Figure1. Iris Scanning
With the advancement of electronics and computer science, mobile communication technology leads us to a fast moving entirely different world. In this scenario, we have lot of responsibilities, one of it is voting for our country, but even we don't have time for it, and also our votes may not useful to our nation, because of fake votes and cheating process happened during the election. This problem is rectified by the latest voting system as “Mobile Voting System” which is discussed in this paper. The mobile voting system uses the efficient techniques, iris recognition and cryptography for the secured voting process. The iris recognition and cryptography avoids the fake votes and cheating process. The election commission spends lot of money, for each election unnecessarily, which will be minimized by this system. This system enables the voter to vote to the Nation from his place itself.
Mobile voting system use the iris recognition and cryptography techniques, for voting purpose, the encryption algorithm is uploaded in the mobile phone. As like the eye scanner which scans the iris is fixed in the mobile, so the mobile phone having camera is preferred for that. To obtain the voting the voters eye iris is recognized. During the transmission from the source (mobile) to destination (election database system) the data is encrypted using the encryption algorithm. The data sending and receiving is doing with the help of the mobile networks.
Everyone in the world has the uniqueness of their own; such uniqueness cannot be imitated/remake by anyone. Such uniqueness is used for a security purpose. As an iris technology produces a very low false rate when compared to other biometrics results are very preferable in our mobile voting system. [1],[2]
Iris scanning can seem very futuristic, but at the heart of the system is a simple CCD digital camera. It uses both visible and near-infrared light to take a clear, high-contrast picture of a person's iris.
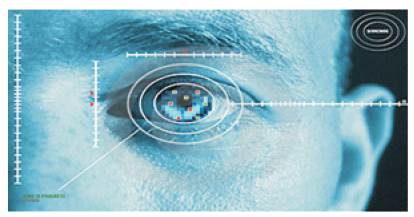
With near-infrared light, a person's pupil is very black, making it easy for the computer to isolate the pupil and iris[1],[2][6]. On look into an iris scanner, either the cameras focuses automatically or use a mirror or audible feedback from the system to make sure that eye is positioned correctly as shown in Figure1. Iris scanner is actually not a scanning device, but it is a digital camera with iris scanning software. Usually, eye should be 20 to 25 cm from the camera. When the camera takes a picture, the computer locates: shown in Figure 2.

Figure1. Iris Scanning
It then analyzes the patterns in the iris and translates them into a code. Iris scanners are becoming more common in high-security applications because people's eyes are so unique (the chance of mistaking one iris code for another is 1 in 10 to the 78th power they also allow more than 200 points of reference for comparison, as opposed to 60 or 70 points in fingerprints. The iris is a visible but protected structure, and it does not usually change over time, making it ideal for biometric identification. Most of the time, people's eyes also remain unchanged after eye surgery, and blind people can use iris scanners as long as their eyes have irises. Eyeglasses and contact lenses typically do not interfere or cause inaccurate readings [2][6] .
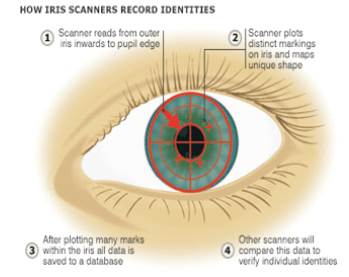
Figure 2. Iris Scanners Record Identities
The patterns of one person's two eyes are quite different from each other and even genetically identical twins have different iris patterns. The change in eye color is not affect the identification of iris. [1][6] .
In the mobile voting system, the voter and the election commission are in separate positions; it may be next district, or may be the other state. So we have to identify the person, whether he/she is a specified person to vote. To identify the respected person iris scanning is used in mobile voting. The first process of mobile voting is to collect the data of voters in the list. The iris of all voters is scanned and the scanned iris code is saved in the election in the form of encrypted.
The two distinct stages involved in the iris scanning are:
It is the first process of iris scanning, the voter has to scan their eye using the iris scanner, and then it is digitally photographed with both ordinary light and visible infrared light. The infrared helps to show up the unique features of darkly colored eyes that do not stand out clearly in ordinary light. These scanned items are then turned into “Iris code” [2][6], which is shown in Figure 3. is stored alongside of voters name and other details in the election database. Likewise iris code of all the voters is listed in the election database system. This enrollment process is usually takes no more than a couple of minutes. In this system about 240 unique features are identified which is 5 times more “point of comparisons” than fingerprint recognition. this process is done by the election commissions eye scanner and database system.

