Figure 1. Four bands (LL, LH, HL, HH) (Kamesh et al., 2017)
The rapid spread of the internet, along with the comprehensive development of digital technologies and easily reproduced digital media, has increased the popularity of media. Nowadays, exchange and transmission of digital images through internet is increasing and thus the protection of image is critical. This has initiated more researchers to develop efficient methods in digital image content protection. Digital watermarking is one of the ways to achieve protection in images. Digital watermarking is a process by which secret data is encrypted into the image without affecting the visual quality of the copyrighted image. This paper presents a block-based image watermarking technology using Discrete Wavelet Transformation (DWT) that does not affect the human visual system. The host images with digital watermark are exposed to cyber attacks when accessible through the open domain in the internet. The experimental results of this study shows that the proposed image watermarking method protects the invisibility of the watermark.
Internet evolution has offered several multimedia tools which provided easy way to duplicate, manipulate and redistribution of image files. This has raised a concern for multimedia security. Digital watermarking is an effective way to tackle this situation. Watermarking is a process to hide some information into the original image imperceptibly (Sharma & Kumar, 2016). This watermark information can be copyright details, authentication data or controlling details which determine the copyright owner of the digital works and certify the authenticity and integrity of image. Using suitable technologies, these details can be used to control copying and reusing the image without the knowledge of the copyright owner, achieving the purpose of copyright protection. Depending on the original image, watermarking techniques can be is classified into blind and non-blind watermarking. Discrete wavelet transform (DWT) has excellent spatial localization and multi-resolution characteristics which are similar to the theoretical model of human visual systems (Makbol et al., 2016), and hence it is more frequently used in digital image watermarking. In image watermarking method, invisibility and robustness are the main requirements for developing. This method is based on spatial domain and transform domain. The image watermarking making method is based on combined DWT and matrix decomposition and thus robust against both geometric attacks and image processing attacks.
In our knowledge, most of the papers focused on SVD based image watermarking. Some research papers are associated with the image watermarking based on QR decomposition and it has been proved that the image watermarking method based on QR decomposition offer better compared to SVD and DCT.
Shaikh Shoaib and R. C. Mahajan in a paper on video watermarking with 3-level DWT proposed a technology which is perceptually invisible. Perceptually invisible means the watermark is embedded in video in such a way that the modification to the pixels values is not noticed. In proposed work using two different videos and different logo images and shown how watermark is detected and watermarks not detected. The secret key given to the watermark image during embedding process and while extracting the watermark image the same secret key is used. The result of MSE should be as low as possible to have less error and the PSNR should be as high as possible to have better quality of reconstructed video (Shoaib & Mahajan, 2015).
Uma Rajput and Nirupma Tiwari proposed a novel technique for RGB digital watermarking based on2- Discrete Cosine Transform with discrete wavelet transform algorithm. For this use of two images- first and second is cover image and secret image. For providing better security, we worked on RGB elements. In this performed on two algorithms first one is 2-DWT and secondly 2-DCT applied on RGB elements. Experimental results Shows that the value PSNR, NE value, and PSNR reach up to 56%. Baiyinget.al In this paper proposed a robust audio watermarking scheme based on LWT-DCTSVD, DWT-DCTSVD with exploration of DE optimization and DM quantization. The attractive properties of SVD, LWT/DWT-DCT, DE and quantization technique make our scheme very robust to various common signal processing attacks. Meanwhile, the proposed scheme is not only robust against hybrid and desynchronization attacks, but also robust against the StriMark for audio attacks. The experimental results validate that the proposed watermarking scheme has good imperceptibility too. The comparison results with other SVD-based and similar algorithms indicate the superiority of scheme (Rajput & Tiwari, 2015).
Vinita Gupta, and Atul Barve published their literature survey on digital image watermarking. They also classified the watermarking techniques based on the transform domain where the watermark is embedded. Also, explain the watermarking properties, applications and techniques used. This paper also shows the different techniques and discusses the important technology called QR code which can be used in future work (Gupta & Barve, 2014).
Manjinder Kaur and Varinder Kaur Attri discussed on the different types of watermarking (Kaur & Attri, 2016) and some of them are listed below:
The watermark is visible that can be a text or a logo. It is used to identify the owner.
