
Table 1. Evolving Blockchain Application Domains (Rosa et al., 2017)
This paper reviews scholarly articles on the application of blockchain technology for secure electronic voting (e-voting). Furthermore, the feasibility of using blockchain technology to replace the existing manual or semi-digitized voting system in developing countries with Nigeria as a case study is performed. To analyse the current state and preparedness of adopting Blockchain Enabled E-voting (BEEV) system in Nigeria, this paper employs the qualitative SWOT (Strengths, Weaknesses, Opportunities, and Threats) and PEST (Political, Economic, Social, and Technological) analysis approach. This evaluation leads us to identify internal and external factors and the strategic direction in adopting BEEV in Nigeria. It is the authors' opinion that this approach could also be tailored to evaluate situations of other developing countries.
“It is enough that the people know there was an election. The people who cast the votes decide nothing. The people who count the votes decide everything” - Joseph Stalin. Democracy is the pillar of every political system and ensures an equal and fair voting system by guaranteeing the right of all eligible voters to freely vote for their preferred party or candidate. The concern on every voters' mind is whether their vote will count and if the votes recording and the final result is accurate. Despite the tremendous technological advancement and digitization of numerous spheres of modern life, most elections are still conducted using paper-ballot and usually offline, especially in developing democracies around the world. Traditional ballot- based voting have the following inherent flaws (Meter, 2015; Oke, Olaniyi, Aboaba, & Arulogun, 2017; Olaniyi, Arulogun, & Omidiora, 2012).
Due to the complexity, cost and time associated with conducting free, fair and credible elections, and the accusations and counter-accusations that follow every election cycle, attention is moving towards adopting current technological advances, away from the traditional paper-ballot voting system. This is in order to eliminate human errors, fraud, and biases, thereby improving trust in the electioneering processes. Consequently, over the years, scholars and democratic experts have advocated for an e-voting (Ibrahim, Kamat, Salleh, & Aziz, 2003; Jan, Chen, & Lin, 2001) to address issues inherent in traditional ballot-paper based voting earlier outlined. This will improve voters' turnout and trust in elections by directly using electronic devices on the internet or voting software application to improve the overall democratic processes. However, the central concern in adopting an electronic voting (e-voting) system is security.
Security challenges in e-voting are well articulated in numerous literature such as (Oke et al., 2017; Chiang, 2009; Dill & Rubin, 2004; Shamos & Yasinsac, 2012) and drawbacks of public key cryptographic implementations in e-voting systems (Meter, 2015). Drawbacks include computational power needed to decrypt votes, possible hacking through random number generation, and system complexities. Therefore, security remains the major concern since voting is done through the internet or dedicated network online (Ayed, 2017) as well as trust in a central body to manage elections. Security requirement of electronic voting includes eligibility, coercion freeness, availability, anonymity, integrity, correctness/accuracy, robustness, fairness, receipt-freeness, voter verifiability, and universal verifiability (Meter, 2015; Wu, 2017).
Trust and privacy are the key elements a voter demands during an election. Trust that the voter's vote will count and privacy that the voter's choice remains personal. Centralization of the internet and cloud computing platforms is another concern since data is residing in a central location and vulnerable to cybersecurity attacks (Al-Saqaf & Seidler, 2017). Attention is therefore shifting to blockchain Distributed Ledger Technology (DLT) as a viable option for application in a peer-to-peer digitized voting system, beyond the traditional blockchain application domain in currency and finance. This drive is due to blockchain's perceived security, transparency, verification, and compliance attributes in a distributed environment, that could address shortcomings inherent in e-voting systems.
