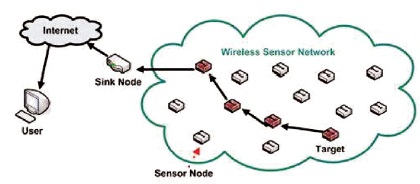
Figure 1. WSN Connectivity
Air media sensor network devices sense and communicate the information gathered from a monitored field through wireless links. The acquired data is forwarded through multiple nodes, and with a gateway, the data is connected to other networks. These networks are used to monitor physical or environmental conditions like sound, pressure, temperature and collectively pass data through the network to the main location. The WSN is incorporated into the wearable devices for various applications using various protocols to connect each node of the network. This paper describes the technology of implementing a WSN in a wearable device and the challenges imposed in working on the network.
Wireless sensor networks (WSNs) are becoming the most productive and cost-effective way of gathering data from the environment, and are considered one of the most important technologies of the twenty-first century in the field of pervasive systems. WSNs certainly cover a huge number of spatially distributed, little, battery-operated, embedded devices that are networked to collect, process, and transfer data to the operators, and control the capabilities of computing and processing. The communication between nodes can be done with each other using transceivers. The WSN connectivity layout is shown in Figure 1. In a wireless sensor network, the number of nodes can be in the order of hundreds/thousands (Abdelhedi et al., 2016; Fafoutis et al., 2018; Rampazzi et al., 2015). Each node observes a cross-section of the field independently with multiple sensors participating in a single sensing operation initiated by an emitting sensor. Joint sensing can increase the sensing region of an individual emitting sensor and generate multiple sensor measurements. Simultaneously, different time points helps to obtain efficient and cost-effective solutions to achieve safe, highly efficient and eco-friendly industrial production/service.
The wearable technology began from the invention of smart watches. Wristwatches were created in the late 1600s but were worn mostly by women as bracelets (Burns et al., 2010; Hossain et al., 2016). Over time, the watches became smaller and more precise and throughout history, many wearable's were designed and introduced in the market. Next to watches, computers were targeted to be fabricated as wearable devices. A group of graduate students from the Tisch School of Arts in New York designed a hoodie that sent pre-programmed text messages triggered by gesture movements (Chowdhury et al., 2011; Latre et al., 2007; Nabi et al., 2012; Nicosia et al., 2018; Xu et al., 2016). The need for wearable devices as listed by Khan et al. (2015) and Rahman and Boutaba (2013) are,

Figure 1. WSN Connectivity
Most of the time, the wearable devices are used for monitoring the health of an individual. In that case, it is necessary to monitor the heart rate, body temperature, breath rate and so on and the respective sensors are incorporated with the help of wearable devices. Today, there is a growing interest to use wearables not only for individual self-tracking but also for corporate health and wellness programs. The wearables create a massive data trail which employers could repurpose for objectives other than health. So more researches are done to study the dark side of wearables. The minimization of the size of sensors and electronic circuits based on the use of microelectronics has played a key role in the development of wearable systems. One of the major hurdles to the adoption of sensing technology, especially for wearable applications, has been the size of the sensors and front-end electronics that, in the past, made the hardware to gather physiological and movement data too obtrusive to be suitable for long-term monitoring applications. Recent developments in the field of microelectronics have allowed researchers to implement devices. This makes it easier for the deployment of hundreds of node in a network (Khan et al., 2015).
Hardware: The WSN is composed of numerous sensors as tiny nodes. In many applications, a WSN communicates with a Local Area Network or Wide Area Network through a gateway. The Gateway acts as a bridge between the WSN and the other network. This enables data to be stored and processed by devices with more resources, for example, in a remotely located server. A wireless wide area network is used primarily for low-power devices known as a Low-Power Wide-Area Network (LPWAN) (Woznowski et al., 2017).
Routing Protocols: Wireless sensor networks are generally small-size, low-energy and low-range un-attenuated sensor nodes. Simulation experiments demonstrated the validity of this novel approach in minimizing routing information stored at each sensor as shown in Figure 2.
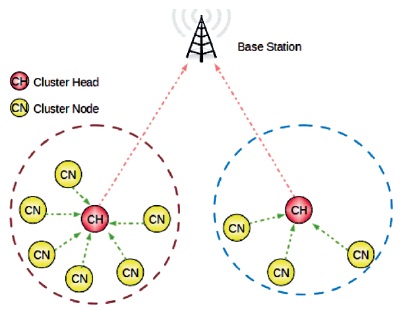
Figure 2. Clustering Routing Protocol
Operating Systems: Operating systems for wireless sensor network nodes are typically less complex than generalpurpose operating systems. They strongly resemble embedded systems for two reasons. First, wireless sensor networks are typically deployed with a particular application in mind, rather than as a general platform. Second, a need for low costs and low power leads most wireless sensor nodes to have low-power microcontrollers ensuring that mechanisms such as virtual memory are either unnecessary or too expensive to implement. It is therefore possible to use embedded operating systems such as eCos or uC/OS for sensor networks. However, such operating systems are often designed with real-time properties (Khalifa et al., 2015).