The watermark is embedded into the image in such a way that it cannot be seen by human eye. It is used to protect the image authentication and also prevent it from being copied. Invisible watermark can be further classified into three types:
Robust Watermark aims to embed information in a file that cannot be easily destroyed. They are designed to resist any manipulations that may be encountered. All applications where security is the main issue use robust watermarks.
They are designed with very low robustness. It is used to check the integrity of objects.
They are differentiated in accordance with the secrecy requirements for the key used to embed and retrieve watermarks. If the original image is not known during the detection process then it is called a public or a blind watermark and if the original image is known it is called a non blind watermark or a private watermark.
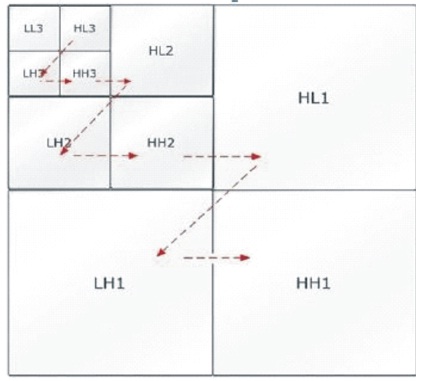
The use of wavelet transform addresses the capacity and robustness of the information hiding of the system features (Shete et al., 2019). The Haar Wavelet Transform is the simple method of all wavelet transform. In this the low frequency wavelet coefficients are generated by average pixel values and high frequency coefficients that are generated by taking half of the difference of the same two pixels. The four bands obtained are LL, LH, HL, and HH.
The LL band is called as approximation band, which consists of low frequency wavelet coefficients, and contains significant part of the spatial domain image. The other bands are called as detail sub bands which consist of a high frequency coefficient and contain the edge details of the spatial domain image. Integer wavelet transform can be obtained through lifting scheme. Lifting scheme is a technique it convert DWT coefficients to Integer coefficients without losing information.
Step 1: Column wise processing to get H and L
H = Co-Ce
L = Ce - (H/2)
where Co and Ce is odd column and even column wise pixels value.
Step 2: Row wise processing to get sub bands LL, LH, HL and HH, Separate odd and even rows of H and L.
Hodd– odd row of H,
Lodd– odd row of L,
Heven– even row of H,
Leven – even row of L.
After applying 1st level DWT of decomposition, there are 4 sub-bands: LL1, LH1, HL1, and HH1. For each successive level of decomposition, the LL sub-band of the previous level is used as the input. To performed second level decomposition, of the DWT is applied to LL1 band which decomposes the LL1 band into the four sub-bands LL2, LH2, HL2, and Hh2 (Figure 1). To performed third level decomposition, of the DWT is applied to LL2 band which decompose this band into the four sub-bands LL3, LH3, HL3 and HH3 (Shete et al., 2019).

Figure 1. Four bands (LL, LH, HL, HH) (Kamesh et al., 2017)
The purpose of digital watermarking is to insert the secret data into the image without significantly affecting the visual quality. This presents a block-based image watermarking scheme based on the transformation and human visual system in the discrete wavelet transform domain. Each level of DWT decomposes an image into four sub-bands namely a LL, HL, LH HH. Most of the information contained in the original image is concentrated into the LL sub band after one level DWT. The LL sub band can be decomposed to obtain another level of decomposition. The decomposition continues on the LL sub-band until the desired result is reached.
The QR decomposition expressed a matrix as the product of orthogonal matrix and an upper triangular matrix. The letter Q is a substitute for the letter O from "orthogonal" and the letter R is from "right", an alternative for "upper".
For any matrix A, we can write
A =QR
Operations based upon orthogonal matrices are very desirable in numeric computation because they do not magnify errors, either those inherited from the underlying data, or those introduced by floating point arithmetic (Moler, 2016).
Among several methods to compute QR decomposition, Gram-Schmidt process is used by most applications. The feature of QR decomposition is that the size is flexible and it is not bound to be a square matrix.
Gram-Schmidt process has its own advantages and disadvantages. The Gram-Schmidt process is inherently numerically unstable. While the application of the projections has an appealing geometric analogy to orthogonalization, the orthogonalization itself is prone to numerical error. A significant advantage however is the ease of implementation, which makes this a useful algorithm to use for prototyping if a pre-built linear algebra library is unavailable.