Blockchain is a peer-to-peer (P2P) Distributed Ledge Technology (DLT) for transparent transaction devoid of a trusted middleman that leverages on the internet, originally developed for crypto-currency virtual currency transactions. The initial focus of blockchain was in the financial sector, but it currently has applications in numerous areas majorly to enhance cybersecurity. Blockchain is defined as an appendable immutable universally distributed open ledger (Kimbel, 2018). The key elements of this definition rests with the keywords: Here apendable means can add to the ledger, immutable means nothing can be deleted or altered from the ledger, universally distributed means equal accessibility of everyone to the same copy of the ledger each time information is updated to ensure validity of all transactions, which makes blockchain trustworthy and an open ledger database, where all transactions are recorded in a clear, shared and transparent manner. The transformation blockchain is envisioned to bring to society will potentially be more than the internet. Whereas internet changed the way information is shared, blockchain will potentially transform the way transactions are done, with trust as a core ingredient. Blockchain finds viable application potentials in many fields, such as in education (Rooksby & Dimitrov, 2017), healthcare system (Kuo, Kim, & Ohno-Machado, 2017), smart cities (Biswas & Muthukkumarasamy, 2016), electricity industry (Pop et al., 2018; Park, Lee, & Chang, 2018; Sikorski, Haughton, & Kraft, 2017), legal industry (Dontsov, 2018), Industry 4.0 (Bahga & Madisetti, 2016; Hofmann & Rüsch, 2017; Rabah, 2017), music industry (O'Dair, Beaven, Neilson, Osborne, & Pacifico, 2016), eGovernment to fight corruption and poverty (Ølnes, Ubacht, & Janssen, 2017), tax administration (Deloitte, 2017), in Agriculture through direct funding to farmers (Lan, Brewster, Spek, Smeenk, & Top, 2017), charity and NGO to establish direct link between the donor and donee (Charities Aid Foundation, 2015a, 2015b), electronic voting (Meter, 2015; Ayed, 2017; Bistarelli, Mantilacci, Santancini, & Santini, 2017; Hegadekatti, 2017), and so many other areas that rely on third party to establish trust. Blockchain is therefore, evolving beyond its initial application in currency and in the financial sector to other numerous domains collectively referred to as Blockchain version 3.0. The summary of these evolving blockchain application domains are outlined in Table 1.

Table 1. Evolving Blockchain Application Domains (Rosa et al., 2017)
As reported in (Lielacher, 2018), Sierra Leone took a bold but cautious step towards utilizing blockchain-based distributed ledger technology, by leveraging on blockchain-based digital voting platform owned by a Swedish start-up company called Agora, to store and verify the votes cast during the country's presidential elections. The country however still maintained the same paper-based ballot casting process it has employed in the past elections. The process includes manual verification of voters' relevant identification documents and casting of their ballots. Subsequently, the voting results were then manually recorded into Agora permissioned blockchain platform, with Agora appointed by relevant stakeholders to act as the party to validate the data contained inside the network. Two main positives came out of this process, timely delivery of results and avoidance of fallouts or violence associated with electioneering processes in the country. Even though Sierra Leone did not use the Agora blockchain platform for the entire voting process, it clearly epitomises that democratic advancement through fair and transparent elections could be achieved using blockchain technology in Africa.
According to (Bitcoin Africa, 2017; UN Economic Commission for Africa, 2017), a growing number of blockchain Financial Technology (FinTech) start-ups are springing up in Africa, mostly in the financial and non-cash remittance ecosystem. Some of these start-ups and their application domains are enumerated in Table 2. In the long run, a number of these start-ups will eventually venture into other application domains driven by opportunities to solve numerous problems in the region including BEEV because of high stakes associated with elections thereby improving trust and transparency.
Blockchain is an integrated technology made up of several concepts and techniques, such as cryptography, mathematics, economic model, and P2P networks based on distributed consensus algorithm (Lin & Liao, 2017). Generally, there are three types of blockchain technology, namely 1) Public blockchain – everyone got assess to transactions and are stakeholders in attaining consensus, as a permmissionless blockchain with no centralized authority required for the verification process. Bitcoin and Ethereum are examples of public blockchain; 2) Private blockchain - There are restrictions on the distributed ledger data access, which is controlled by a few designated authorities, usually owned by an individual, government, or private business. It operates as a permissioned blockchain with a central authority for process verification; 3) Consortium blockchain – This is a hybrid blockchain implementation which can be private or public. But assess to distributed ledger data is permissioned. Examples are Eris and Hyperledger.
Secure Hash Algorithm (SHA-256) encryption is the most used encryption and mostly associated with Blockchain, due to the unique attribute of its Hash function, which produces unique outputs when specified by different inputs. A Hash function is the private and public key uniquely created to identify an individual at the same time preserving privacy. It was originally developed by United States National Security Agency (NSA) to ensure uniqueness of codes (Ayed, 2017). Figure 1 depicts the logic flow of SHA-256 encryption representation. A SHA-256 is made up of 256-bit encryption, 32 bytes, and 64 alphanumeric characters long every time. For example, an input plaintext of Blockchain and blockchain yields uniquely different hash keys, even with just difference of the first letter capitalised:
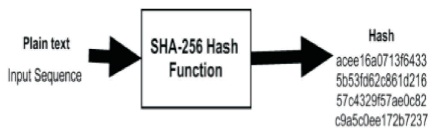
Figure 1. SHA-256 Hash Function Logic Representation
Blockchain:
625DA44E4EAF58D61CF048D168AA6F5E492DEA166D8 BB54EC06C30DE07DB57E1
Blockchain:
EF7797E13D3A75526946A3BCF00DAEC9FC9C9C4D51 DDC7CC5DF888F74DD434D1
However, there are other cryptographic algorithms that are in use in electronic voting systems like RSA public key cryptography, Zero-knowledge-proof, Homomorphic encryption, Mix-nets scheme, Secret sharing and Threshold encryption, Everlasting privacy, and Blind signatures. For details, readers can refer to (Meter, 2015).