In the current market, there are different types of wearable devices:
Smart Watches: These devices work more than just telling the time for users. It shows the notification of the call, messages, emails, social-media updates and so on.
Fitness Tracker: It helps to keep track of the number of steps the user walks continuously and uses this information to report accurate data on calorie burn and exercise done by the user. Figure 3 shows the layout of working of a smart shirt.
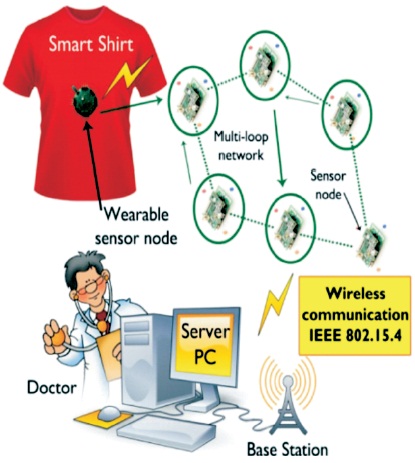
Figure 3. Working Model of a Smart Shirt
Head Mounted Display: This wearable takes the user to a world of virtual reality and provides new visual information directly into the user's eyes.
Sports Watches: It is similar to the fitness tracker that is especially for sports personnel to track the individual's pace, heart rate, etc., which comes with a GPS tracker.
Smart Jewellery: These jewelries are designed as earrings or necklaces to notify the users of their text messages, calls or emails when their phone is out of their range.
Implantable: These wearable electronics are surgically implanted under the skin used for medical reasons like tracking contraception's, insulin levels, etc.
Challenges in Wearables: The biggest challenge in wearable devices is the short lifetime because of the customer engagement. Bad quality, pain to sync with smartphones, poor battery life, uncomfortable and awful design, UX problems, are some of the functional reasons which degrades the quality of device. Like mobile technology, wearable technology is considered as a disruption in the world of business, however, the growth and popularity of a technology always comes with concerns on the problems and difficulties in the area of data security and privacy. Since the devices are worn frequently it may gradually damage the device causing the reduction in the quality.
Problems in WSN: Communication failures are a common problem of WSN. Another issue is heterogeneity. The protocol used to connect the sensor nodes should be simple and light-weighted as it will be difficult to handle huge data at the same time. Communication delay in sensor network can be high because of limited communication channel shared by all nodes within each other's transmission range. Self-Management is the nature of many sensor network applications that they must operate in remote areas and harsh environments, without infrastructure support or the possibility for maintenance and repair. Therefore, sensor nodes must be self-managing in a way that they configure themselves. The nodes should be able to control and adapt themselves according to the field in which they are operated. Sensor nodes are randomly deployed over the region without any infrastructure and prior knowledge of topology. In such a situation, it is the wok of the nodes to identify its connectivity and distribution between the nodes. Many sensor networks, once deployed, must operate without human intervention, that is, configuration, adaptation, maintenance, and repair must be performed in an autonomous fashion. Attenuation limits the range of radio signals, that is, a radio frequency (RF) signal fades while it propagates through a medium and while it passes through obstacles. As a result, an increasing distance between a sensor node and a base station rapidly increases the required transmission power. As a consequence, during these down-times, the sensor node cannot receive messages from its neighbors nor can it serve as a relay for other sensors. Therefore, some networks rely on wake up on demand strategies to ensure that nodes can be woken up whenever needed. A sensor's hardware constraints also affect the design of many protocols and algorithms executed in a WSN. For example, routing tables that contain entries for each potential destination in a network may be too large to fit into a sensor's memory. Instead, only a small amount of data (such as a list of neighbours) can be stored in a sensor node's memory. Many wireless sensor networks collect sensitive information. The remote and unattended operation of sensor nodes increases their exposure to malicious intrusions and attacks. While there are numerous techniques and solutions for distributed systems that prevent attacks or contain the extent and damage of such attacks, many of these incur significant computational, communication, and storage requirements, which often cannot be satisfied by resource constrained sensor nodes thus will be discarded.
The inherent nature of WSNs makes them deployable in a variety of applications. The paper also surveys the various challenges of WSNs that may occur in the near future as when deployed in underwater acoustic sensor systems, sensing based cyber physical systems, time critical applications, cognitive sensing and spectrum management, and security and privacy management. With all the advances in sensor networks from the hardware to the network protocols to the algorithms, it is in some ways surprising that sensor networks are still not mainstream (like the Internet, cell phones, Wi-Fi, etc.)