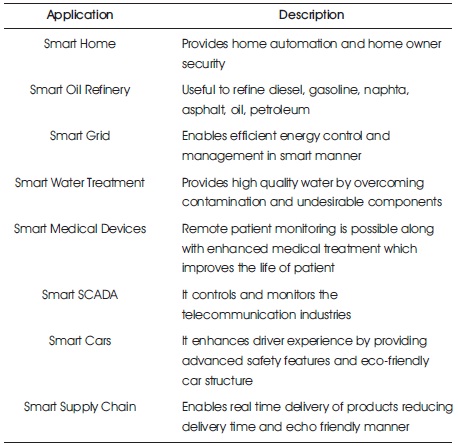
Table 1. CPS Applications
Cyber Physical System (CPS) is an integration of sensing, monitoring and analyzing devices connected with each other and establishes communication through internet. This system is prone to many cyber-attacks such as Man-In-The-Middle Attack, Denial of Service Attack, Cross-Site Scripting Attack, SQL Injection Attack, Password Cracking Attack, etc. Present security measures to protect CPS against cyber-attacks includes use of Intrusion Detection System (IDS), Firewalls, Anti-Malware, Anti-Virus, Anti-Spyware, HTTPS/SSH Encryption, Faradays Cage, Password Policy with periodic password change, Least Privileges, Strong Code, Intrusion Prevention System (IPS), etc. All these security measures have one or more challenges in their implementation such as reduced performance, higher power consumption, high transmission delays, huge cost, etc. Also, firewall, IPS, antivirus can only prevent the known threats. Today, many threats have no fixed pattern and their pattern are adaptable. Hence, all these intrusion prevention and protection systems becomes ineffective to protect the CPS against cyber-attacks. This paper reviews how Splunk Enterprise Security (Splunk ES) can be used to secure the CPS against all known, unknown and adaptable cyber threats with minimum user efforts and cost. Operation Technology Option in Splunk ES provides real time predictive analysis of cyber-attacks. By using artificial intelligence, machine learning and behavioral analysis, Splunk can predict any cyber-threat to CPS, 30 to 45 minutes in advance. Splunk can trigger the alert to CPS administrator who can implement the precautionary measures and protect the CPS before the actual occurrence of cyber-attack. This research performs the demonstration of cyber-attack on CPS and shows the result generated by Splunk ES.
Cyber Physical Systems (CPS) plays important role in Industry 4.0 revolution. Real time and accurate working of all remotely interconnected devices is the key power of CPS. CPS is integration of cyber system with physical system for exchange of various sensitive data in real time (Poon et al., 2006). The main role of CPS in industry 4.0 revolution is to fulfil the dynamic and agile production requirement to improve the efficiency and effectiveness of entire industry (Chun et al., 2010). Effective use of CPS in Industry 4.0 increases the gross value of German business up to 267 billion Euros by 2025 (Rad et al., 2015). CPS is a network of various interconnected embedded systems. These systems can monitor, analyse and manipulate various IoT related objects and processes. Sensors, aggregators and actuators are the three main components of CPS. CPS system adapt and control the physical world by sensing surrounding environment (Haidegger et al., 2020). Using real time computations, the CPS can change the run time processes (Siddappaji & Akhilesh, 2020). Table 1 shows various applications of CPS along with description (Yaacoub et al., 2020).

Table 1. CPS Applications
CPS can be used in power transmission system, communication system, agriculture system and military system (Chen, 2010). It can also be used in drones, robotics and autonomous cars (Bou-Harb, 2016; Miller & Valasek, n.d.) Medical services can be enhanced by the use of CPS (Sklavos & Zaharakis, 2016).
Large scale deployment of CPS are prone to multiple cyber-attacks due to the heterogeneous nature of CPS. The main reason for these attacks is the dependency of sensitive and private data on CPS. These cyber-attacks lead to catastrophic effects on CPS which leads to offensive network overhead with unaccepted latency.
CPS are also susceptible to zero-day vulnerabilities issue which must be minimized by regularly updating its software, application and operating system.
Several research papers explain various CPS security goals (Alguliyev et al., 2018; Humayed et al., 2017; Ye et al., 2016; Yoo & Shon, 2016). The method to maintain CPS security has been presented in Ye et al. (2016). Johnson (2010) and, Kumar and Patel (2014) explained challenges with CPS security issues. The big data security issues in CPS were explained in Kocabas et al. (2016) and Lai et al. (2019). IoT storage issues are explained in Abera et al. (2016). Operating system vulnerabilities were presented in Chen et al. (2016). The cryptographic algorithms can protect the CPS against cyber-attacks (Francillon & Castelluccia, 2008; Roemer et al., 2012). The comprehensive CPS security in terms of vulnerabilities, attacks and threats are not presented in the reviewed literature.
This paper presents the proactive CPS monitoring and threat detection using Splunk Enterprise Security platform.