The structure of blockchain is basically made up of the block header and block body. The block header is made up of encrypted unique hashes, while the block body is made of transaction counters and transactions saved in a block (Ayed, 2017). A summarised structure of the blockchain block structure is highlighted in Table 3 (Ayed, 2017).
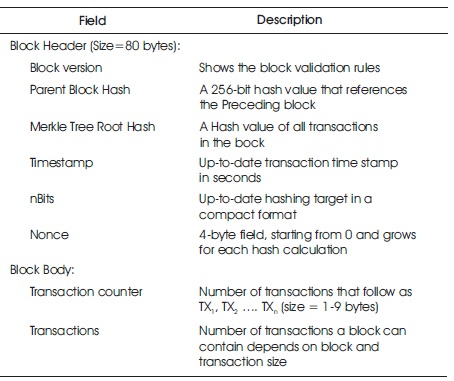
Table 3. Blockchain Single Block Structure
The key technical challenge in Distributed Ledger Technology (DLT) is the process of reaching consensus. When a community of computers or nodes on the network need to reach an agreement on how transactions happen, information should be updated in the distributed ledger without trusting any one single computer or node. In order words, it is a way of deciding who in the community of computers has a right to add the next block onto the blockchain through arriving at a mathematical solution on supercomputers, to avoid chaos on the chain. The whole idea is to have a ledger forming a fine single-chain as blocks are added to the blockchain, rather than a chaotic tree-like blockchain, which results to a massive amount of wasted energy on computation and no consensus attained. This chaotic tree- like occurrence is technically referred to as forks. The specific technical challenges include high computational cost, massive energy consumption, scalability, transaction throughput and speed, security and fairness in reaching a consensus. In the following subsections, the major distributed ledger consensus protocols and approaches are discussed.
1.1.1 Proof-of-Work (PoW)
PoW was started and popularised by Bitcoin (Nakamoto, 2008), it is based on the mechanism, where the longest block full of transactions is added to the next block. The drawbacks of this approach are the high computational cost associated with reaching a consensus and the massive amount of electrical energy needed by the supercomputers in the processes. There is also the issue of scalability and transaction throughput per second. With this bitcoin-based protocol, only seven transactions per second are feasible. On the order hand, some experts are of the opinion that the slowness is for security reasons, to allow all nodes verify all transactions and allow time to agree on a consensus, in the process ensuring fairness and averting a fork. But with transactions such as in financial markets or stock exchanges where thousands of transactions occur per second, there is the need to scale up the transaction throughput from what is obtainable with this bitcoin protocol. Even though security experts believe that a combination of PoW with nonce value and SHA-256 hashes translate to high security, there remain other problems associated with PoW systems, such as improving scalability and better consensus reaching mechanisms. These challenges inherent with PoW motivates researchers to find new consensus approaches (Vukolić, 2015).
1.1.2 Leader-Based System (LBS)
In LBS, all nodes in the network inform a designated leader of their transactions, the leader then decides on the order of transaction and notifies the entire network. However, there are security challenges with this approach. Scenarios could be a deliberate Distributed Denial of Service (DDoS) virus attack on the designated leader, which will lead to total system collapse. Examples of Leader-based systems are PBFT, Raft, and Paxos.
1.1.3 Proof-of-Stake (PoS)
PoS is usually referred to as economy-based systems. It is an approach where the community of nodes vote based on what they think the consensus would be, by voting with the majority. The idea here is to observe carefully voting patterns of other nodes on the network and vote with the majority to reach consensus. It is called economy-cased system because it is likened to Adams Smiths theory of moral sentiments in economics, as voting judgement is inspired by sentiments merely observing how the majority are voting. It is more like sympathy voting. PoS consumes less energy compared to PoW and assumption that trustworthy nodes control at least 51% of network mining power to ensure a secure system. However, there are the possibilities of collusion by bad stakeholders to gather the required 51% mining power. This raises the question of how secured the system is. Its main drawback is nothing at stake problem. Owing to these challenges new PoS protocols have been designed and proposed such as delegated proof of stake (DPoS) and other hybrid systems of PoW, LBS and PoS, by combining the advantages of these protocols.