Figure 3. 512 Byte Iris code
This process is done by the election database system at the time of voting.
Verification:
Encrypted Iris code = Encrypted Reference Iris Code
Input1 = Reference Code
Cryptography is a physical process that scrambles information by rearrangement and substitution of content, making it unreadable to anyone except the person or system capable of unscrambling it. In mobile voting system the goal of cryptography is to make it possible for voter and the database management system to exchange a message in such a way that other people can't understand the message. If any other people trying to read the vote that was not intended for them and they initially don't know the encoding method, it's called the “Cracking” the code. Here the receiver's public key and the receiver's private key are the voter iris recognized sample code. This sample code is unique, so the transmission of vote from the voter only possible. This cryptography helps to voting process without fake, cheating process during the transmission of the data. Even if any other ceases the data they can't read it, because it's in encrypted form. The encryption algorithm used for this purpose is very efficient algorithms like RSA, which should be common to both voter and the election database management system.
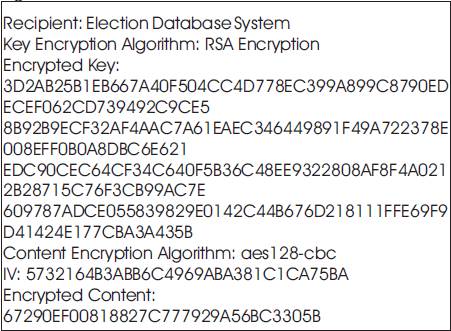
Generate two large random primes, p and q, of approximately equal size such that their product n = pq is of the required bit length, e.g. 1024 bits. [5][7]
If Iris code = "Hello world!"
That is, the 12 bytes in hex format,
PT=48656C6C6F20776F726C6421
Then, using the 128-bit session key from above,
KY=4E636AF98E40F3ADCFCCB698F4E80B9F
And the uniquely-generated 128-bit initialization vector (IV)
IV=5732164B3ABB6C4969ABA381C1CA75BA
The cipher text using AES-128 in CBC mode with PKCS padding is,
CT=67290EF00818827C777929A56BC3305B.
The voter would then send a transmission to the election database including the following information in some agreed format:
Eye scanner is uploaded in the mobile. The voter eye is recognized by iris recognizer. Then the output iris code is encrypted by using encryption [5] algorithm and then sends to the election database system through mobile networks by short code instant messaging system. [8][10] The election database systems receives the input data which has been sent by the voter and compare it with the reference iris code encrypted parameter. If both are same the election database system sends the parties list to the voter else reject the input. Then the voters have to choose the vote and encrypts data before send it[4]. After that the database management system sends the “received” message to the voter. Again the voters have to sends the iris code in the form of encrypted [4]. If the two iris sample code and the iris reference code are same, the eye scanned iris code [3] are decrypted [5] including with the party list and the vote will be saved in the election database management system. So it is very secured process as shown in Figure 4.
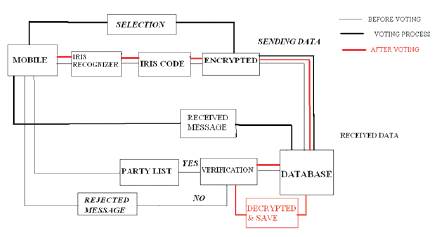
Figure: 4 Main process of Mobile Voting System
The transmitting and receiving of the datum are done by using the mobile networks, so the process is very fast [9]. The election data base system is provided region wise in order obtain the fast process without colliding of datum. so the human interaction in the process of voting is only the voter. While scanning the eye during the iris recognition the distance between the eye and the mobile is 20-25cm [4],[7],[5], which gives better scanning clarity. The process is automatic, so man interaction is very rare except the voter. The counting of the votes and the publishing of results are done very simpler and faster than other voting systems presenting in actual practice.
This method of mobile voting is an enlighten feature in mobile communication technology. By this system we won't spend and waste our time and energy by standing in queues for voting. And important note is that there is no chance for fake votes. For this voting system a single database setup is enough to manage the voting process. It's a security assured method, because the systems provides security for voting, is iris recognition and cryptography. This intelligent system should not allow to cheating process. In the mobile voting technology the main aim is to introduce an advance method of voting, that's too a social project that helps the public and the government.