Various critical infrastructures such as smart grid, agriculture, military, healthcare, automobile sector, supply chain uses CPS. Hence, CPS is an attractive target for attackers to gain the large financial gain. The goals of CPS security attacks can be carried out by criminals and terrorists for economic and political gain. These attacks break the confidentiality, integrity and availability of CPS information. Hence, for wide spread use of CPS in all sectors, CPS security against all external, internal, active and passive attack is of prime important.
The main motivation of this work is to identify all cyberattacks on CPS using Splunk ES before their actual occurrence. Also, post attack CPS condition can be determined by Splunk ES.
CPS architecture consist of various layers and components. The three layers, viz., perception, transmission and application communicate using different technologies and communication protocols. Table 2 details the components in each layer, their objectives, the target of the attach and the possible security measures.
At this layer, CPS collects the data from physical world using sensors and other components. This data includes heat, electrical signal, location, power consumption, sound and light signal.
This layer is subjected to passive reply, eavesdropping and port scanning attack. This attack mainly threatens the confidentiality and authentication of information. To secure CPS against these attacks data protection needs to be established using trust management and source authentication.
This layer interchanges the data between perception and application layer. This layer uses internet, Wi-Fi, cloud and access point for data transmission. This layer is subjected to Man-in-the-middle (MitM), Denial-of-service (DoS), Distributed-Denial-of-Service (DDoS), repudiation and replay attack. This attack breaches confidentiality, integrity, availability and authentication of data. Strong password policy and strong authentication method helps CPS to secure against these attacks.
This layer processes the received information from transmission layer, analyze the data and take the decision based on received data. This layer issues appropriate commands to sensors and actuators. This layer is prone to various attacks such as Malicious Code Injection, Botnets malware, Trojans, Worms and Buffer Overflow attack. These attacks mainly breaches the confidentiality, security, safety, and authentication of data.
To overcome the attack on this layer, strong authentication and authorization must be implemented. Trust management must be implemented along with Firewall, Intrusion Detection System (IDS) and Intrusion Prevention System (IPS).
CPS is highly prone to malicious code injection attacks (Chen et al., 2016; Francillon & Castelluccia, 2008). CPS is also susceptible to code-reuse attack (Roemer et al., 2012), and false data injection attack (FDIA) (Francillon & Castelluccia, 2008), non-control data attacks (Hu et al., 2016) and Control-Flow Attestation (C-FLAT) attacks are also observed on CPS. Some other common cyber-attacks on CPS are briefly explained.
Attacker intercepts the non-secure CPS network to obtain the sensitive credentials such as username and password etc. In passive eavesdropping, attacker only listens to the transmitted message by CPS components. In active eavesdropping, attacker performs scanning, spoofing probing and message tampering to gain the sensitive information.
In this attack third-party execute the malicious code on targeted CPS related employee browsers. This script achieves session hijacking, key stroke logging, unauthorized remote victim's machine access etc.
Attacker read and modify the SQL database of CPS. Some CPS are relying on SQL data management (Gudivada et al., 2018). Using SQLi attack, the attacker can shut down the SQL database and interrupt the CPS operation.
This attack mainly targets the CPS authenticity (Davi et al., 2010; Loukas, 2015). In this attack, attacker cracks the password of engineers and managers to gain the access of CPS related to sensitive data. This attack uses brute force attack method (Owens & Matthews, 2008) and dictionary attack method (Narayanan & Shmatikov, 2005).
Attacker can perform email phishing, vishing, spear phishing attack on CPS engineers and specialists. Using this attack, the attacker can hack the complete system of these professionals.
This attack affects the real-time CPS operation performance by intercepting the transmitted and received packets between Industrial Control Systems (ICSs), Remote Terminal Units (RTUs), and Programmable Logic Controllers (PLCs). This affects the availability of CPS.
Denial-of-Service (DoS) and Distributed-Denial-of-Service (DDoS) attack floods the CPS components by multiple requests and crash the CPS operation. This attack uses blackhole (Al-Shurman et al., 2004), teardrop (Solankar et al., 2015), ping-of-death (Yihunie et al., 2018), smurf (Kumar, 2007) methods, etc., to make the CPS unavailable for its legitimate users.
This attack exploits TCP handshake process by multiple SYN request to CPS. Attacker do not respond back to the server which results in buffer overflow error (Shrouf et al., 2014). This attack crashes the CPS.
In this attack, attacker scans for the weaknesses of CPS and on the identification of weakness, the selected CPS website will be manipulated watering hole attack and by backdoor, rootkits or zero-day exploit (Lemon et al., 2002).
In this, attacker steals the CPS data or harm the working of CPS devices using various malwares such as botnets, spyware, ransomware, trojan, rootkit, worm, virus, etc.
Splunk is a software platform used to analyse machinegenerated data from networks, hardware devices, servers, IoT devices, etc. User can create meaningful dashboard, reports, data models and alerts by monitoring the real time logs generated from these devices. Splunk Enterprise Security and Splunk IT Service Intelligence are two add-on of Splunk which are used to proactively monitor various cyber threats on all Splunk connected devices.