1.1.4 Voting-Based System
This is a consensus reaching protocol, where an individual node sends a vote over the internet, which make it a theoretical extremely slow approach. Hence, it has found very little real-world application.
At this junction, based on the consensus protocols described above, it is pertinent to briefly introduce the concept of Byzantine Fault Tolerant (BFT) (Castro & Liskov, 1999). BFT means the moment in time during transactions when it is clear that consensus is approaching and when consensus is attained and the mathematical surety that all nodes will reach exact consensus. BFT can either be asynchronous Byzantine (aBFT) or partly asynchronous Byzantine (paBFT), depending on the prior assumptions about existence and non-existence of trustworthy stakeholders in the network environment. With aBFT assuming that there exist untrustworthy nodes in the network environment and paBFT assuming otherwise.
Hashgraph is a fully aBFT, based on the mathematical assumptions that consensus will be attained if less than one-third of the nodes are untrustworthy. Hashgraph leverages on a gossip protocol to send messages to all computer nodes on every transaction sent and received on the network to facilitate a quicker time of reaching a consensus agreement. It is essentially sending two compressed hash messages by a node to the next node, eventually forming a complete histor y of all communication in the entire network, referred to as hashgraph in memory. With aBFT based consensus protocols, like the hashgraph, there is higher surety that consensus is going to be reached as opposed to nonbyzantine based protocols like PoW or PoS, which merely based on confidence level over time. Hashgraph addresses the concerns associated with PoW, these are increased scalability and transactions throughput, significantly lower computational overhead and power consumption and security. Readers could refer to (Baliga, 2017; Chalaemwongwan & Kurutach, 2018) for details on blockchain consensus models.
Estonia, Norway, New South Wales, and Washington D.C. in the US are a few places around the world utilizing internet electronic voting systems. However, despite the advantages with e-voting systems, there are still security concerns bordering on transparency and centralization of the systems (Meter, 2015; Ayed, 2017). Such security issues are still the only major factors slowing down its adoption in other developed democracies such as France and UK.
The conduct of the general election in Nigeria before 2015 election was manually driven with a high level of electoral fraud by electoral authorities, government authorities, political gladiators, and erring voters (Olaniyi, Arulogun, Omidiora, & Okediran, 2015). However, the year 2015 witnessed the embrace of application of electronic voting technology to authenticate and validate voters. This application of Information and Communication Technology (ICT) brought partial sanity to democratic decision-making process, but with salient socio-technical issues, such as failed Smart Card Readers (SCRs) (Osho, Yisa, & Jebutu, 2015); Subscriber Identification Module (SIM) issues (Vanguard Nigeria, 2015); Voter's biometrics fingerprint verification issues (Kuo et a., 2017). While the proposal for the automation of the voter's identification and verification could not be approved by the parliamentary screening for 2015 election, the aftermath of the application continues to generate momentum and will eventually reverberate sooner or later if necessary examinations of previous and possible security threats are not anticipated and solved before future elections (Oke et al., 2017; Olaniyi et al., 2015; Ahmad, Abdullah, & Arshad, 2015).
The recent legislative amendment of the Electoral Act by the Nigerian Senate empowering the countr y's Independent National Electoral Commission (INEC) to introduce and implement any e-voting technology it deems suitable (Policy and Legal Advocacy Centre (PLAC), 2017; Verified Voting Foundation, 2017), is a good development towards the conduct of future elections and the possible adoption of BEEV in Nigeria.
There are a few organization currently attempting to build BEEV solutions, such as Civitas, Helios, TIVI, FollowMyVote, Bitcongress, Votecoin, and Kaspersky Lab Business Incubator's secure online voting based on blockchain called Polys (Kubjas, 2017). Most of these solutions are still in the developmental stages. Some works on BEEV in literature are briefly described as follows and summarized in Table 4.
Ayed (2017) conceptualizes a BEEV system to meet the requirements of authentication, anonymity, accuracy, and verifiability. With the first vote cast, the first transaction added to the block and referred to as the foundation block, which contains the elected candidate's name, on which other votes for that candidate are built on and voting transactions update for every casted vote. The system also made provisions for blank or protest vote, however, the system allows voting only once, which makes it impossible to change vote in case of a mistake. A general representation of the system from requesting to vote, authentication and vote casting, encryption and adding a vote to blockchain is depicted in Figure 2.