The case of minute extraction is discussed as this technique will be used in the proposed watermarking system to protect the digital images.
The ridge coordinates and extract ridge features are defined between two minutiae. In the ridge-based coordinate system is defined by a minutia (called origin) and vertical and horizontal axes starting from the origin minutia. To represent the relative position of the minutiae according to the origin, horizontal axes can be defined. The ridge- based on coordinate system, the ridge features that described the relationship between the origin and arbitrary minutiae. To determine the Ridge Type (RT), each minutia is first classified as an end point or a bifurcation. If a minutia is an end point, there is only one ridge belonging to the minutia. If the minutia is a bifurcation, there are three ridges connected in the minutiae.
A fingerprint is a distinct pattern of ridges and valleys on the finger surface of an individual. A ridge is defined to be a single curved segment whereas a valley is the area between two adjacent ridges. And the dark areas of the fingerprint are called ridges and white area that exists between them is known as valleys.
In case of a fingerprint identification system, the captured fingerprint images are needs to be matched against the stored fingerprint templates of every user in the database. It involves a lot of computation and search overhead and thus we need a fingerprint classification system that will help us to severely restrict the size of the templates database. To accomplished, we extract the minutiae features and match against the incoming fingerprint. The template size of minutiae- based on the fingerprint representation is small and the most of the fingerprint identification systems are based on minutiae.
Minutiae points are the major features of a fingerprint images are used in the matching of fingerprints. These minutiae points are use in the uniqueness of a fingerprint image. A good quality of a fingerprint image can have 25 to 80 minutiae depending on the fingerprint scanner resolution and the placement of finger on the sensor The feature extraction can be shown in Figure 2.
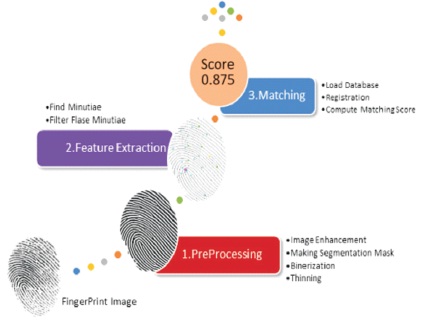
Figure 2. Feature Extraction (Alilou, 2020)
The duplicate copy of a digital media is as good as the original and hence the issue of piracy and copyright protection is alarming. Illegal production and unauthorized distribution of digital media has become a high alarming problem in protecting the copyright of digital media. Digital watermarking has been proposed as one of the solution for the copyright protection and digital right management. (Jothibai, 2017).
DWT is applied to provide more security in the watermarking process and there is no biometric is given as key. A watermark is designed for residing permanently in the original digital data even after repeated reproduction and circulation. An optimized watermarking embedding and extraction method is supposed to meet necessities of perceptual transparency, robustness to sustain signal processing attacks and also needs to be secure. Perceptual transparency means that the insertion of the digital watermark in the host image does not change the visibility of image.
The proposed ridge features are four types: ridge count, ridge length, ridge curvature direction, and ridge type. These ridge features have some advantages in that they can be represent the topology information in entire ridge patterns existing between two minutiae and are not changed by nonlinear deformation of the finger. For instance, patient data inserted in the image is defined as a posterior control mechanism since the content was still available for the interpretation and protected. Spatial Domain Wavelet Transform (DWT) features watermarking system substitutes or modulates the image pixels spatially with the message.
The Wavelet Packet Transform (WPT) are the most commonly adopted transforms in the digital watermarking world. Each of the selected blocks is then processed individually to embed the watermark. Wavelet transform is applied as a wavelet transform on each selected block. Thus, wavelet properties are employed to achieve higher performance by the proposed scheme. Wavelet transform has gained popularity because of its wavelet properties. This method requires less computation time than Cosine transform, and wavelet transform and Wavelet Packet Transform (WPT) is more accurate in the modelling aspects of HVS because of the multi-resolution property of any wavelet transform. Advantages of Robustness in watermarking. Ownership assertion can be most secured one. This system using a minutia approaches. This system recognition is accurate. This system identifies quickly.