This paper uses Splunk Enterprise Security to monitor the cyber-attacks on CPS. The logs from various sensors and actuators located at perception layer are collected by using intermediate forwarder. These logs are then transmitted to heavy forwarder. This forwarder transfers the logs to indexer. Indexer stores these logs in the form of indexes. From search head one can search the required data over the CPS.
Figure 1 shows the data transmission from CPS to Splunk ES. The present system implements indexer clustering architecture with three indexers forming a cluster and they can index maximum up to 100 GB of data from forwarders. Forwarders takes the logs from all perception layer components using 514 UDP port and send these logs to indexers using 9997 TCP port. Indexer creates the indexes. Search head can read these indexed data using 8089 TCP port. The indexers used by Splunk Enterprise or Splunk IT Service Intelligence (ITSI) can index up to 350 GB of data. But the indexers used by Splunk Enterprise security can index maximum up to 150 GB of data.
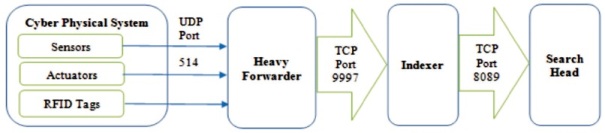
Figure 1. CPS to Splunk Enterprise Security Data Transmission
To improve the security visibility in Operational Technology (OT) environment, this research uses Splunk Add-on for OT Security. This add-on expands the capacity of Splunk Enterprise Security. The Figure 2 shows OT security posture dashboard. Relative risk of CPS of over time is shown by Risk Score. As shown in the Figure 2, totally 238 devices are connected with Splunk Enterprise Security out of which every device has medium risk with 66.9 score. Currently 35 devices are facing a security threat. The alerts are created by pre-configured correlation searches, i.e., notable events are generated in the occurrence of any security threat or unexpected CPS behaviour. Currently 9 notable events are created by Splunk ES which can predict that in next 30 to 45 minutes 9 types of cyber-attacks or any other threats will be injected to CPS. By this prior intimation the user can drill down the details of all these 9 notable events and secure the CPS from these 9 predictable situations.
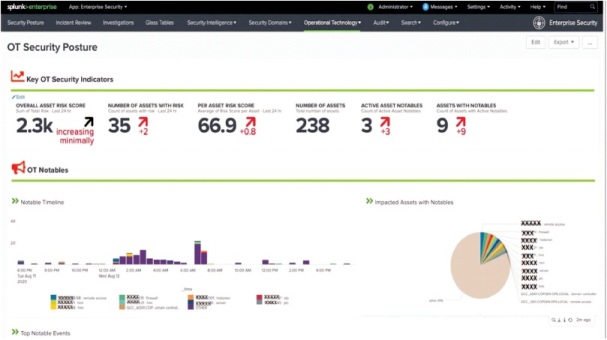
Figure 2. OT Security Posture Dashboard
After predicting the anticipated threat on 9 devices, user can perform the detailed investigation of each and every device in OT Asset Investigator dashboard as shown in Figure 3. In this investigation by OT Asset Information, user can understand the model of device, its location, risk priority, etc. By observing OT Asset Behavioral Indicator panel user can analyse the risk score change in last 48 hours, total number of devices connected with the risky device, total number of network ports accessed by risky device and total number of sessions created by risky device.
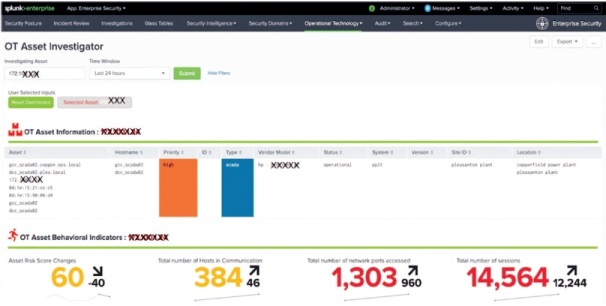
Figure 3. OT Security Investigator Dashboard
Using these two dashboards, user can estimate and identify the priority of the critical devices. Based on the analysis, the user can make a decision to secure the critical and high priority devices. After securing the high priority devises, the user can secure low priority devices. In this way, the entire CPS can be proactively monitored and secured with Splunk ES.
This paper explains the architecture of Cyber Physical System. Various attacks on each layer of this architecture are explained in detail. These attacks degrade the performance of CPS. Hence, it is essential to secure the CPS against all these cyber-attacks. After the cyber-attack, the working of CPS is already disturbed and mitigation efforts are unproductive. Hence, it is essential to proactively monitor the cyber-attack in CPS and remove the critical and high priority threats from CPS. This can be done using Splunk Enterprise Security platform. This platform uses OT Security add-on by which one can monitor the risk of all CPS components. The details of the OT Security add-on dashboards are explained in this paper.
Finally, it can be concluded that the Splunk ES is a good solution to proactively monitor all cyber-attacks on the entire enterprise CPS.