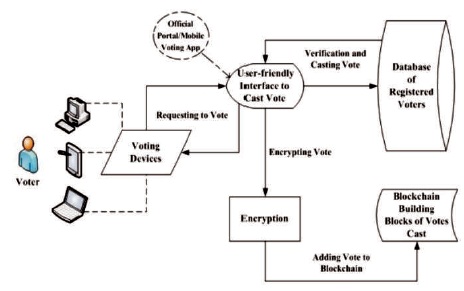
Figure 2. Conceptual BEEV Framework (Ayed, 2017)
In (Meter, 2015), a modified PoS consensus protocol with less computational overhead compared to PoW for a web-based BEEV system using Homomorphic with a threshold-encryption scheme is proposed. The author utilises a proprietary defined blockchain protocol named as BallotCoin, as against using Bitcoin protocol since a different consensus method is proposed and implemented.
The researchers in (Liu & Wang, 2017) proposed a BEEV system using blind signature encryption method for protecting voters' choices during elections. The authors claim that the solution satisfies all e-voting requirements, except the coercion-resistance attribute, which was challenging to implement due to the desirable transparency property of blockchain.
Artificial Intelligence (AI) and blockchain are two technologies that are potentially going to revolutionize society. As they have found global acceptance across all industries, from data analytics on Google or Microsoft platforms to the banking and financial sectors, as well as in smart cities, were they are being increasingly utilized. In blockchain, data is stored in an encrypted distributed ledger format across numerous computers, hence the need for new AI techniques that will be able to analyze and make sense of data stored in this format. Blockchain technology is not entirely immune to cybersecurity and software bugs because human programmers are central in the development and deployment of blockchain systems (Marwala & Xing, 2018), in addition to known flaws associated with encryption algorithms (Meter, 2015) and the frequent cyber-attack on bitcoin blockchain systems. An example will be a situation where the shortest chains are deliberately extended as oppose to longest block full of transactions to be added to the next block, leading to system collapse. Owing to these arguments the decentralized attributes of blockchain does not entirely hold. Going forward, numerous researchers are of the consensus that the security and other attributes of blockchain technology can be greatly enhanced by leveraging on AI techniques.
In this section, the authors employ a combination of SWOT and PEST analytical approaches based on a similar work by (Ha & Coghill, 2006), to assess the current state and prospects of BEEV system in Nigeria. They assess internal and external factors in Strengths, Weaknesses, Opportunities, and Threats in relation to Political, Economic, Social, and Technological influencing factors. It is outlined and summarized in Table 5.
Blockchain is still at the developmental stage in Nigeria, with early application entry mainly in the banking and financial sectors driven by fintech innovators. This is an early good sign for blockchain future development in other application domains for Nigeria including BEEV. However, the overall future of BEEV system is still in its incubation phase. But, if governments wish to adopt blockchain based voting, they would need to invest resources and most likely partner with the private fintech companies for a tailored BEEV system for the region. Adoption will depend on a favourable political, about-economic, and technological environment in Nigeria and the entire African region, as clearly shown in Table 5. Internet voting will inevitably be an option in the near future using smartphone devices or other electronic machines, and blockchain technology can be of great assistance for voting to become secure.
The internet pioneers’ initial vision was an independent and decentralised platform for information sharing, but over the years the internet has become too centralised and managed by a few tech giants such as Google. Will blockchain suffer the same fate? Only time will tell. Even though blockchain faces several challenges, such as security concerns, software bugs, inadequate legal and regulatory frameworks, etc., it is the authors' opinion that careful implementation of blockchain technology in the democracy of developing countries adhering to the troika pillars of people, processes and technology, could usher in peace, stability and sustainable development. However, adoption must be done gradually. It is observed that most BEEV works in literature are mostly theoretical and remains to be tried and evaluated in a large-scale real-world scenario. A mixed approach of existing voting systems and blockchain is proposed in the context of Nigeria for the short and medium term. A tailored BEEV is also emphasized for developing democracies taking into consideration, security and data integrity in fairness to scalability, flexibility, and complexity of blockchain architectural design choices that will be user- friendly. Finally, it will be interesting to apply a quantitative SWOT and PEST analysis in addition to incorporating stakeholders' support and expectations to evaluate BEEV in Nigeria. This is an open issue for future research endeavours.
This work was supported by the Department of Electrical and Electronic Engineering Science at the University of Johannesburg, South Africa.