighted depending on the value of the bits. If the LSB is logic one then the pixel intensity containing that value is increased otherwise pixel intensity is decreased.
In the Figures from 1 to 16 the visual attack: known cover image steganalysis of the cover and its stego images are shown. In the attacked images for all the eight images there is red highlighted area where the hidden data is suspected. In the highlighted area the pixel intensity value of the cover image and the stego image are different. If any highlighted area is seen after the detection program is implemented then it is detected that the images may contain the hidden data otherwise not. In the Figures 17 to 32 the visual attack: Enhanced LSB Technique (universal Technique) steganalysis of the cover and its stego images are shown. The LSB of the images are highlighted. In the attacked images for all the eight images there is some portion of the image which gets distorted from the original cover image. This happens because in this portion of the image the LSB of the incoming stego images does not give any information about the original cover image. The deviation from the original image indicates that there is variations in the pixel value. So, hidden data may be there. For the implementation of this detection swb. jpg 5 technique the analytic is having information only about the stego image. If the distortion occurs after the detection program is implemented then it is detected that the images may contain the hidden data otherwise not.

Figure 17 |

Figure 18 |

Figure 19 |

Figure 20 |

Figure 21 |

Figure 22 |

Figure 23 |

Figure 24 |

Figure 25 |

Figure 26 |

Figure 27 |

Figure 28 |

Figure 29 |

Figure 30 |

Figure 31 |

Figure 32 |
In this method of analysis, for the detection of the secret image it is considered that the analytic is having the information about the cover image along with the incoming stego image [16].
In this method of analysis, for the detection of the secret image, it is considered that the analytic is having the information about the cover image along with the incoming stego image [16].
Table 1 shows the comparison of the performance of all the four steganalysis techniques on the basis of the memory space requirement, simulation time and information requirement for the implementation of the detection coding algorithm. Comparison of these techniques is done (Figure 33). From the comparison Table it is observed that the Visual Attack: Enhanced LSB technique (Universal attack) is best among the four attacks. This technique required less simulation time. The code of the universal attack required less memory space. The area of the image where secret data is hidden is properly visible. In spite of all these the main feature of the universal attack is that, no other information is required by the analytic except the Stego image.

Figure 33. Comparison of the Steganalysis Attacks
All the four steganalysis methods are implemented to the same set of stego images and cover images from the database generated previously. These are histogram analysis: known cover image and image smoothness: known cover image in the statistical attack and mri.tif 6 visual attack: known cover image and visual attack: enhanced LSB technique in the visual attack. In visual attack the detection method is proposed depending on the variations in the visual texture of the image whereas in the statistical attack the detection method is suggested depending on the variation in the statistical properties of the images. Among these, visual attack: enhanced LSB technique is the universal steganalysis technique and rest three are embedding algorithm based steganalysis techniques. These techniques are capable of detecting the presence of secret data in the stego images. Although attacks specific to an embedding method are helpful in coming up with better embedding methods, their practical usage seems to be limited. Thus universal steganalysis techniques seem to be the real solution since they are able to detect stego images even when a new embedding technique is being employed. According to the comparison given in the Table 1, it can be concluded that visual attack: enhanced LSB technique is the better one. The visual attack by enhancing the LSB’s of the stego image and statistical attack by introducing the image smoothening are the steganalysis techniques introduced in this paper.
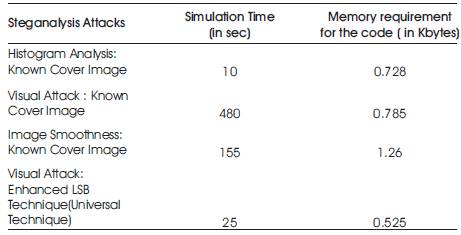
Table 1. Comparison of the four Steganalysis Attacks