Figure 3 shows the block diagram of the proposed method.
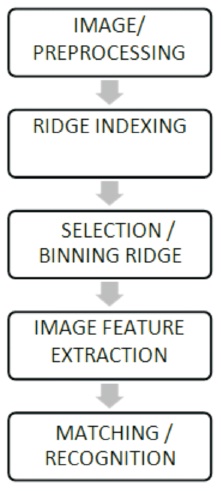
Figure 3. Block Diagram of the Proposed Method
The inter module dependency diagram can be shown in Figure 4.
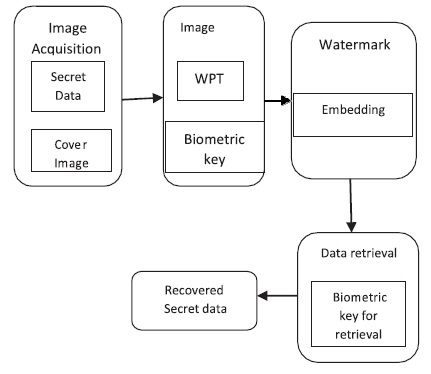
Figure 4. Inter Module Dependency Diagram (Kowsalya, & Subanandhini, 2016)
The proposed system was verified using MATLAB and the results of the images are presented from Figures 5 to 10.
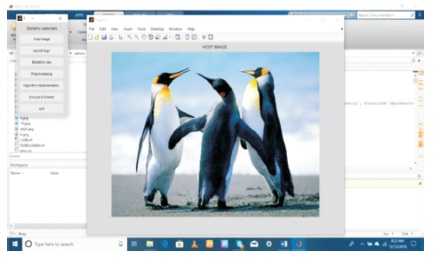
Figure 5. Host Image
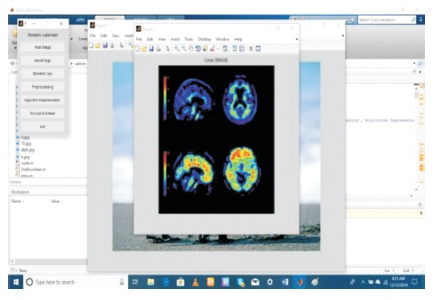
Figure 6. Embedded Secret Image
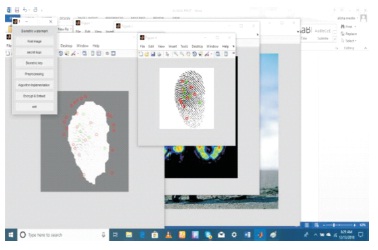
Figure 7. Biometric Key
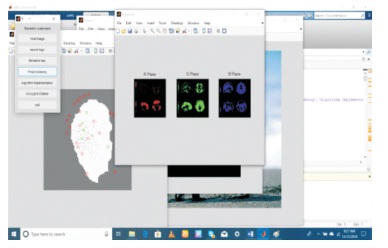
Figure 8. Preprocessing with the Biometric Key
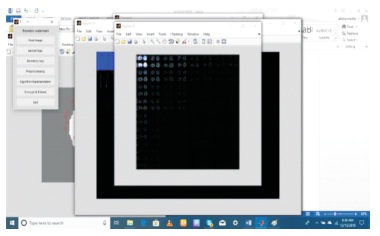
Figure 9. Implementation of the Algorithm
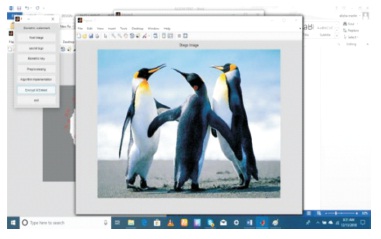
Figure 10. Encrypted Image Embedded with Invisible Watermarking
In this paper, by using this proposed technique, biometric data was inserted in the image using the defined posterior control mechanism since the content was still available for the interpretation and protected. Optimized image based on FA in DWT-QR domain is proposed. Spatial Domain Wavelet Transform (DWT) features watermarking system substitutes or modulates the image pixels spatially with the message. The experiment results show that the proposed image watermarking method is not only is invisible, but is also robust against most of the image processing attacks.